Method and apparatus for authenticating multicast messages
A message and multicast technology, used in digital data authentication, user identity/authority verification, information technology support systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
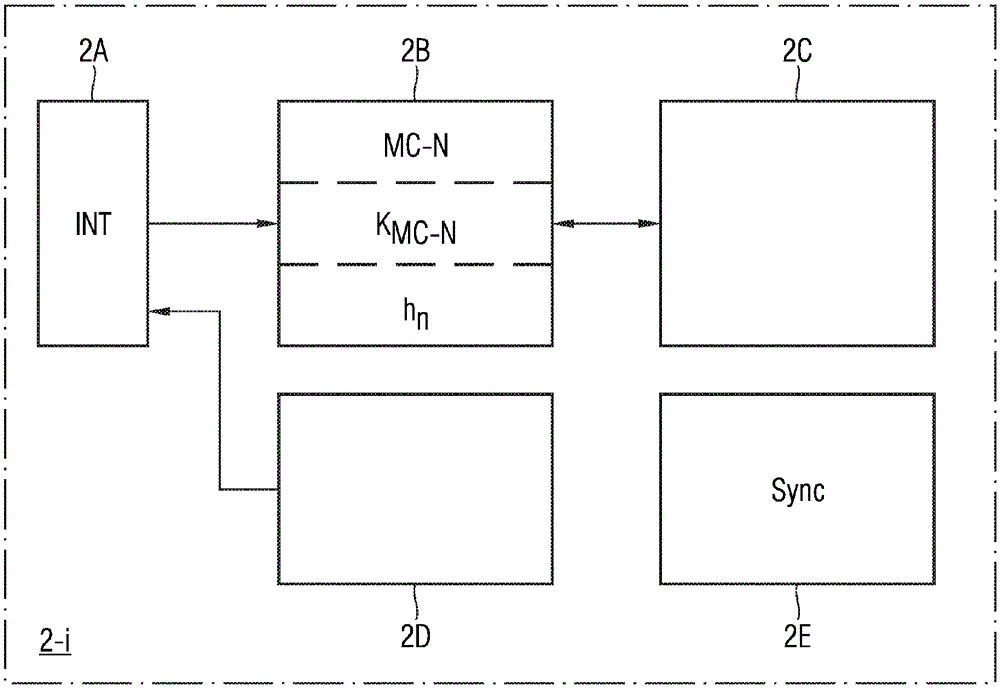
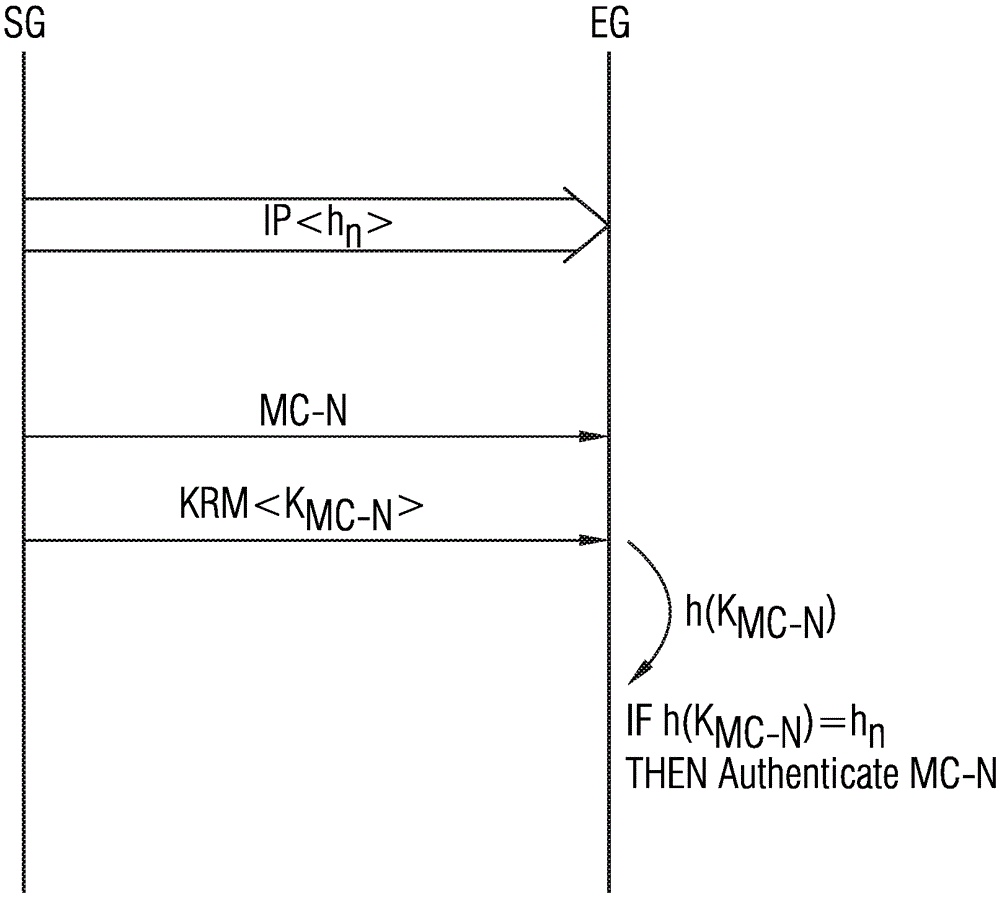
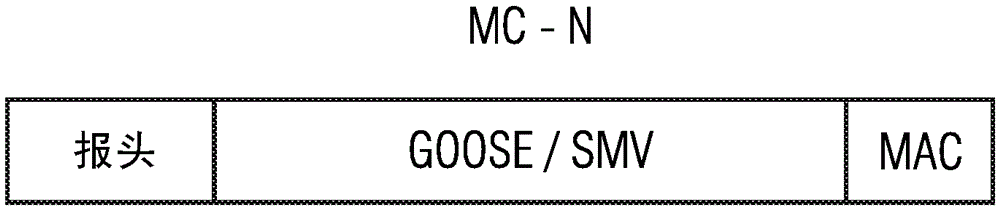
[0050] As can be seen from FIG. 1, the authentication method for authenticating multicast messages according to the invention can be used, for example, in a peer-to-peer system 1 with a plurality of field devices 2-1, 2- 2, 2-3, ..., 2-m. The field devices 2-i can communicate with each other via wireless or wired message connections by exchanging messages with each other. The field device 2-i can be a permanently installed field device, but also a mobile field device. Field device 2-i can send messages as a sending device and can receive messages as a receiving device. If an event is recognized by a field device (e.g. field device 2-i shown in Fig. 1), field device 2-i can act as a sending device to send the multicast message MC-N to the remaining field devices of point-to-point system 1 , as shown in Figure 1. Field devices 2-i can be, for example, measuring devices, monitoring devices or other control devices.
[0051] FIG. 2 shows a block diagram of a possible embodimen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com