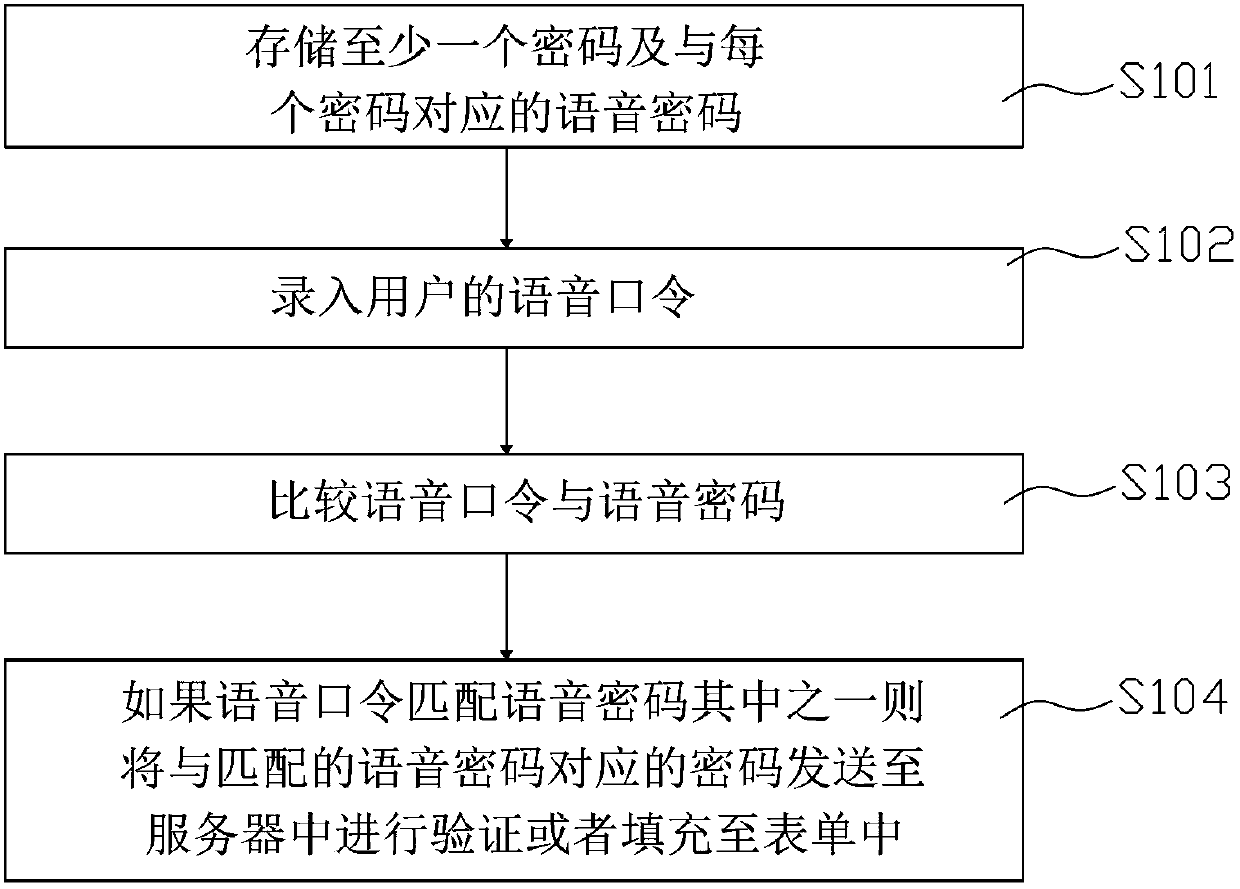
User authentication method, user authentication device and intelligent terminal
A user authentication and user technology, applied in the direction of user identity/authority verification, digital data authentication, etc., can solve problems such as forgetting passwords, time-consuming and laborious, troublesome password input, etc., to achieve obvious improvement, obvious user experience, and avoid multiple repeated input The effect of the password
