Secret key generation method based on multi-modal biological characteristics
A biometric feature and key generation technology, which is applied in the fields of information security and biometrics, can solve problems such as insufficient key length, unsatisfactory recognition rate and rejection rate, and poor cross-terminal support for user data decryption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific implementation, but the scope of the present invention will not be limited in any way.
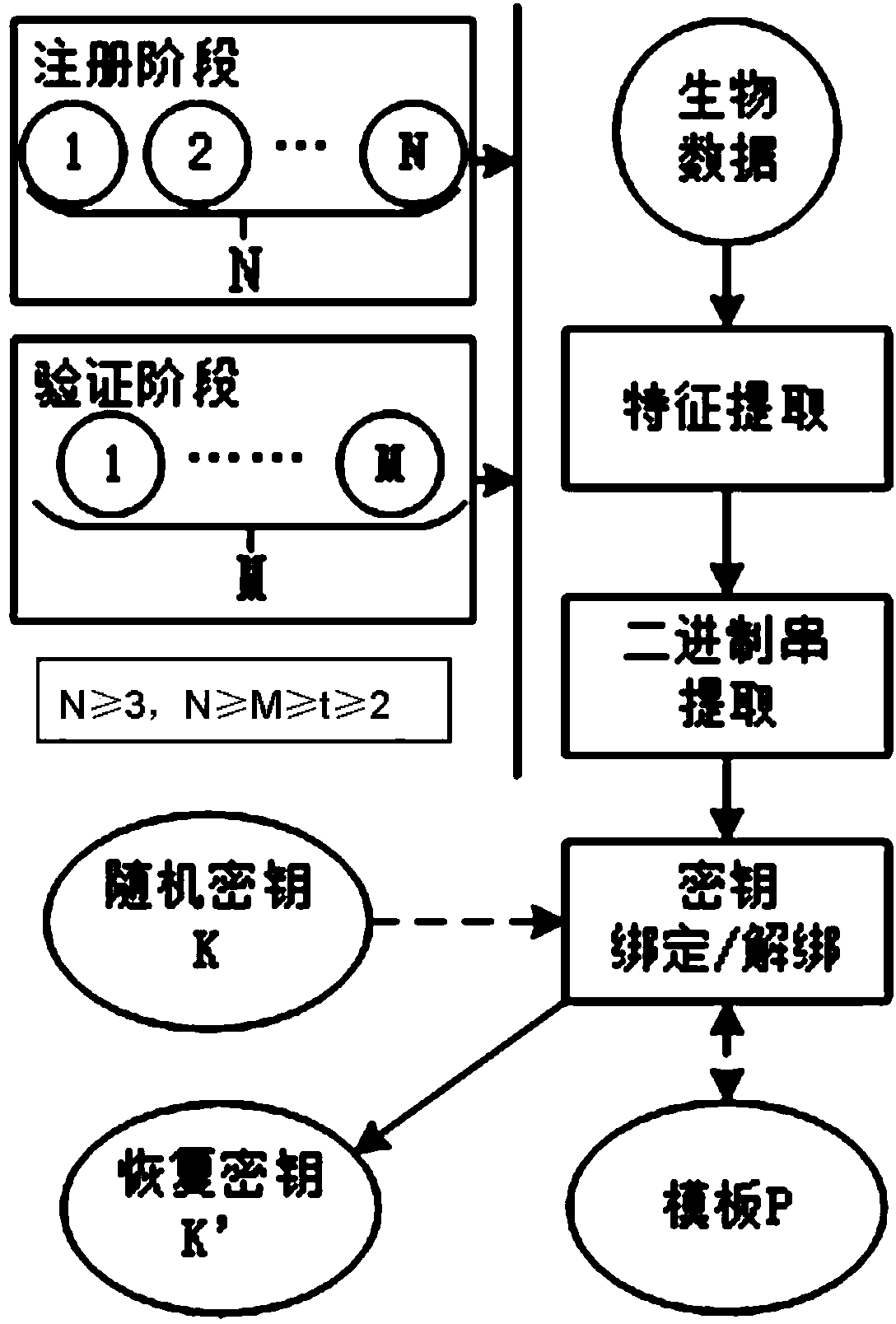
[0036] This implementation example uses figure 1 The overall framework diagram of the multimodal biometric key generation shown. It mainly includes three modules: biometric vector extraction, codeword extraction, and key binding / unbinding.
