Email encryption/decryption system and its method
An encryption key and email technology, which is applied in the field of email encryption/decryption systems, can solve problems such as the inability to effectively guarantee the security of email transmission, and achieve the effect of avoiding leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
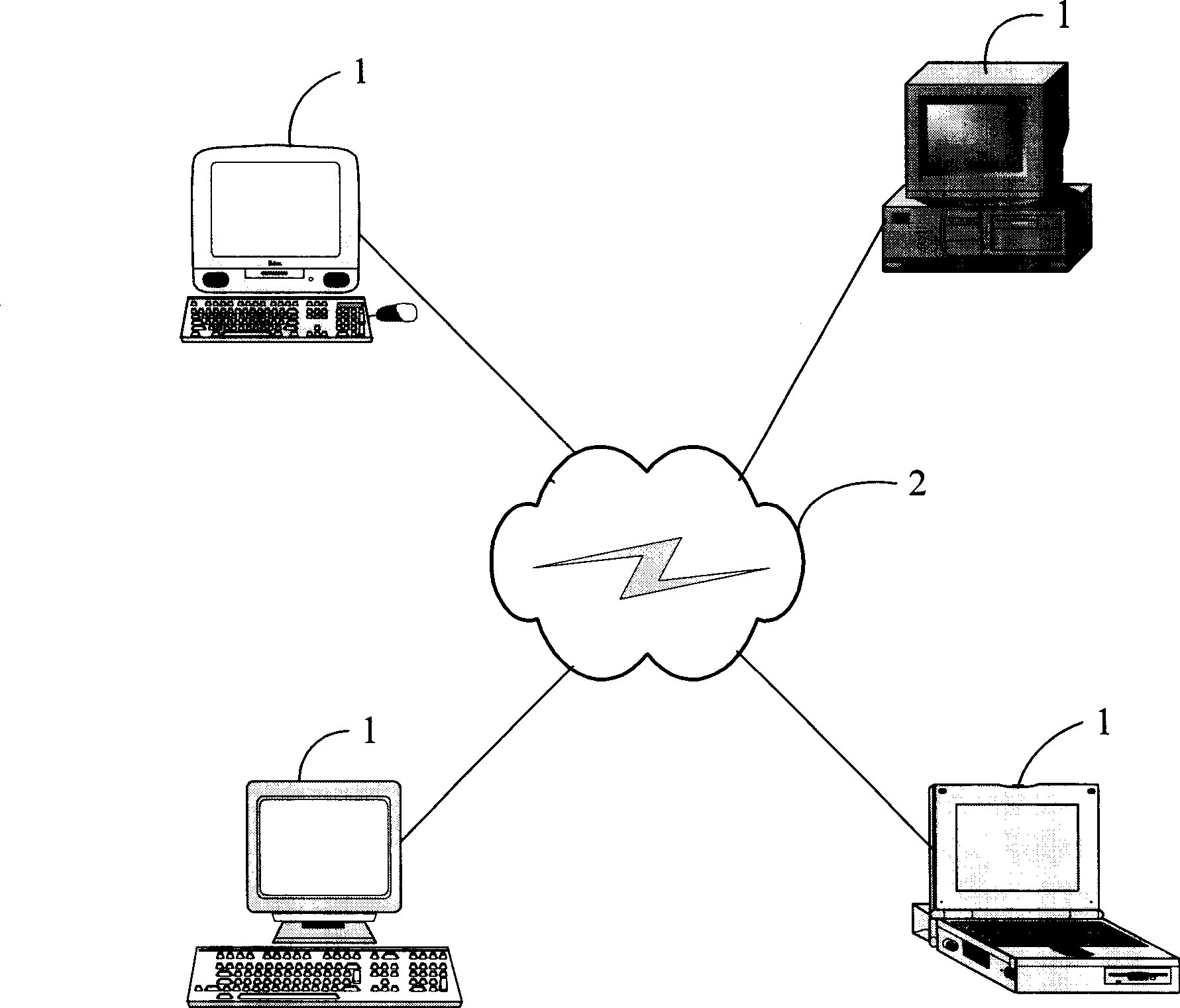
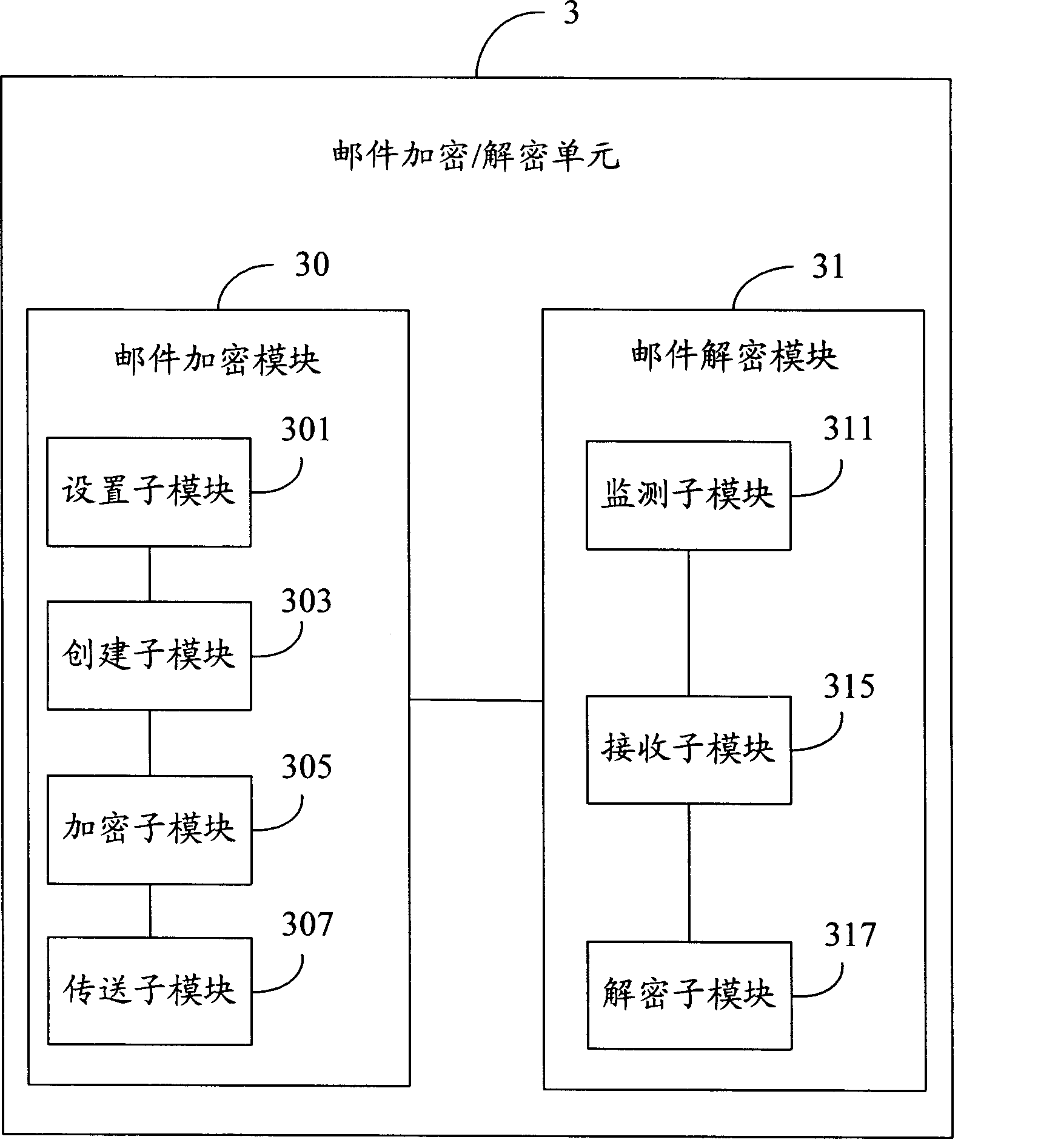
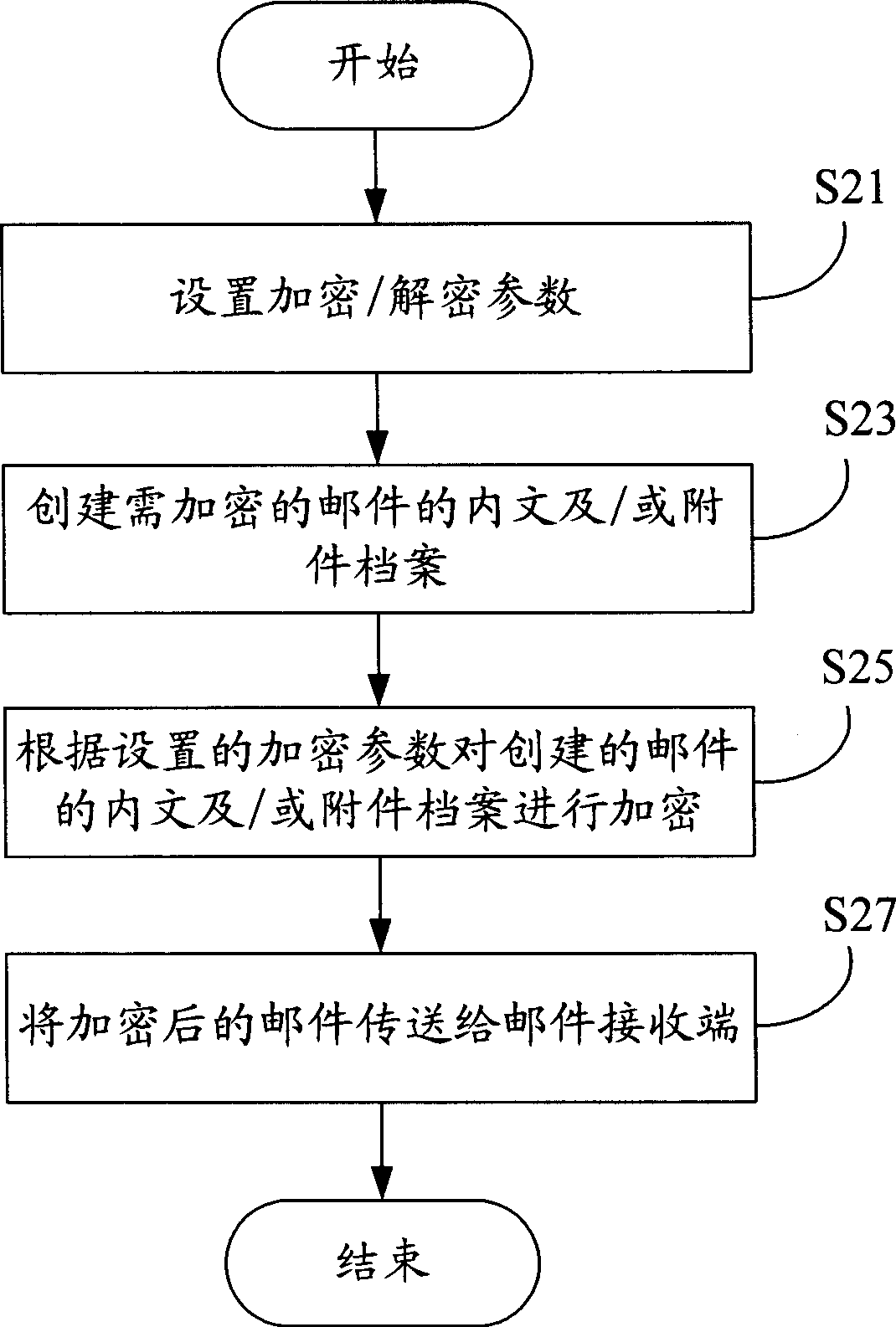
[0014] Such as figure 1 Shown is a hardware architecture diagram of a preferred embodiment of the mail encryption / decryption system of the present invention. The system includes a network 2 for data communication, and a plurality of computers 1 (taking four computers as an example) for communication connection through the network 2 . The network 2 may be the Internet, an intranet or other applicable networks. Described computer 1 can be any applicable data processing equipment, and it is installed with a mail communication software (for example: the Lotus Notes software that U.S. Lotus Company develops), and also is installed with a mail encryption / decryption unit 3 (as figure 2 shown). The computer 1 realizes the mail communication between computers by utilizing the mail communication software. The mail encryption / decryption unit 3 is used for encrypting the mail sent by the computer 1 and decrypting the encrypted mail received by the computer 1 .
[0015] Such as figu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com