Method and device for identifying malicious website
A malicious website and identification method technology, applied in the direction of platform integrity maintenance, etc., can solve the problem that malicious websites cannot be identified and processed, and achieve the effect of improving identification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0098] This embodiment is a specific application scenario of the present invention. Through this embodiment, the method provided by the present invention can be described more clearly and specifically.
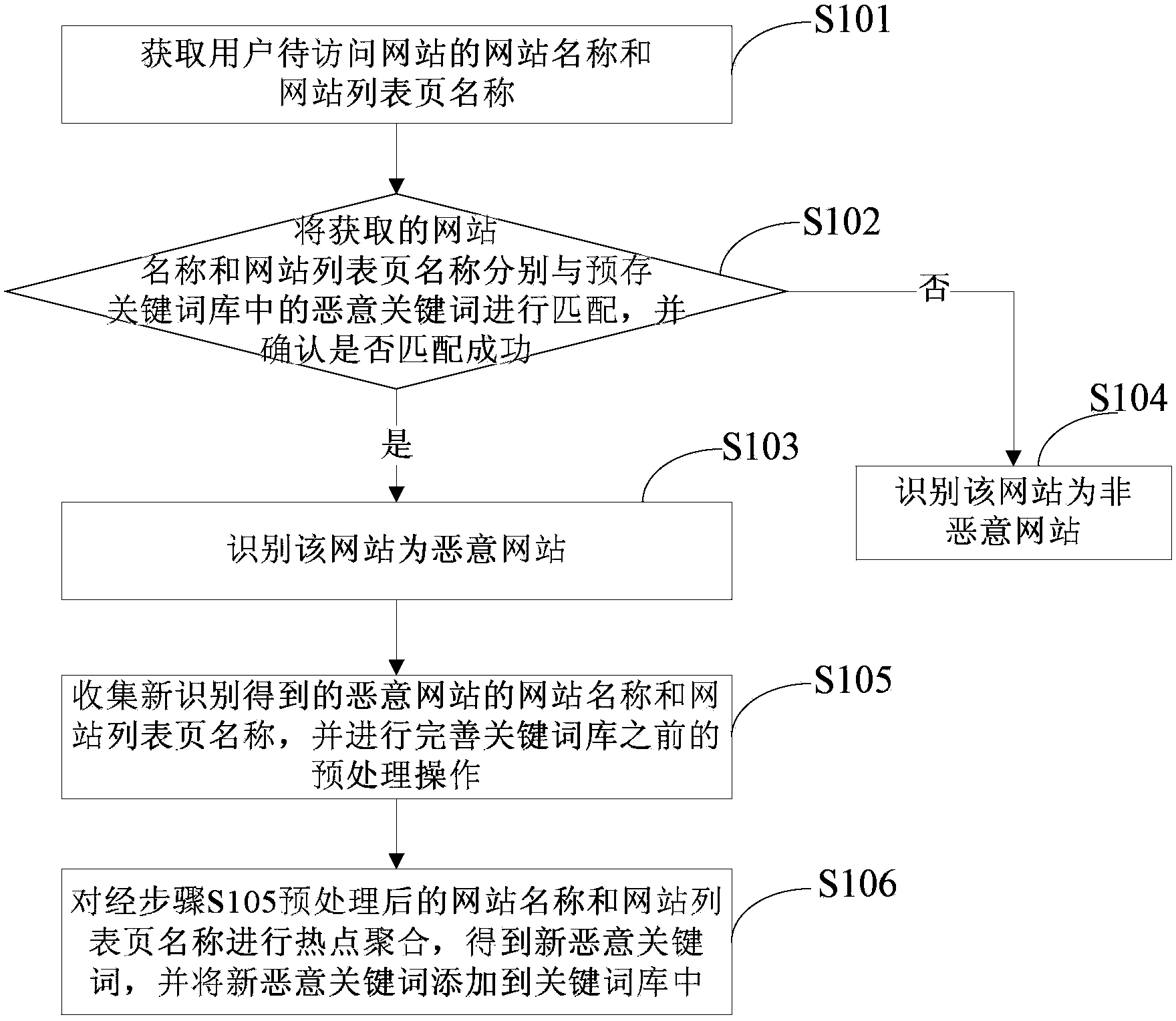
[0099] figure 1 A flow chart of a method for identifying a malicious website according to an embodiment of the present invention is shown. The method specifically includes steps S101 to S106.
