Resource access method and URG
A technology for user resources and resource access, applied in the field of resource access methods and user resource gateways, can solve the problems of long execution and response time of resource access, and many signaling interactions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
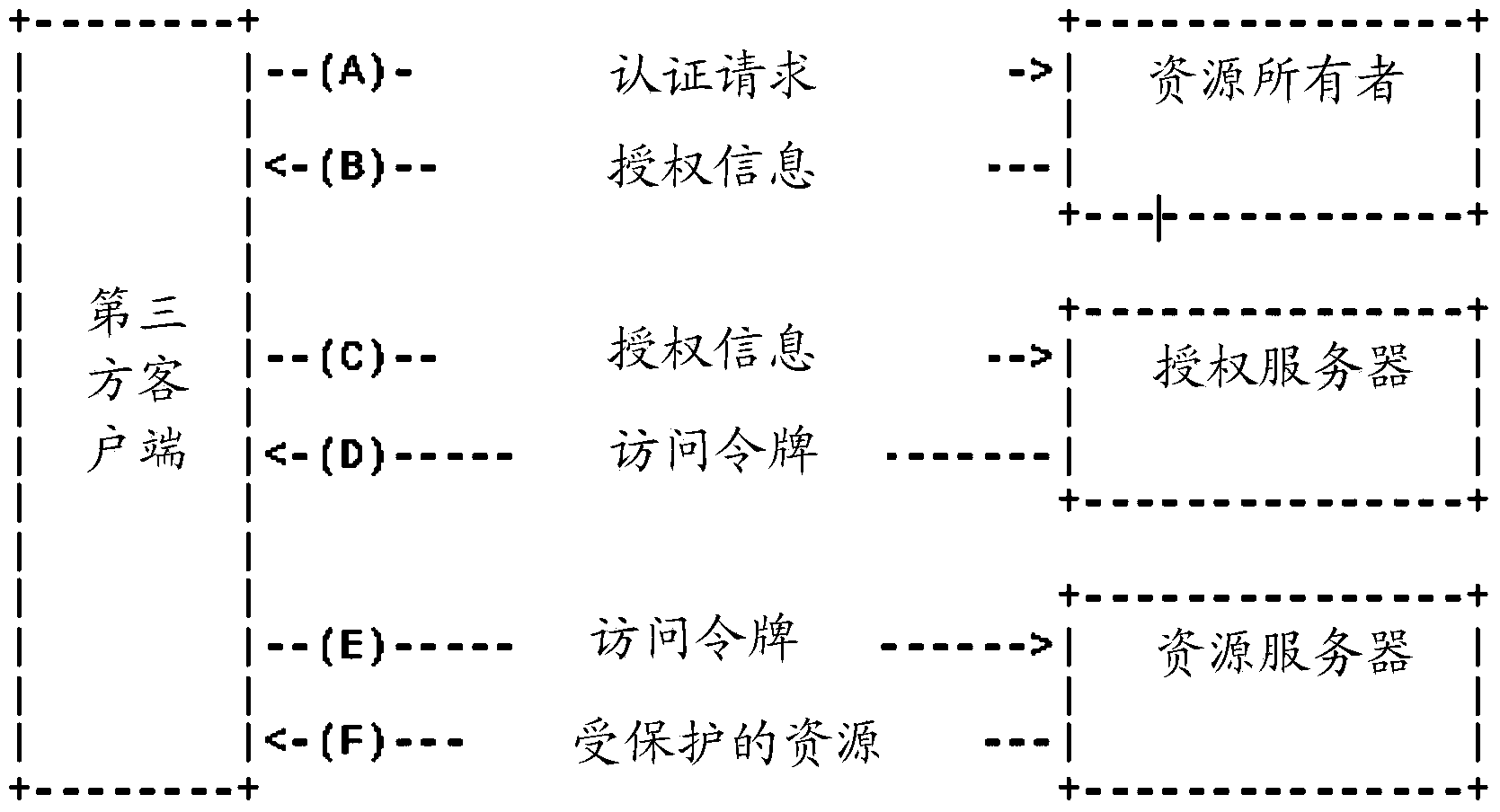
[0074] Embodiments of the present invention provide a resource access method and a user resource gateway, which are used to solve the problem in the prior art that there are many signaling interactions between the client and the resource server or the authorization server when the client accesses resources, so the execution of accessing resources and Technical issues with long response times.