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
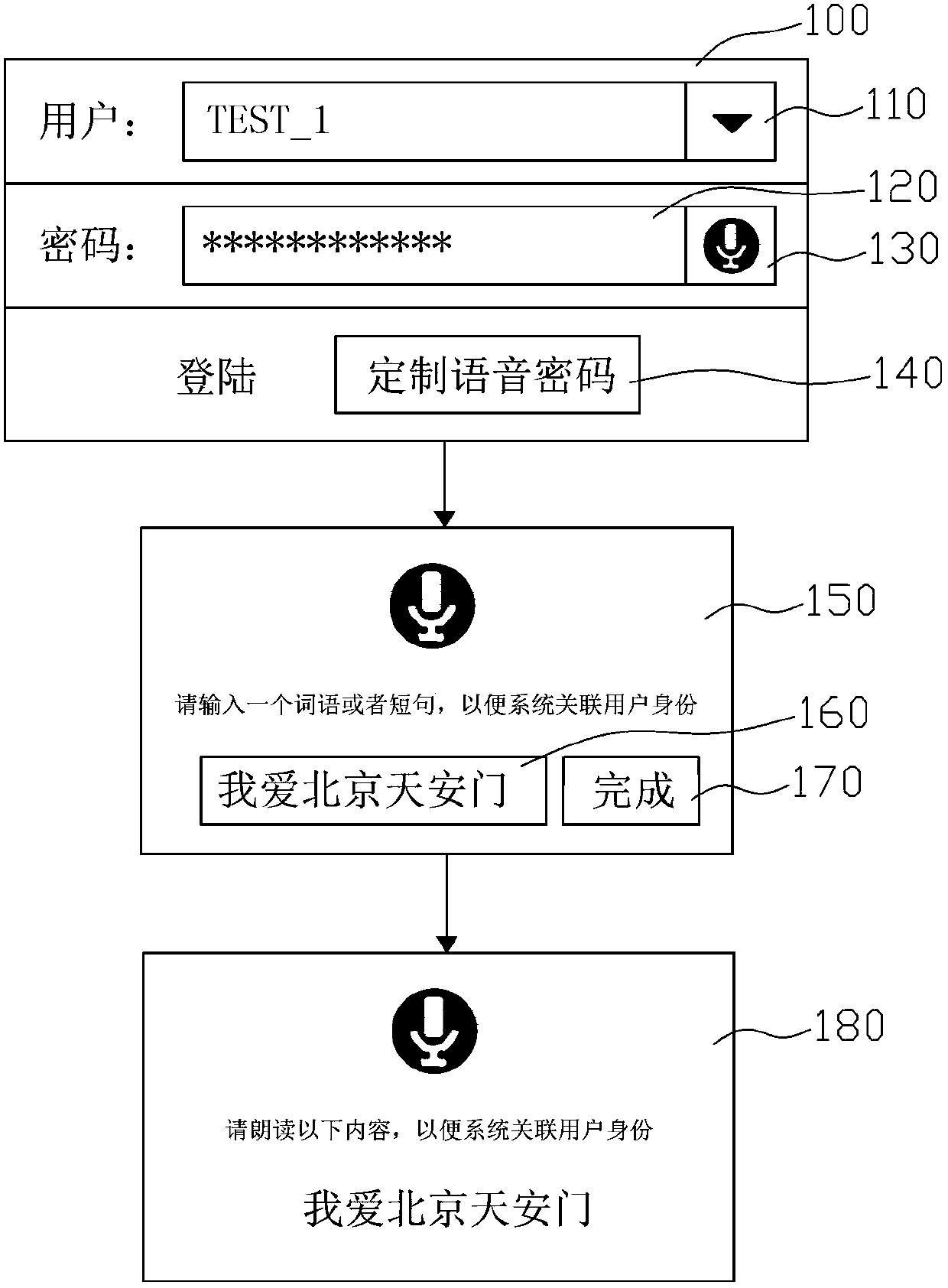
[0037] figure 2 It is a schematic diagram of the user login interface 100 displayed in the user authentication method of the first embodiment. Such as figure 2 As shown, the login interface 100 includes a drop-down list 110 , a text input box 120 , a button 130 , and a button 140 .
