A state machine-based security monitoring correlation analysis method and system
A technology of security monitoring and correlation analysis, applied in the field of network security, which can solve the problems of reduced system inspection efficiency and system inspection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The state machine-based safety monitoring association analysis method proposed by the present invention is described as follows in conjunction with the accompanying drawings and embodiments.
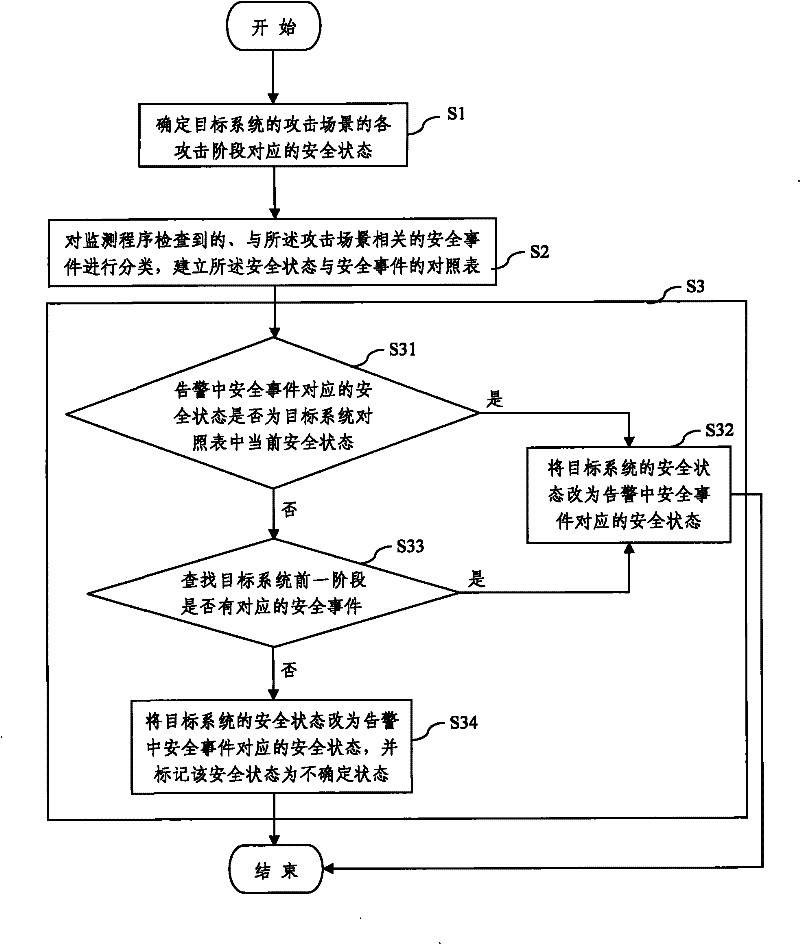
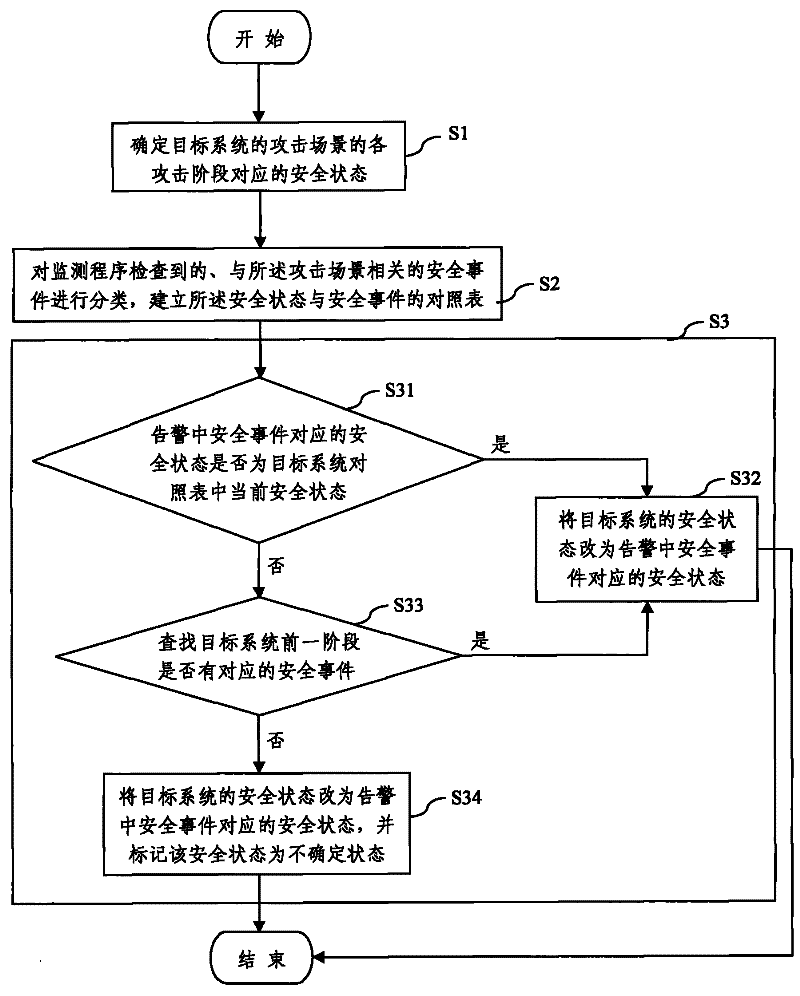
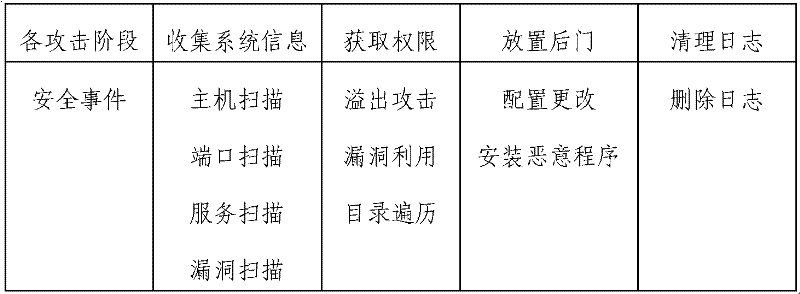
[0036] Such as figure 1 As shown, step S1 determines the security status corresponding to each attack stage of the attack scenario of the target system, where the attack scenario refers to the set of security events generated when interdependent and time-ordered mutual behaviors occur, and the attack scenario can be constructed through rules To identify real attack events and predict the next action of the attack, the security status usually includes the collection of target system information, access to permissions, backdoor entry, and log cleaning.
[0037] In step S2, classify the security events related to the attack scenario detected by each monitoring program, and establish a comparison table of security status and security events, that is, a comparison table of each attack ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com