WLAN (wireless local area network) credible transmission realization method based on 802.1x authentication protocol
A technology of authentication protocol and implementation method, applied in the direction of wireless network protocol, wireless communication, network topology, etc., to achieve transparency and ensure the effect of real connection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
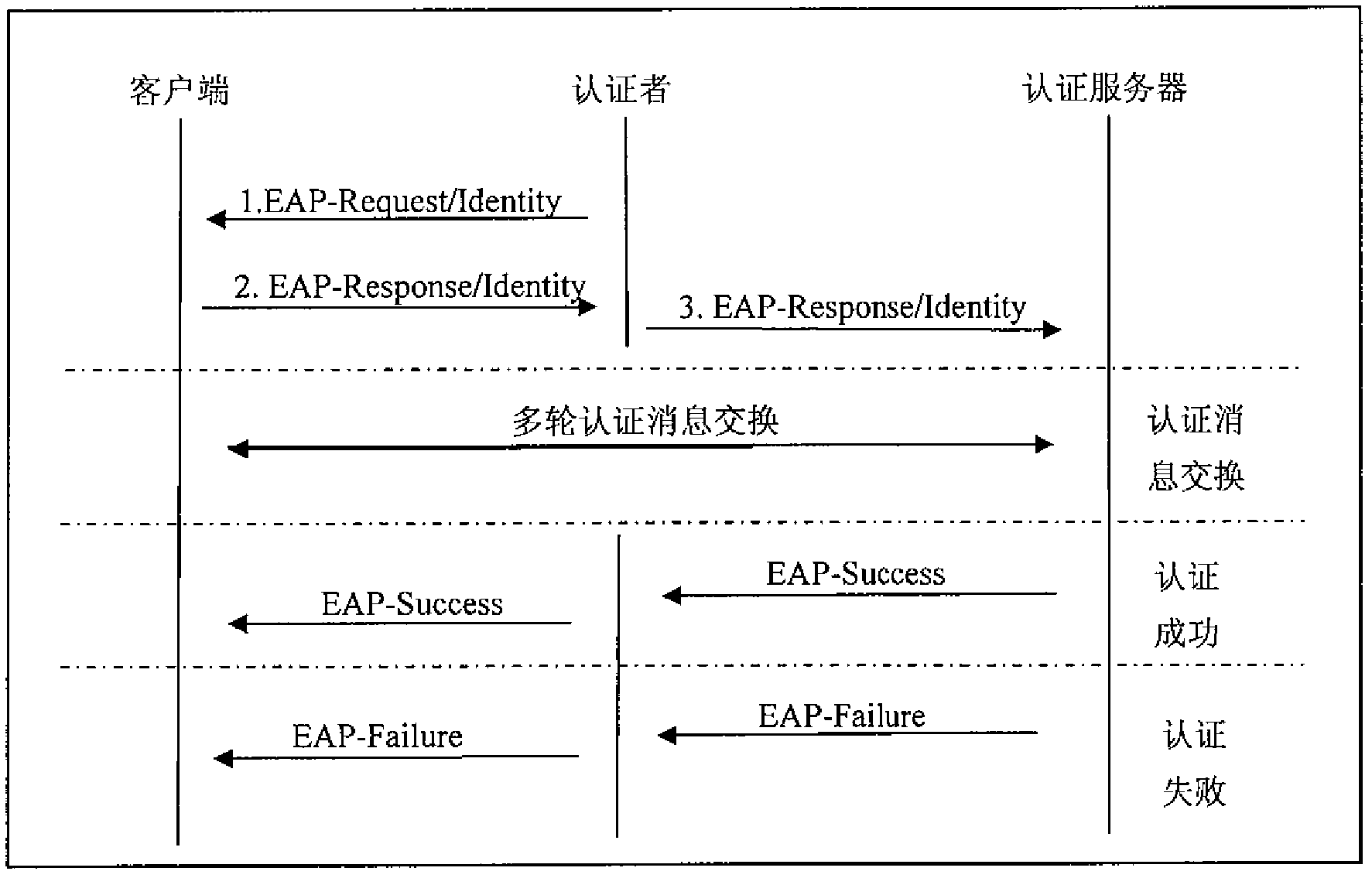
[0039] A method for realizing WLAN trusted transmission based on the 802.1x authentication protocol of the present invention requires the client to be equipped with a trusted security chip TPM on hardware, and its BIOS supports the TPM; and requires the client to install a measurement module on software. The client has its own AIK public and private keys. The method provided by the present invention needs to make the following modifications to the 802.1x authentication protocol:
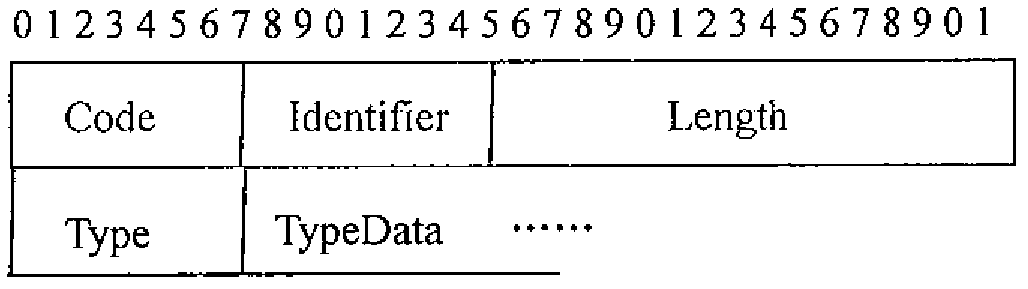
[0040] (1) Define a new value for the Type field in the EAP packet, denoted as TPM, which is used to indicate that the authentication server side needs to verify the platform status information of the client. When the value of the Type field is TPM, the value of the corresponding TypeData field is used to describe the type of platform information to be verified. In the present invention, an EAP-Request (Response) whose Type field value is TPM is recorded as EAP-Request (Response) / TPM.
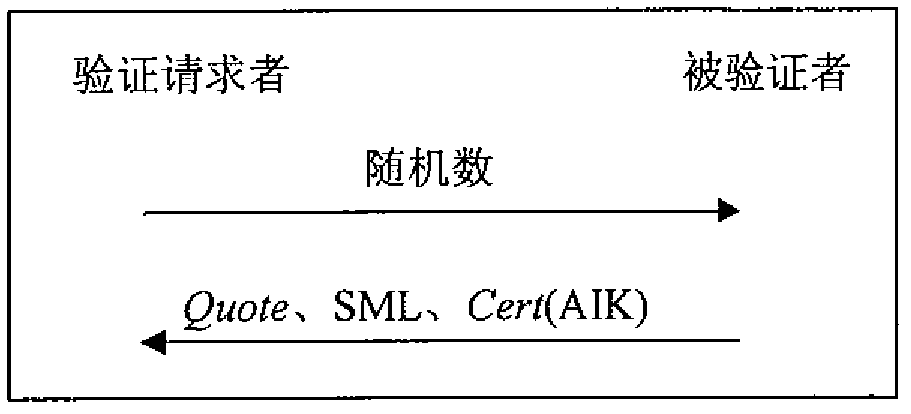
[0041] In t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com