Method and system for determining legal terminal
A judgment method and terminal technology, applied in the field of communication, can solve the problem of being unable to distinguish between a completely cloned terminal and a legitimate terminal, and achieve the effect of protecting rights and interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
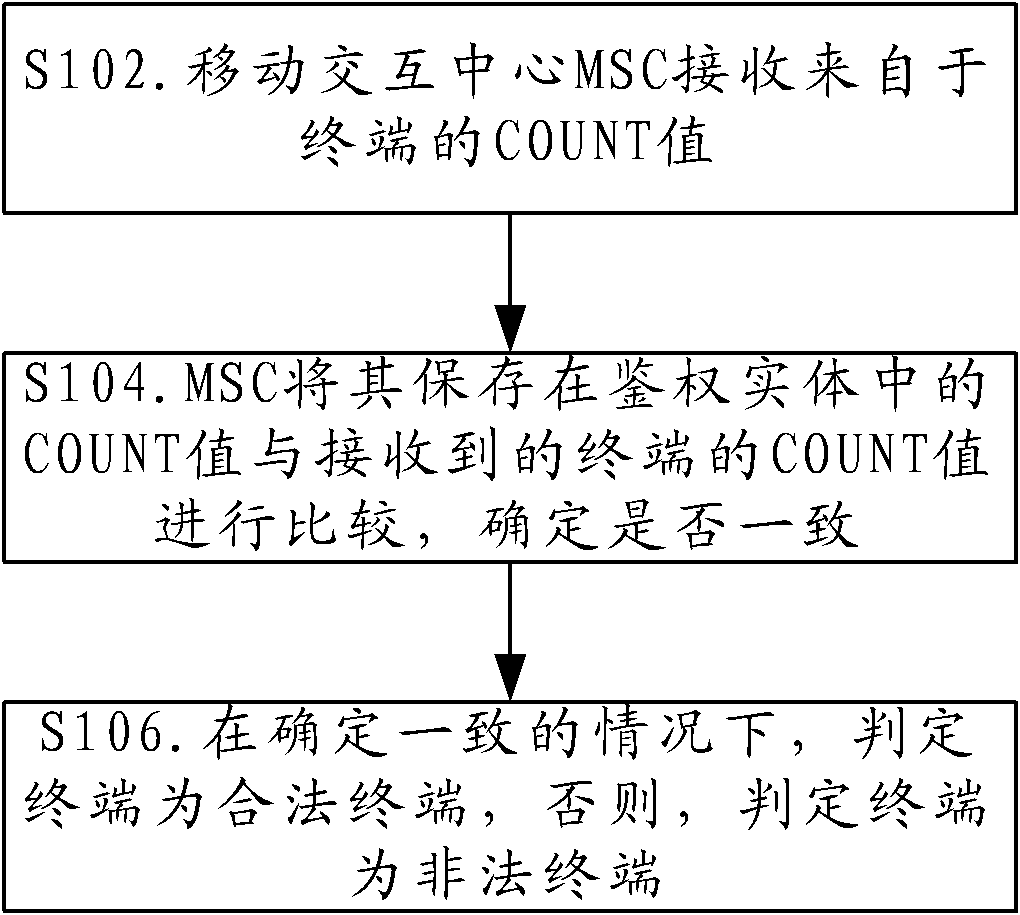
[0036] Assume that the updated COUNT value of the legal terminal is 1 (0 before the update), the COUNT value of the clone terminal is 0, and the COUNT value recorded by the authentication center is the updated COUNT value of the legal terminal. Both BS and MSC are set to require authentication. In this way, the terminal will carry authentication parameters in the access message.
