Mobile terminal privacy protection method and device
A privacy protection and mobile terminal technology, applied in the field of information identification, can solve the problems that identification methods cannot classify private content, etc., and achieve the effect of flexible access and flexible private content
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
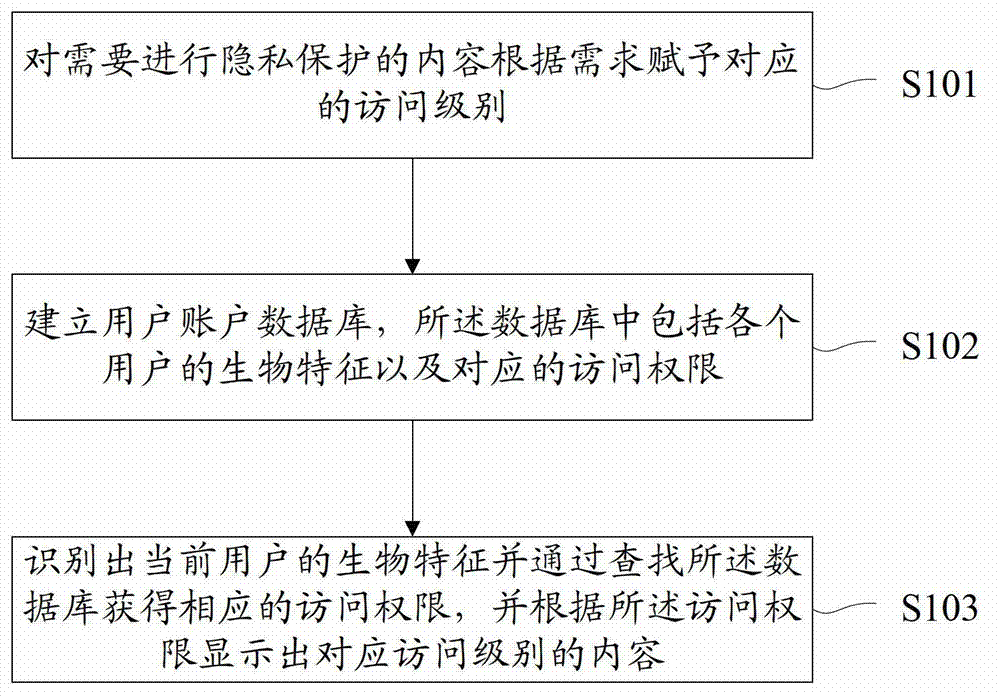
[0020] figure 1 The flow of the mobile terminal privacy protection method provided by the first embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0021] The mobile terminal privacy protection method provided in this embodiment includes the following steps:
[0022] Step S101, assigning corresponding access levels to the content requiring privacy protection according to requirements.
[0023] In real life, there are situations where different users can see the corresponding privacy protection content, such as the problem of family photos mentioned in the background technology above, users and their family members can see their own family photos, but the family members cannot see the user’s private photos. In order to achieve this purpose, in this step, it is necessary to assign a corresponding access level to each content that needs privacy protection, so that users wi...
Embodiment 2
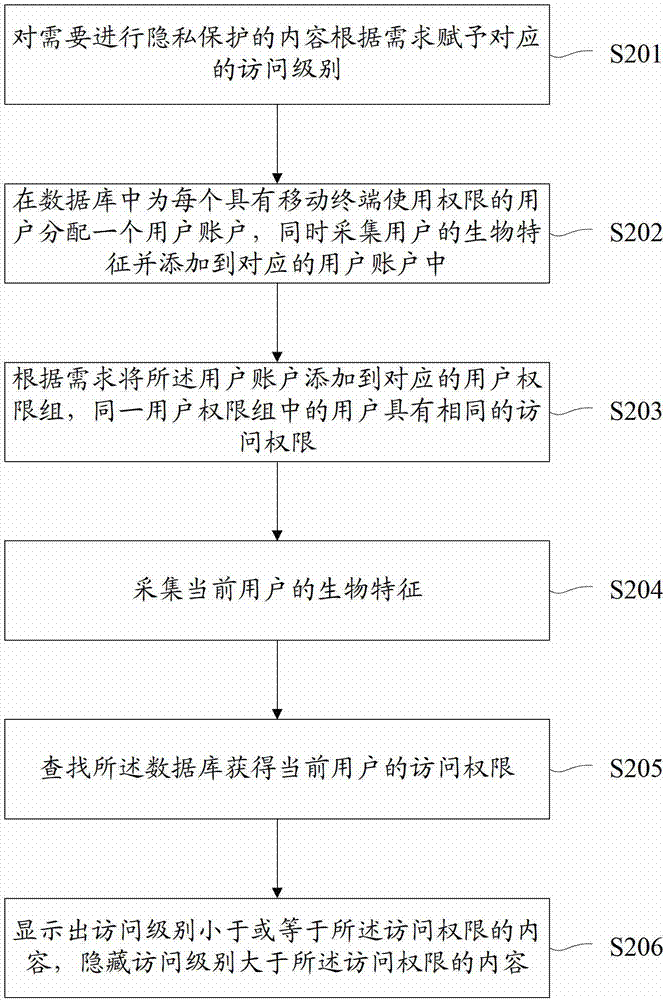
[0030] figure 2 The flow of the mobile terminal privacy protection method provided by the second embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0031] The mobile terminal privacy protection method provided in this embodiment includes the following steps:
[0032] Step S201, assigning corresponding access levels to the content requiring privacy protection according to requirements.
