Space link protocol blind identification method and system
A link protocol and blind recognition technology, applied in the transmission system, digital transmission system, electrical components, etc., can solve the problems of increasing space and time overhead, low mining efficiency, mining processor overflow, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
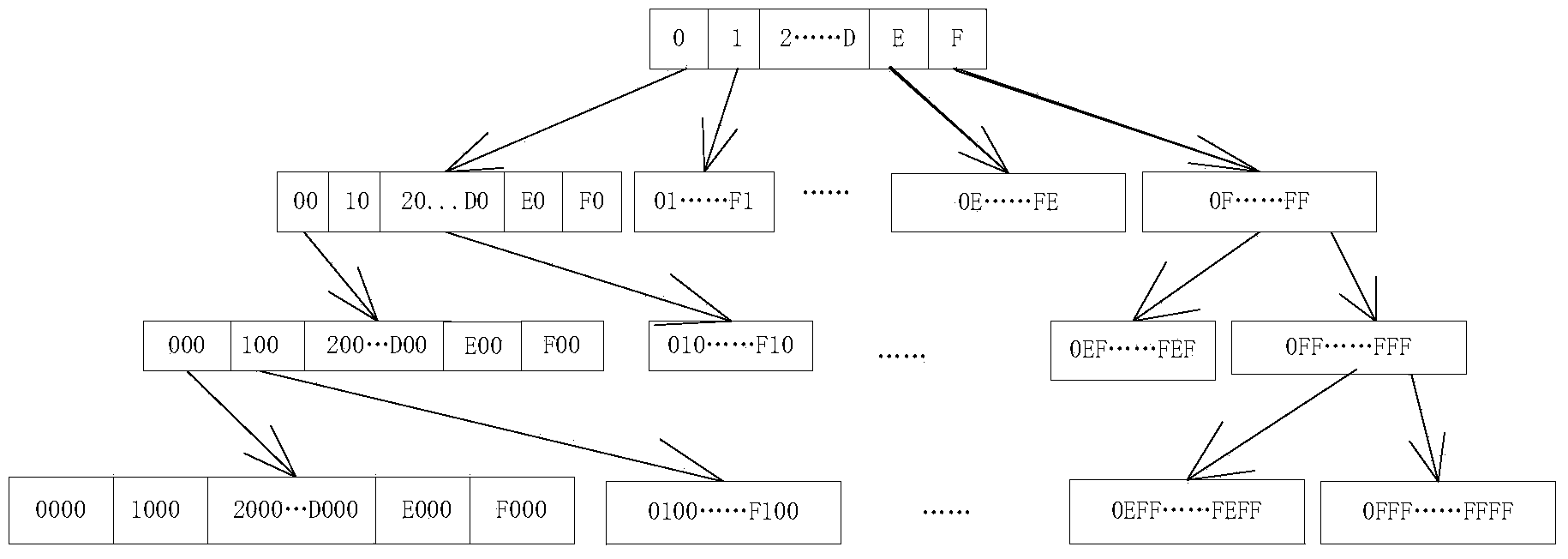
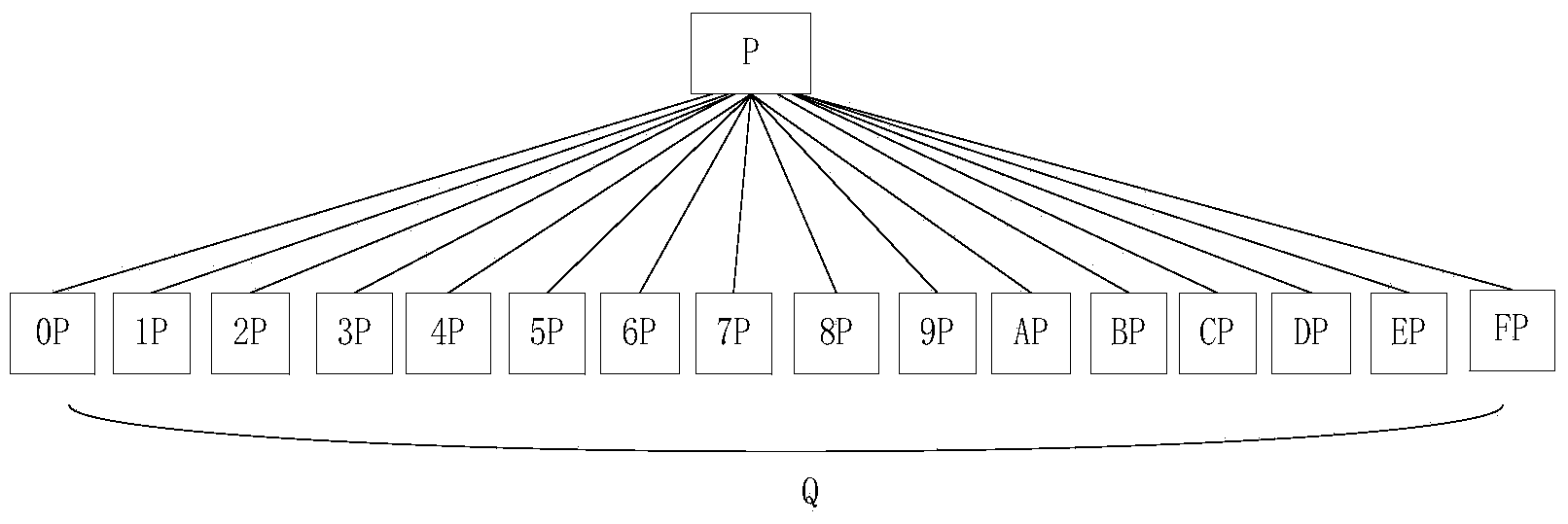
[0073] Among the identification objects targeted by this method, binary bit stream data (or other data that can be converted into binary) is converted into hexadecimal, called target data. The hexadecimal data element contains sixteen numbers from 0 to F, so the pattern sequence P with a length of k is combined with a hexadecimal number to form sixteen subsequences Q with a length of "k+1". They are OP, 1P, 2P, 3P, 4P, 5P, 6P, 7P, 8P, 9P, AP, BP, CP, DP, EP, FP, and the relationship between the subsequence Q and the pattern sequence P of length k is as follows: Figure 1-b As shown, enumerating all sequences with a length of 1 to k in the target data can form a complete hexadecimal tree linked by parent-child relationship. Figure 1-a is a complete hexadecimal state diagram, Figure 1-b is one of the states.
[0074] If you want to mine the counting of frequent sequences within the length of k bits in the target data, you need to create k buffs, and then read the characters i...
Embodiment
[0113] Assume that the target data is a set of binary data with a data size of 12Kbyte, frame synchronization codeword: 1ACFFCID (unknown), frame length: 256 byte (unknown).