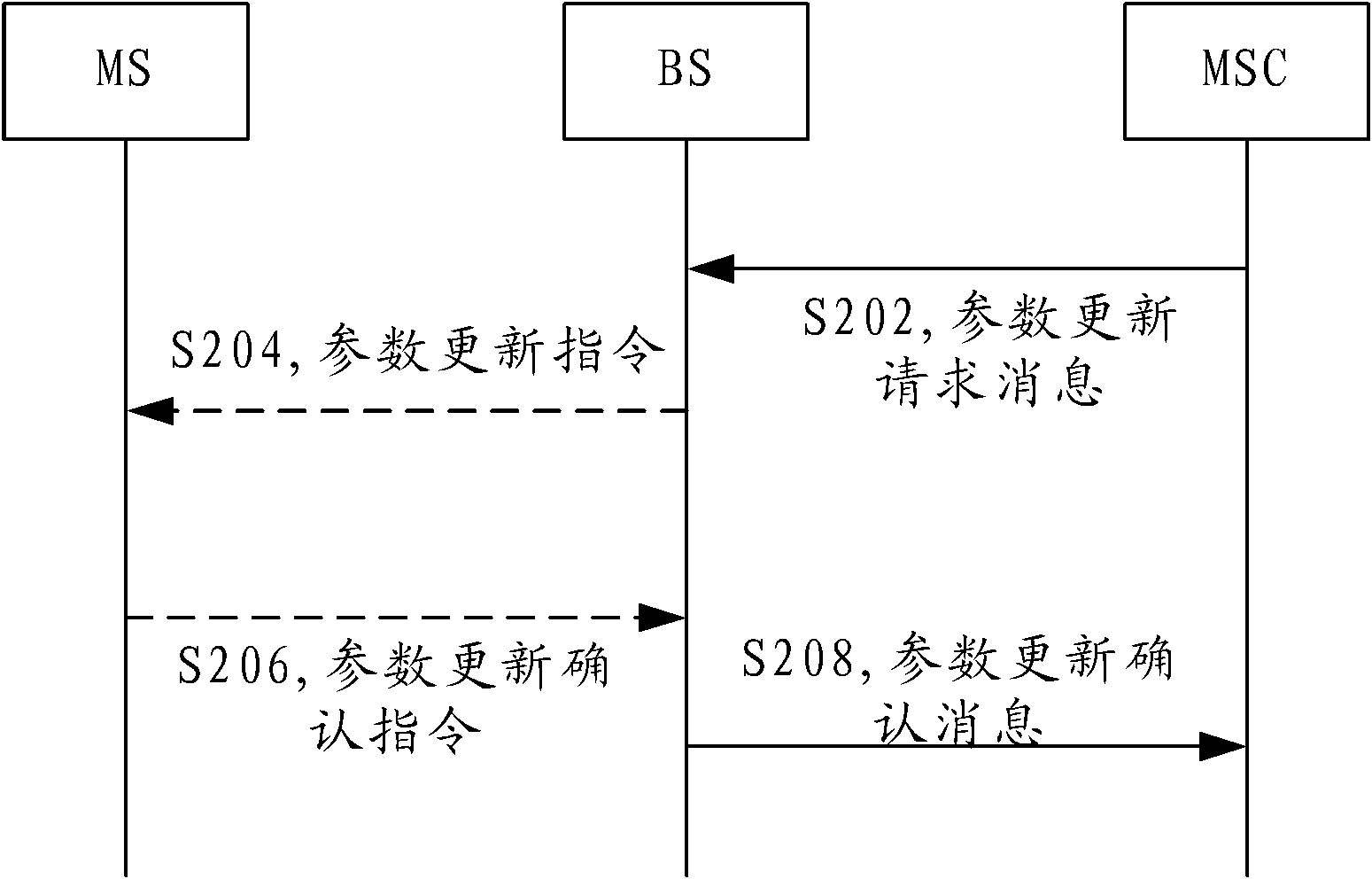
[0037] After the caller is successfully established, the core network initiates a parameter update process, so that the terminal can update the COUNT value of the authentication parameter. By default, the COUNT value saved by all terminals is 0. When the terminal receives a Parameter Update Order (Parameter Update Order) message, the above-mentioned legal terminal will update the COUNT and save the new COUNT value. When the call comes in, it will In the authentication parameters, the updated COUNT value is brought to the BS, and the BS transparently transmits it to the MSC.
[0038] Combine the followin...
