A method for providing authorized access to a service application in order to use a protected resource of an end user
A technology for end-user and service applications, used in digital data protection, instrumentation, digital data authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
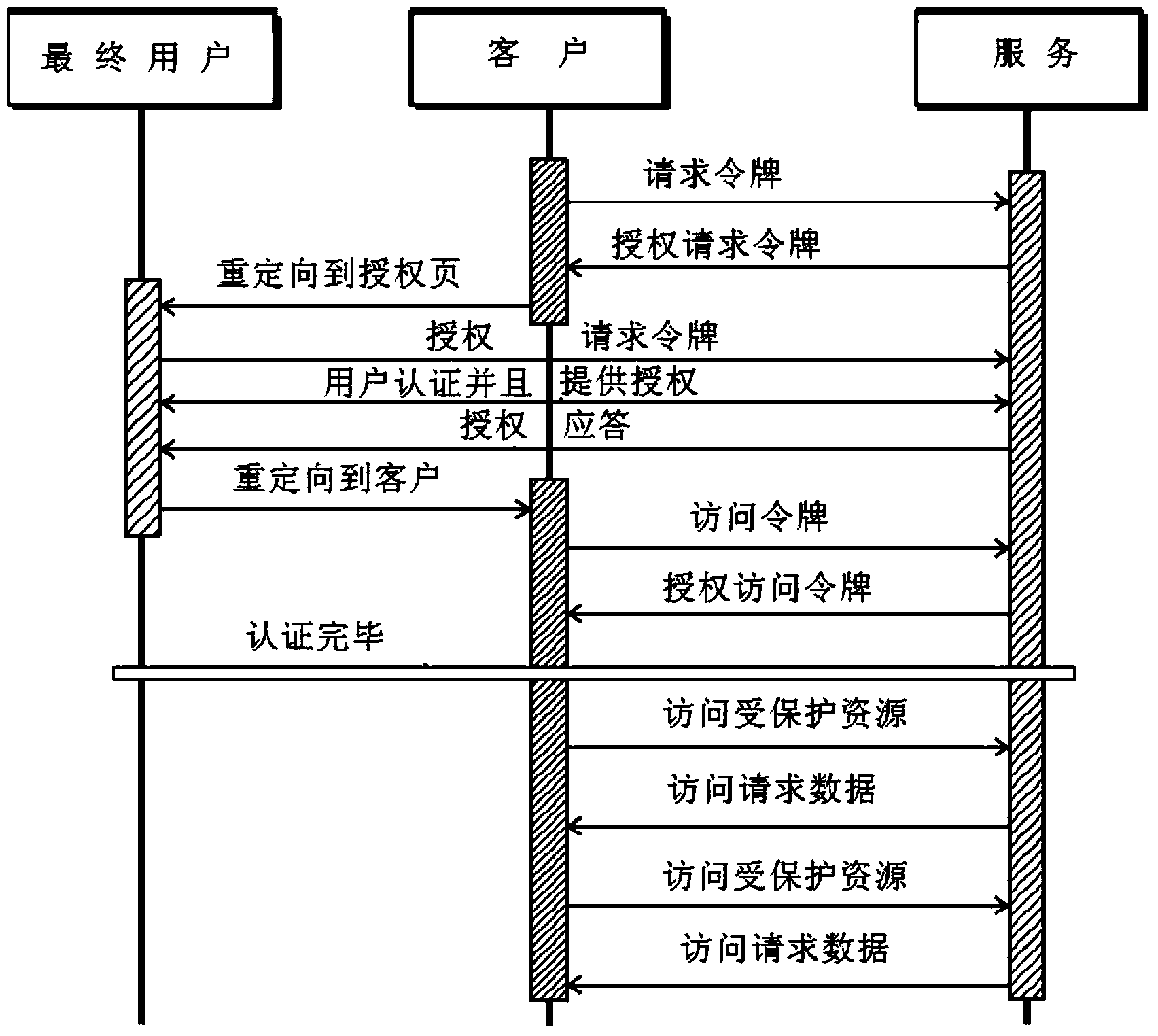
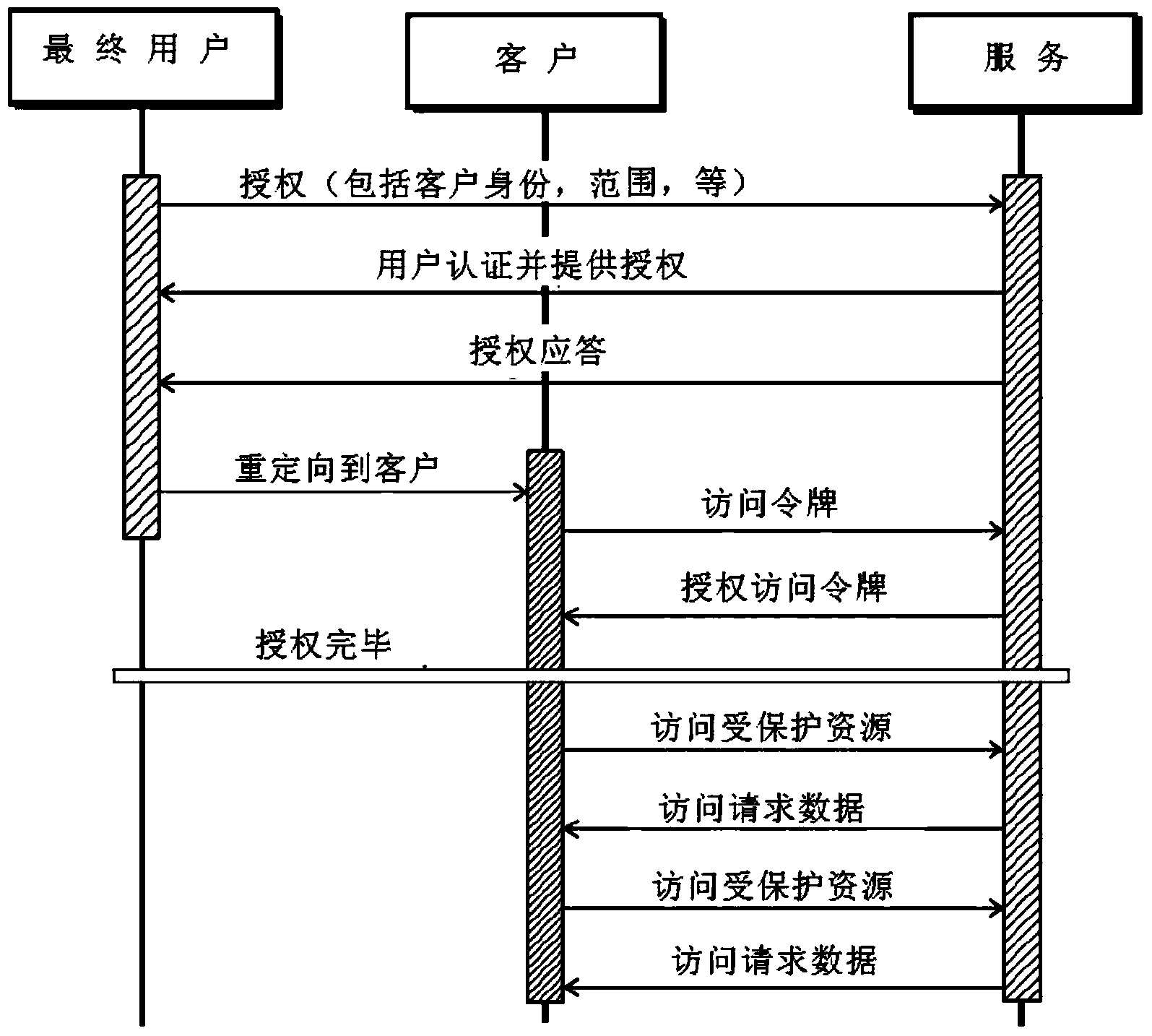
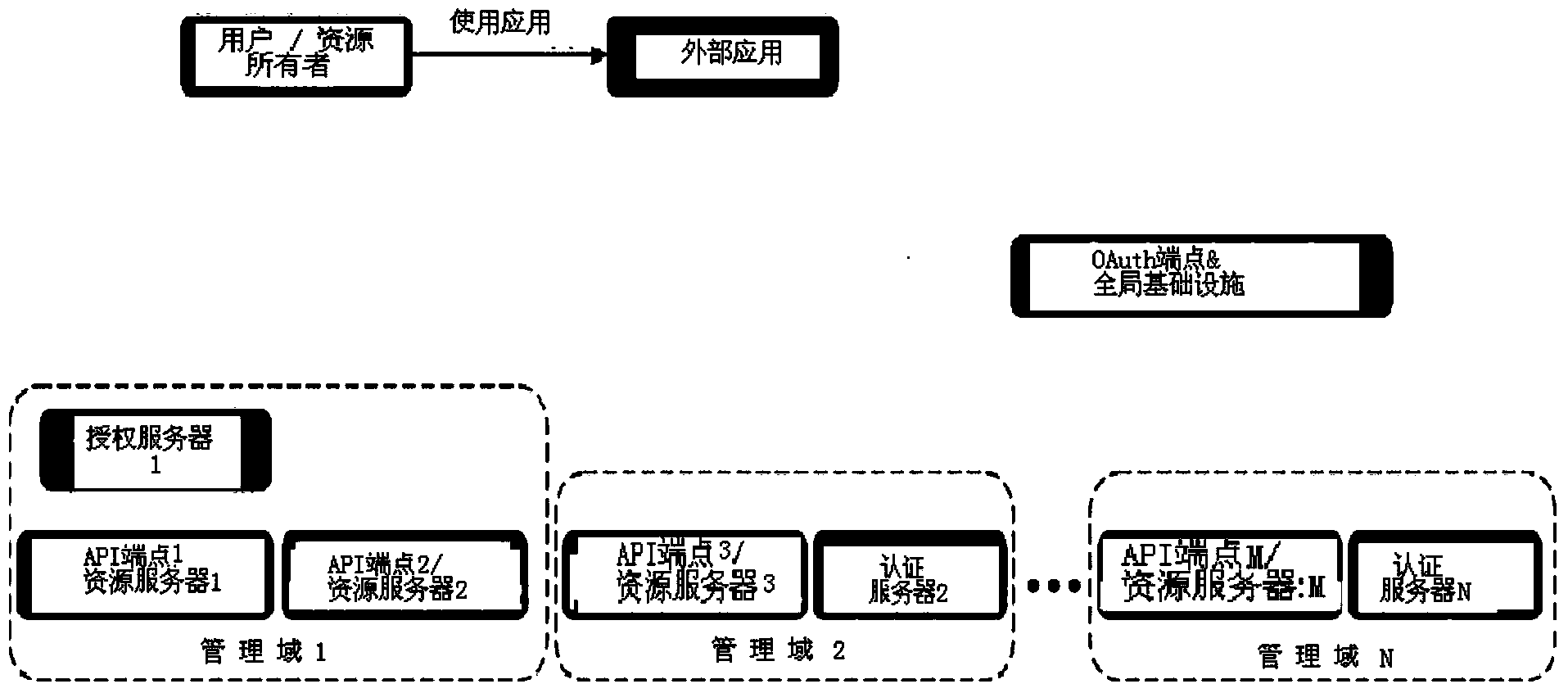
[0055] The present invention provides a solution for applying OAuth 1.0 and / or 2.0 to scenarios of highly distributed and potentially changing API publications. Such as image 3 According to the graphical representation of the scenario shown in , the following requirements must be considered:
[0056] - API endpoints (ie, exposed services or resources) are OAuth1.0 or OAuth2.0 compliant and have no knowledge of each other or any global infrastructure.
[0057] -Each API endpoint belongs to a management domain, which is responsible for implementing access control to the local API endpoint. Administrative domains usually correspond to service providers, but a service provider may have multiple administrative domains.
[0058] - Does not have any prior knowledge of API endpoints or admin domains for external applications that must be used by every end user.
[0059] - The point of API exposure and the management domain can change over time.
[0060] First, since the applicati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com