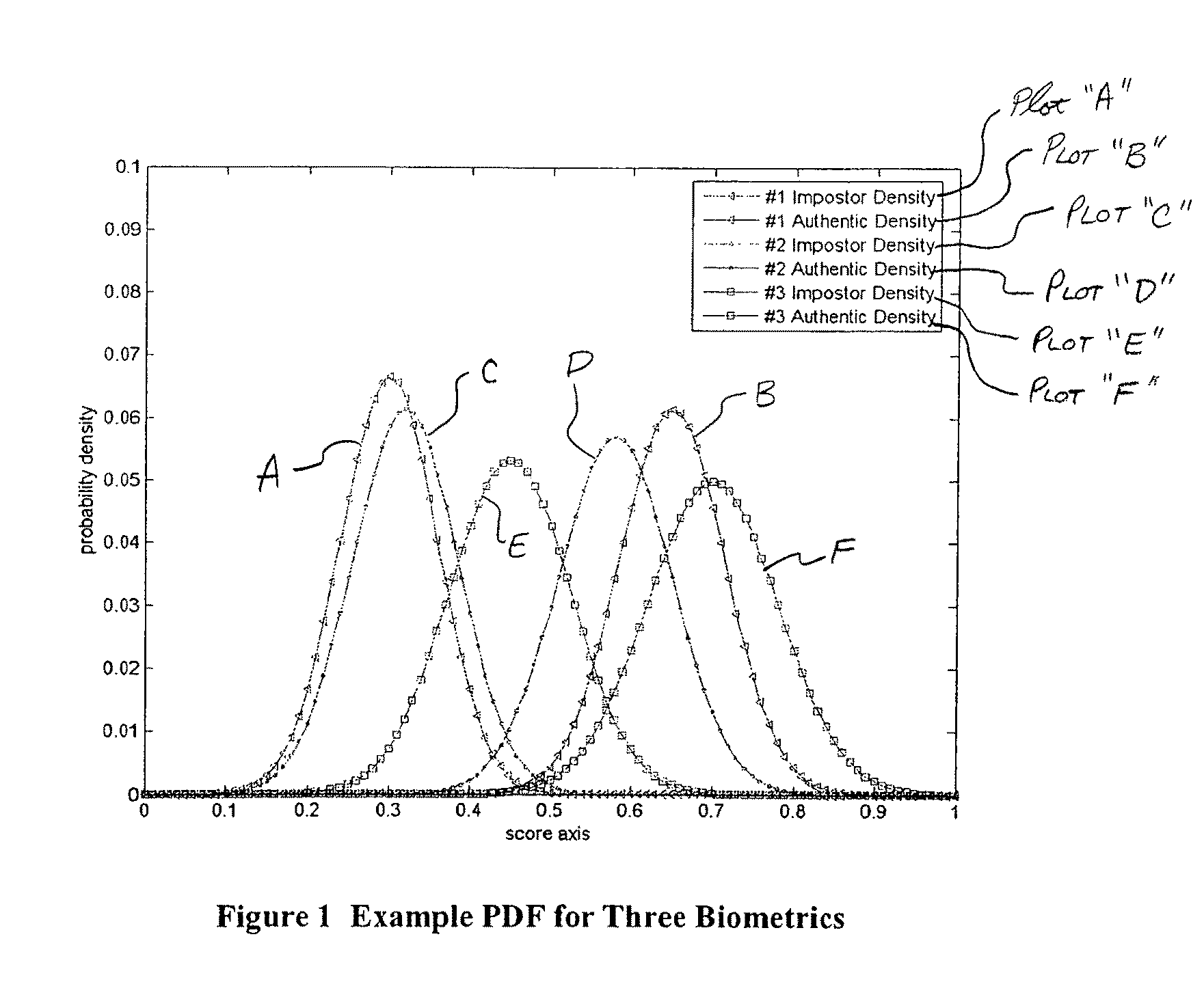
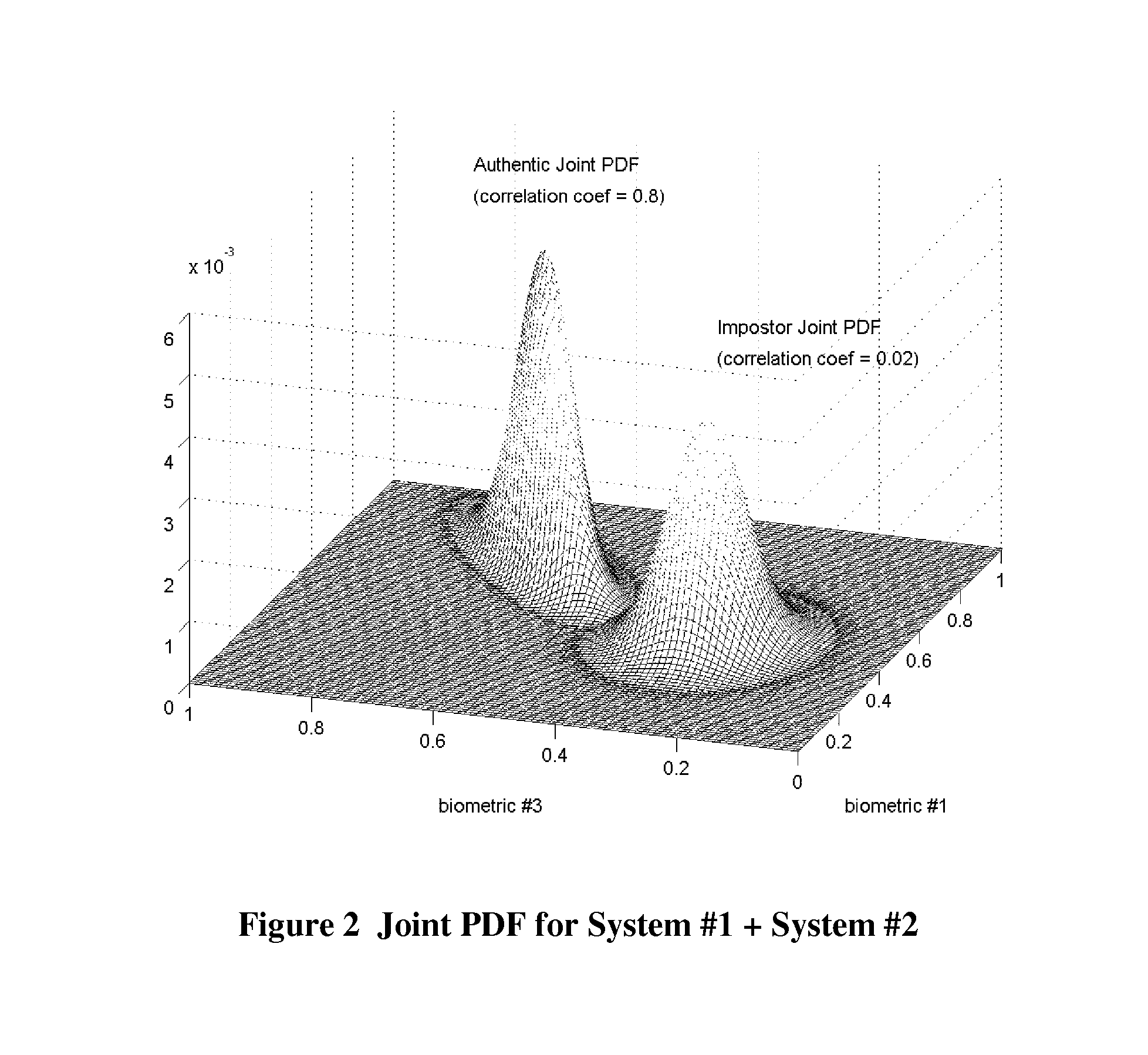
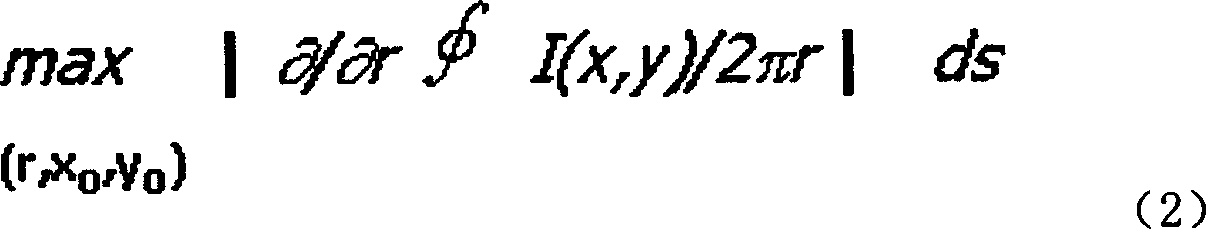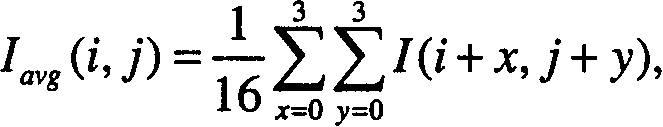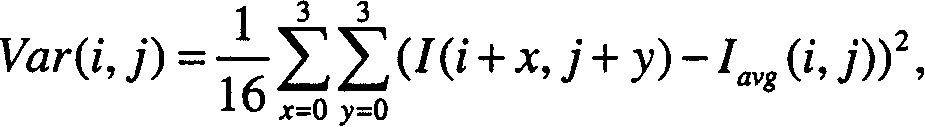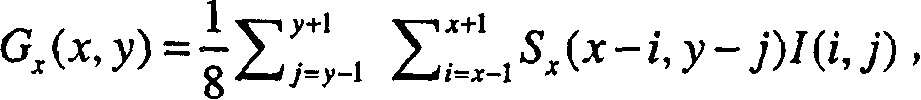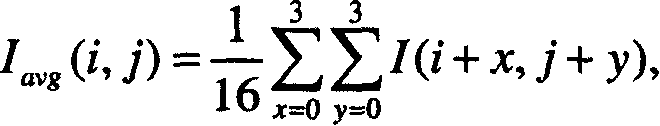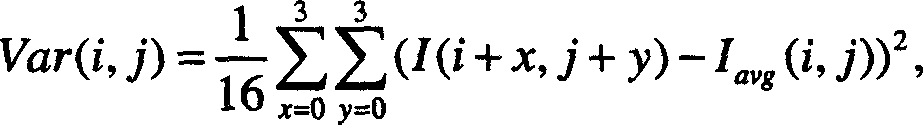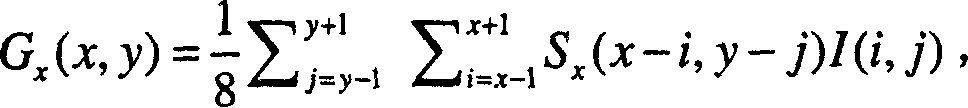Patents
Literature
98 results about "False rejection rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
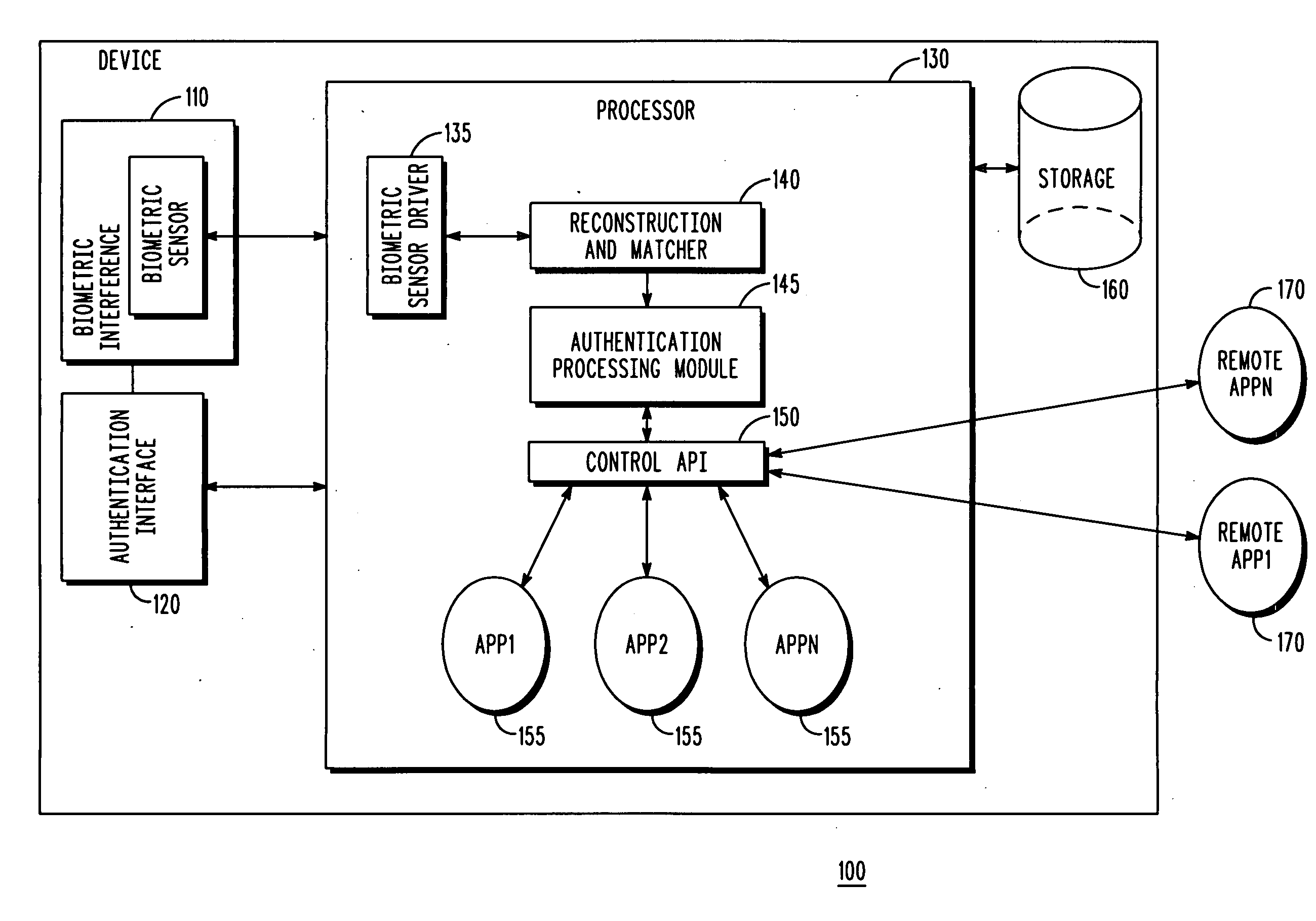
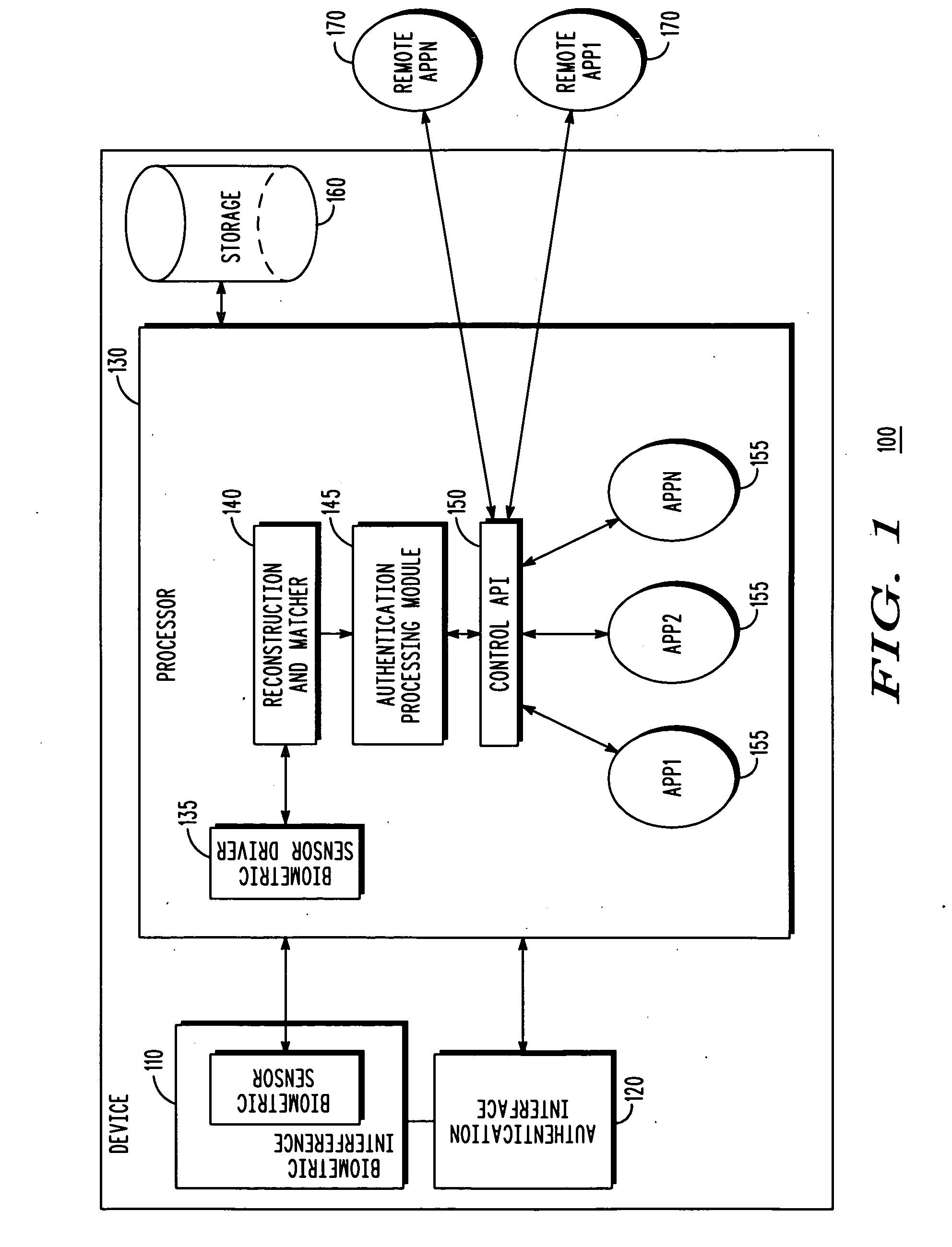
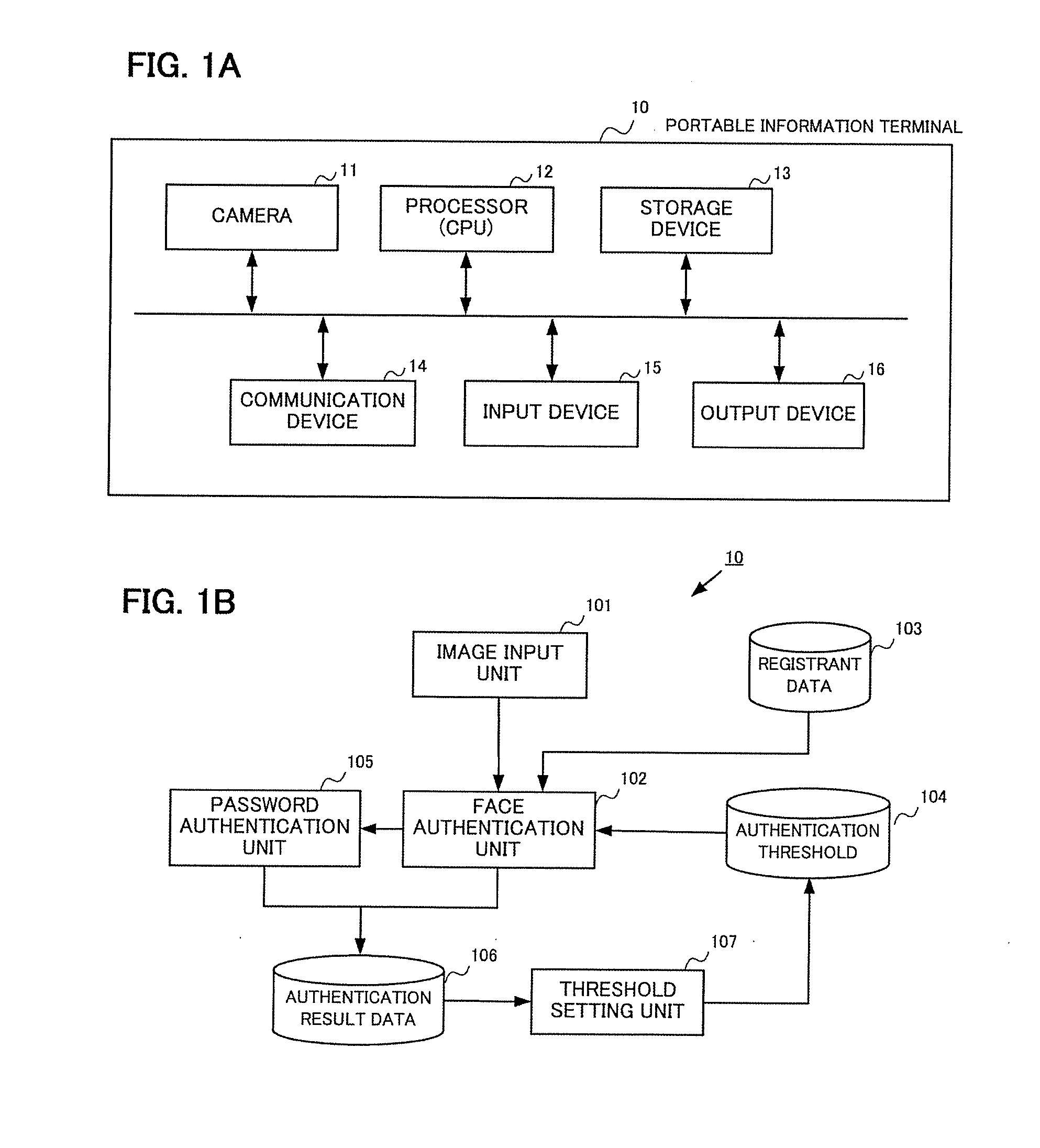
Biometric authentication based upon usage history
InactiveUS20100180127A1User identity/authority verificationComputer security arrangementsData miningFalse rejection rate
Customized biometric authentication based at least in part upon usage history and learning capabilities of a user is provided. A biometric sample of a user received at a biometric interface of a device is compared with at least one stored template that uniquely identifies the user, and a match score generated when the biometric sample matches one of the stored templates. The match score is compared to a match score threshold value of an application that the user is attempting to access to generate match score comparison results, and an updated false reject ratio (FRR) for the last N matches of the user is calculated. The user is allowed to access the application when the match score comparison results indicate that the match score is at least equal to the match score threshold value and the updated FRR is less than a FRR threshold value of the application.
