Security card management method and system
A technology of security system and management method, applied in the field of security card management method and system, can solve the problems that the system can no longer meet new requirements, operation and maintenance, management control and expansion difficulties, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
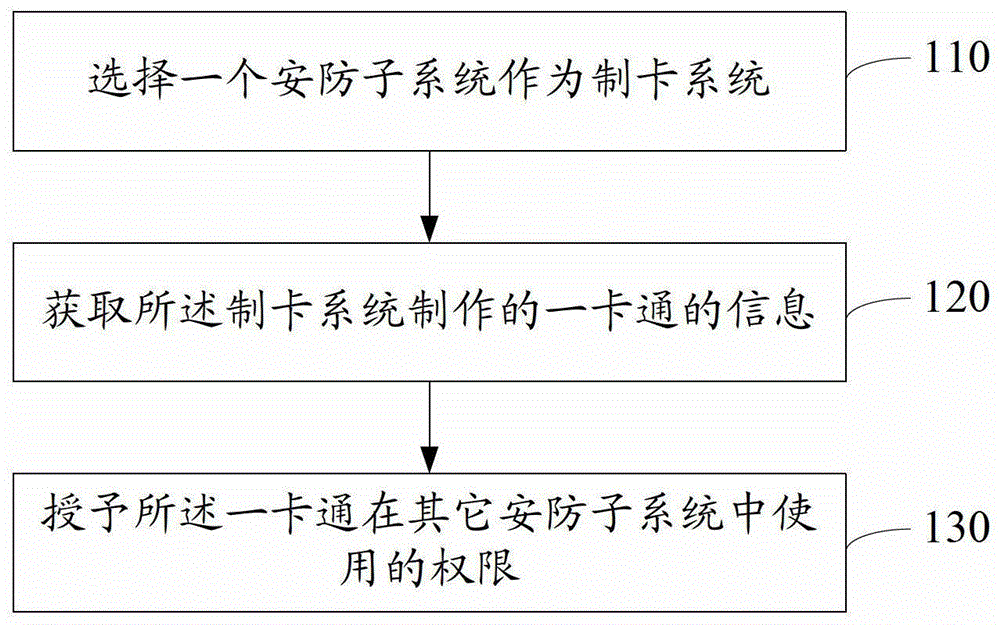
[0015] Please refer to figure 1 , the embodiment of the present invention provides a security card management method, including:
[0016] 110. Select a security subsystem as the card making system.
[0017] The security subsystems of different vendors installed in the enterprise are managed centrally and uniformly, and the management platform can be called the security system integration platform. In this embodiment, one of the security subsystems can be selected as the card making system through the security system integration platform, and the security card made by the subsystem can be an IC card (Integrated Circuit Card, integrated circuit card), ID card (Identification Card, identity identification card) or CPU (Central Processing Unit, central processing unit) card. The security card will be commonly used among various security subsystems in the future, so it will be referred to as an all-in-one card in the following.
[0018] 120. Obtain the information of the all-in-...
Embodiment 2
[0032] Please refer to Figure 4 , the embodiment of the present invention also provides a security card management system, including:
[0033] A selection module 410, configured to select a security subsystem as a card making system;
[0034] An acquisition module 420, configured to acquire the information of the all-in-one card produced by the card production system;
[0035] Authorization module 430, configured to authorize the said one-card to be used in other security subsystems.
[0036] Further, the authorization module 430 may include:
[0037] The first authorization unit 4301 located on the security system integration platform is used to perform first-level authorization, to grant the one-card permission to be used in other security subsystems, and to send the one-card information to other subsystems;
[0038] The second authorization unit 4302 located on other security subsystems is used for secondary authorization, granting the one-card permission to use the equ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com