Network attack and defense test resource deployment method based on mobile agent
A mobile agent and resource technology, applied in the field of network attack and defense test resource deployment, can solve the problems of not supporting dynamic adjustment, lack of overall view of network attack and defense test resource deployment, easy deployment errors, etc., and achieve the effect of good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0077] An embodiment of the present invention is illustrated below:
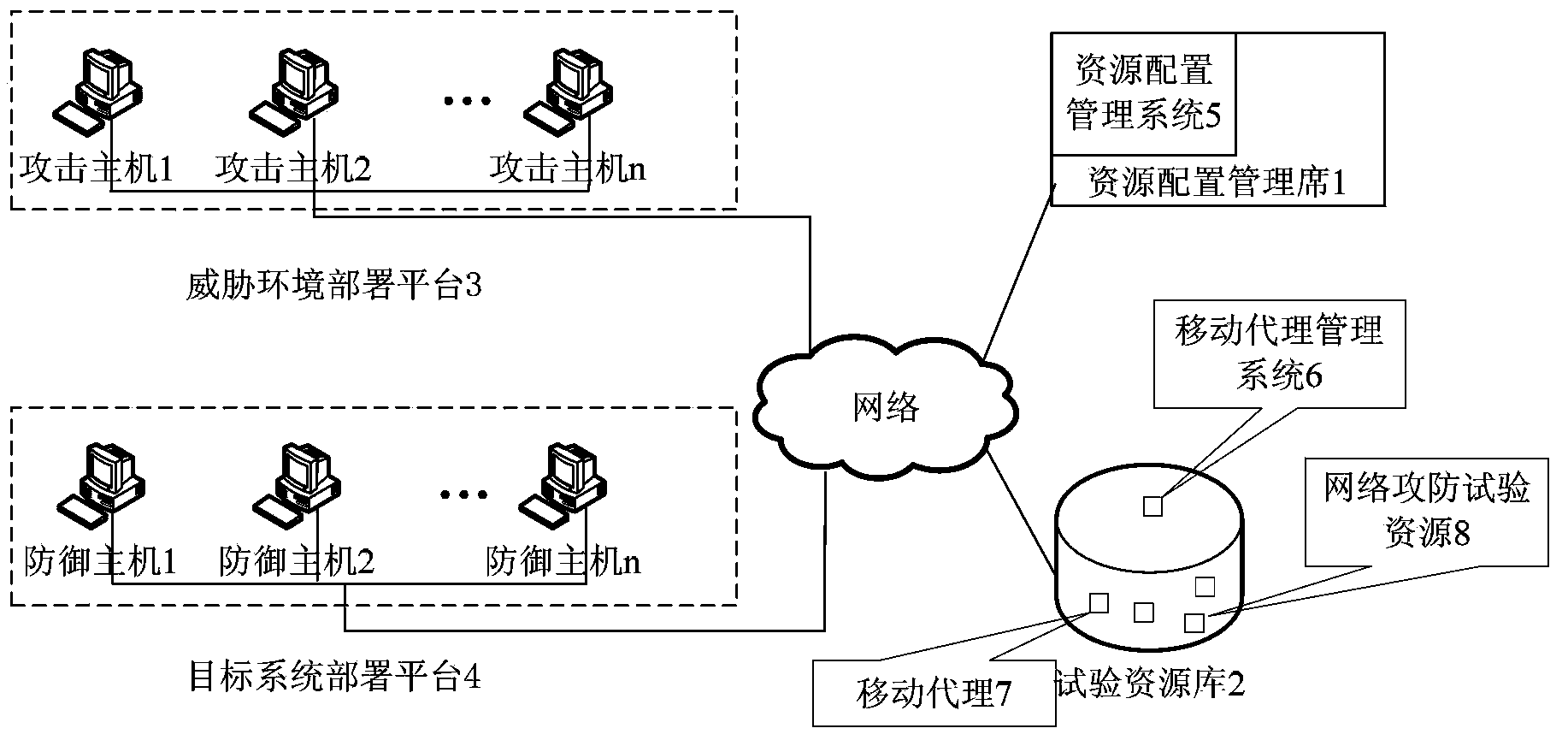