Owner:MOTOROLA SOLUTIONS INC
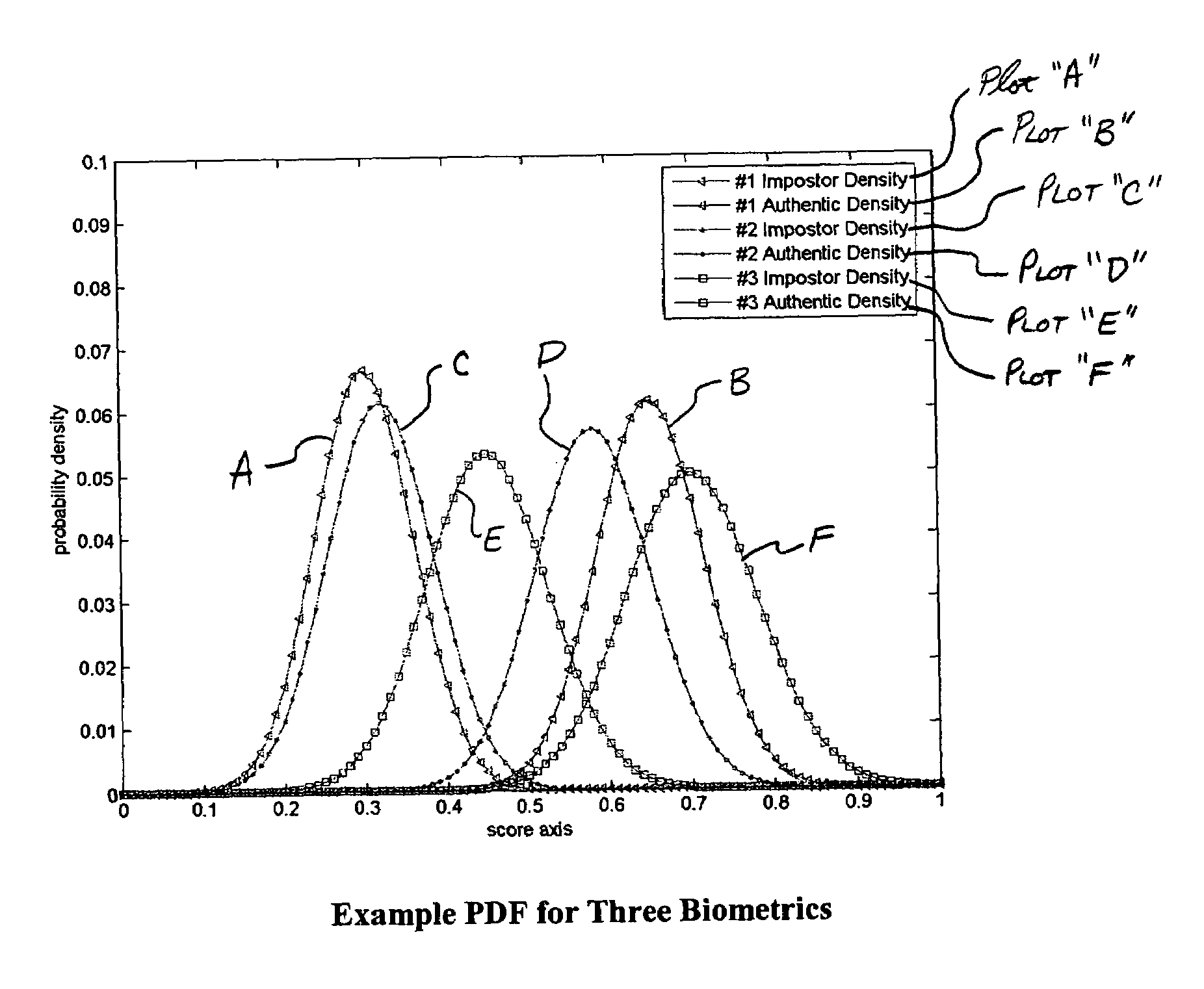
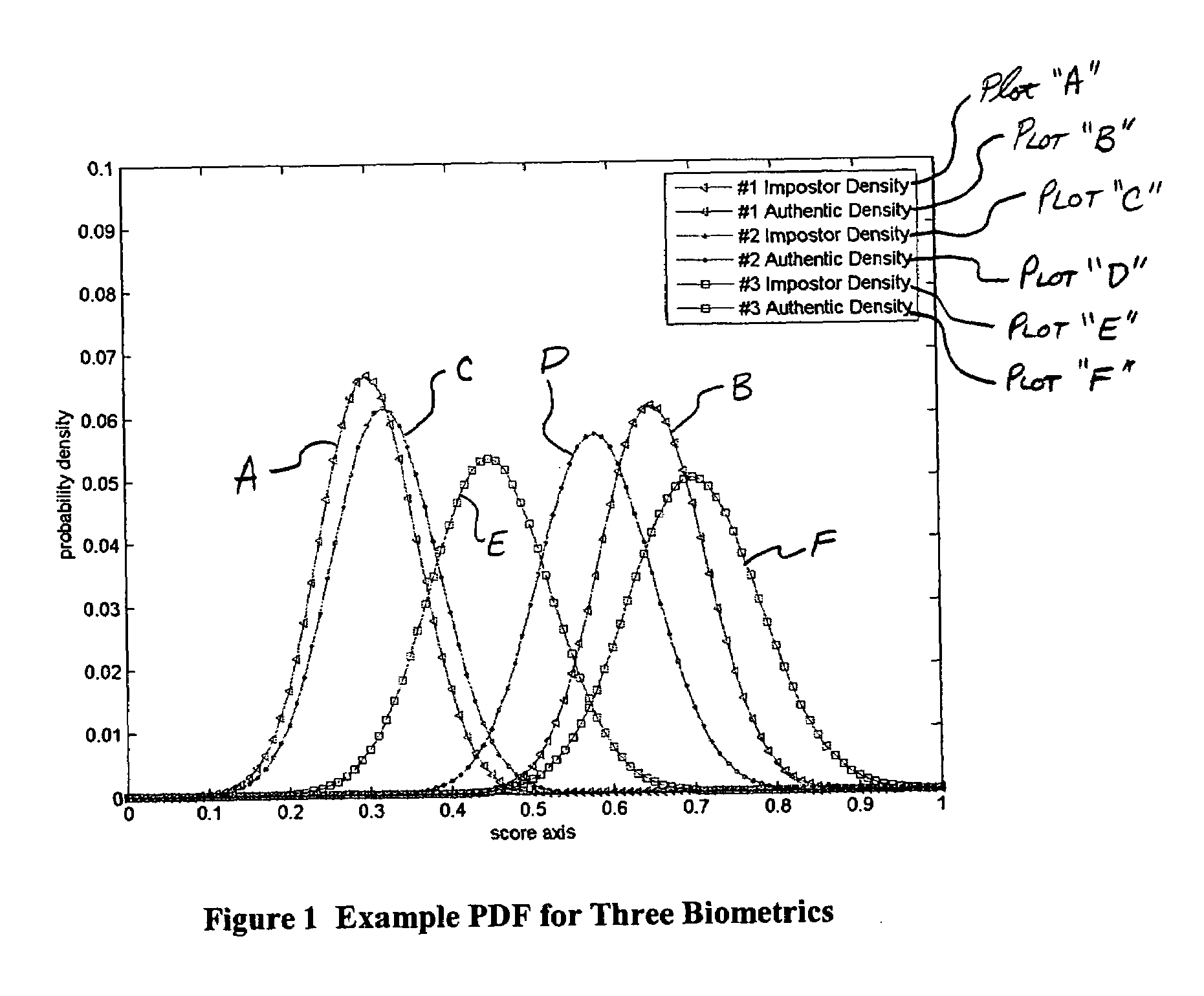
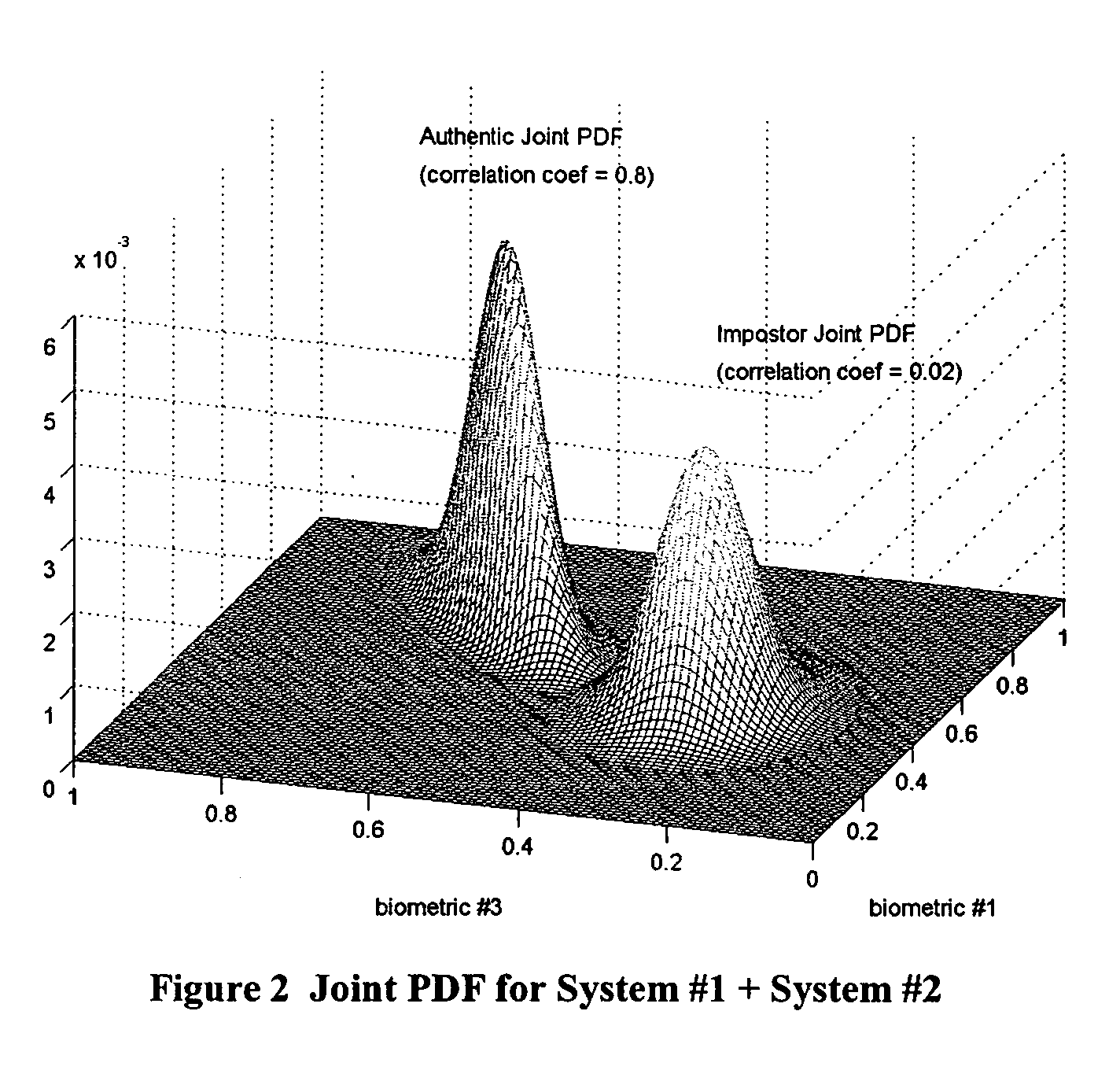
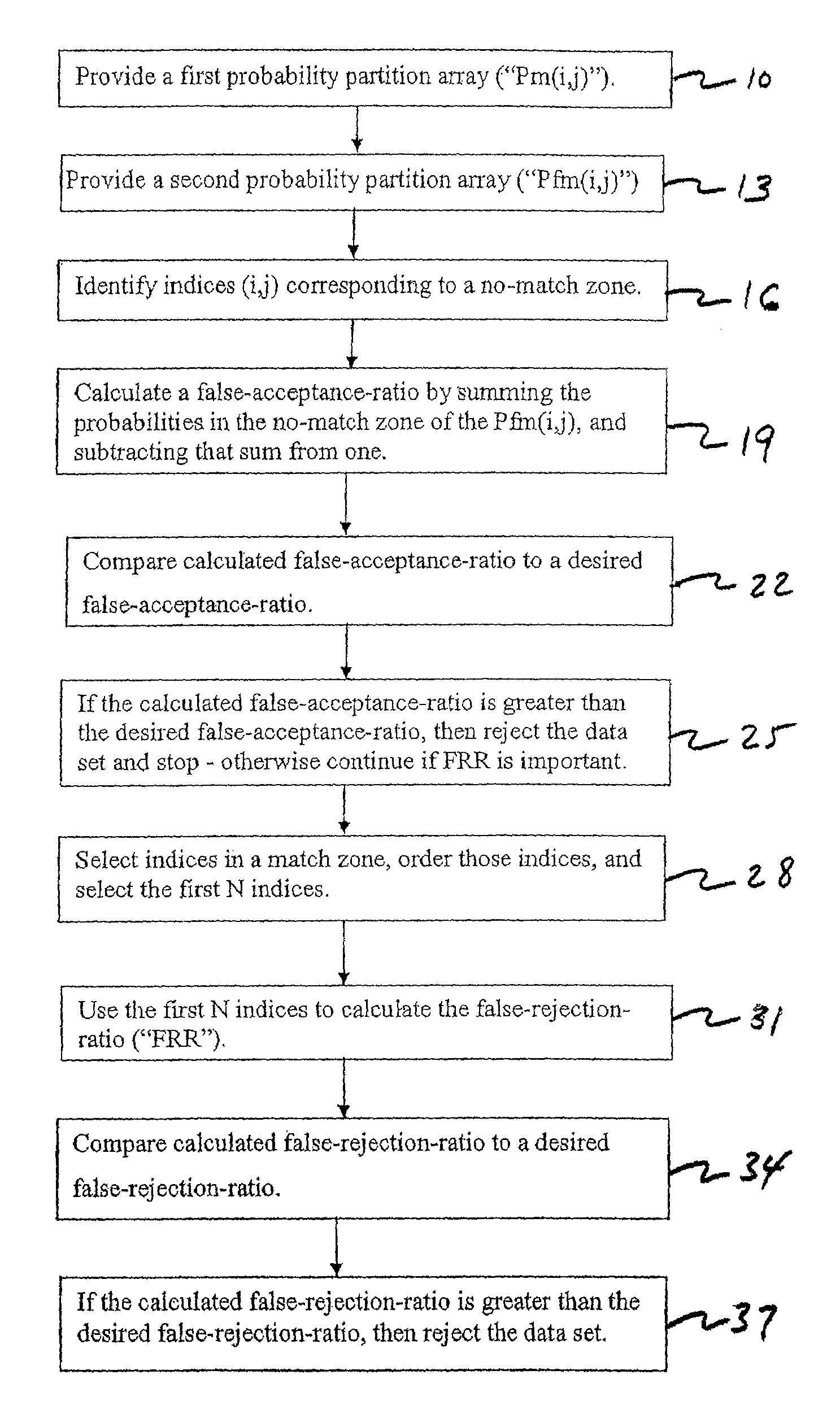
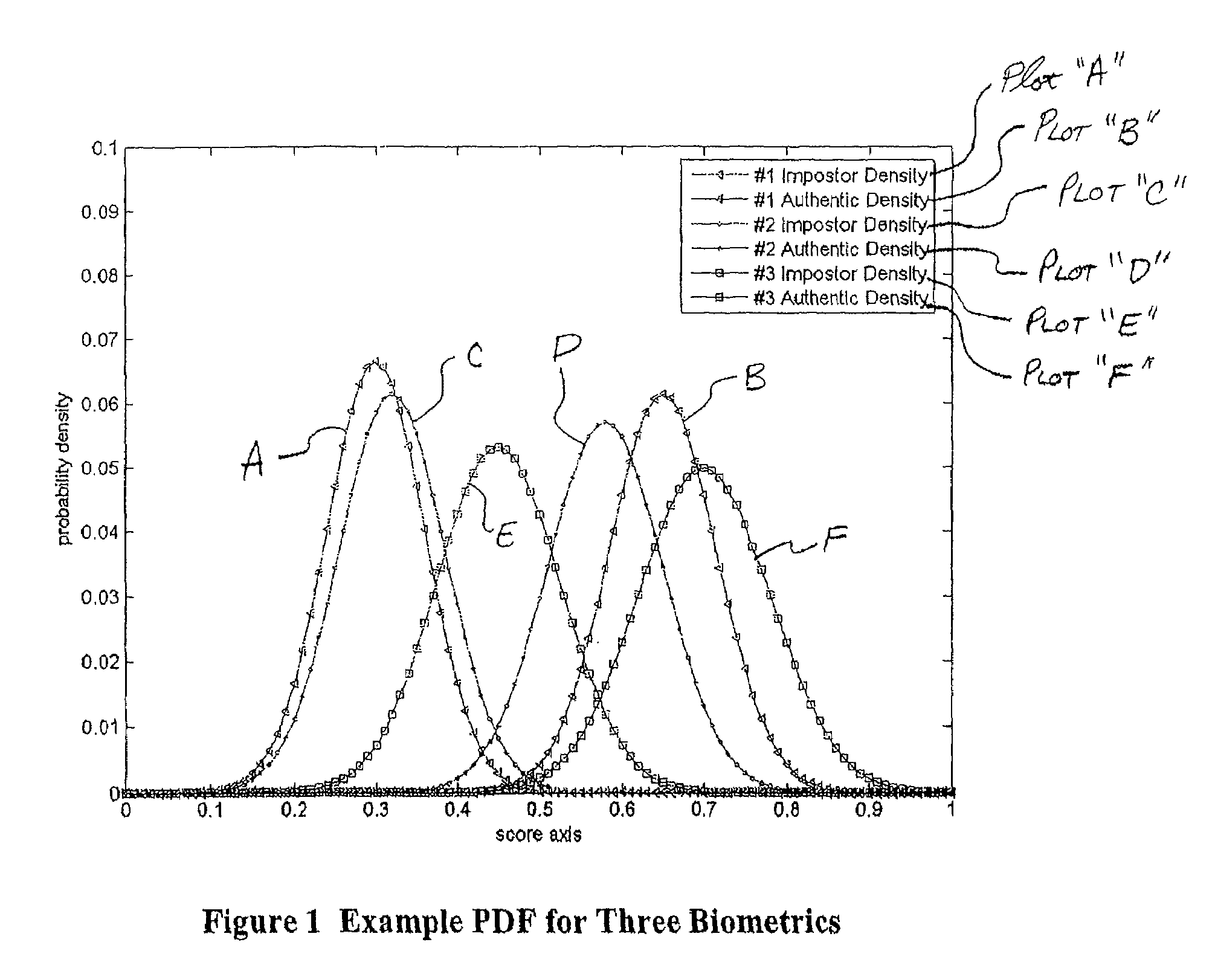
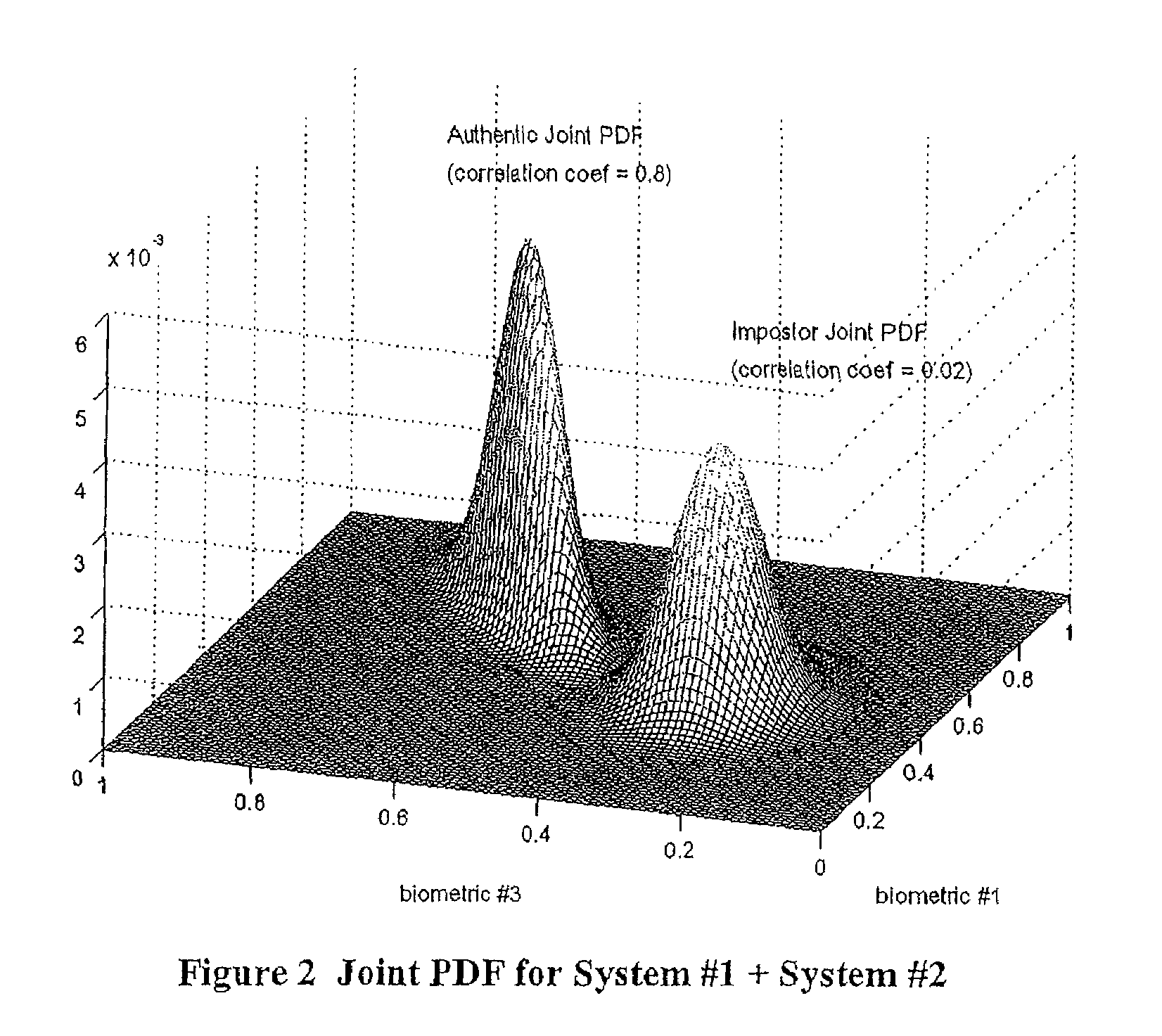
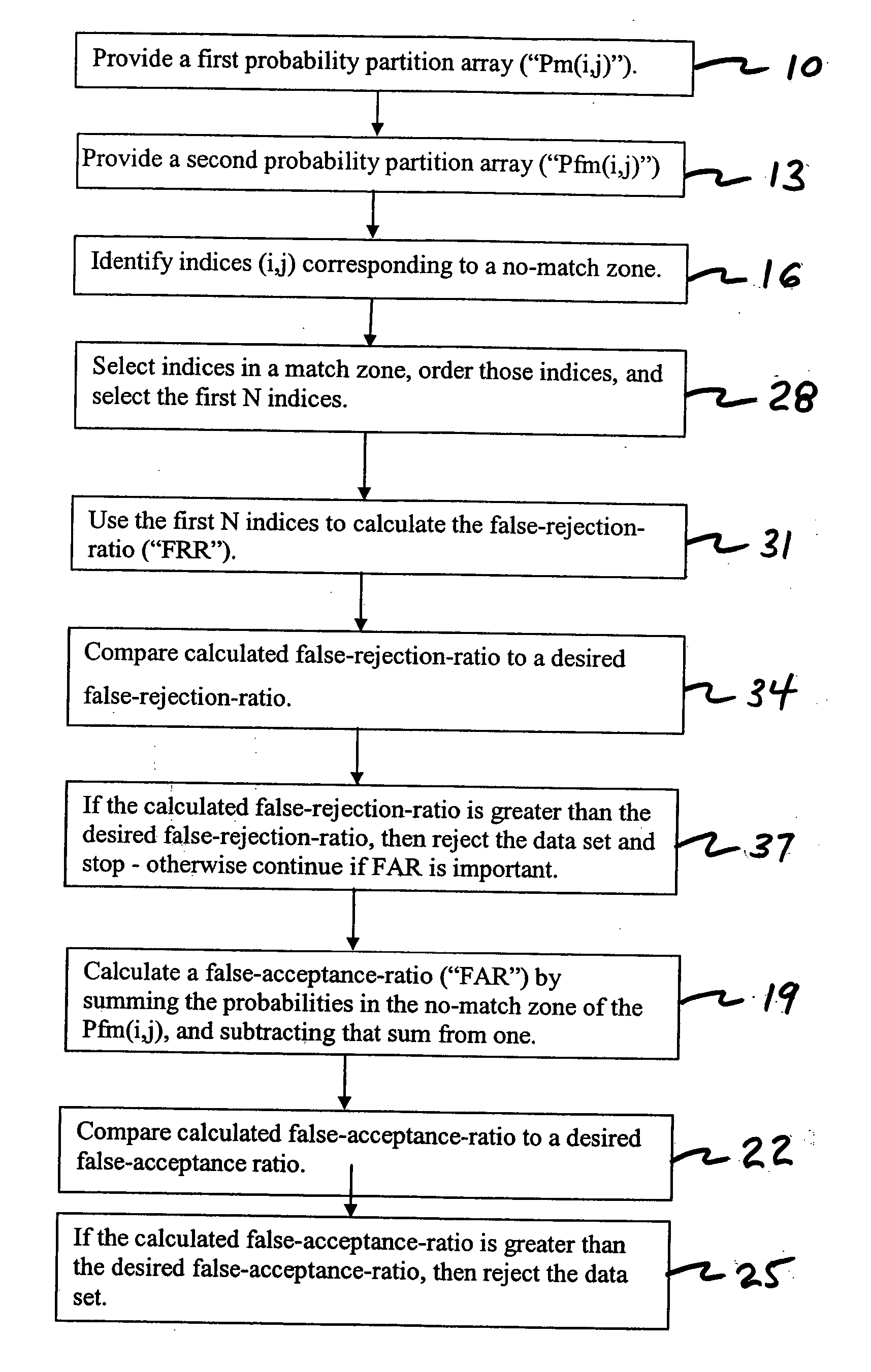
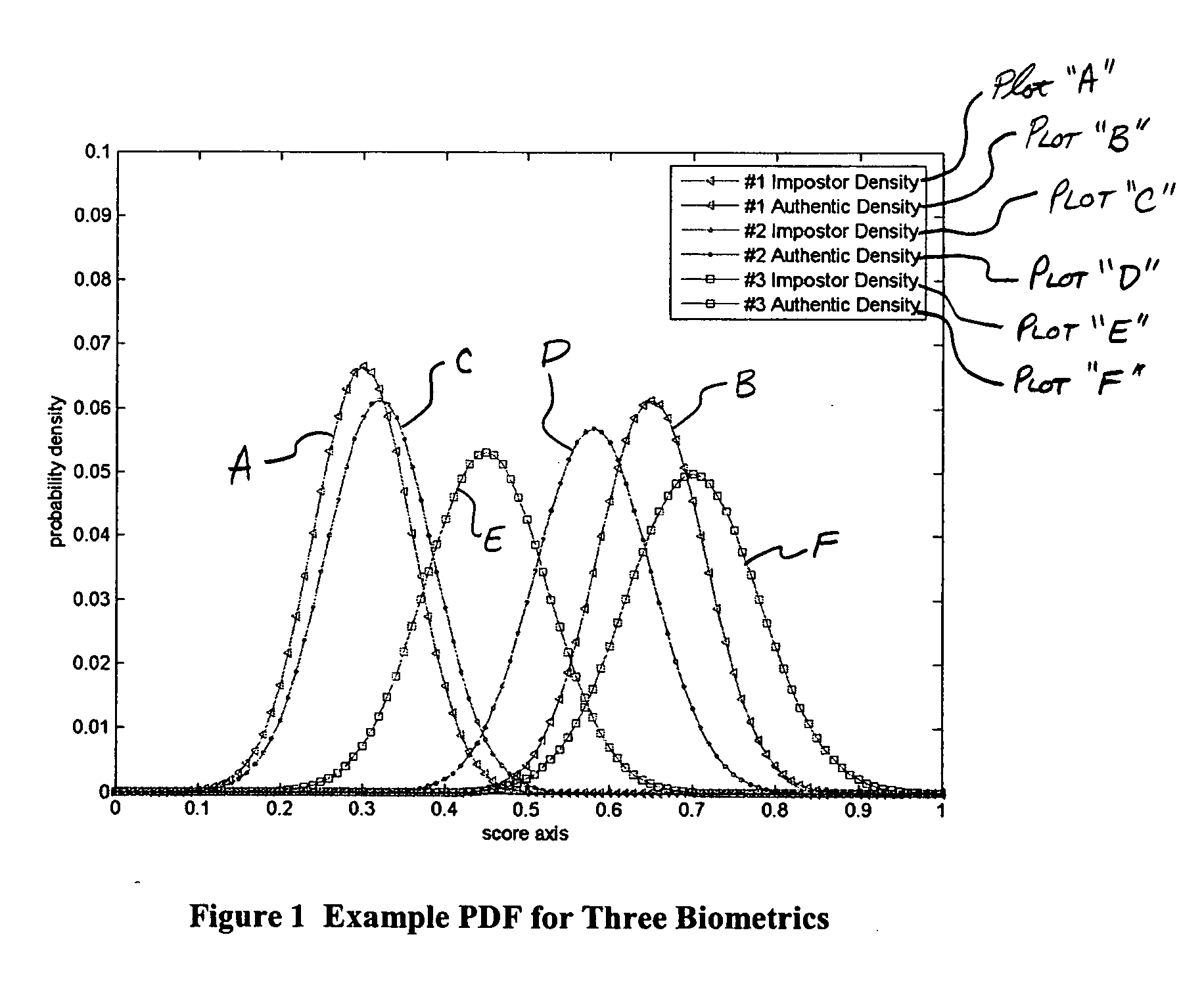
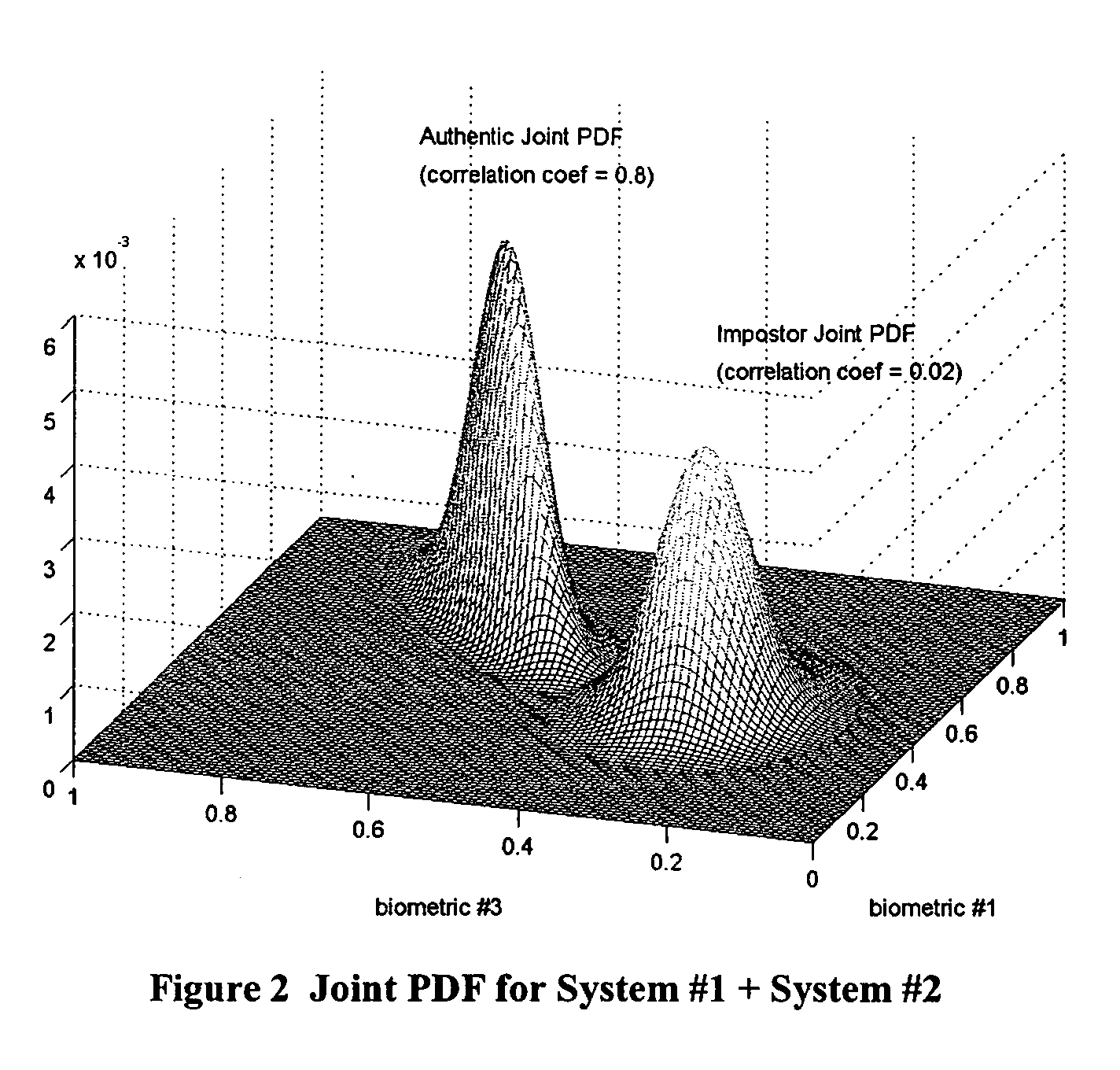
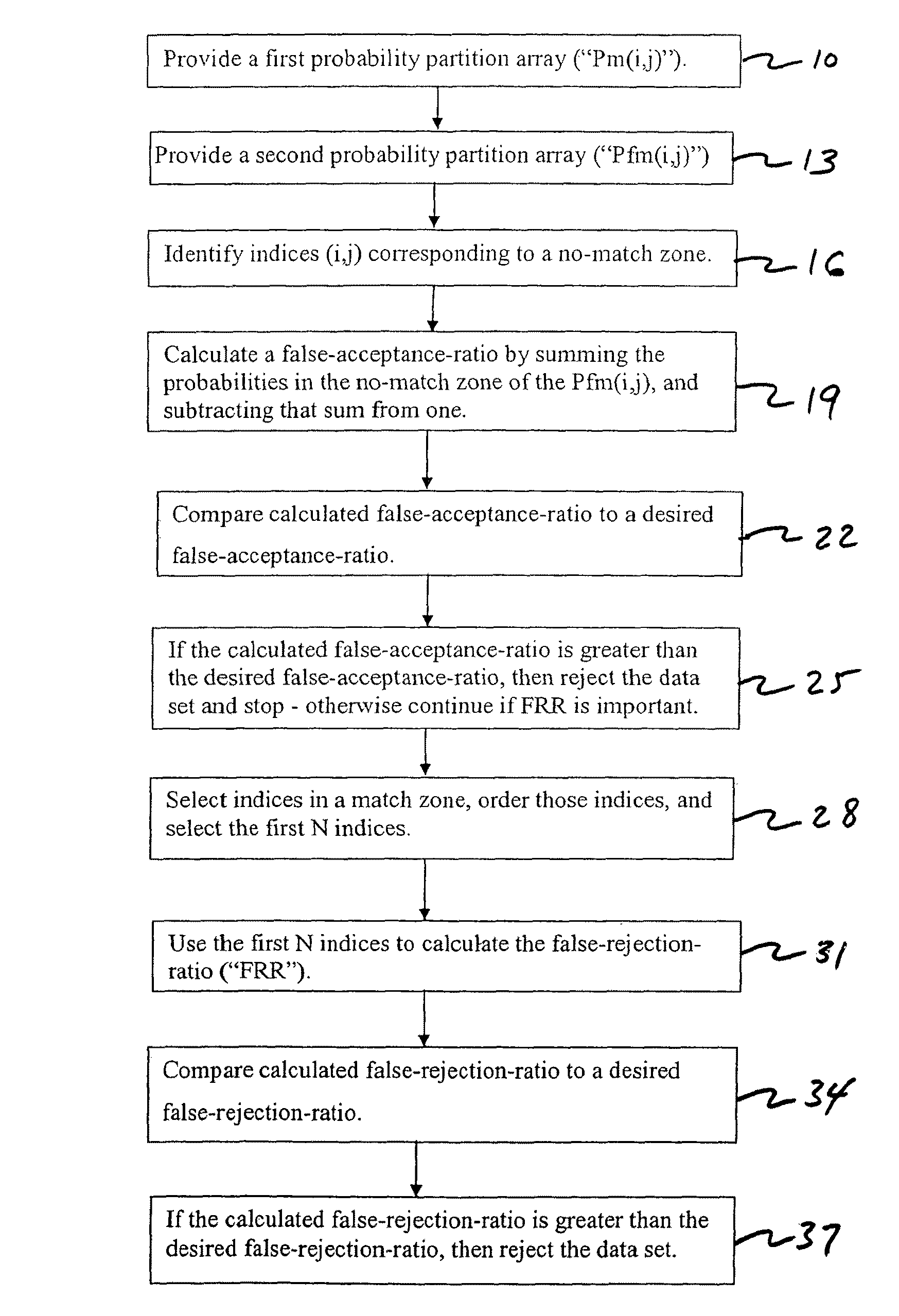