[0100] S101. Obtain the website name and website list page name of the website to be visited by the user.
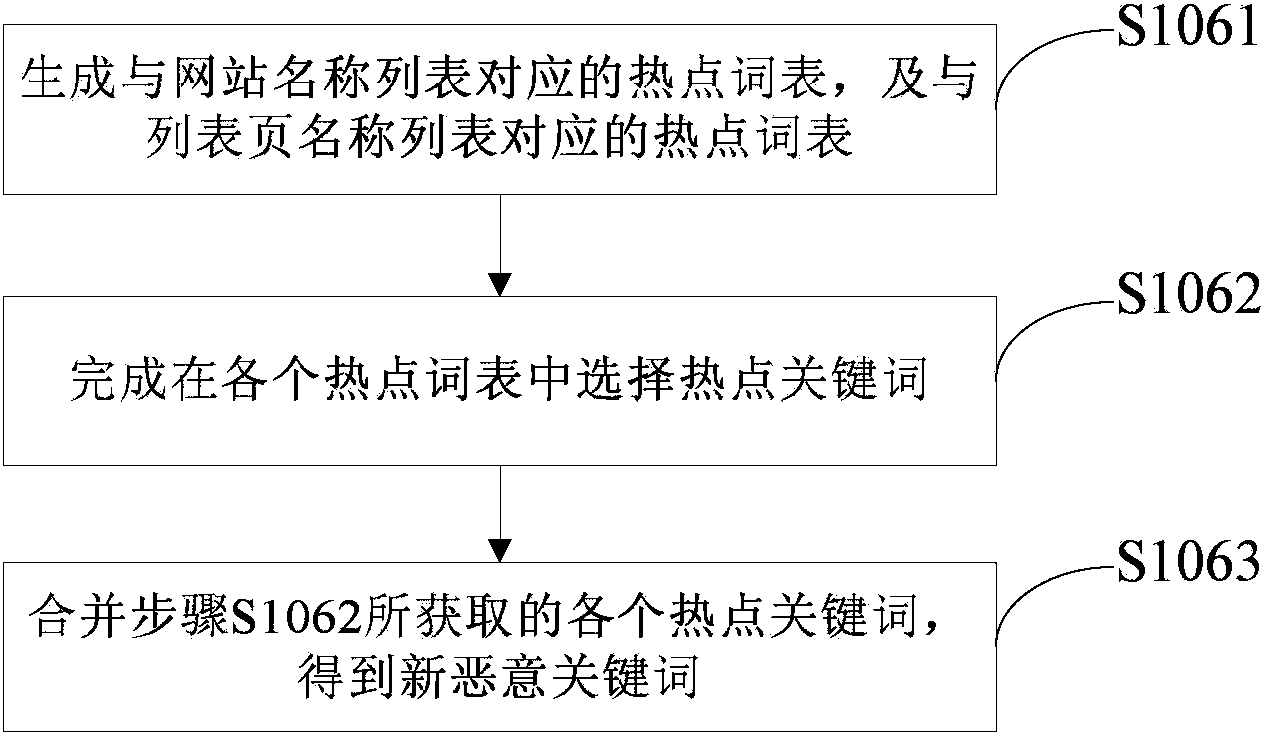
[0101] In this embodiment, the website name and website list page name are identification information of the website, which represent the function or content of the website. When developers name a website, they generally name it according to the function or content it contains. In addition, when a user visits a certain website, the website will display multiple content-categorized pages to the user through the website list page, so that the user can select the link of interest ...
Embodiment 2
[0147] This embodiment is another specific application scenario of the present invention. Through this embodiment, the method provided by the present invention can be described more clearly and specifically.
