Software protection method based on cloud server
A cloud server and software technology, applied in electrical components, transmission systems, etc., can solve the problems of high usage costs for software developers, and it is difficult for small applications to protect small applications, and achieve the effect of reducing costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
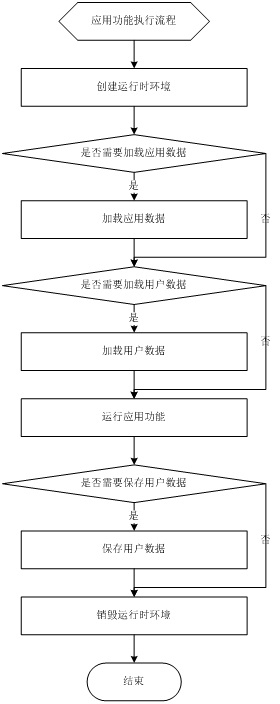
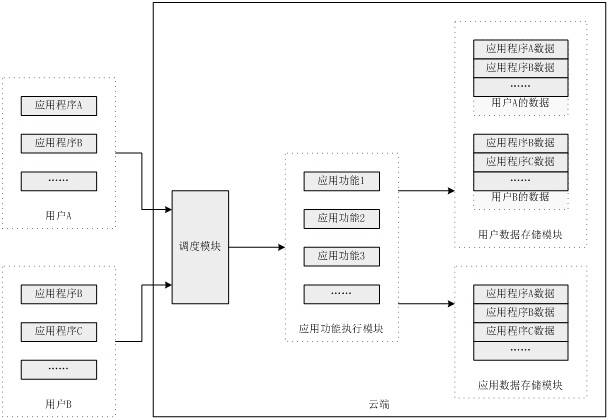
[0063] In this embodiment, the original dispatching module of the cloud server is divided into three modules, namely the cloud server portal module, the user identity authentication module and the dispatching module.
[0064] The cloud server portal module is used to provide a service interface to the application program. The service interface refers to the related method interface responsible for the interaction between the front-end device and the cloud server. Through the service interface, data can be requested from the cloud server according to the application program request. The cloud server returns the result to the service interface, and the service interface returns data to the client.
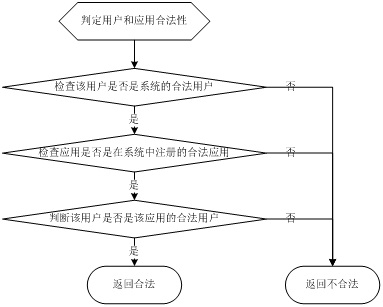
[0065] The user identity authentication service module is used to authenticate the identity of the user. According to a specific embodiment of the present invention, multiple authentication methods are used for authentication, such as signature, certificate, and so on.
[0066] The ...
Embodiment 2
[0076] Assuming that the application in this embodiment is a GPS navigation application (hereinafter collectively referred to as GPS), according to an embodiment of the present invention, the functions of Bluetooth, rear view, driving record, and monitoring and security in GPS have been placed on the cloud server.
[0077] In this embodiment, some of the above functions are uploaded to the cloud server. The application information will be saved on the cloud server, assuming it is saved in the table APPInfo.
[0078] The cloud server will save the system user information for the identity authentication module to verify whether it is a legitimate user, assuming that the information is stored in the table UserInfo.
[0079] Users who download and use applications through payment or other forms and the corresponding application information will also be stored in the cloud server, assuming that they are stored in the table User-APP.
[0080] When user A sends a call request to the...
Embodiment 3
[0085] According to one embodiment of the present invention, the application program is a PDF application program P, which can create, display, edit, mark, and print documents in PDF format on the mobile device. It is assumed that the editing and marking functions in the PDF program have been stored in In the cloud server, it is assumed that this PDF program needs to be downloaded and used for a fee, so users who pay to download this application are legal users of this PDF application.
[0086] An application such as PDF that uploads some functions on the cloud server will be marked as a legitimate application on the cloud server, and the cloud server will determine whether the application and the user are legal through files or database tables or other identifiers. According to a specific implementation of the present invention, it is assumed that the cloud server in this example stores corresponding legal application information, legal application-user correspondence informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com