Method for forwarding message, and method and device for generating table entry
A technology for forwarding messages and entries, applied in the field of communications, and can solve problems such as large storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
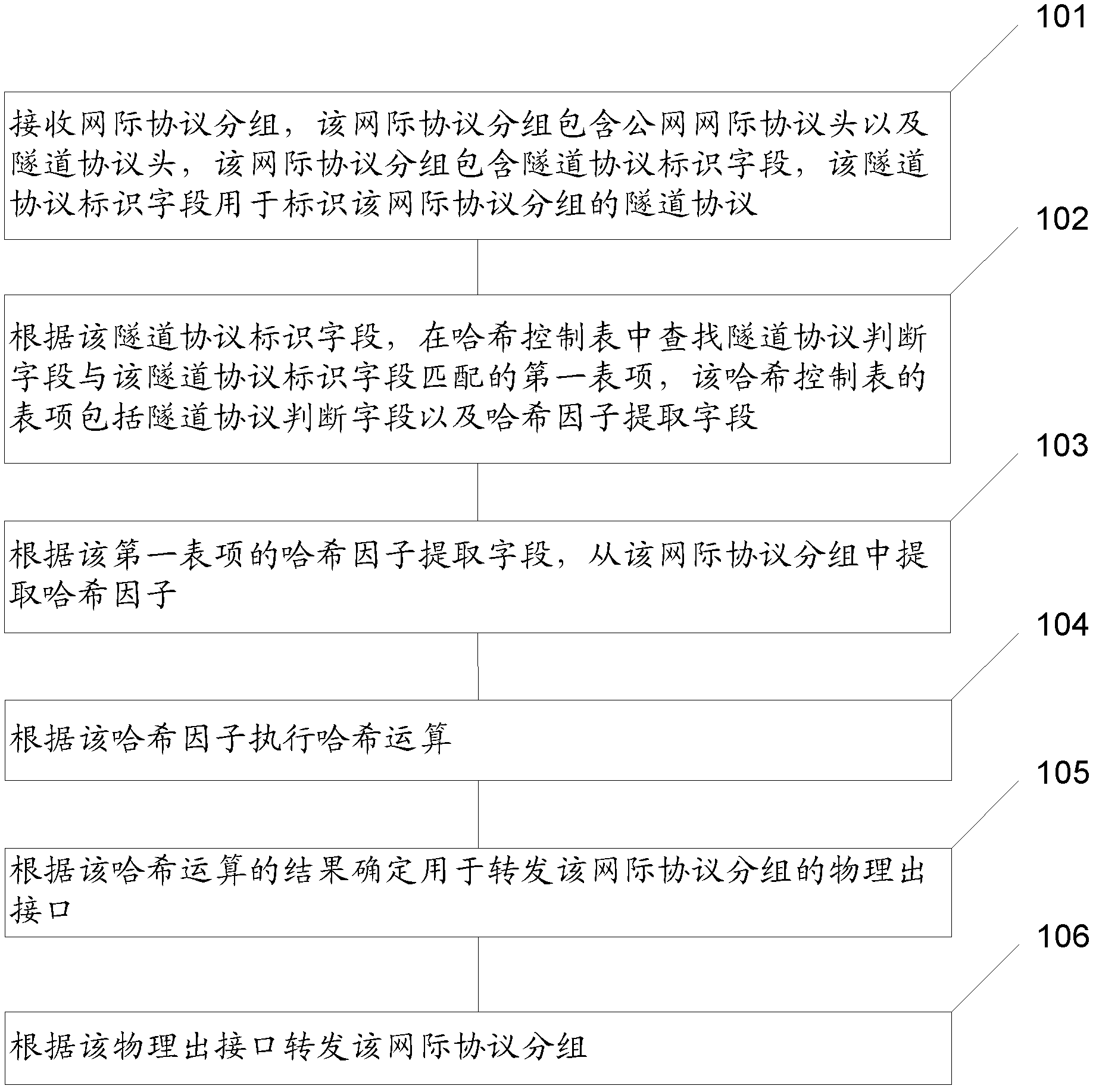
[0035] The embodiment of the present invention provides a method for forwarding a message, which can be used in a scenario where a hash operation is required. For example, when a router forwards an IP packet whose tunneling protocol is the GRE protocol, according to the packet forwarding method provided in the embodiment of the present invention, a hash factor can be obtained from the IP packet, and then a hash operation can be performed. see figure 1 , figure 1 It is a flowchart of a method for forwarding a message provided by an embodiment of the present invention, and the method includes:
[0036] 101: Receive an IP packet, where the IP packet includes a public network IP header and a tunnel protocol header. The Internet Protocol packet contains a Tunneling Protocol Identification field. The tunnel protocol identification field is used to identify the tunnel protocol of the Internet protocol packet.
[0037] During specific implementation, the Internet Protocol of the I...