Embodiment 2
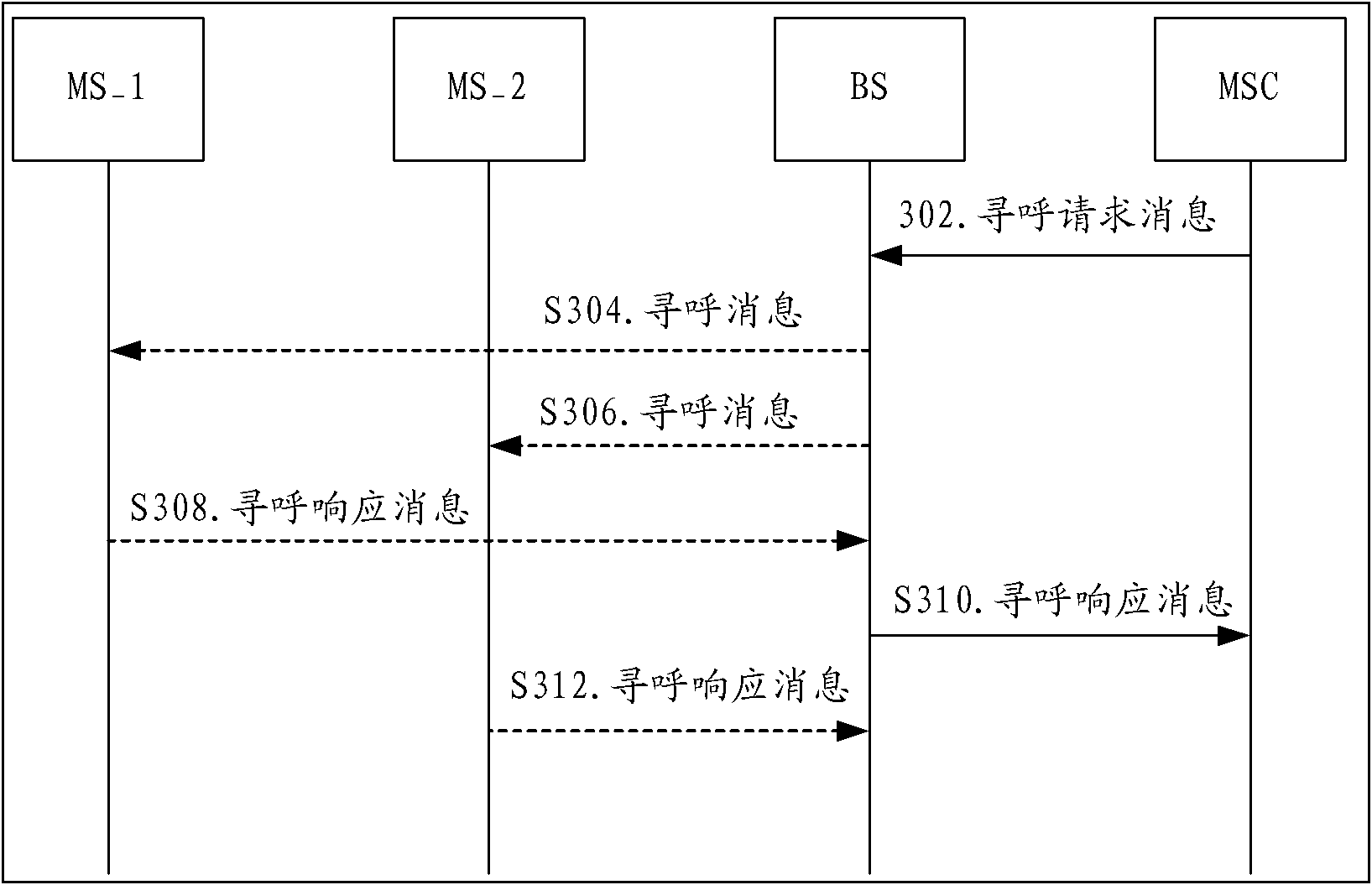
[0057] In this embodiment, the COUNT field is added to the paging request message. When the core network sends the paging message, the recorded COUNT value of the legal terminal is sent to the BS through the paging message, and the BS is recording the COUNT value of the paging message. When the BS receives the paging response, it compares the COUNT value of the authentication parameter in the paging response message with the COUNT value of the authentication parameter of the paging request message. If the COUNT value is inconsistent, it means that the paging response message returned by the clone terminal is cloned. The BS directly discards the paging response message and does not process it. If the COUNT value is consistent, it continues processing according to the normal paging response flow. This can avoid the problem of paging failure caused by the clone terminal first responding. In order to better understand the above process, the following combination Figure 4 Detailed ...
Embodiment 3
[0073] This embodiment is implemented by modifying the air interface protocol. It is necessary to also add the COUNT field in the channel assignment message. When the call is established, the COUNT value of the legal terminal is filled in the channel assignment. After the terminal receives the channel assignment, it saves it with the COUNT value in the message. When the COUNT value is inconsistent, the channel assignment message is not processed, and the channel assignment message is processed only when the COUNT value is consistent. Specifically, such as Image 6 As shown, it should be noted that this embodiment needs to be performed before specific implementation Figure 5 Step S502 in the illustrated embodiment and before step S502 Figure 4 The steps of the above embodiment. Specifically, the specific implementation plan includes:
[0074] Step S602, the BS sends a channel assignment message to the cell accessed by the legal terminal MS_2 and the non-access message supporting...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com