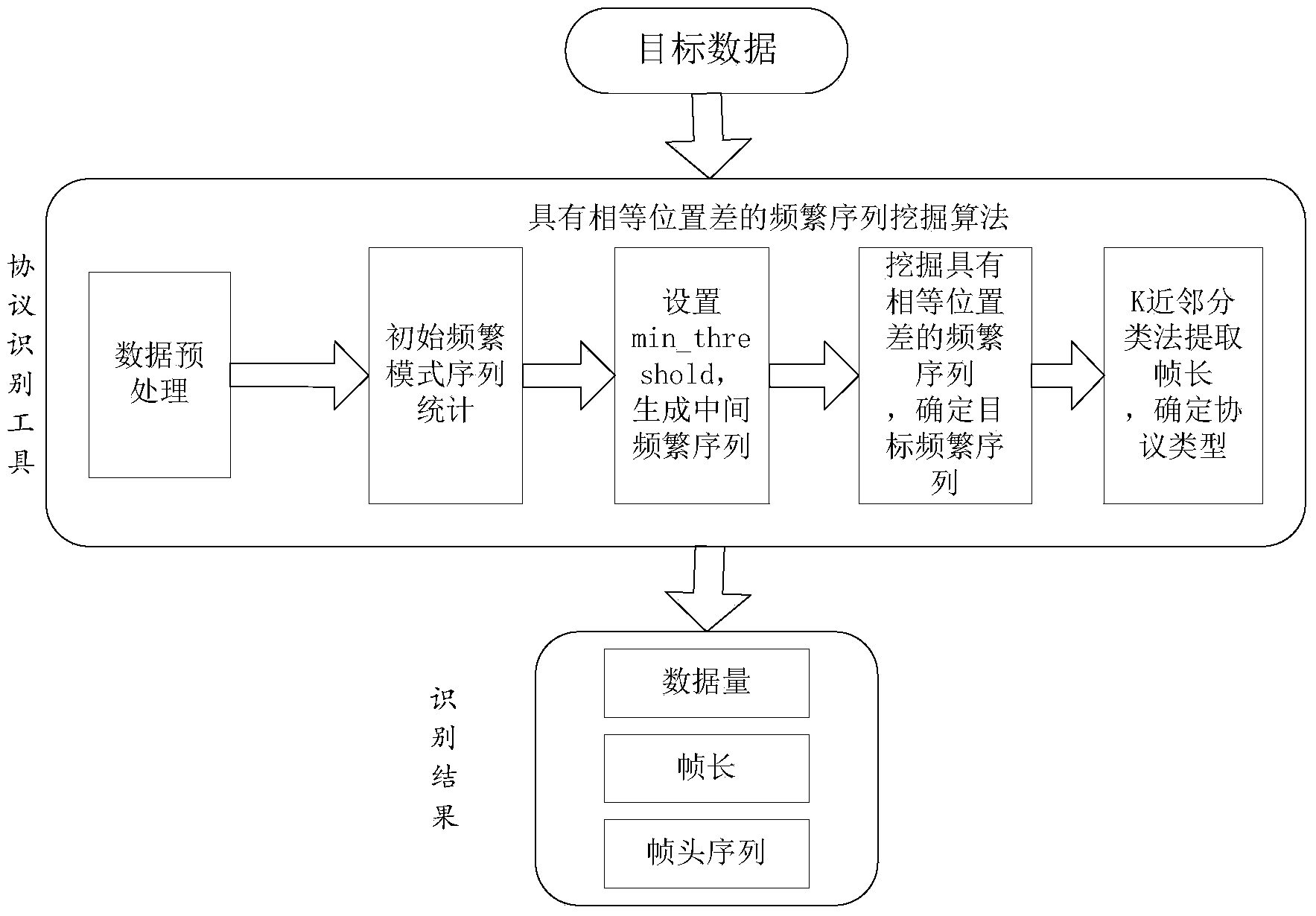
[0114] Concrete implementation steps after adopting the scheme of the present invention are:
[0115] 1) Read the binary bit stream data file ccsds_data.raw stored in the hard disk of the computer in advance.
[0116] 2) Perform data preprocessing, convert binary data into hexadecimal data, and generate target data ccsds_data.hex.
[0117] 3) Set the length of the pattern sequence to 4 bits (empirical value), call the method of the complete hexadecimal tree of the finite state machine, perform initial frequent sequence statistics on the target data ccsds_data.hex, and generate the initial frequent sequence set:
[0118]{1ACF,ACFF,C1D4,0066,C025,AB95,3FE2,72C3,6012,B01A,2228,2222,B952,10C8,01AA,AAAA,A10C,021C,FC1D,FFC1,03FE,1020,2030,3040,4050 ,5060,6070,7080,8090,90A0,A0B0,B0C0,C0D0,D0E0,E0F0},
[011...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com