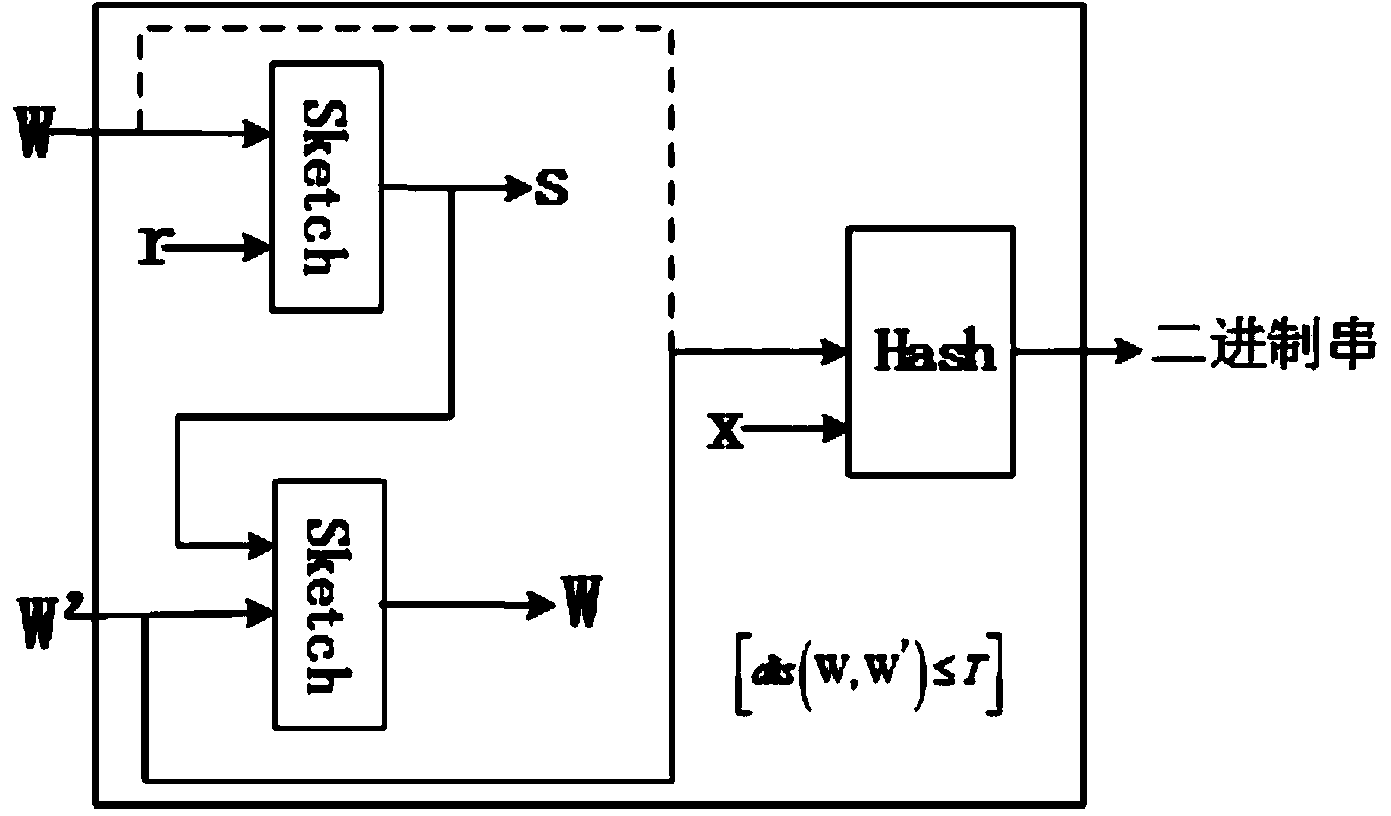
[0037] figure 2 Shown is the codeword extraction module. When registering or verifying, each biometric feature will generate or restore the corresponding codeword.