Multimodal Fusion Decision Logic System For Determining Whether To Accept A Specimen
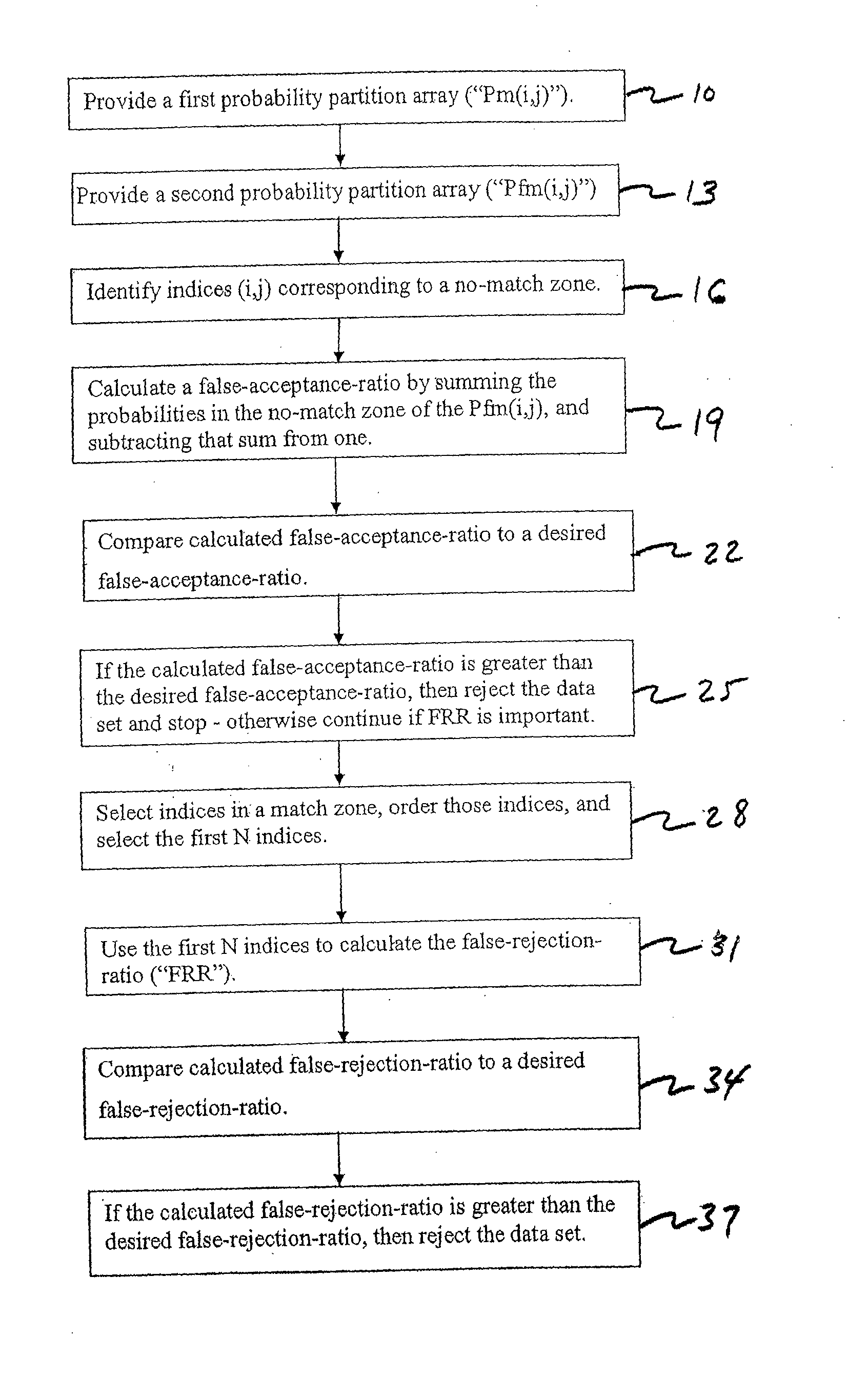
InactiveUS20090171623A1Mathematical modelsDigital data processing detailsData setFalse acceptance ratio
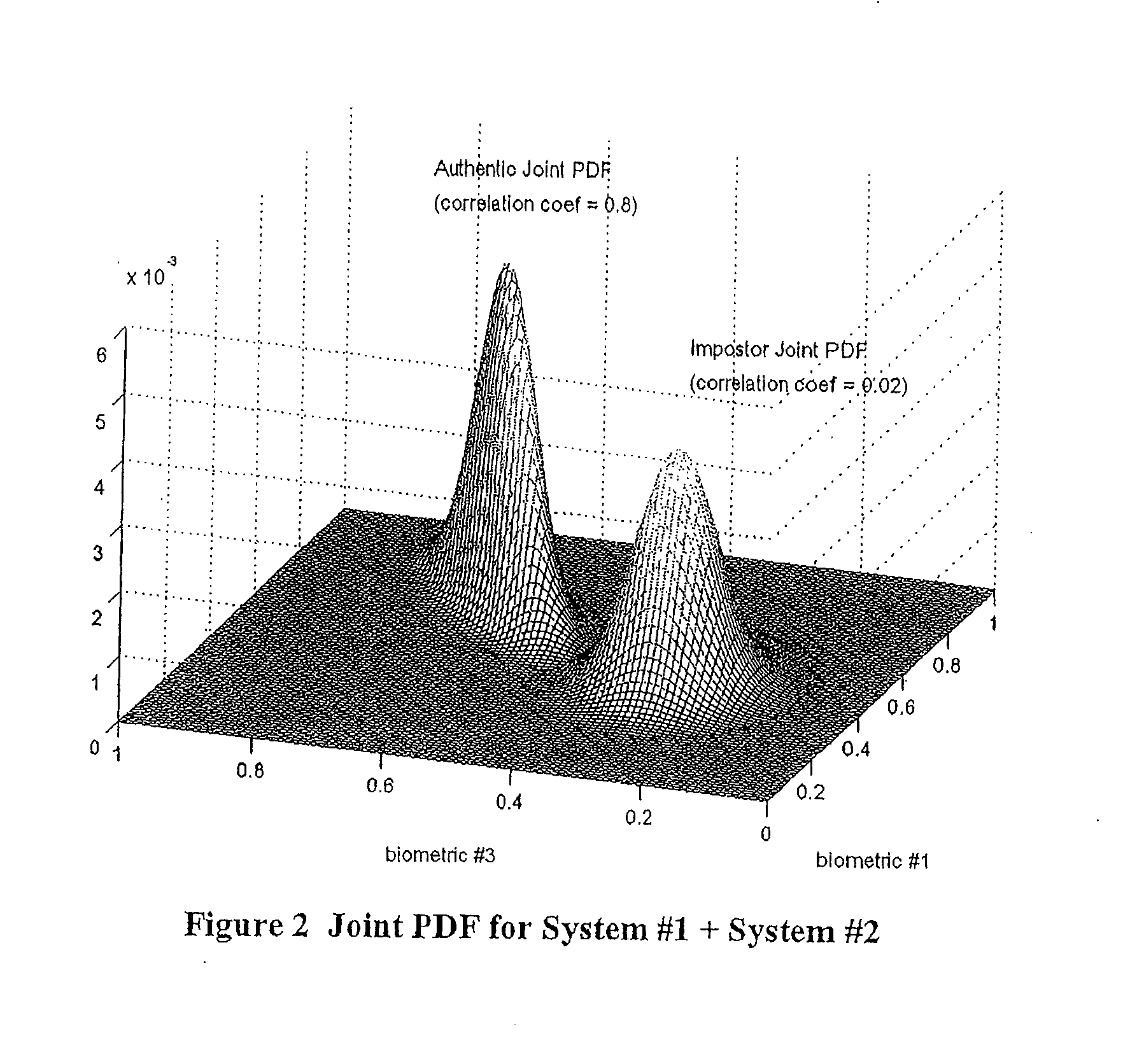
The present invention includes a method of deciding whether a data set is acceptable for making a decision. A first probability partition array and a second probability partition array may be provided. One or both of the probability partition arrays may be a Copula model. A no-match zone may be established and used to calculate a false-acceptance-rate (“FAR”) and / or a false-rejection-rate (“FRR”) for the data set. The FAR and / or the FAR may be compared to desired rates. Based on the comparison, the data set may be either accepted or rejected. The invention may also be embodied as a computer readable memory device for executing the methods.