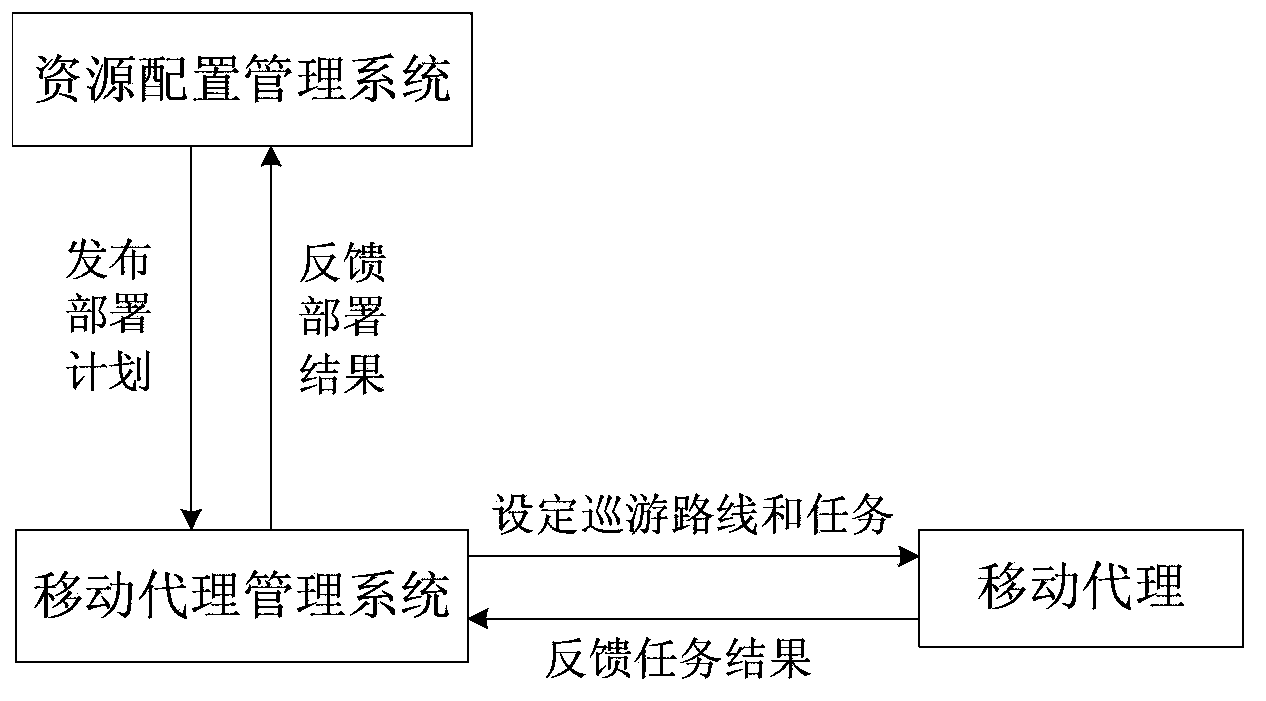
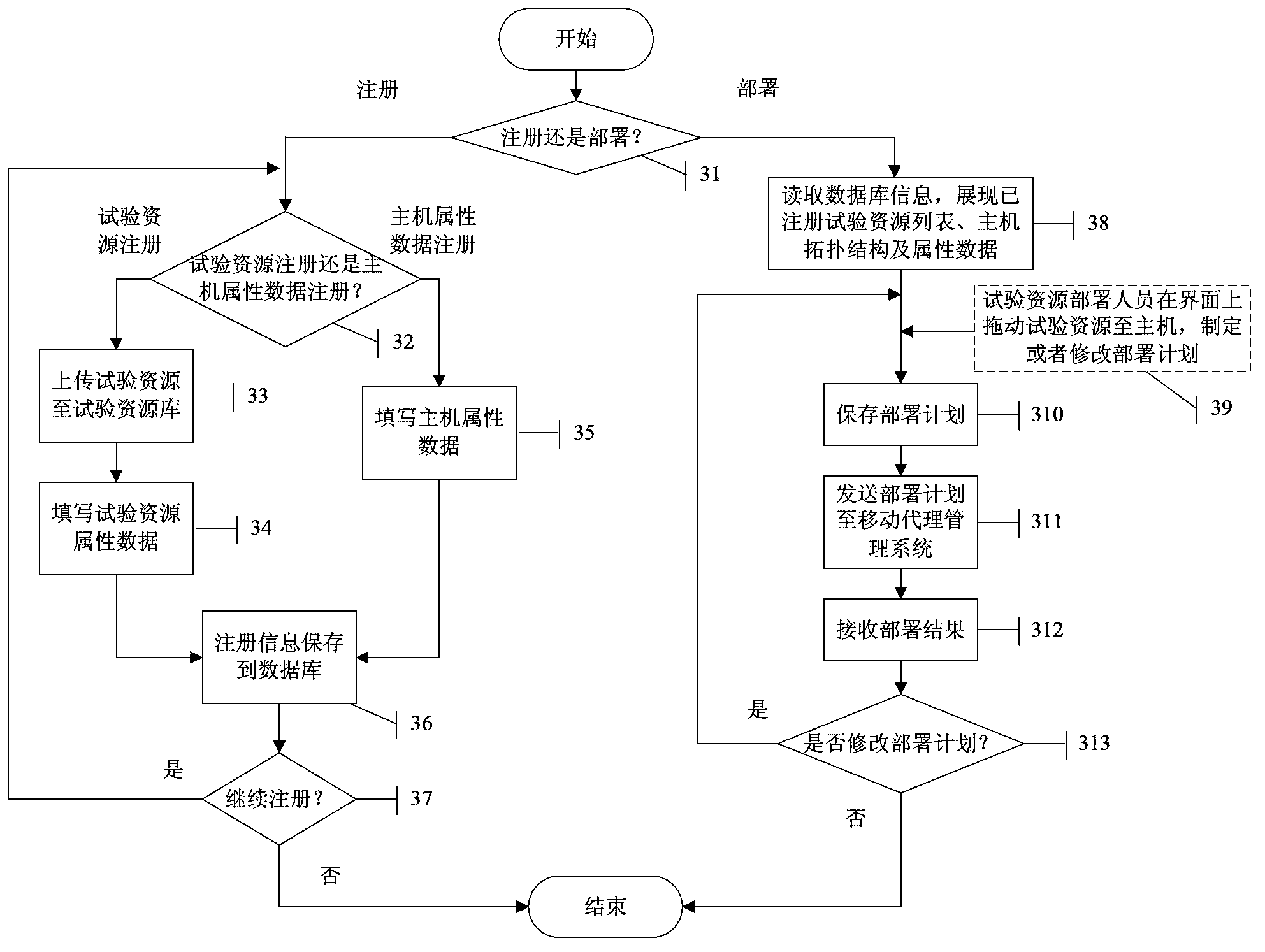
[0078] The resource configuration management seat, the test resource library, the threat environment deployment platform and the target system deployment platform are interconnected through routers in the local area network 192.168.8.0 / 22. The IP address of the resource configuration management seat is 192.168.8.2, the computer model is Lenovo ThinkCentre M8250t, and the operating system winXP sp3, the resource configuration management system has been deployed; the IP address of the test resource library is 192.168.9.2, the computer model is Lenovo ThinkCentre M8250t, the operating system is winXP sp3, the mobile agent management system and mobile agent have been deployed; the network segment of the threat environment deployment platform is 192.168.10.0 / 24, 10 attacking hosts, IP address 192.168.10.2-192.168.10.11, computer model Lenovo ThinkCentre M8250t, operating system winXP sp3; target system deployment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com