Access authentication method for wireless mesh network
A wireless mesh network and wireless mesh network technology, applied in wireless communication, user identity/authority verification, security devices, etc., can solve problems such as two-way authentication MKD logic conflicts, avoid link establishment failure, and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
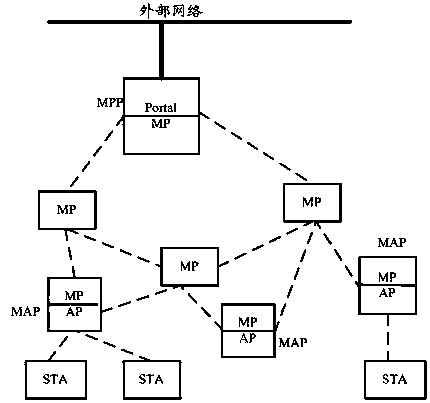
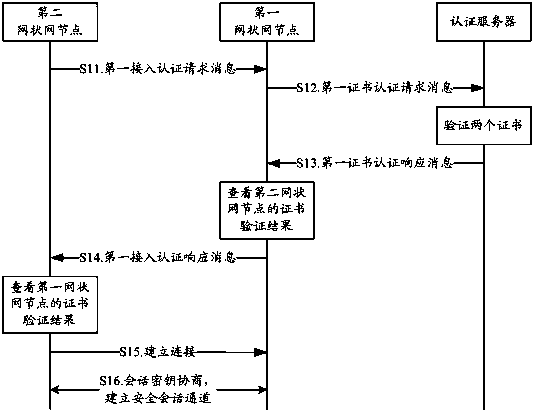
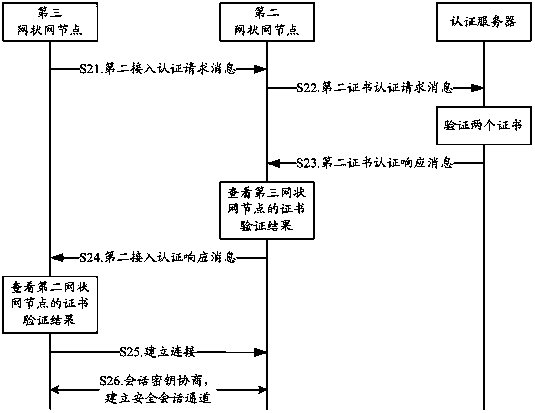
[0031] DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENTS, the second mesh network node detects the reception of the surrounding mesh network nodes by receiving beacon frames of the surrounding mesh network nodes, or the second mesh network node sends detection request frames. Signal Strength (Received Signal Strength, RSS) to discover the first mesh network node that has passed authentication, and use the first mesh network node as the authenticator to send a first access authentication request message to it.
[0032] S12: After receiving the first access authentication request message, the first mesh network node uses a private key to encrypt the certificate of the first mesh network node and the first access authentication request message together to generate a first certificate The authentication request message is sent to the authentication server;
[0033] S13. After receiving the first certificate authentication request message, the authentication server uses the public key o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com