Working method of dynamic token
A technology of dynamic tokens and working methods, applied in the field of information security, can solve the problems of easy loss, cracking, and misappropriation of dynamic tokens, and achieve the effects of preventing misappropriation, preventing losses, and reducing the probability of successful group lifting.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0051] Example one
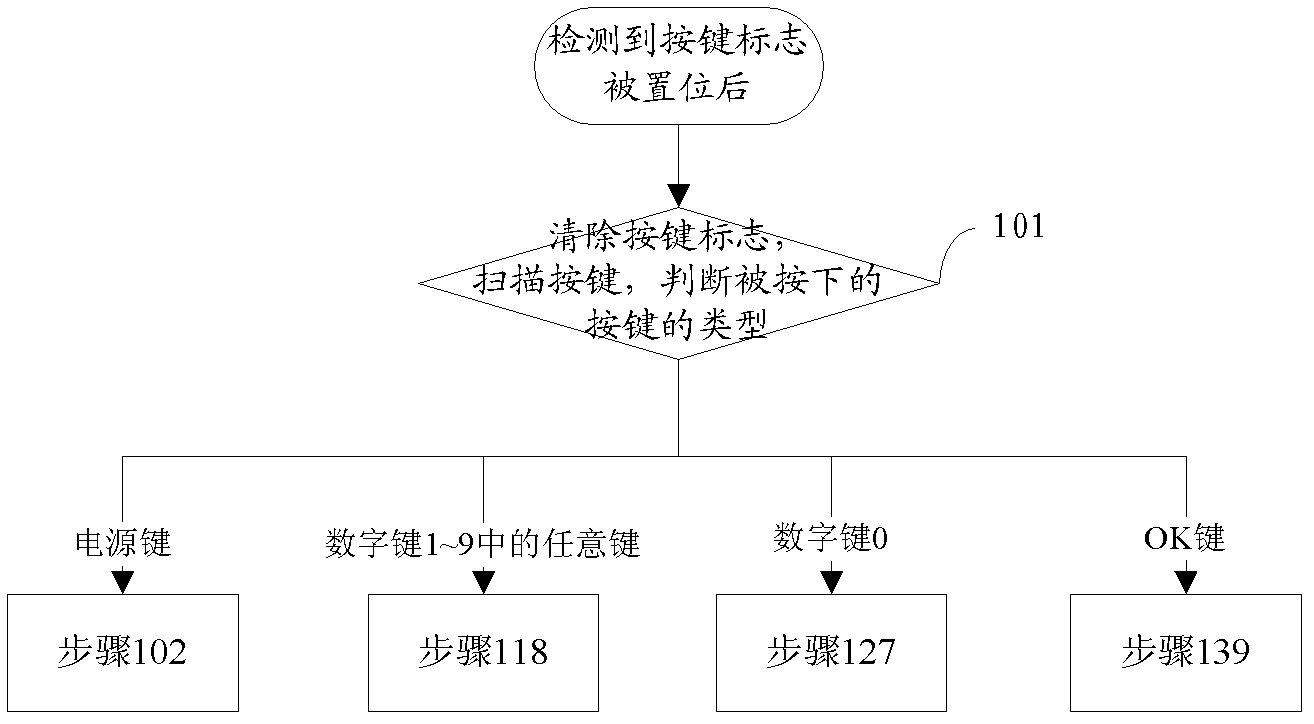
[0052] In order to effectively prevent the possibility of dynamic token being stolen, dynamic token loss, seed file loss, and group lifting, an embodiment of the present invention provides a dynamic token working method, wherein the dynamic token is usually Sleep state, wake up when a button is pressed, set the button flag, when the power button is continuously pressed for more than a preset time, or when there is no key input within a predetermined time, it will re-enter the dormant state, and the status indicator will be restored at the same time The default value, save the current available password retries and the current state of the lock flag.
[0053] When it is detected that the button flag is set and the dynamic token has not been initialized, the dynamic token detects whether the LCD screen and the keyboard are available according to the type of the pressed button;
[0054] When it is detected that the button flag is set and the dynamic token has been ...
