Cloud security downloading method
A cloud security server, security technology, applied in the field of computer security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
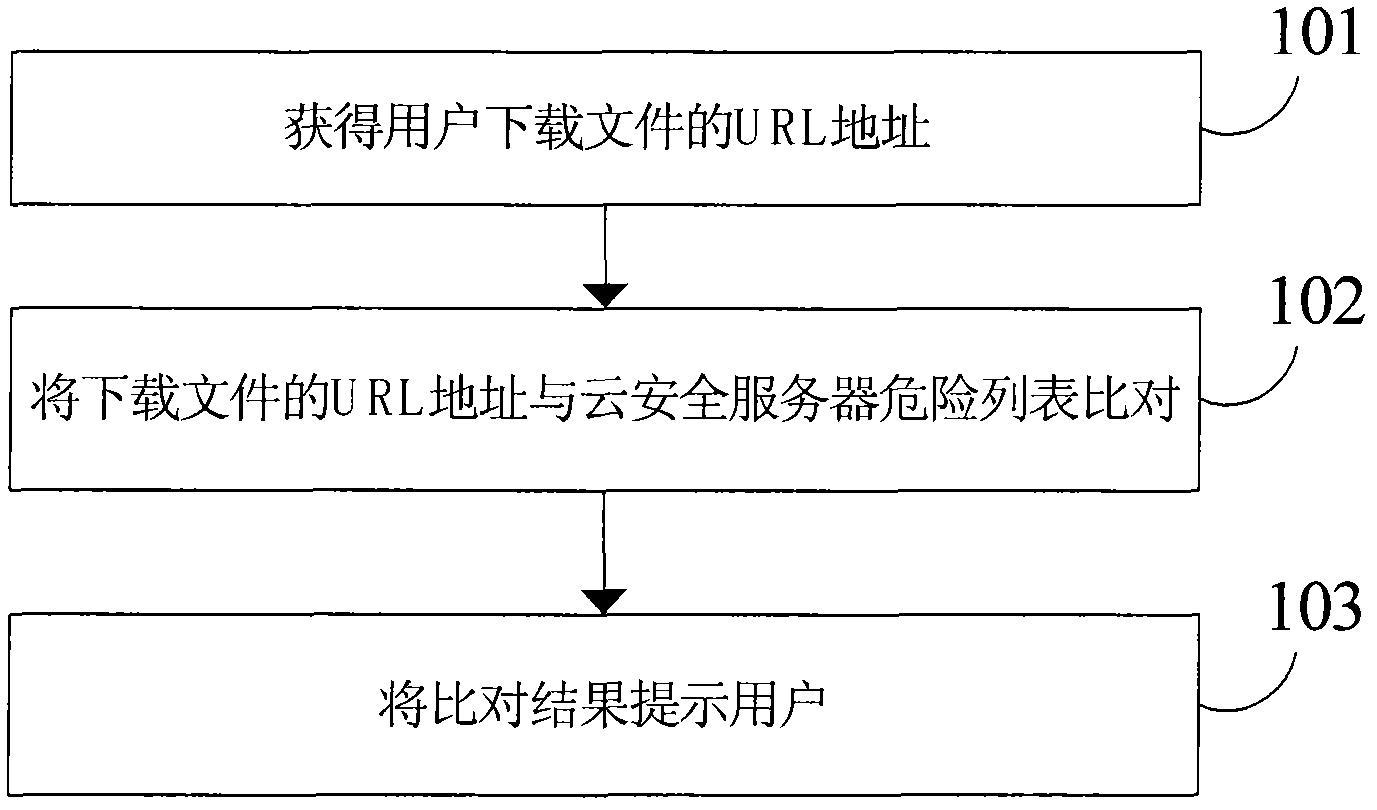
[0017] Since companies have different understandings of "cloud", the "cloud security" we finally see is still very different. Among them, foreign anti-virus software is mainly used to mark the processes in the user's computer through the server group on the Internet. Any files marked as trusted will no longer participate in the daily scanning, thus greatly improving the running speed of the daily scanning . And this design is similar to the "white list" we are familiar with.
[0018] In comparison with domestic anti-virus software, each user client will become a member of the "cloud security". They monitor the abnormal behavior of the software in the network and automatically send it to the server for analysis. After processing, distribute the virus or Trojan processing program to each client, so that any computer with anti-virus software can detect and kill the new virus in a short time.
[0019] However, in many cases, users may not have antivirus software with cloud function, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com