Two-factor identity authentication method based on Chinese character format information
A format information and identity authentication technology, applied in the field of two-factor identity authentication based on Chinese character format information, can solve the problem of poor challenge code non-uniqueness, and achieve the effect of improving non-uniqueness, providing security barriers and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
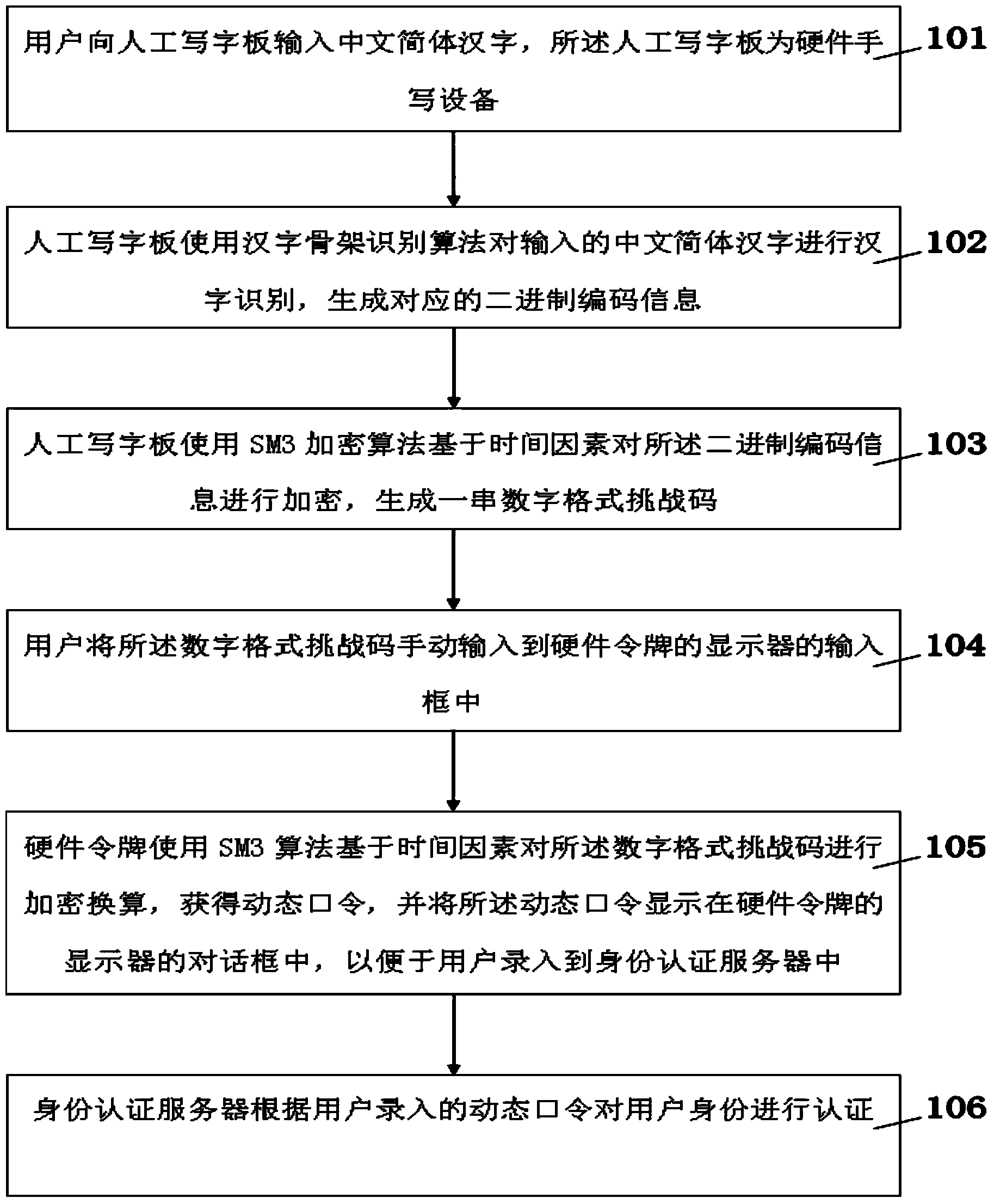
[0016] First, please refer to figure 1 , figure 1 It is a method flowchart of a two-factor identity authentication method based on Chinese character format information in the present invention, and the authentication method includes the following steps:
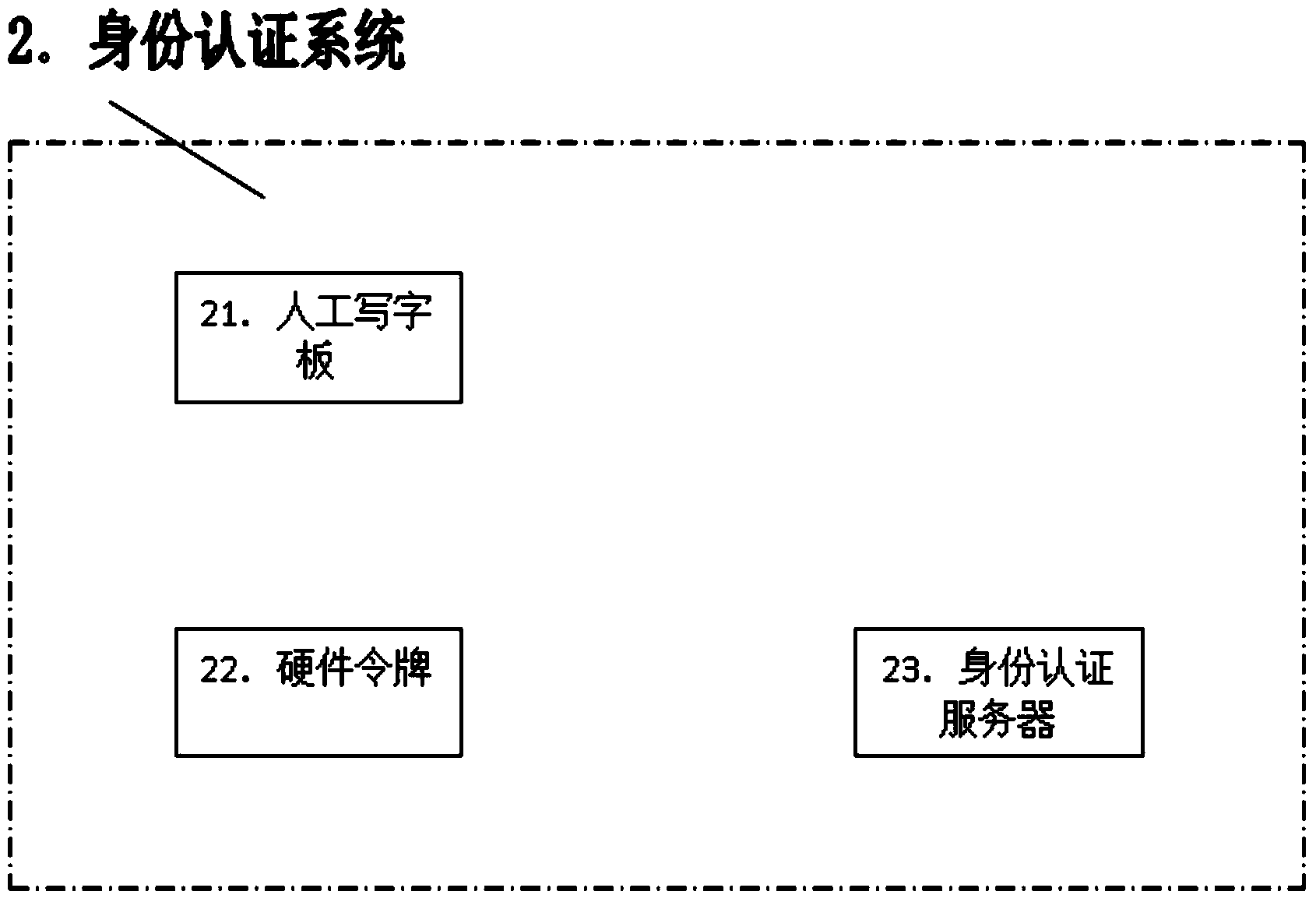
[0017] Step 101: The user inputs simplified Chinese characters to the manual tablet, which is a hardware handwriting device;
[0018] Step 102: The artificial writing board uses the Chinese character skeleton recognition algorithm to perform Chinese character recognition on the input Chinese simplified Chinese characters, and generates corresponding binary coded information;
[0019] Step 103: The manual tablet uses the SM3 encryption algorithm to encrypt the binary coded information based on the time factor to generate a string of challenge codes in digital format;
[0020] Step 104: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com