Key negotiation method, key management server and terminal
A technology of key management and key negotiation, which is applied in key distribution to reduce the transmission of signaling and ensure the security of media streams
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
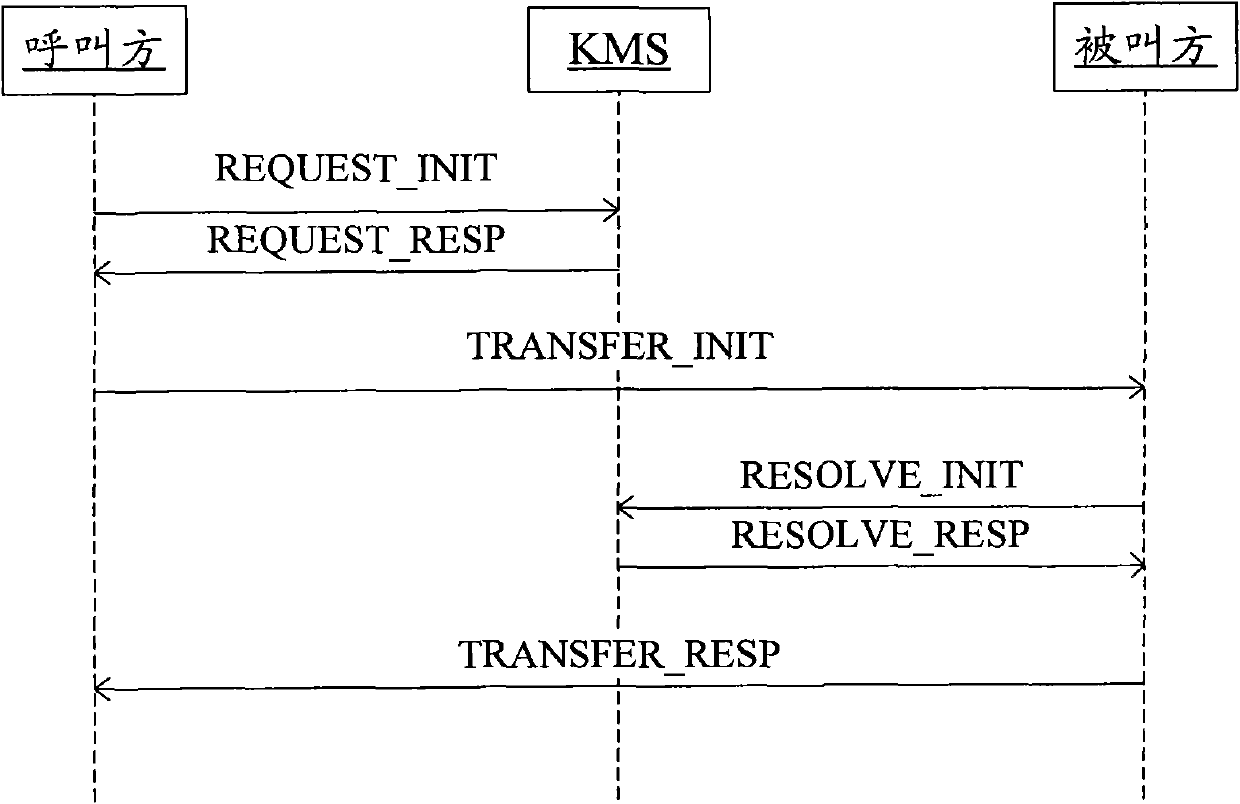
[0059] Figure 7 is a flowchart of a method for common end-to-end key agreement according to an embodiment of the present invention, such as Figure 7 As shown, the method includes the following steps S701 to S707:
[0060] In step S701, the caller IMS user A first determines the ticket policy, takes corresponding methods according to the policy, and generates corresponding parameters.
[0061] From step S702 to step S703, user A generates a random number Ra, writes Ra into TICKET in OR payload Ea(Ra||ID-A||ID-B), and then puts ID-A, ID-B and TICKET into TRANSFER_INIT message, put the TRANSFER_INIT message in the SIP INVITE message and send it to user B through the IMS network, where Ea(Ra||ID-A||ID-B) is Ra| encrypted by the shared secret key Ka of user A and KMS |ID-A||ID-B, where ID-A and ID-B are the public user IDs of users A and B respectively. In addition, BTIDa needs to be carried in the plain text, which is used to instruct KMS to go to the BSF to obtain the A's sh...
example 2
[0069] Figure 8 is a flowchart of a method for key agreement in a Forking scenario according to an embodiment of the present invention, such as Figure 8 As shown, the method includes the following steps S801 to S810:
[0070] Step S801: First, the caller IMS user A determines the ticket policy, takes a corresponding method according to the policy, and generates corresponding parameters.
[0071] From step S802b to step S803b, user A generates random number Ra, writes Ra into TICKET in OR payload Ea(Ra||ID-A||ID-R), and then puts ID-A, ID-R and TICKET into TRANSFER_INIT message, put the TRANSFER_INIT message in the SIP INVITE message and send it to user B through the IMS network, where Ea(Ra||ID-A||ID-R) is Ra| encrypted by the shared secret key Ka of user A and KMS |ID-A||ID-R, where ID-A and ID-R are the public user IDs of the calling user and the called user respectively. In addition, the plain text also needs to carry BTIDa, which is used to instruct KMS to go to BSF to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com