Owner:QUALCOMM INC
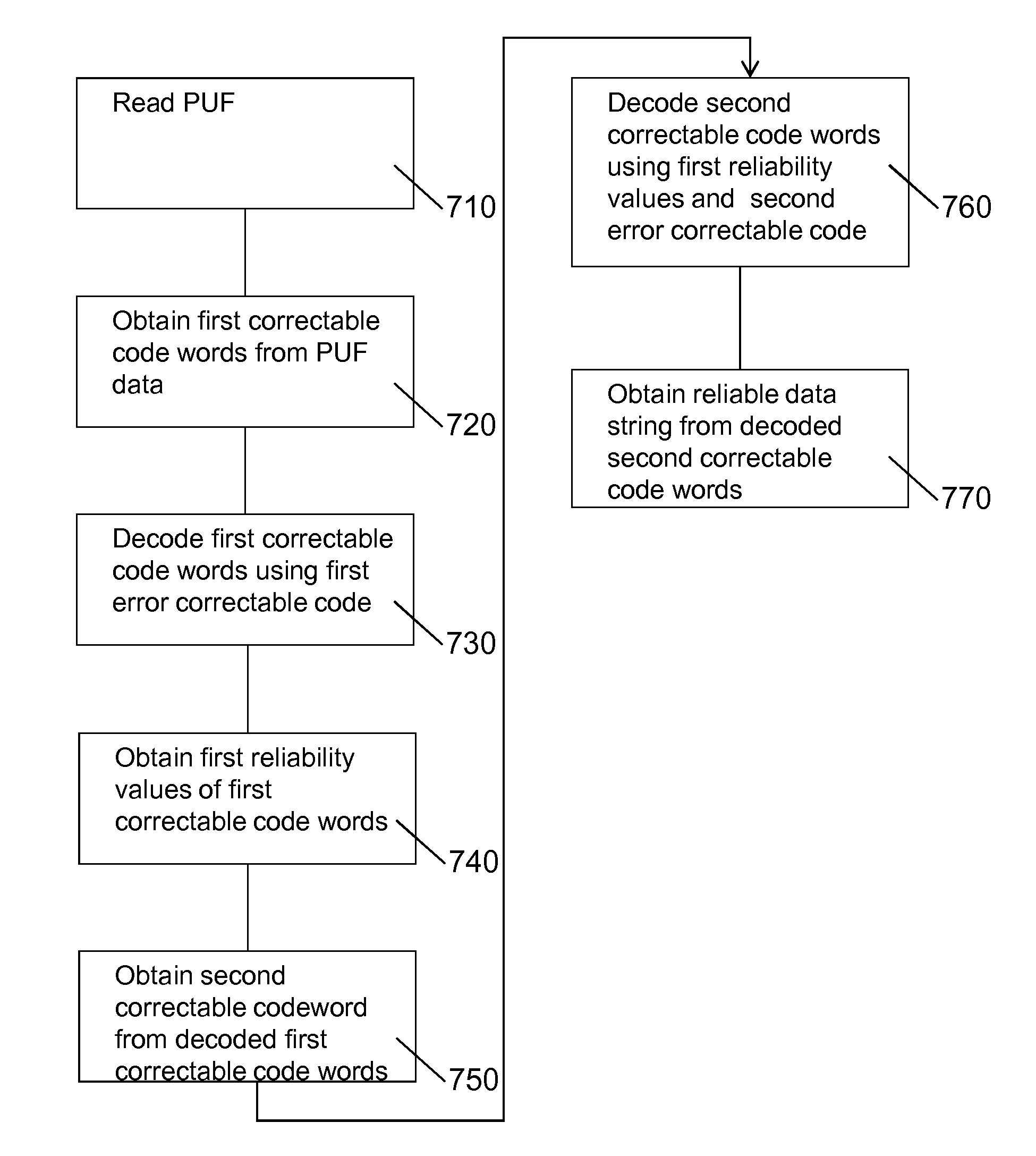
Physically unclonable function (PUF) with improved error correction
ActiveUS20140325237A1Avoid excessive errorMore informationUnauthorized memory use protectionHardware monitoringSoft-decision decoderDependability
A cryptographic system for reproducibly establishing a reliable data string, such as a cryptographic key, from a noisy physically unclonable function (PUF, 110) is provided. The system comprises a hard decision decoder (150) to decode a first multiple of error correctable data words to obtain a second multiple of corrected and decoded data words and a reliability information extractor (180) to determine reliability information, e.g. soft decision information, that is indicative of a reliability of corrected and decoded data words. The system further comprises a soft decision decoder (160) configured to use the reliability information to decode at least one further correctable data word. Error correcting a PUF using reliability information decreases the false rejection rate.
Owner:INTRINSIC ID
Multimodal fusion decision logic system
InactiveUS7287013B2Electric signal transmission systemsMultiple keys/algorithms usageData setComputer science
The present invention includes a method of deciding whether a data set is acceptable for making a decision. A first probability partition array and a second probability partition array may be provided. A no-match zone may be established and used to calculate a false-acceptance-rate (“FAR”) and / or a false-rejection-rate (“FRR”) for the data set. The FAR and / or the FAR may be compared to desired rates. Based on the comparison, the data set may be either accepted or rejected. The invention may also be embodied as a computer readable memory device for executing the methods.
Owner:QUALCOMM INC
Bioassay system based on iris texture analysis
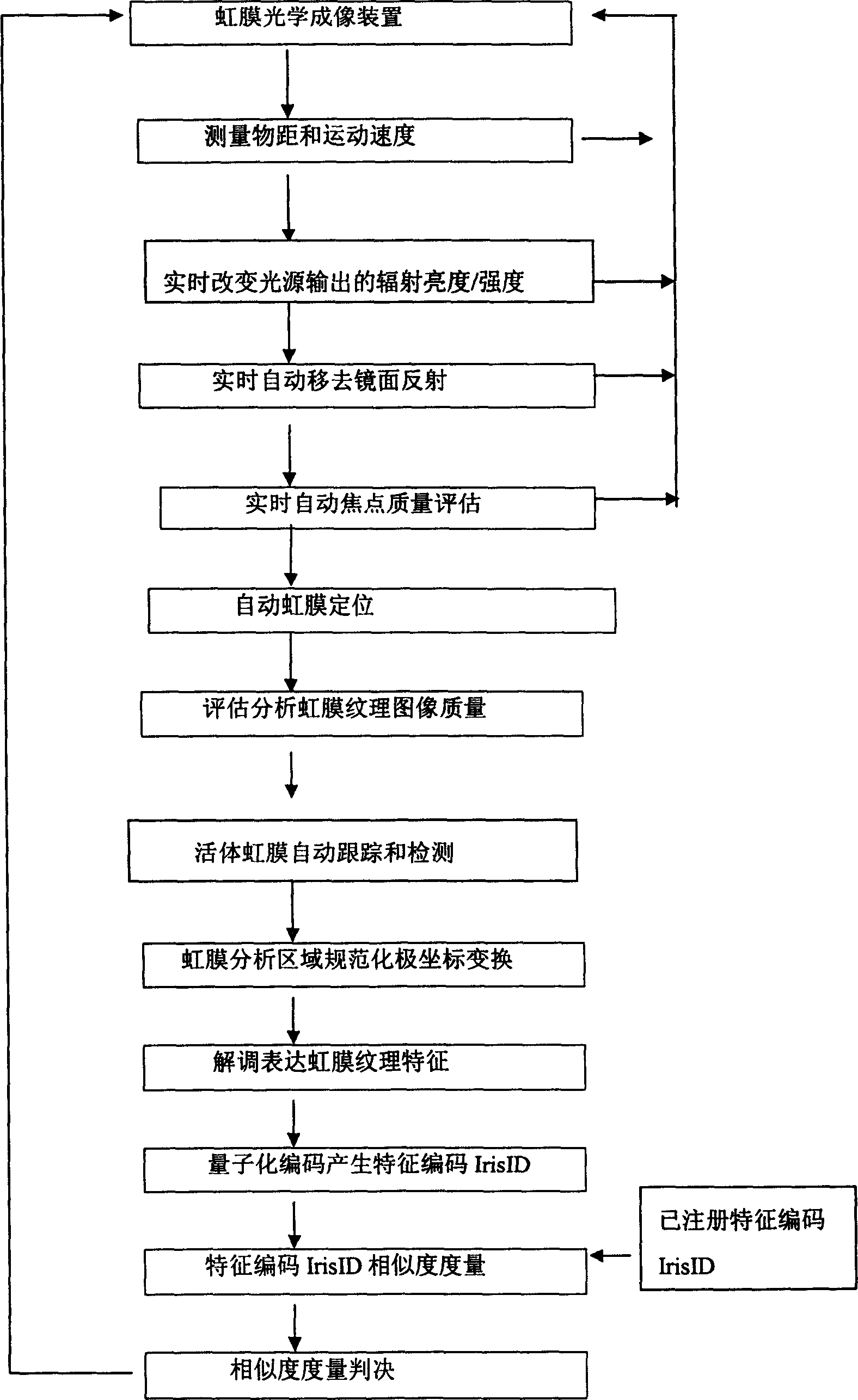
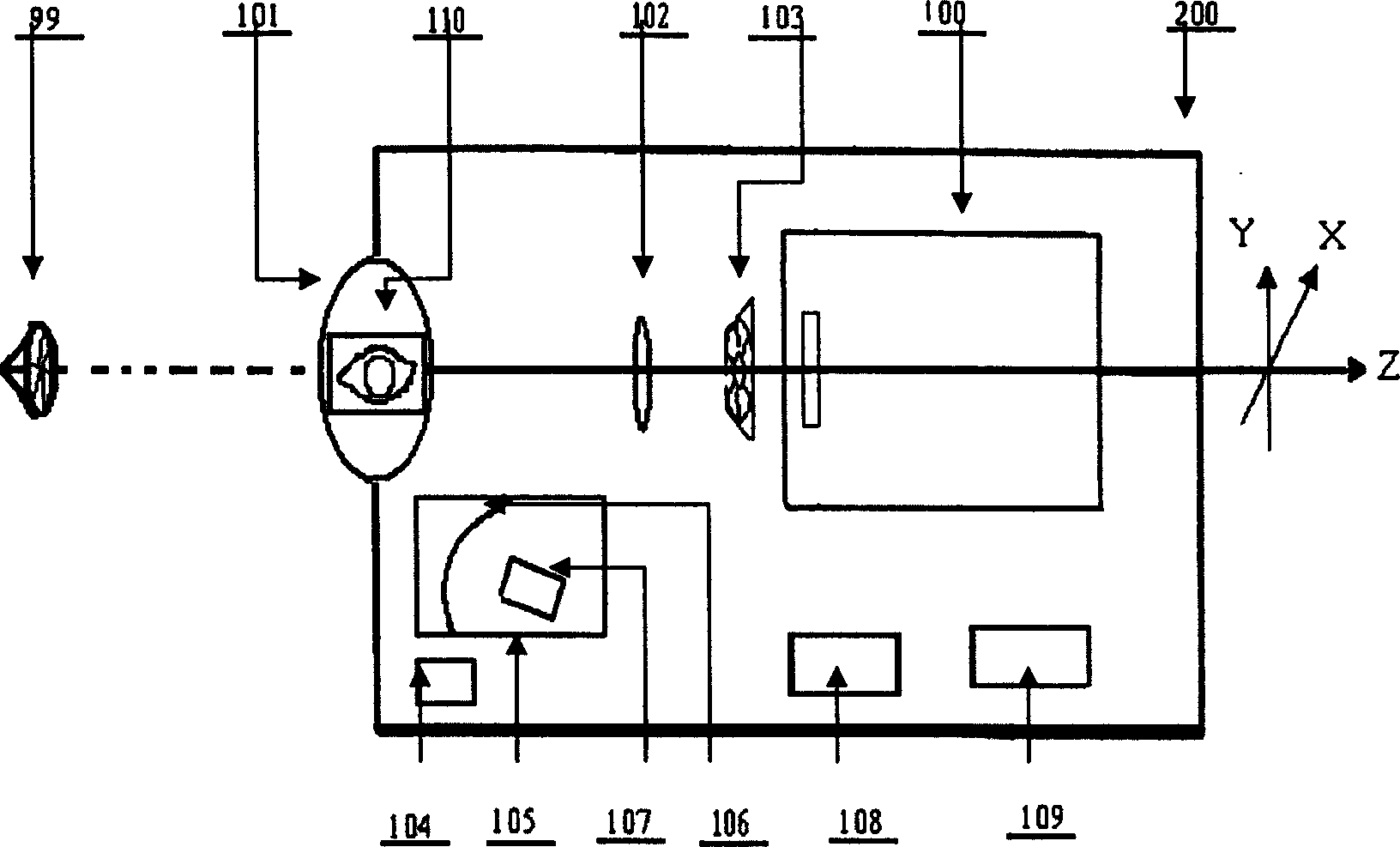
ActiveCN1623506AImprove qualityAvoid positioning failurePerson identificationCharacter and pattern recognitionImaging conditionNon invasive
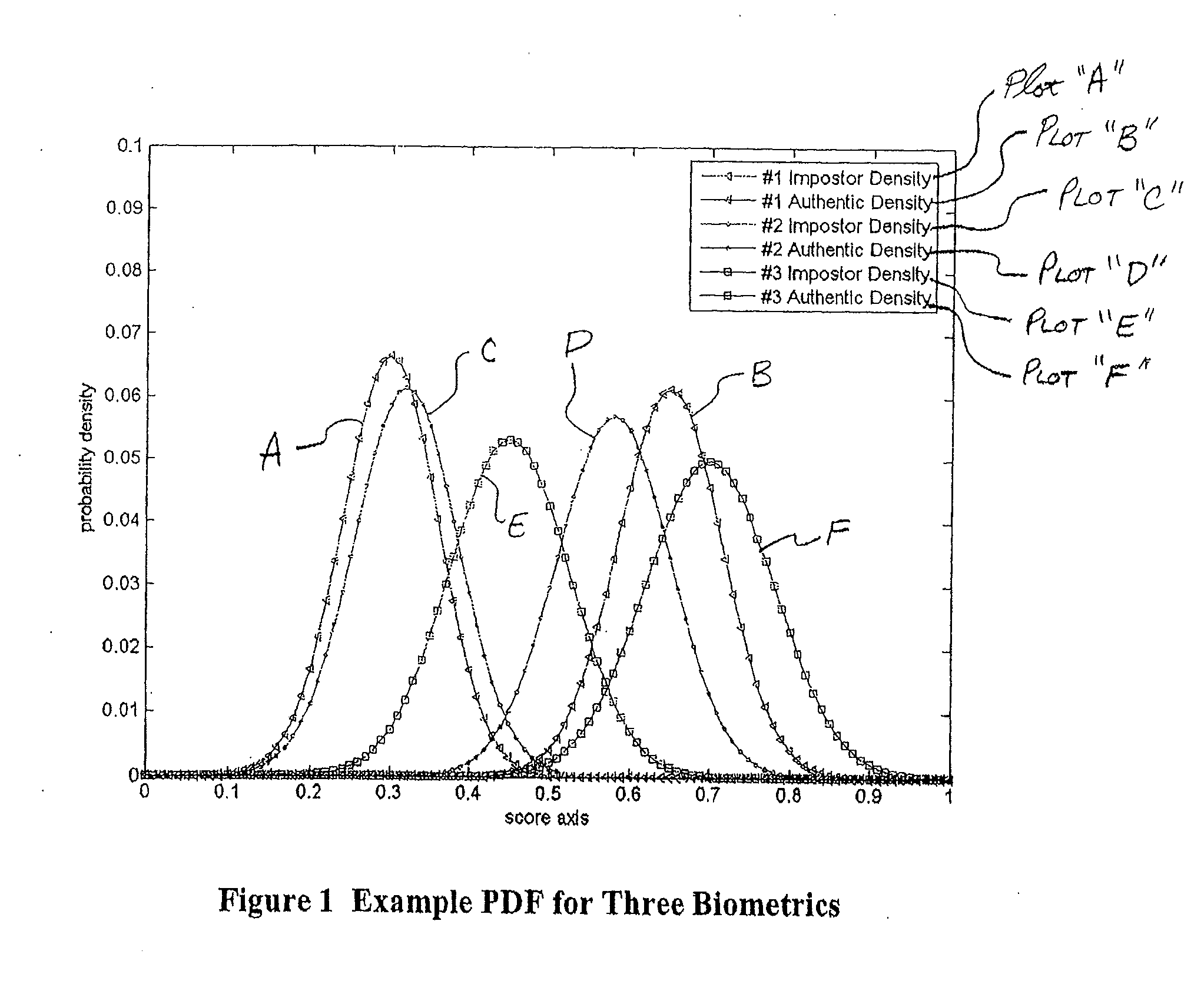
The invention is a biometric system based on iris texture analysis, which overcomes the defects in the prior art that lack the support of iris image quality analysis mechanism and cannot complete the evaluation of iris texture image quality. The invention acquires iris texture images, automatically locates iris, evaluates and analyzes the quality of iris texture images, automatically tracks and detects living iris, standardizes polar coordinate transformation of iris analysis area, demodulates and expresses iris texture features, and generates feature code IrisID by quantization coding. Encoding IrisID similarity measurement, similarity measurement