Embodiment 2
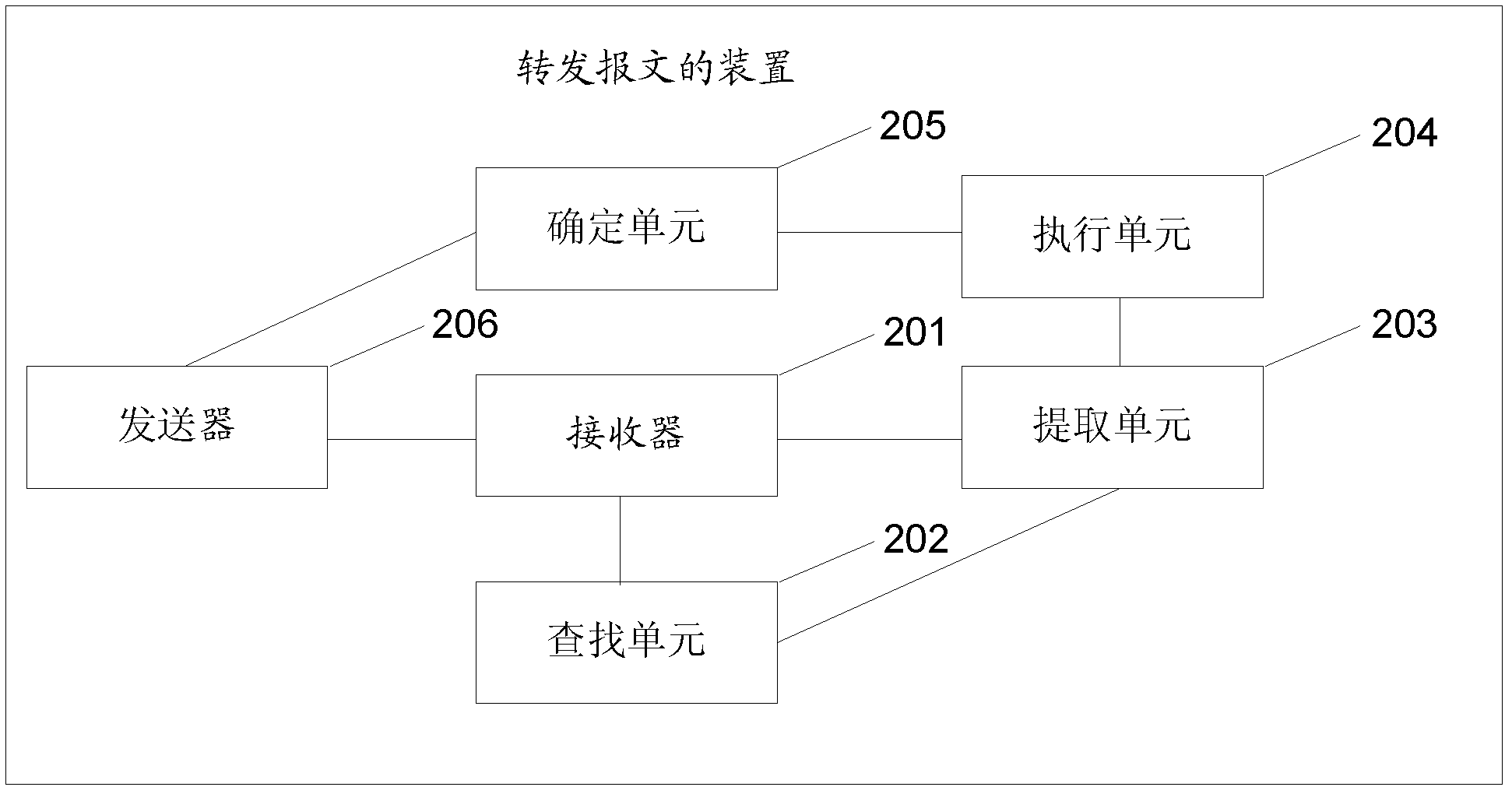
[0083] An embodiment of the present invention provides a device for forwarding messages, which can be used in scenarios where hash operations are required. For example, when a router forwards an IP packet whose tunneling protocol is the GRE protocol, the device for forwarding a packet according to the embodiment of the present invention can obtain a hash factor from the IP packet, and then perform a hash operation. see figure 2 , figure 2 It is a schematic diagram of a device for forwarding a message provided by an embodiment of the present invention, and the device includes:
[0084] The receiver 201 is configured to receive an IP packet, and the IP packet includes a public network IP header and a tunnel protocol header. The Internet Protocol packet contains a Tunneling Protocol Identification field. The tunnel protocol identification field is used to identify the tunnel protocol of the Internet protocol packet.
[0085] During specific implementation, the Internet Prot...
Embodiment 3
[0132] The embodiment of the present invention provides a method for generating table entries, which can be used in scenarios where hash operations are required. For example, when a router forwards an IP packet whose tunneling protocol is the GRE protocol, according to the method for generating an entry provided by the embodiment of the present invention, a hash factor may be obtained from the IP packet, and then a hash operation may be performed. see image 3 , image 3 It is a flowchart of a method for generating entries provided by an embodiment of the present invention, and the method includes:
[0133] 301: Generate an entry of the hash control table, the entry includes a tunnel protocol judgment field and a hash factor extraction field, and the tunnel protocol judgment field is used to judge whether the tunnel protocol identification field of the Internet Protocol packet matches the tunnel protocol judgment field , the IP packet includes a public network IP header and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com