Method and architecture for handling conflict of security policies and unified converter
A technology for security policy and conflict handling, which is applied in the field of communication and can solve problems such as security policy conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The purpose of the present invention is to provide a general and extensible security policy conflict detection and resolution framework and processing method to meet the requirements of unified security policy deployment.
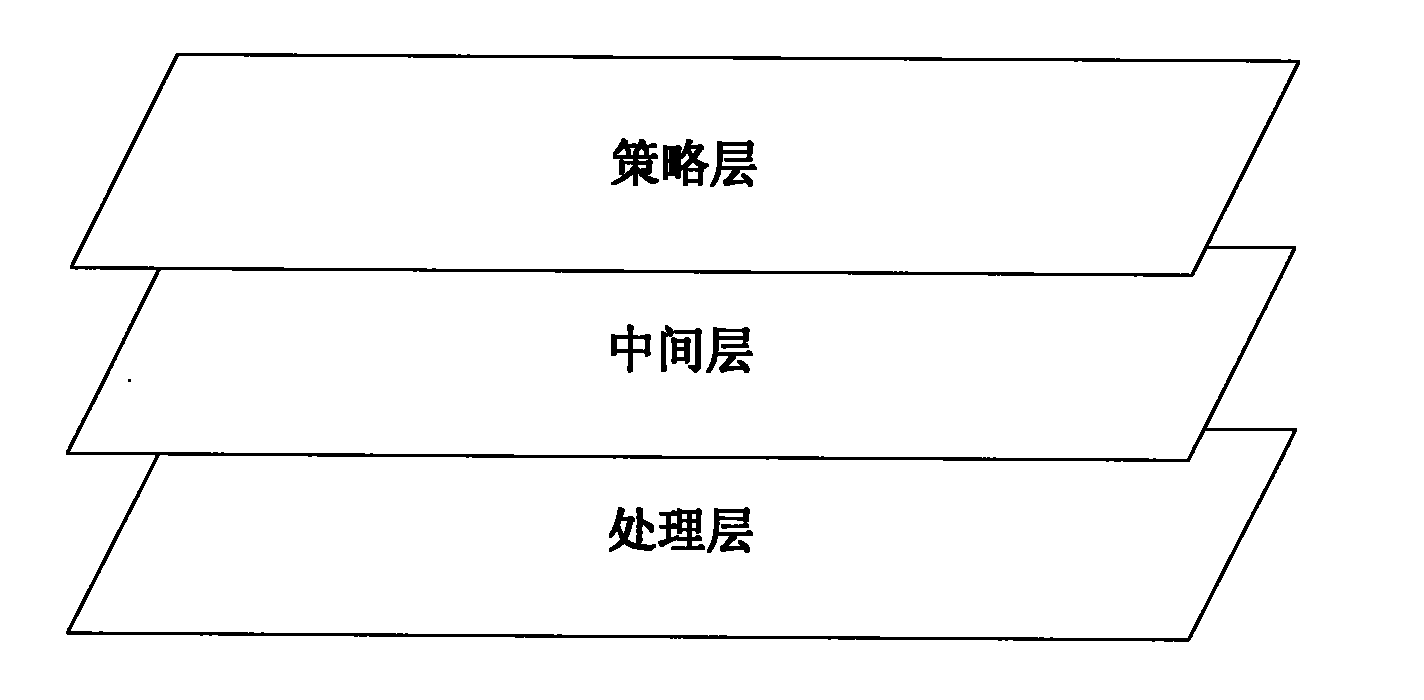
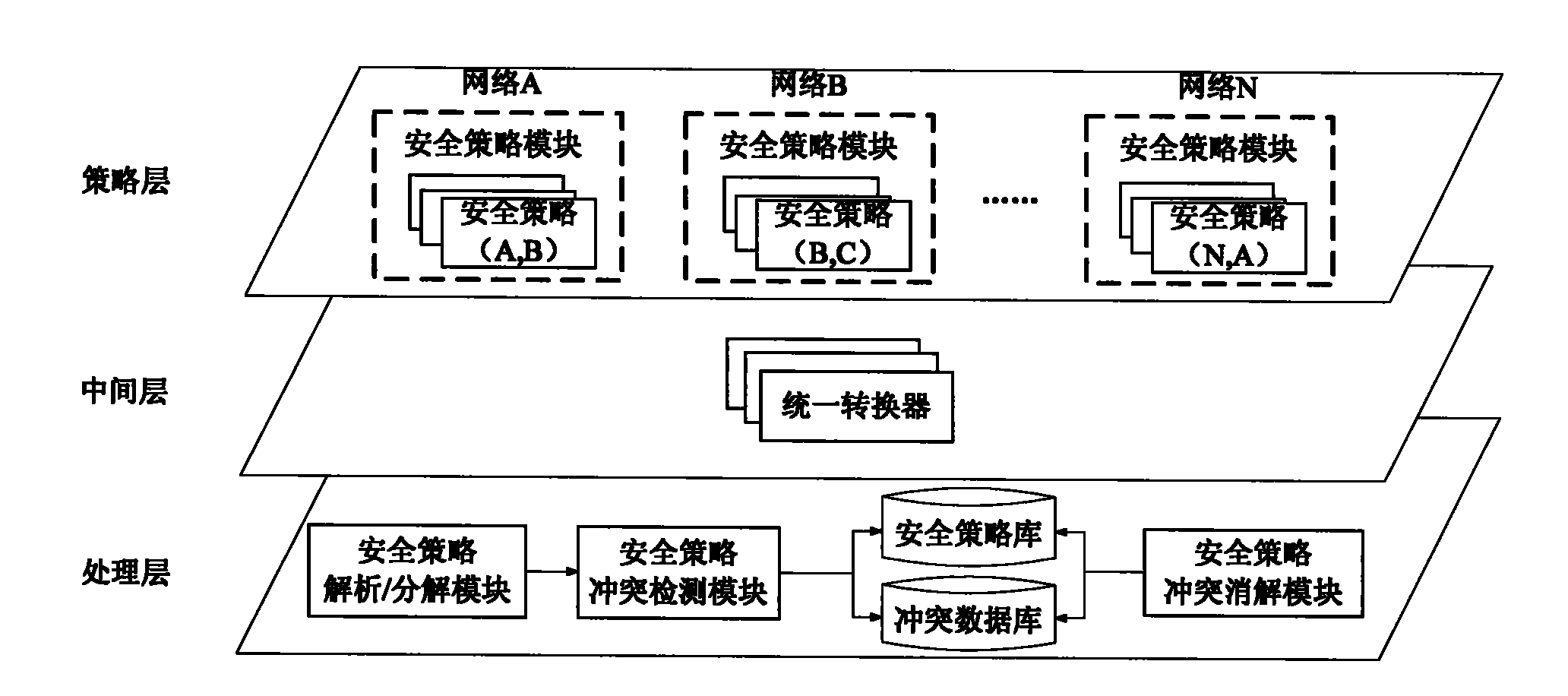
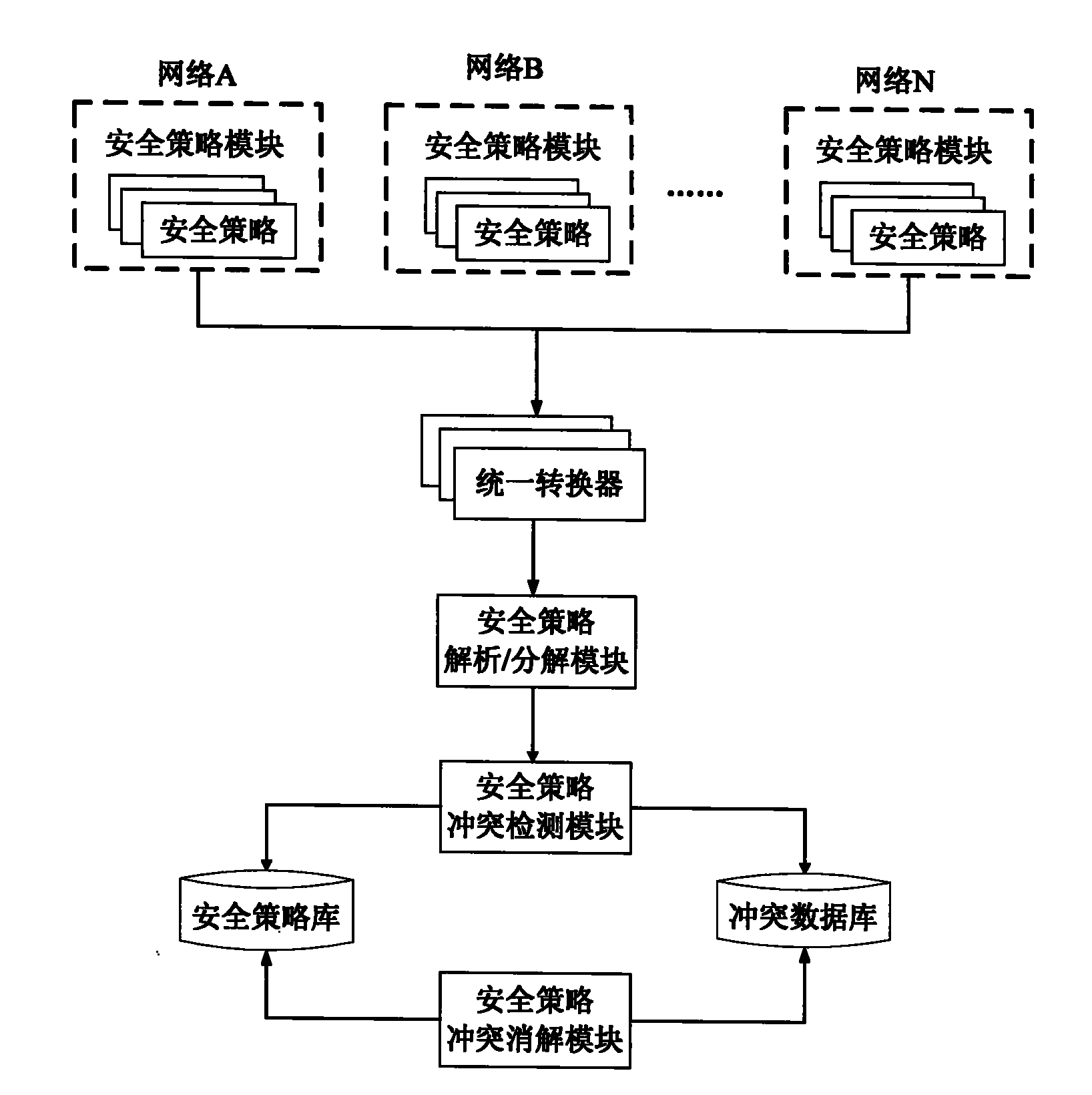
[0048] In order to achieve the above purpose, the embodiment of the present invention provides a security policy conflict processing architecture, such as figure 1 As shown, the architecture can be divided into the following three layers: strategy layer, middle layer and processing layer. Among them, the main functions of each layer are described as follows:
[0049] Policy layer, which is a collection of security policies and is used to carry security policies from different networks. These security policies can be defined through different formal specification languages or GUI methods.
[0050] Among them, the security policy is a description of behavior rules related to system security, which can guide the behavior management of the system on a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com