judgment and other steps are realized. The invention realizes the basic characteristic requirements of an ideal system: automaticity, non-invasiveness, friendly man-machine operation interface and high-quality imaging image; no correlation between geometric affine transformation and nonlinear affine deformation; no dependence on external imaging conditions ; Random probability distribution coding; High-precision false acceptance rate and false rejection rate performance.
Owner:SUZHOU SIYUAN KEAN INFORMATION TECH
Multimodal Fusion Decision Logic System Using Copula Model
The present invention includes a method of deciding whether a data set is acceptable for making a decision. A first probability partition array and a second probability partition array may be provided. One or both of the probability partition arrays may be a Copula model. A no-match zone may be established and used to calculate a false-acceptance-rate (“FAR”) and / or a false-rejection-rate (“FRR”) for the data set. The FAR and / or the FAR may be compared to desired rates. Based on the comparison, the data set may be either accepted or rejected. The invention may also be embodied as a computer readable memory device for executing the methods.
Owner:QUALCOMM INC
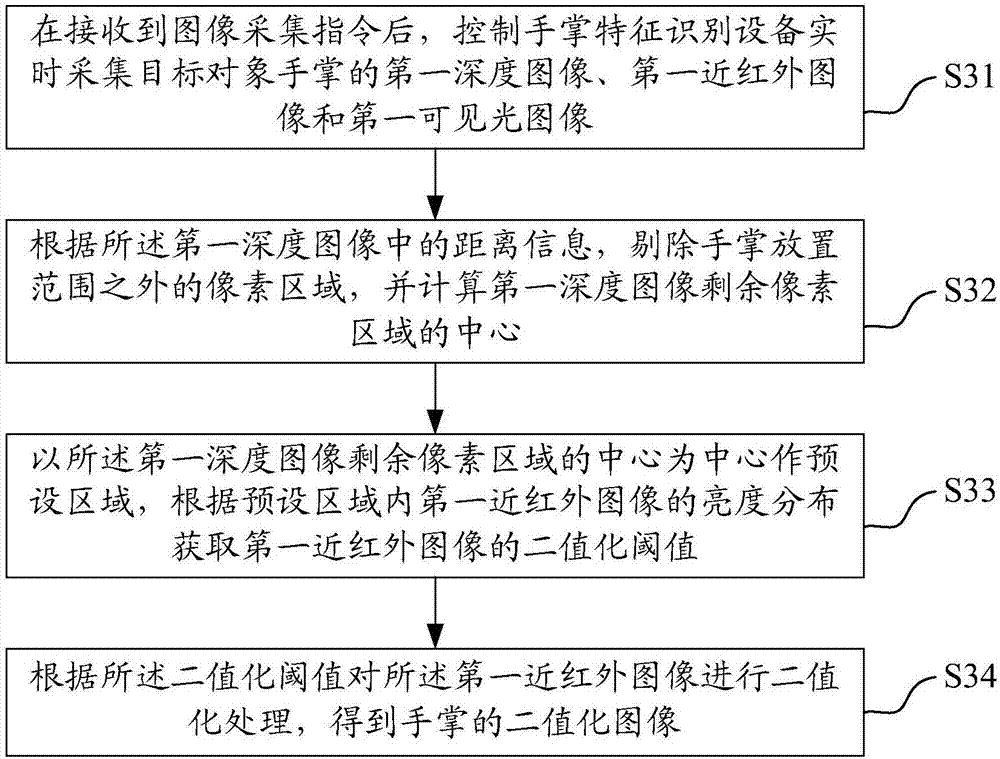
Palm feature identification method, palm feature identification device and storage medium
InactiveCN107341473AImprove stabilityImprove robustnessPrint image acquisitionMatching and classificationPattern recognitionPalm print
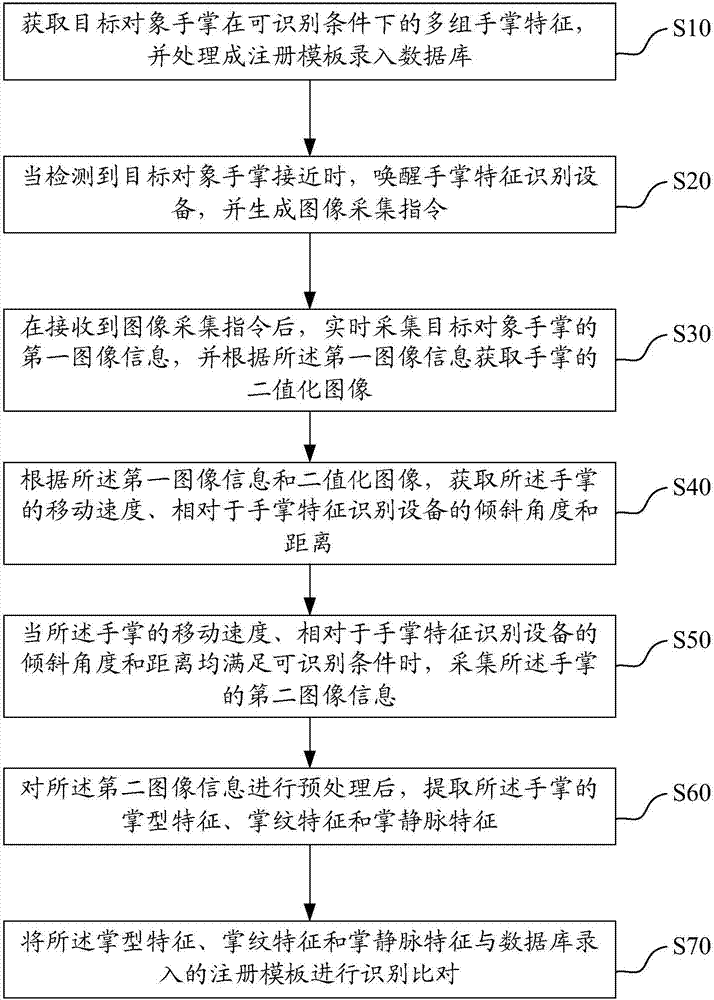
The invention provides a palm feature identification method, a palm feature identification device and a storage medium. The palm feature identification method comprises the following steps: after an image collection instruction is received, collecting first image information of a palm in real time, obtaining a binary image of the palm according to the first image information, then obtaining a moving speed of the palm and an inclination angle and distance of the palm relative to the palm feature identification device according to the first image information and the binary image, collecting second image information of the palm when an identifiable condition is satisfied, extracting a palm shape feature, a palm print feature and a palm vein feature of the palm after preprocessing the second image information, and finally performing identification and comparison on the palm shape feature, the palm print feature and the palm vein feature with a registration module recorded in a database. The problem that the identification error rate and the refusal error rate are relatively high caused by the movement and inclination of the palm is avoided, and the stability, robustness and accuracy of the identification are improved.
