Effective realization method for credible OpenSSH
An implementation method, a trusted technology, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve problems such as security, functional compatibility, performance, and rapid deployment without considering and solving
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
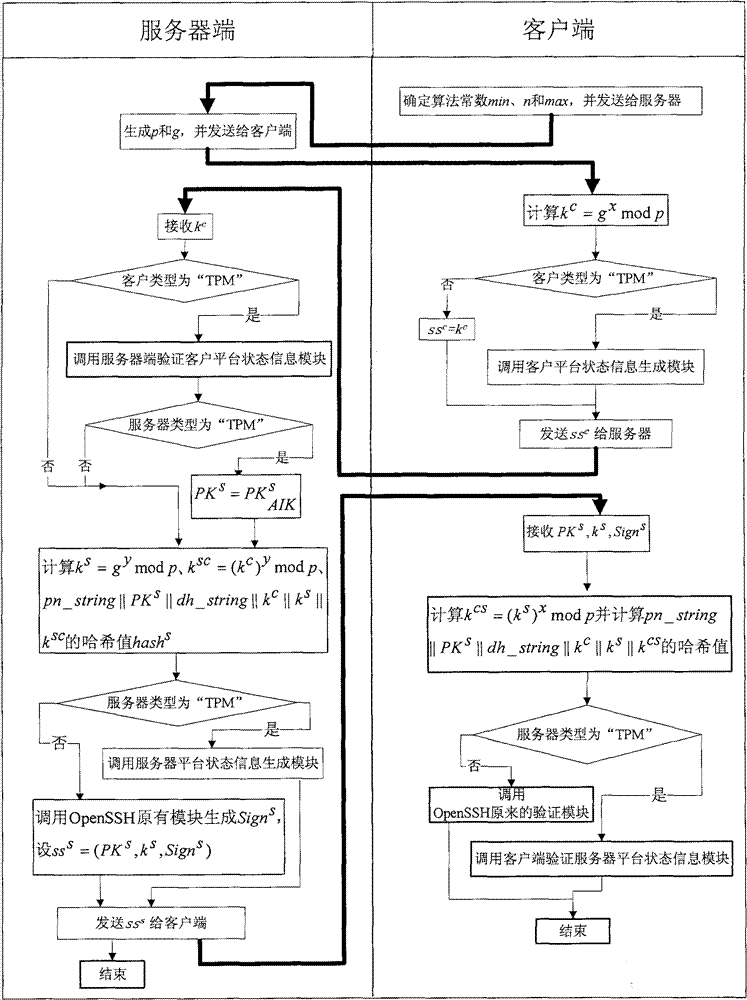
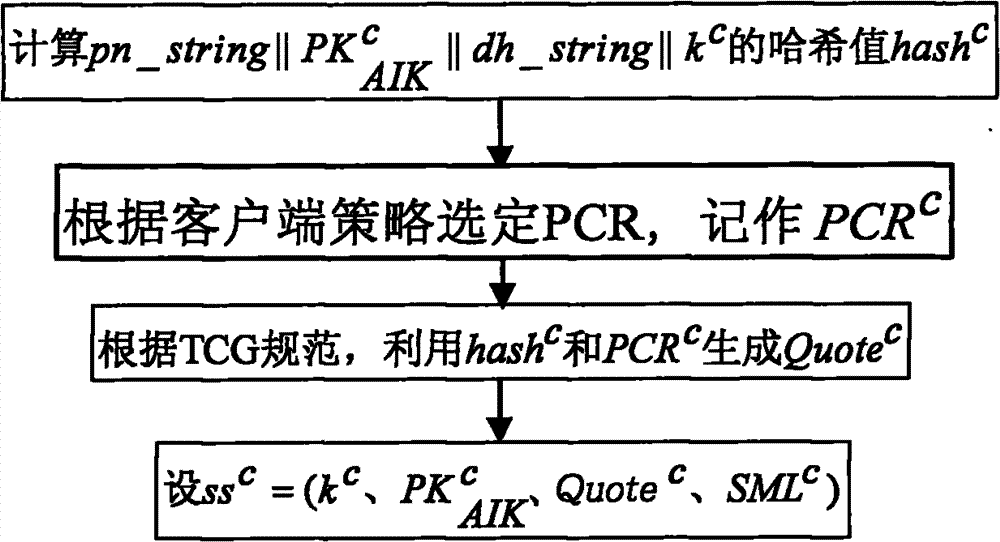
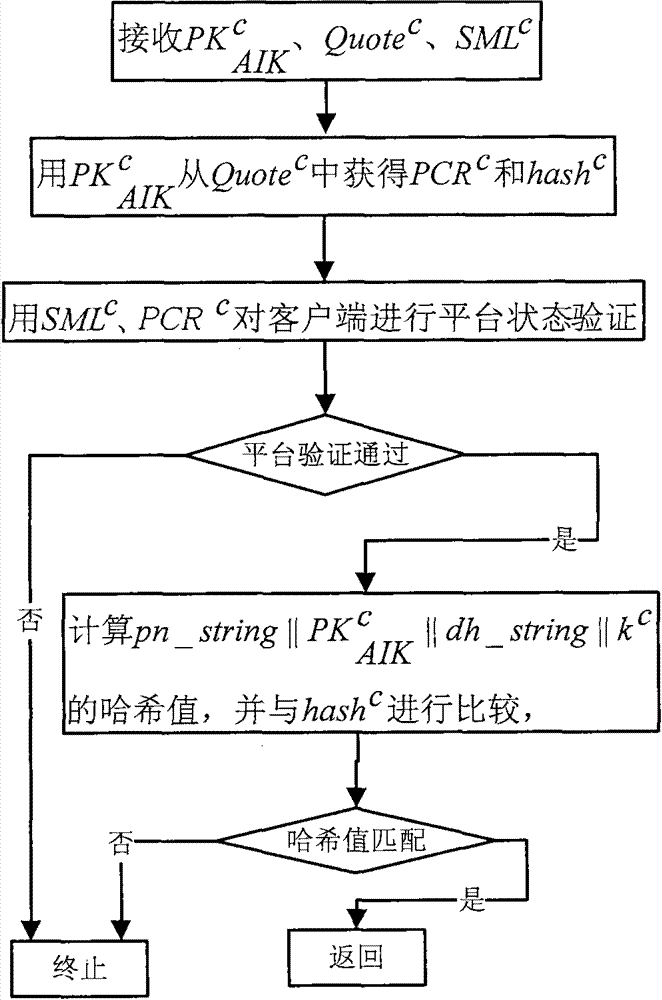
[0032] The method provided by the present invention assumes that the server and the client are equipped with a trusted security chip TPM on the hardware, and the BIOS of the server and the client both support TPM; on the software, it is assumed that the server and the client are installed with an operating system trusted boot manager, A trusted operating system that supports hardware TPM and trusted measurement modules is installed. In addition, the server and client are installed with TPM software protocol stack (TrouSers) software. The specific implementation steps of the method provided by the present invention in version 4.7 and above of the open source OpenSSH software are as follows:
[0033] Step 1. Modify the formation process of the identity authentication algorithm negotiation string: add three candidates, which are represented by the variables ssh-TPM-TPM, ssh-TPM-option, and ssh-option-TPM; trusted client and available The server side constructs an identity authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com