[0075] The technical solution in the embodiments of the present invention is to solve the above-mentioned technical problems, and the general idea is as follows:
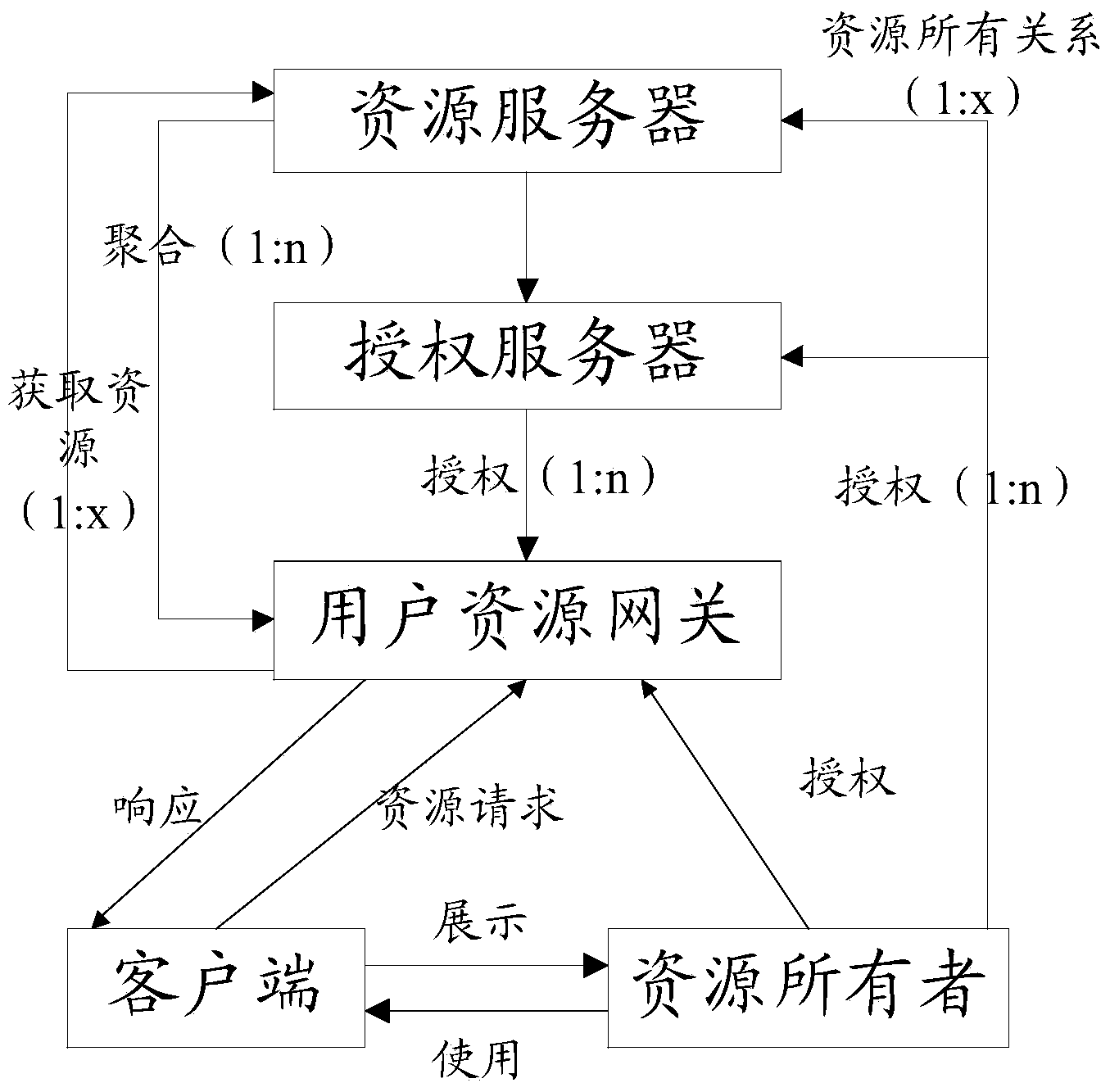
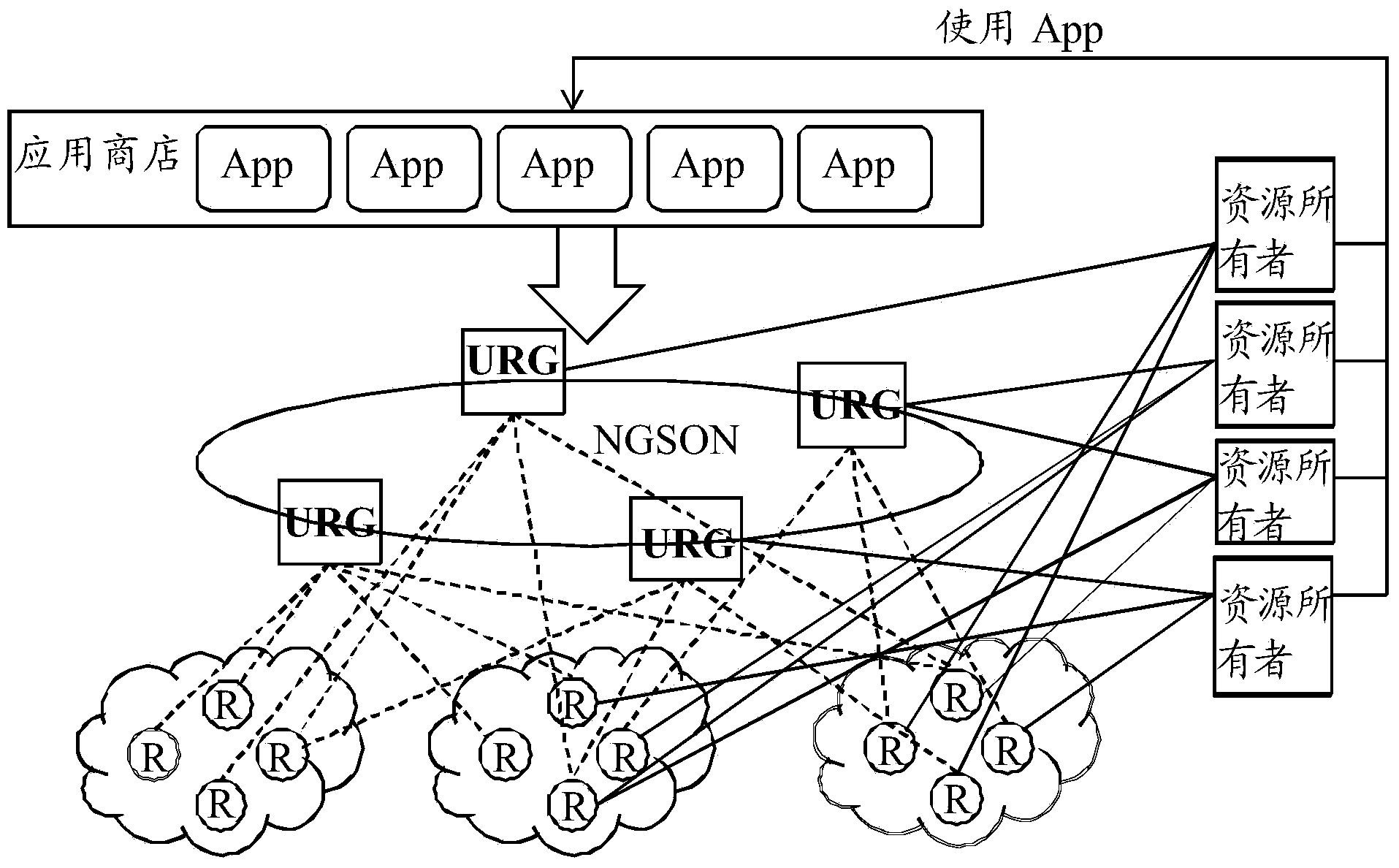
[0076] In an embodiment of the present invention, the User Resource Gateway (URG) receives the resource aggregation request sent by the resource owner, and the resource aggregation request includes the user ID and the resource identifier of the M-type service, and the resource identifier is specifically It can be a resource name or a resource storage address; among them, M is a positive integer; URG sends an authorization req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com