Security element and method to inspect authenticity of a print
A technology of security elements and content, applied in the field of security elements, can solve the problems of expensive ink, limited application of security elements, and inability to identify hidden watermarks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
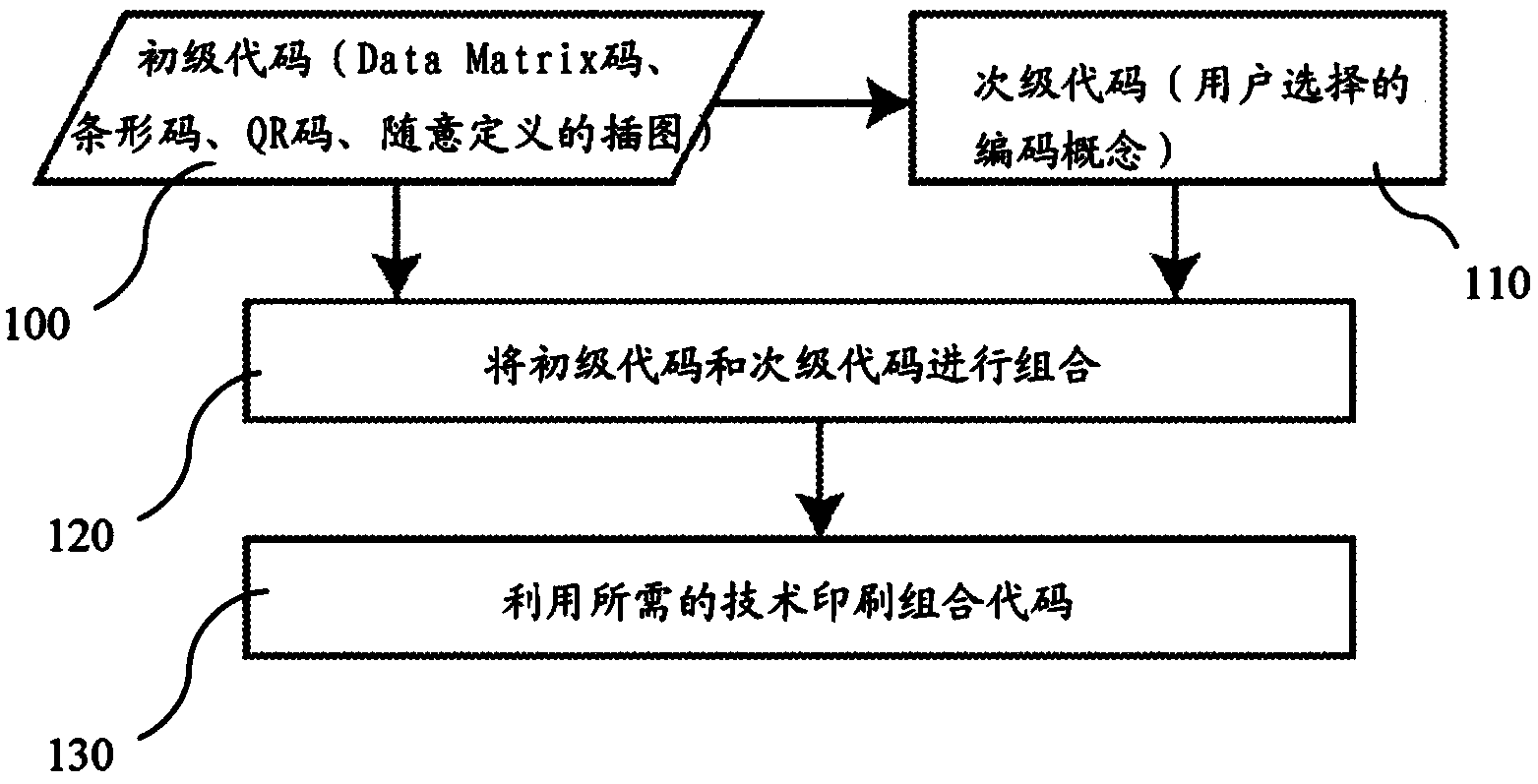
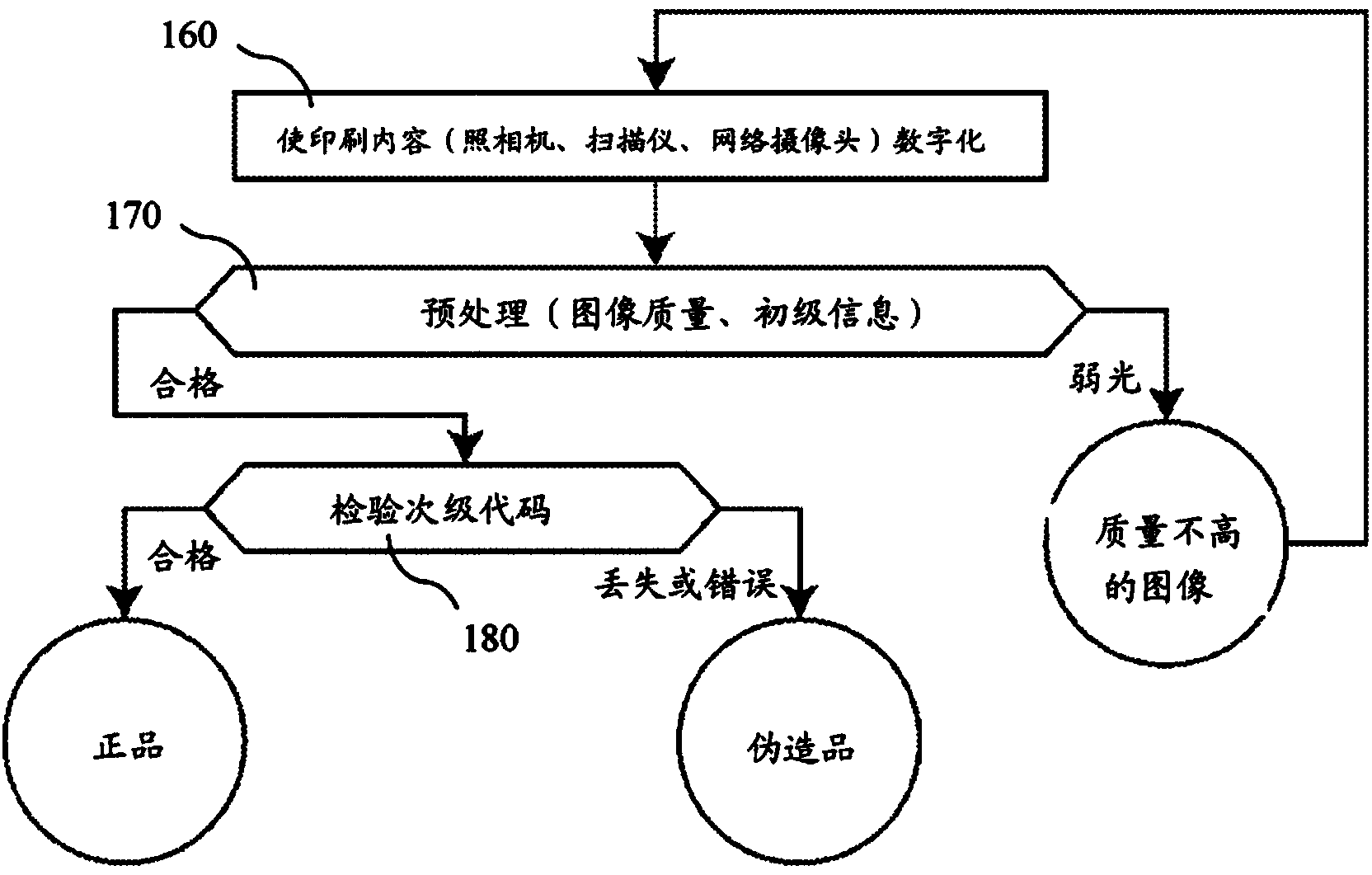
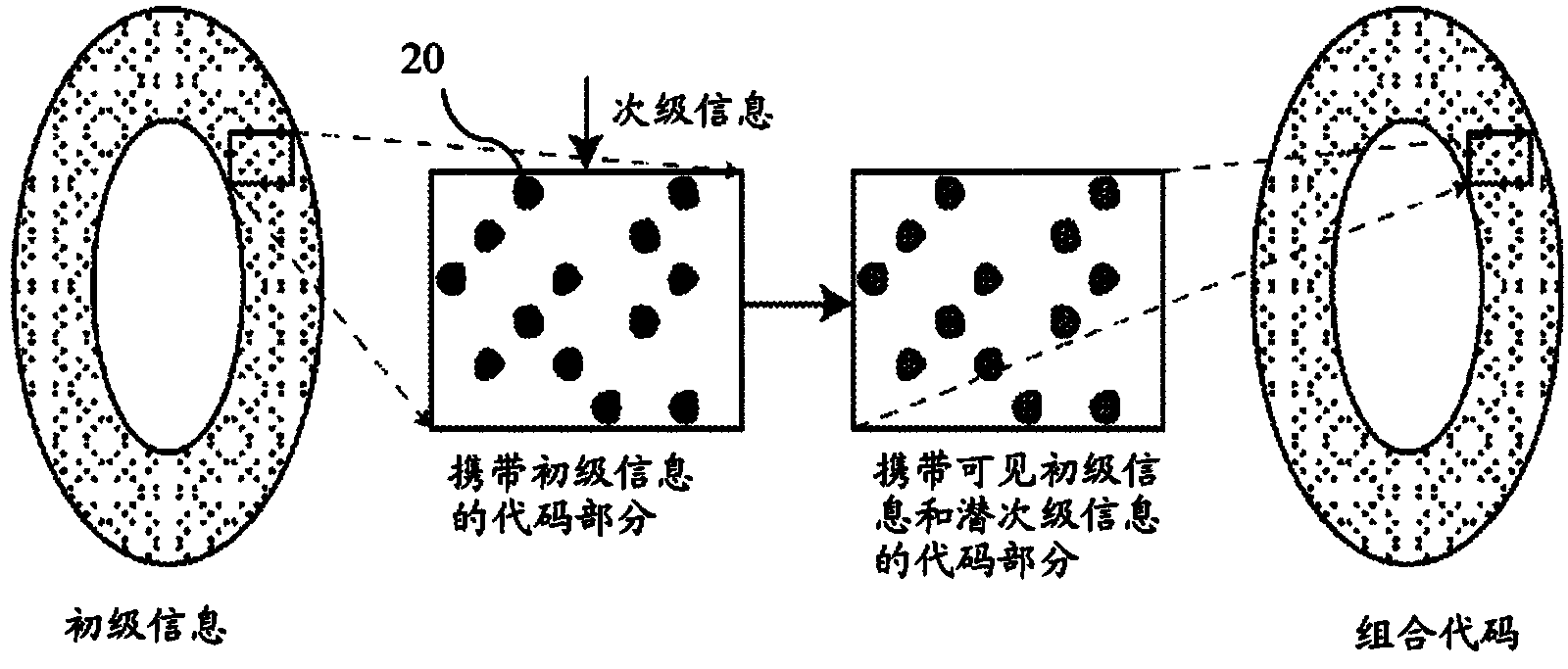
[0028] Figure 1A A general method of generating a security element formed of combined codes according to the invention is shown in . Accordingly, a code carrying the information is selected (step 100 ), formed of well-known code symbols (eg barcode, QR code, Data Matrix code, mobile code) or a uniquely coded line or point code. According to another possibility, the code carrying the primary information can also be formed by a line code or a point code hidden in a decorative graphic illustration of the printed content. Furthermore, the code carrying the primary information may be the primary information itself, which is simply printed in an uncoded manner onto the printed substrate. The printed substrate can be any document or the surface of an object to be protected, especially for example bank rolls, securities, invoices, product packaging, ID cards / labels, covers, tickets, certificates, personal documents, vouchers or any other similar documents . Primary information refe...
PUM
| Property | Measurement | Unit |
|---|---|---|
| Size | aaaaa | aaaaa |
| Wavelength | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com