Mobile user identification code IMSI protection method based on pseudonym
A technology of mobile user identification and user identification, which is applied in the field of mobile communication security, and can solve problems such as costly, difficult to use, and insufficient compatibility of existing users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
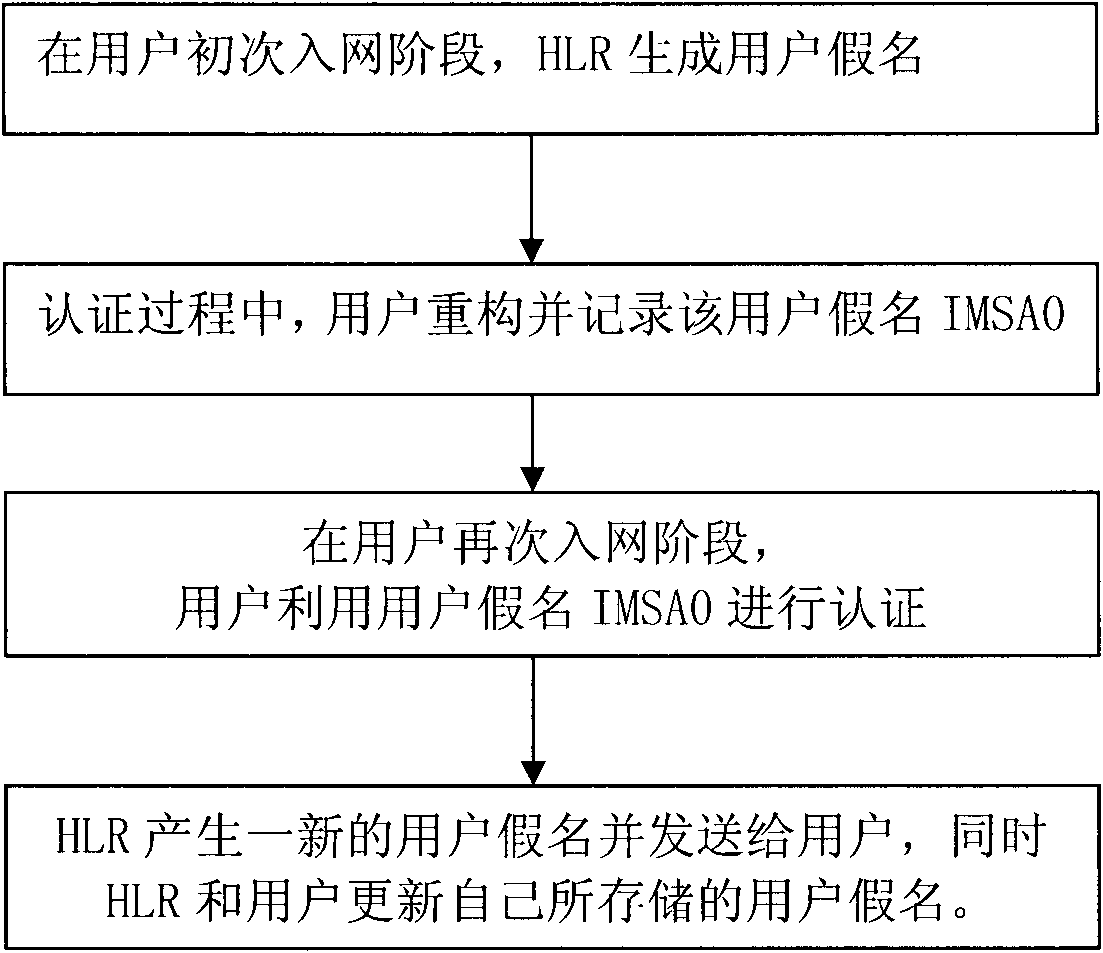
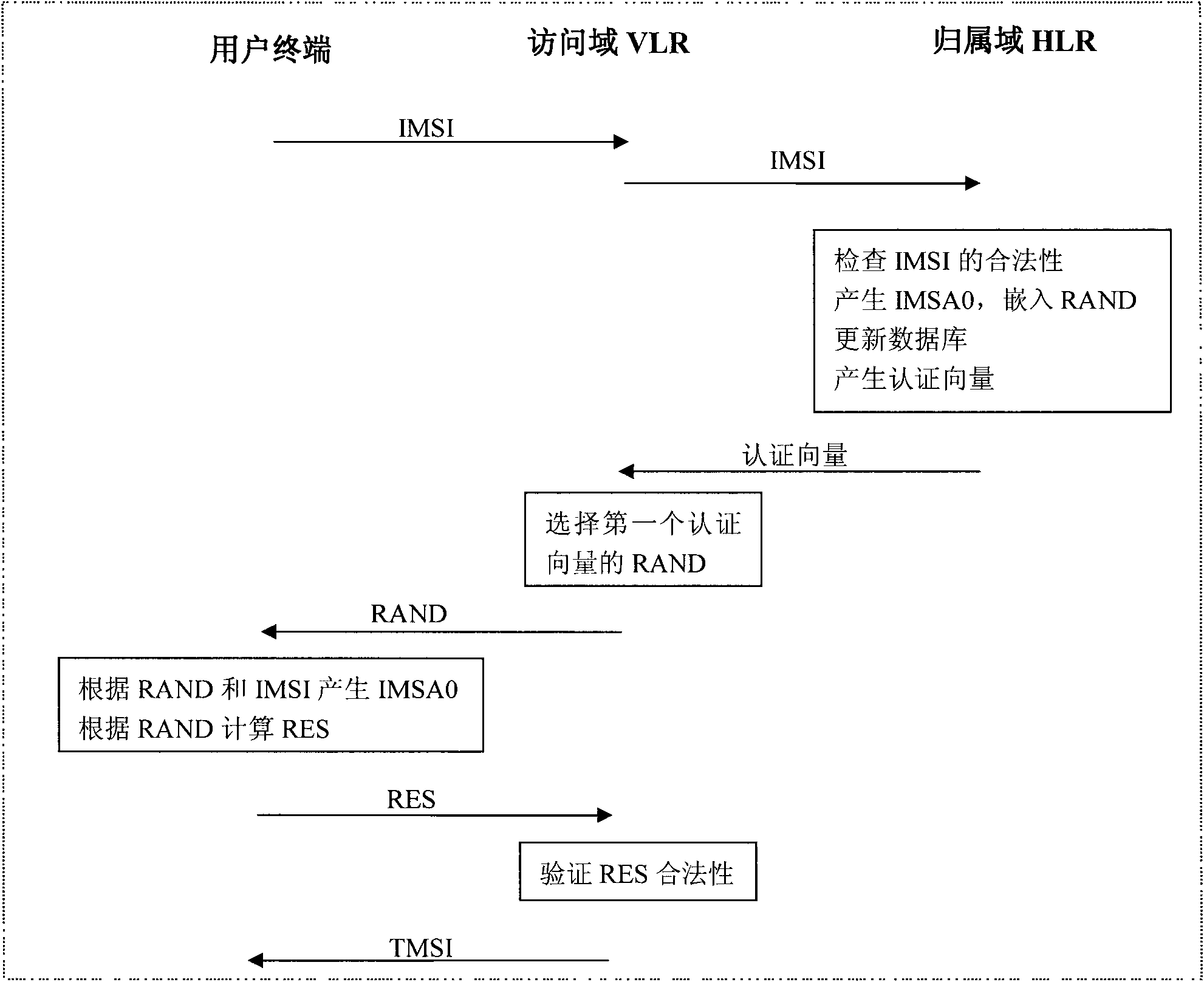
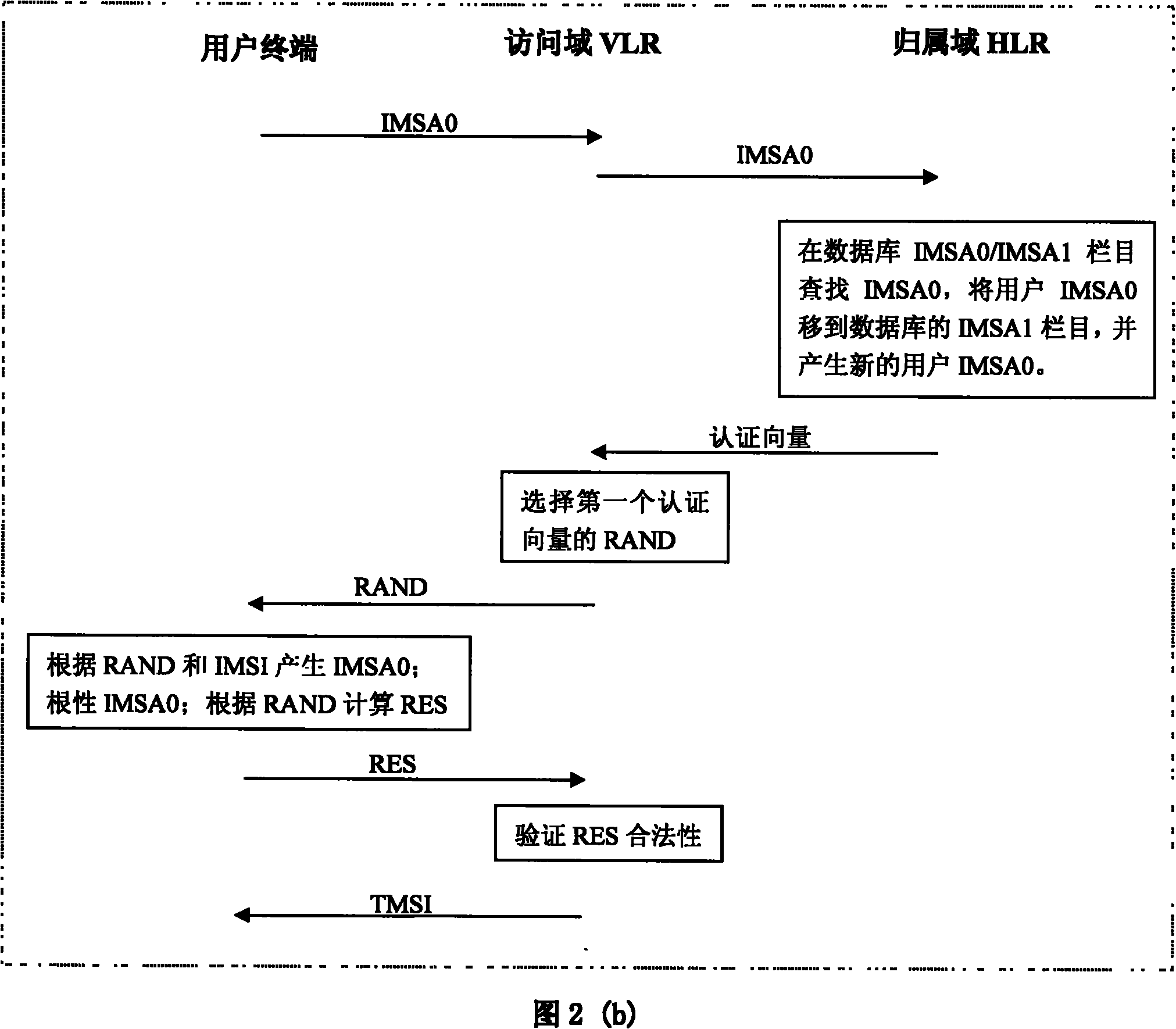
[0087] In order to better illustrate the working principle of the present invention, a specific embodiment is given below. Suppose a mobile user’s IMSI number is 460010911221001, then according to the first 3 digits of the IMSI number, it can be determined which country the user is from. According to the agreement, 460 means China, so when roaming anywhere in the world, after seeing the IMSI number, The route to find the HLR is first transferred to an interface in China according to the first three digits 460. Then determine the operator according to the next 2 digits 01, the next 2 digits 09 are fixed, the next 4 is the number 1122, which means the HLR logo in the operator represented by 01, and the last 4 digits are 1001 Indicates the user whose identification field is 1001 in the HLR. This embodiment considers the situation that the user pseudonym field has only 4 bits (that is, 16 bits).
[0088] When it is necessary to generate IMSA0 according to the IMSI, the first 11 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com