Key expanding method for encrypting block cipher
A key expansion, block cipher technology, applied in the field of data encryption and decryption, can solve the problems of not being able to resist cryptanalysis, reducing practicability, and not being able to achieve high-speed, synchronous encryption and decryption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
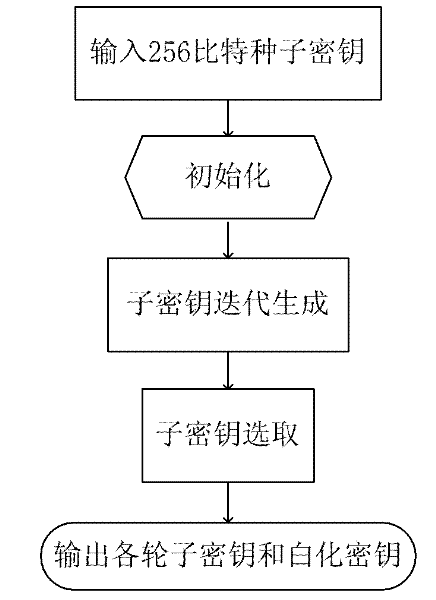
[0050] The following describes technical details such as steps, schemes and other technical details of generating 8 rounds of block cipher algorithms with a key length of 256 bits and whitening subkeys through a 256-bit seed key, so as to provide a thorough understanding of the present invention.
[0051] according to figure 1 implementation flow chart. The present invention implements the steps of initialization, key iterative generation algorithm and sub-key selection algorithm in sequence.
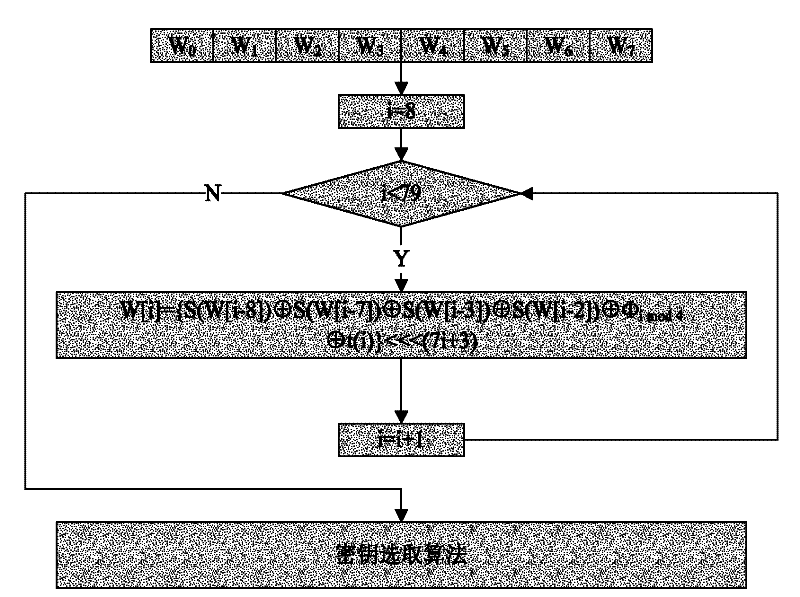
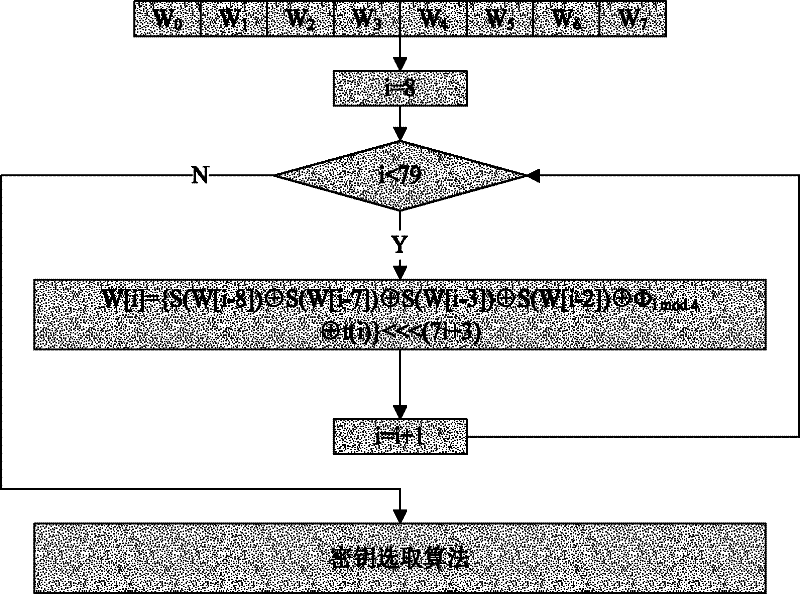
[0052] In the initialization, the 256-bit seed key is written into the array in sequence: W[0], W[1], W[2], W[3], W[4], W[5], W[6], W[7], as input. W[8], W[9], ..., W[79] are used to store the subkeys generated by extension.
[0053] The extended key is iteratively generated by the subkey iterative algorithm, the principles and methods of the extended structure design, iterative function design and constant design are as described in the content of the invention, and the iterative pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com