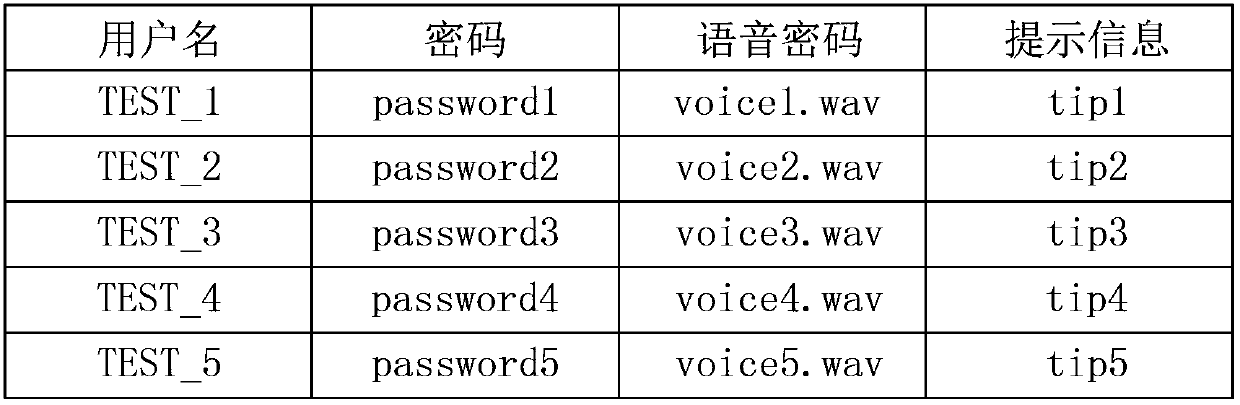
[0038] The drop-down list 110 is used to allow the user to select a user name, and the user names in the list are obtained according to historical records. That is to say, the user authentication method in this embodiment also stores the user name. image 3 Shown is a schematic diagram of user names, passwords, voice passwords, etc. stored in this embodiment. Depend on image 3 User data as shown, correspondingly, as in Figure 4 As shown, when the drop-down list 110 is expanded, there are 5 usernames TEST_1 to TEST_5 in the list.
[0039] The text input box 120 is used to allow the user to input a text password, and the button 130 is used to allow the user to start the speech password rec...
no. 2 example
[0046] In this example, if Image 6 As shown, when performing user authentication, the user does not need to select a user name or enter a text password in the text input box. After the user clicks the button 130, the process is generally similar to that of the first embodiment, but the process of comparing the voice password read out by the user with the voice password is slightly different. In this embodiment, since the user name and password are not selected, the voice password cannot be associated with the user name, and the voice password and the voice password need to be compared one by one. After the voice password is successfully matched, the user name and password are determined according to the voice password in turn. At this time, the user name and password can be filled in the drop-down list 110 and the text input box 120 respectively, and the user can click the login button to complete user authentication. In addition, the user name and password may be directly s...
no. 3 example
[0049] In this example, if Figure 7 As shown, there is no one-to-one correspondence between user names and passwords. Generally speaking, the number of passwords will be greater than the number of users, that is, a user name may have multiple passwords.
[0050] Thus, when performing user authentication, such as Figure 4 As shown, the user can select a user name in the drop-down list 110 or input the user name by himself, and then when the user presses the button 130 ( figure 2 ) pops up as Figure 8 The interface shown here prompts the user to read the voice password aloud. The voice password can be determined by the user according to the actual situation. After the voice password is recorded, the system combines the voice password with Figure 7 The voice passwords shown are compared one by one, and then the password is determined according to the matching voice password and the password can be filled into the text input box 120, or the password and the user name are se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com