Method for protecting mobile phone information security
A mobile phone information and security technology, applied in the direction of telephone communication, branch equipment, electrical components, etc., can solve problems such as user losses, and achieve the effect of preventing losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
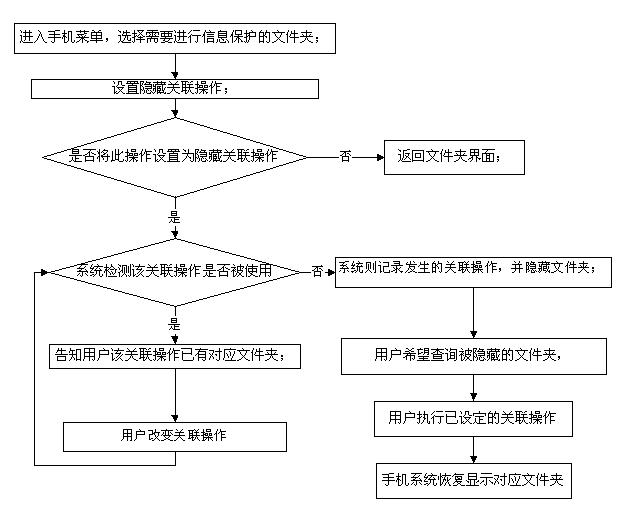
[0025] Such as figure 1 As shown, in an embodiment of a method for protecting mobile phone information security according to the present invention, the method includes the following steps:
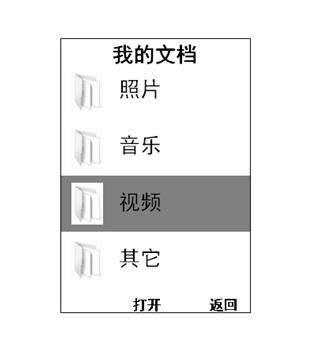
[0026] S1. Enter the mobile phone menu, select the folder that needs information protection, such as figure 2 ;
[0027] S2. Set the associated operation of hiding "video", such as long pressing the "*" key; in order to prevent misoperation, the system performs the following steps:
[0028] S2.1. The system asks the user whether to long press the "*" key as the associated operation of this file, such as image 3 ;
[0029] S2.2. If no, return to the folder interface; if yes, enter step S3.
[0030] S3. If the associated operation is not used, the system will record the associated operation and hide the folder, as shown in the figure;
[0031] S4. If the associated operation has been used, the system informs the user that the associated operation has a corresponding folder; the user c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com