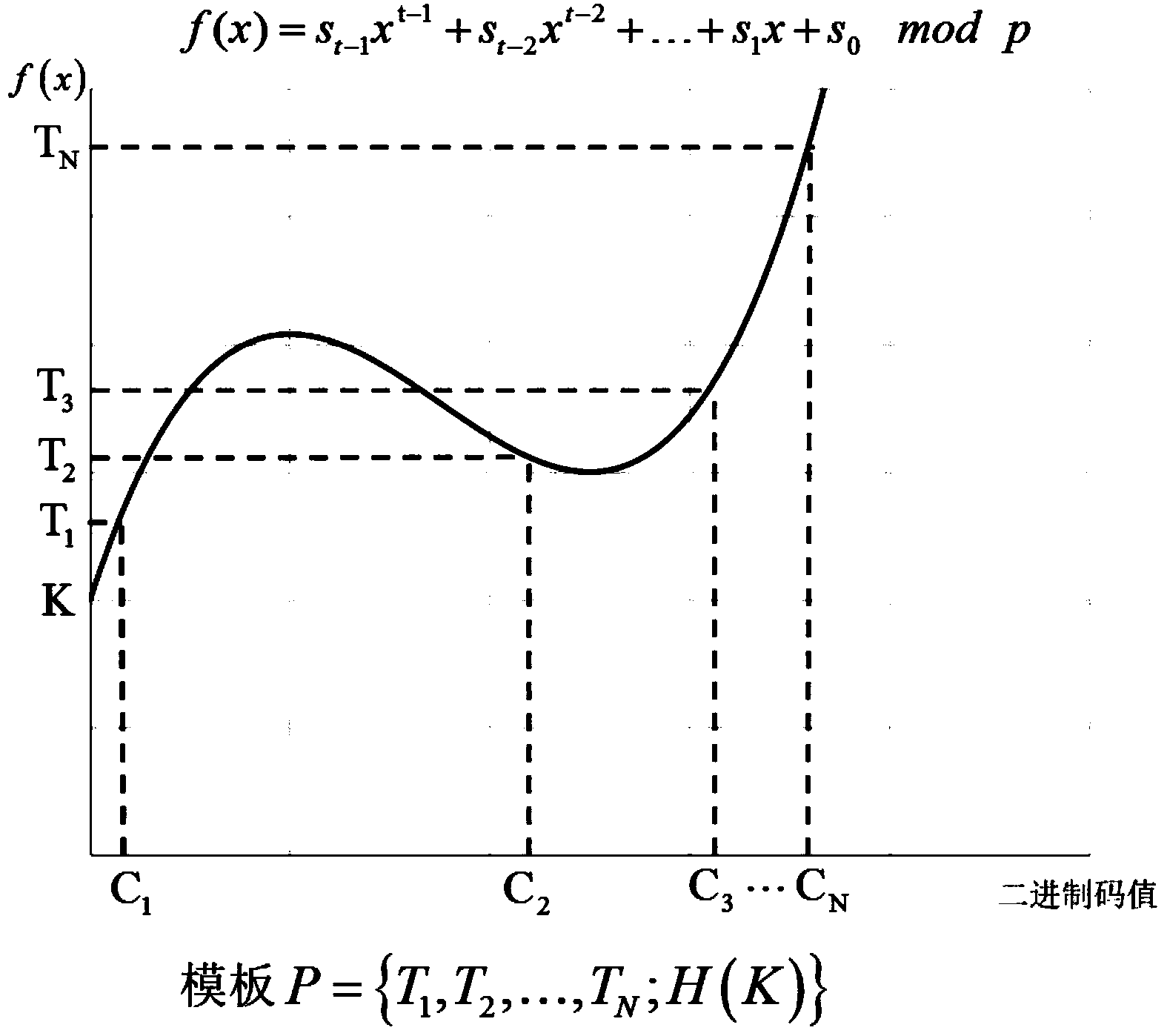
[0038] image 3 Shown is the key binding or unbinding module. When registering or verifying, you can bind or unbind a pre-generated random key.
[0039] In this implementation example, it is assumed that there are four types of biological data during registration, that is, N=4. The preset threshold value t=3, that is, only three kinds of biometric data can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com