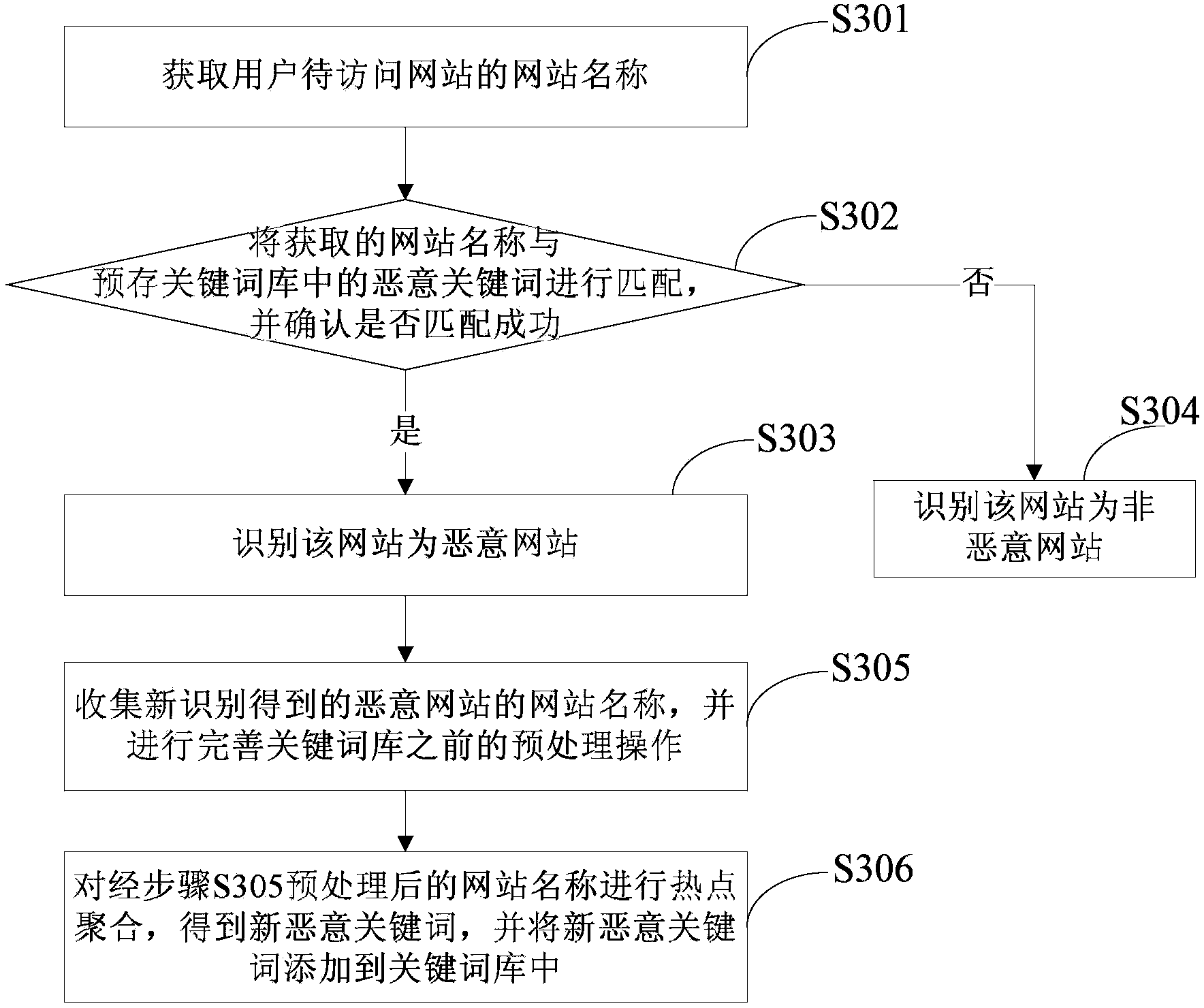
[0148] image 3 A flow chart of a method for identifying a malicious website according to another embodiment of the present invention is shown. The method specifically includes steps S301 to S306.
[0149] Step S301, obtaining the name of the website or the name of the website list page to be visited by the user.
[0150] The name of the website or the name of the website list page in this embodiment has been introduced in detail in the first embodiment above, and will not be repeated here.
[0151] It should be noted that when the obtained website identification information is only the website name or only the name of the website list page, the malicious website identification method adopted in this embodiment is the same. In order to introduce the method provided by...
Embodiment 3
[0178] Figure 5 A block diagram of an apparatus for identifying a malicious website according to another embodiment of the present invention is shown. The device 600 includes:
[0179] The memory 601 is configured to store a keyword library containing malicious keywords;
[0180] a user input interface 602 configured to receive an instruction from a user to visit a website;
[0181] An information acquirer 603, coupled to the user input interface 602, configured to acquire identification information of the website to be visited;
[0182] The information matcher 604 is coupled with the above-mentioned memory 601 and the information acquirer 603, configured to read the memory 601 and the information acquirer 603, and match the identification information with the malicious keywords in the keyword library;
[0183] The malicious website identifier 605 is coupled with the information matching unit 604 and is configured to identify the website as a malicious website if the infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com