Example Embodiment
[0094] Example two
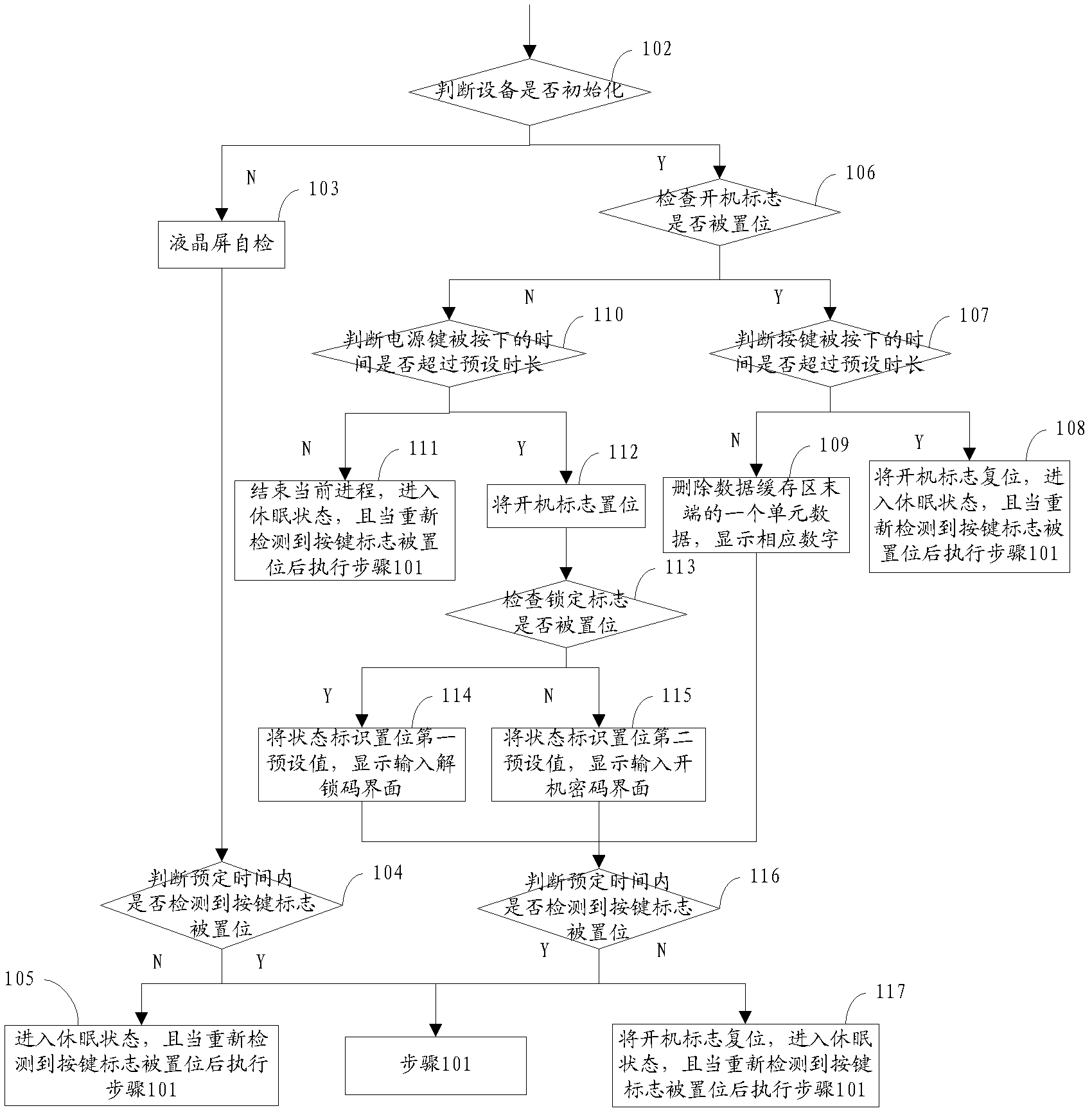
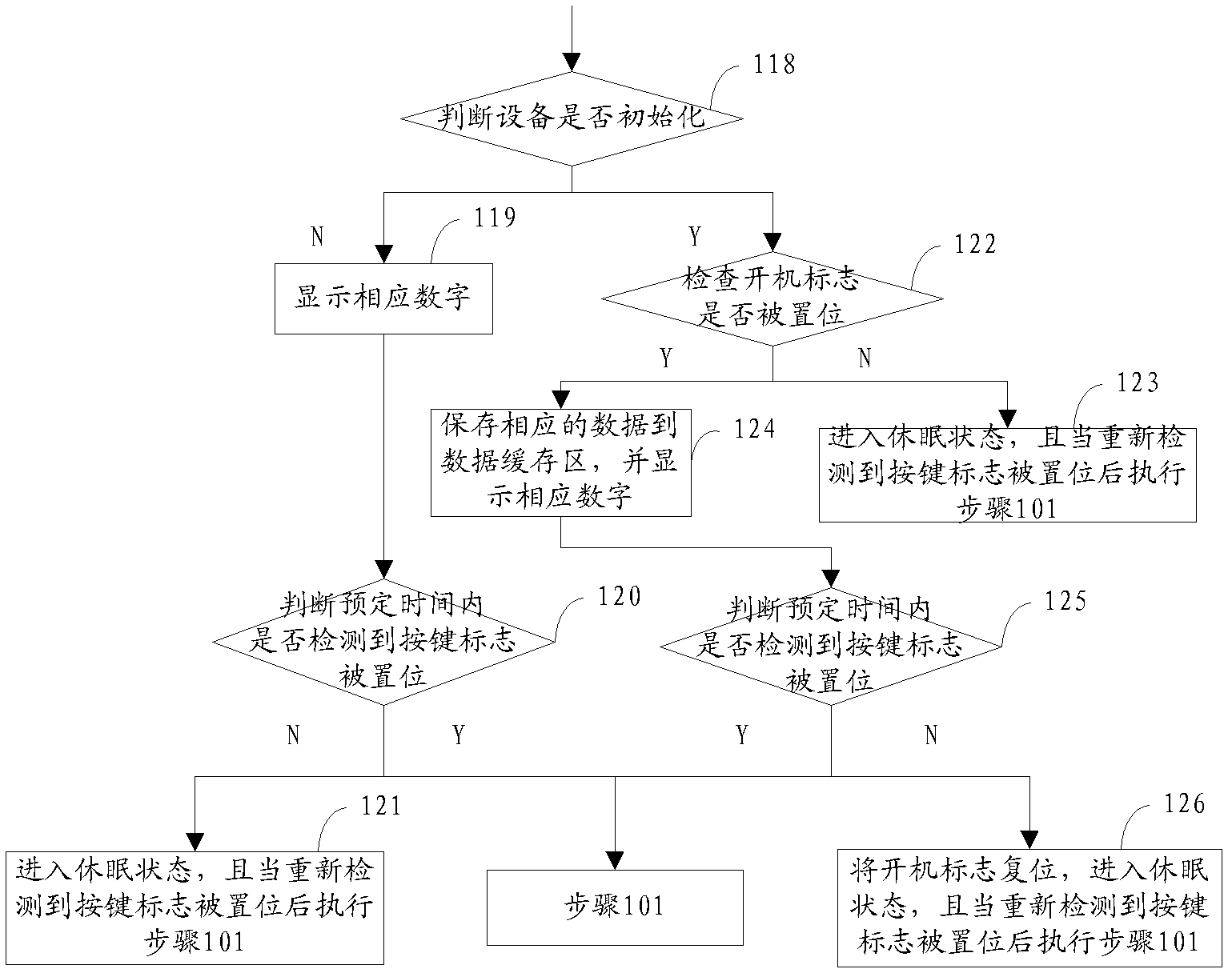
[0095] In order to effectively prevent the theft of dynamic tokens, loss of dynamic tokens, loss of seed files, and the possibility of group lifting, the embodiment of the present invention uses the power key and the delete key to share a key, and the number keys 1-9 are used as the first number key group. The number key 0 as an example of the second number key group provides a specific implementation method of the dynamic token provided in the first embodiment, wherein the dynamic token is usually in a sleep state, and when a button is pressed Wake up when down, and set the button flag. When the power button is continuously pressed for longer than the preset time, or there is no button input within the predetermined time, it will re-enter the dormant state. At the same time, the status indicator will be restored to the default value and the current available will be saved. The number of password retries and the current status of the lock flag. See figure 1 ...
Example Embodiment
[0179] Example three
[0180] In order to effectively prevent the possibility of dynamic token being stolen, dynamic token loss, seed file loss, and group lifting, the embodiment of the present invention provides another dynamic token working method, wherein the dynamic token is usually In the dormant state, wake up when a button is pressed, set the button flag, when the power button is continuously pressed for longer than the preset time, or when there is no key input within a predetermined time, it will re-enter the dormant state, and the state will be marked Restore to the default value, save the current available password retries and the current state of the lock flag.
[0181] When it is detected that the button flag is set and the dynamic token has not been initialized, the dynamic token detects whether the LCD screen and the keyboard are available according to the type of the pressed button;
[0182] When it is detected that the button flag is set and the dynamic token has be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com