Method and apparatus for authenticating multicast messages
A message and multicast technology, applied in digital data authentication, user identity/authority verification, information technology support system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
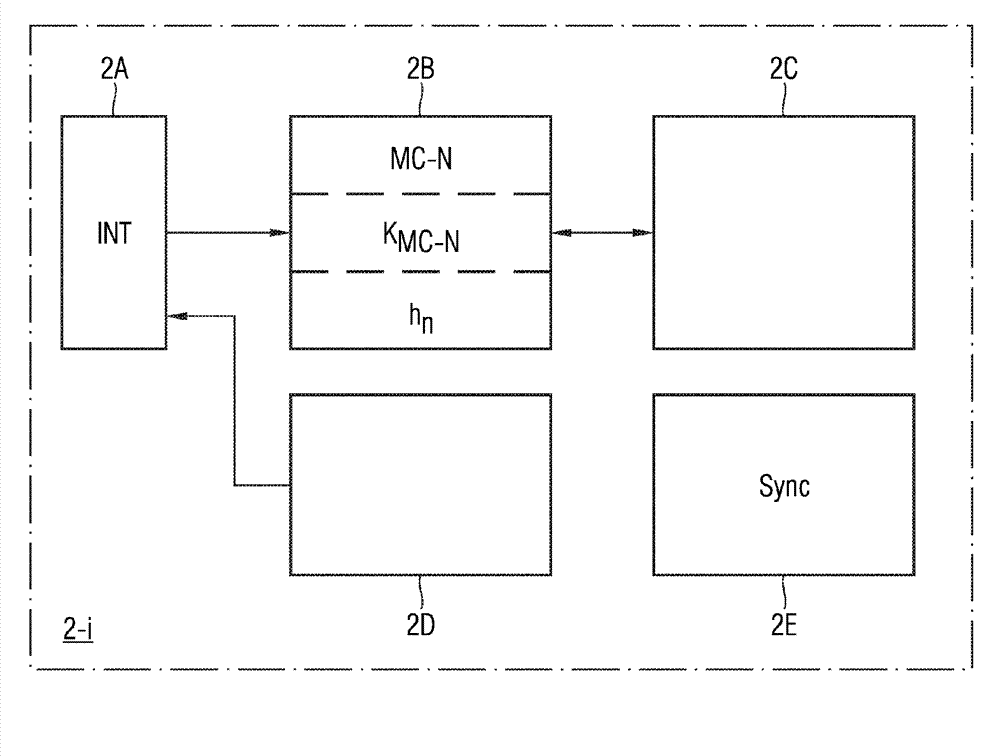
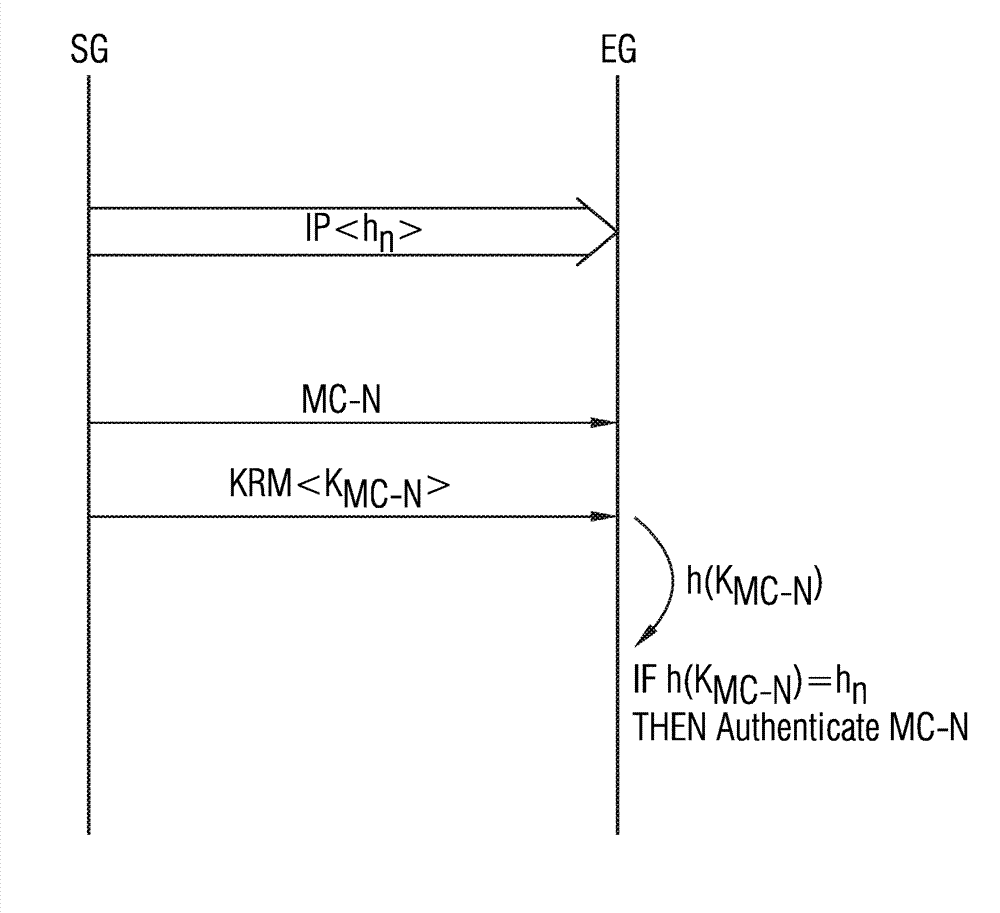
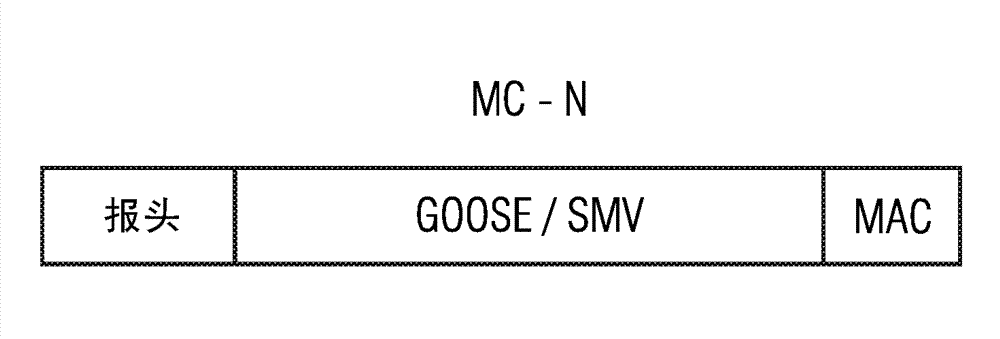
[0050] as from figure 1 As can be seen in , the authentication method for authenticating multicast messages according to the invention can be used, for example, in a peer-to-peer system 1 with a plurality of field devices 2-1, 2-2, 2- 3, ..., 2-m. The field devices 2 - i can communicate with each other via wireless or wired message connections by exchanging messages with each other. The field devices 2-i can be permanently installed field devices, but also mobile field devices. The field device 2-i can send messages as a sending device and can receive messages as a receiving device. If passed through a field device (such as figure 1 The field device 2-i) shown in the event recognizes the event, then the field device 2-i can act as a sending device and send the multicast message MC-N to the remaining field devices of the point-to-point system 1, as in figure 1 shown in . Field devices 2 - i can be, for example, measuring devices, monitoring devices or other control ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com