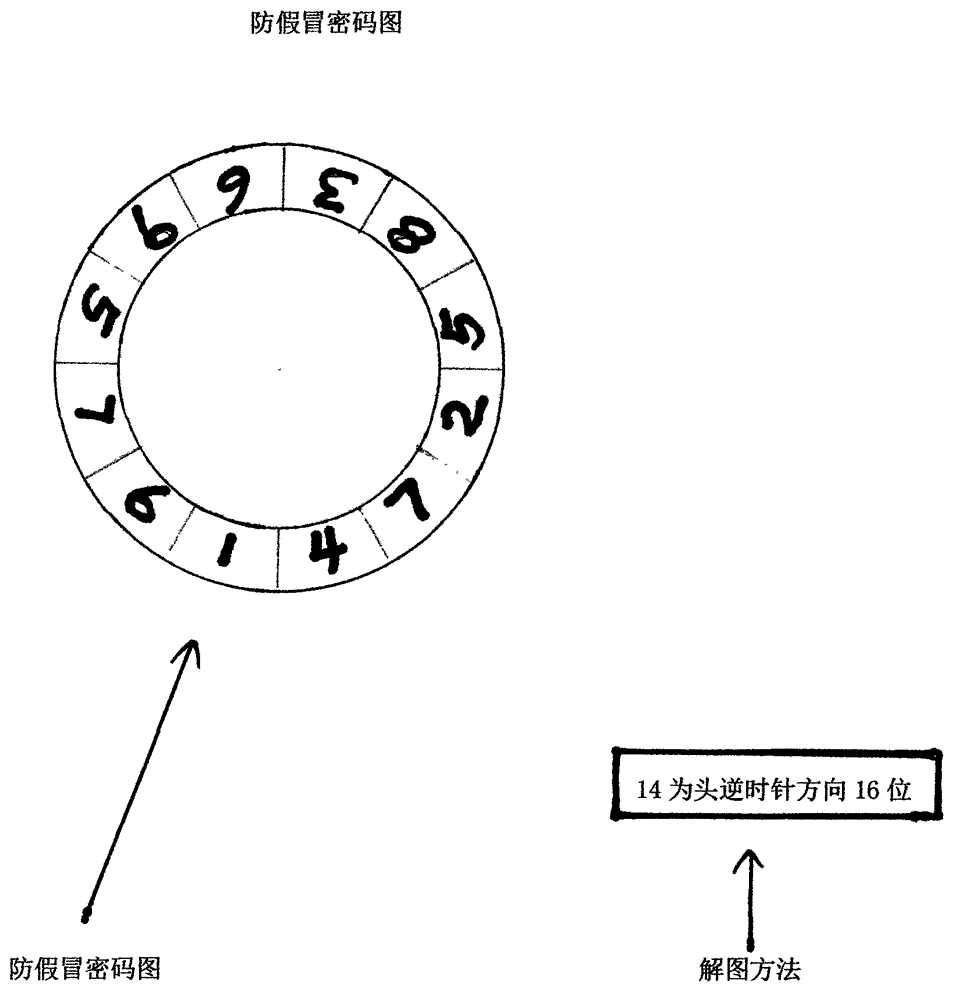
Anti-counterfeit cipher graph
An anti-counterfeiting and password technology, which is applied in the field of anti-counterfeiting password maps, can solve the problems of not being able to prevent the anti-counterfeiting password counterfeiting method, and that the anti-counterfeiting password cannot be reused.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0007] Such as figure 1 Shown: the anti-counterfeit password that prevents counterfeiting is hidden in the anti-counterfeit password diagram, if there is no way to solve the diagram, the only correct anti-counterfeit password cannot be obtained. As long as the anti-counterfeit password diagram is placed in the package, and the method of deciphering the diagram is placed in the product, counterfeiters can be prevented from obtaining the anti-counterfeit password by purchasing the package.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com