[0033] This step is the same as step S101 in the first embodiment, and will not be repeated here.
[0034] Step S202, assigning a user account in the database to each user with the right to use the mobile terminal, and at the same time collect the user's biometric features and add them to the corresponding user account.
[0035] In the embodiment of the present invention, after setting the access level of the access content, it is necessary to establish a user account database, and es...
Embodiment 3
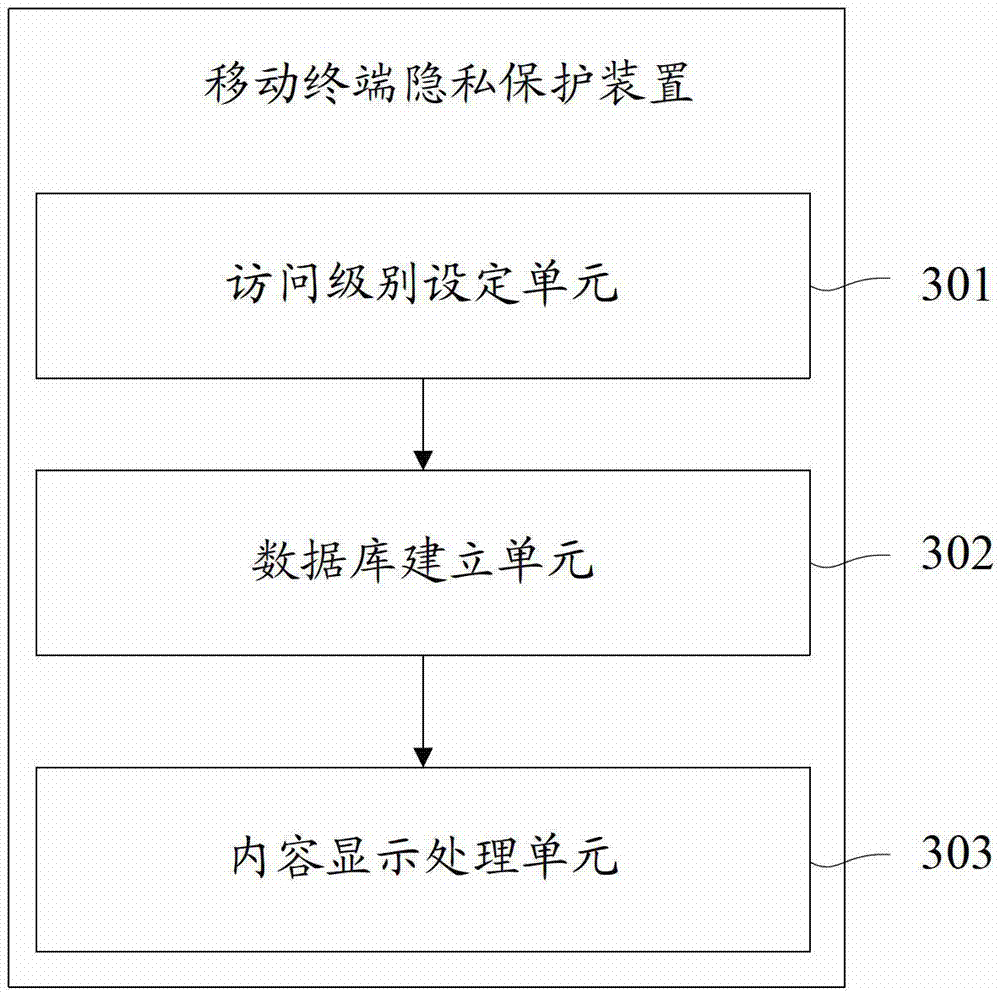
[0046] image 3 The structure of the mobile terminal privacy protection device provided by the third embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0047] The mobile terminal privacy protection device provided in this embodiment includes:
[0048] An access level setting unit 301, configured to assign a corresponding access level to the content requiring privacy protection according to requirements;
[0049] A database establishment unit 302, configured to establish a user account database, which includes biometric features of each user and corresponding access rights;
[0050] The content display processing unit 303 is configured to identify the biometric feature of the current user and obtain corresponding access rights by searching the database, and display content corresponding to the access level according to the access rights.
[0051] Each functional unit 3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com