Owner:深圳市中识智能科技有限公司
Multimodal fusion decision logic system using copula model
The present invention includes a method of deciding whether a data set is acceptable for making a decision. A first probability partition array and a second probability partition array may be provided. One or both of the probability partition arrays may be a Copula model. A no-match zone may be established and used to calculate a false-acceptance-rate (“FAR”) and / or a false-rejection-rate (“FRR”) for the data set. The FAR and / or the FAR may be compared to desired rates. Based on the comparison, the data set may be either accepted or rejected. The invention may also be embodied as a computer readable memory device for executing the methods.
Owner:QUALCOMM INC
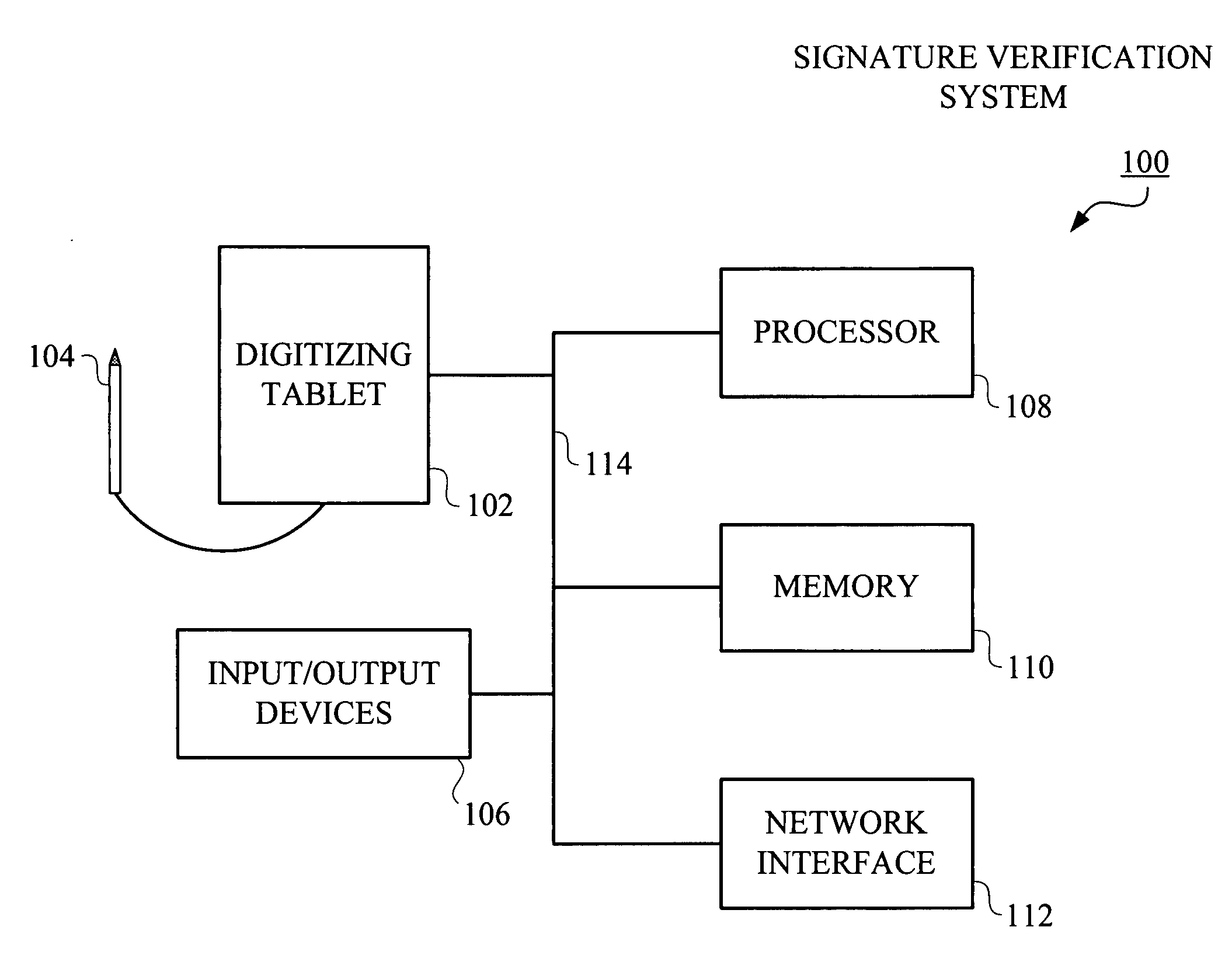
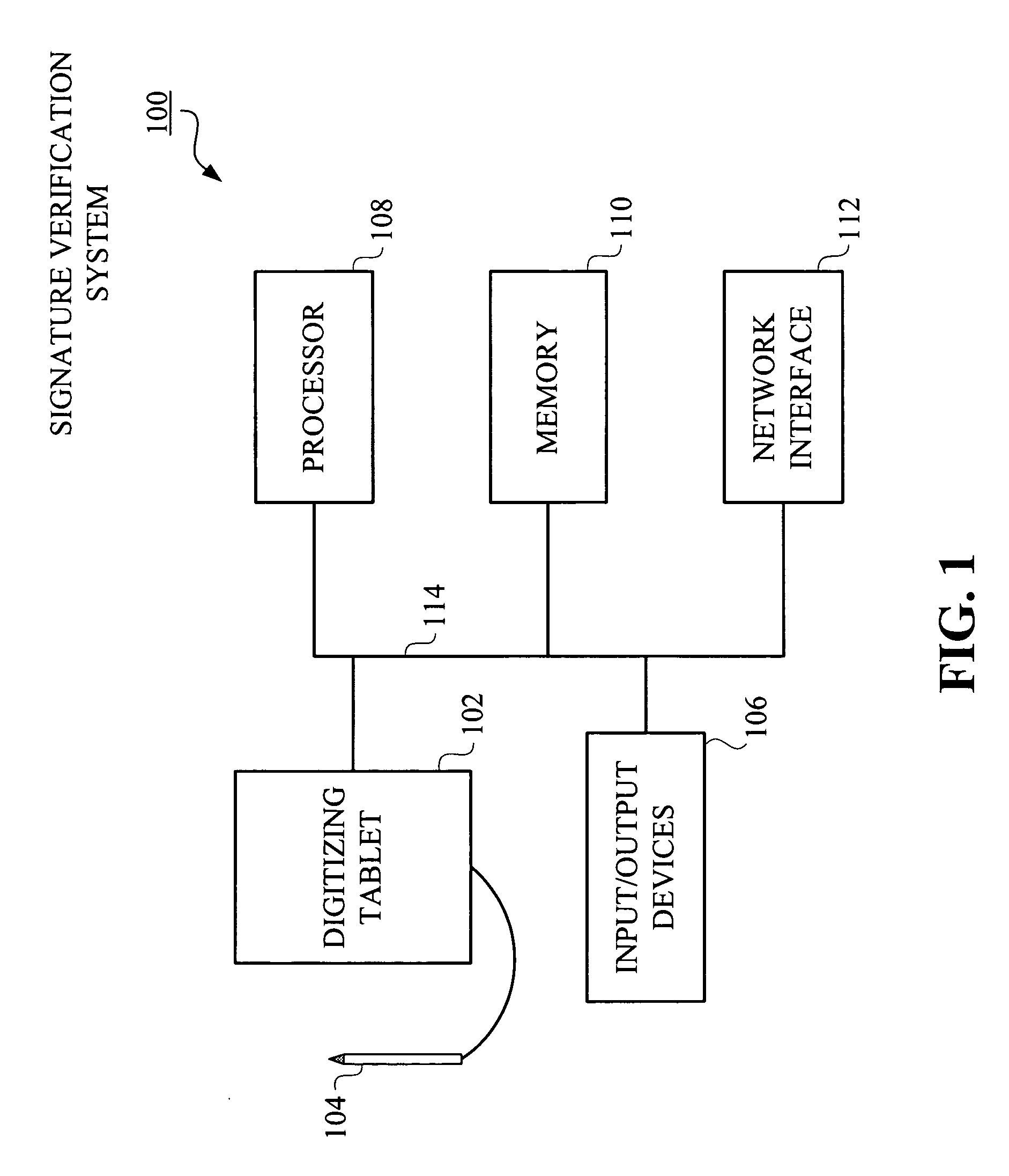
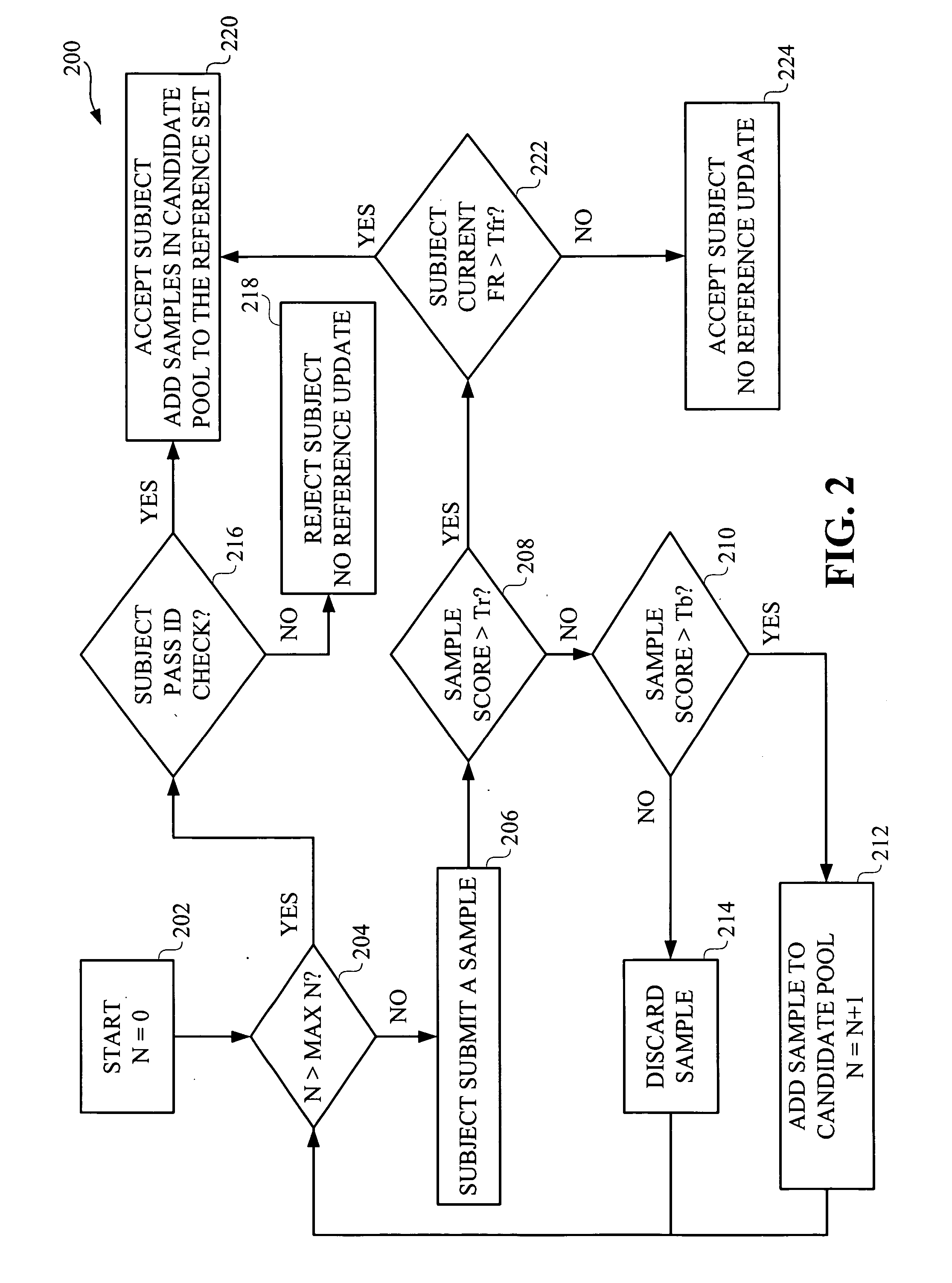
Method and apparatus for rolling enrollment for signature verification
InactiveUS20070177773A1Simple technologyCharacter and pattern recognitionDigital data authenticationVerification systemFalse rejection rate
Improved techniques are disclosed for adapting signature verification systems to natural signature variations. For example, a technique for adapting a signature verification system to variations in a signature of a user includes the following steps / operations. One or more signature samples are obtained from the user. The one or more obtained signature samples are submitted by the user as part of a regular authentication procedure associated with the signature verification system. A reference set of signature samples for the user is updated through selection of one or more signature samples from the obtained signature samples, such that the updated reference set is usable by the signature verification system for verifying subsequent signature samples attributed to the user. The selection of the one or more signature samples used to update the reference set is conditioned on a false rejection rate of the user when at least one obtained signature sample of the user is authenticated and on an identification check when no obtained signature sample is authenticated.
Owner:IBM CORP
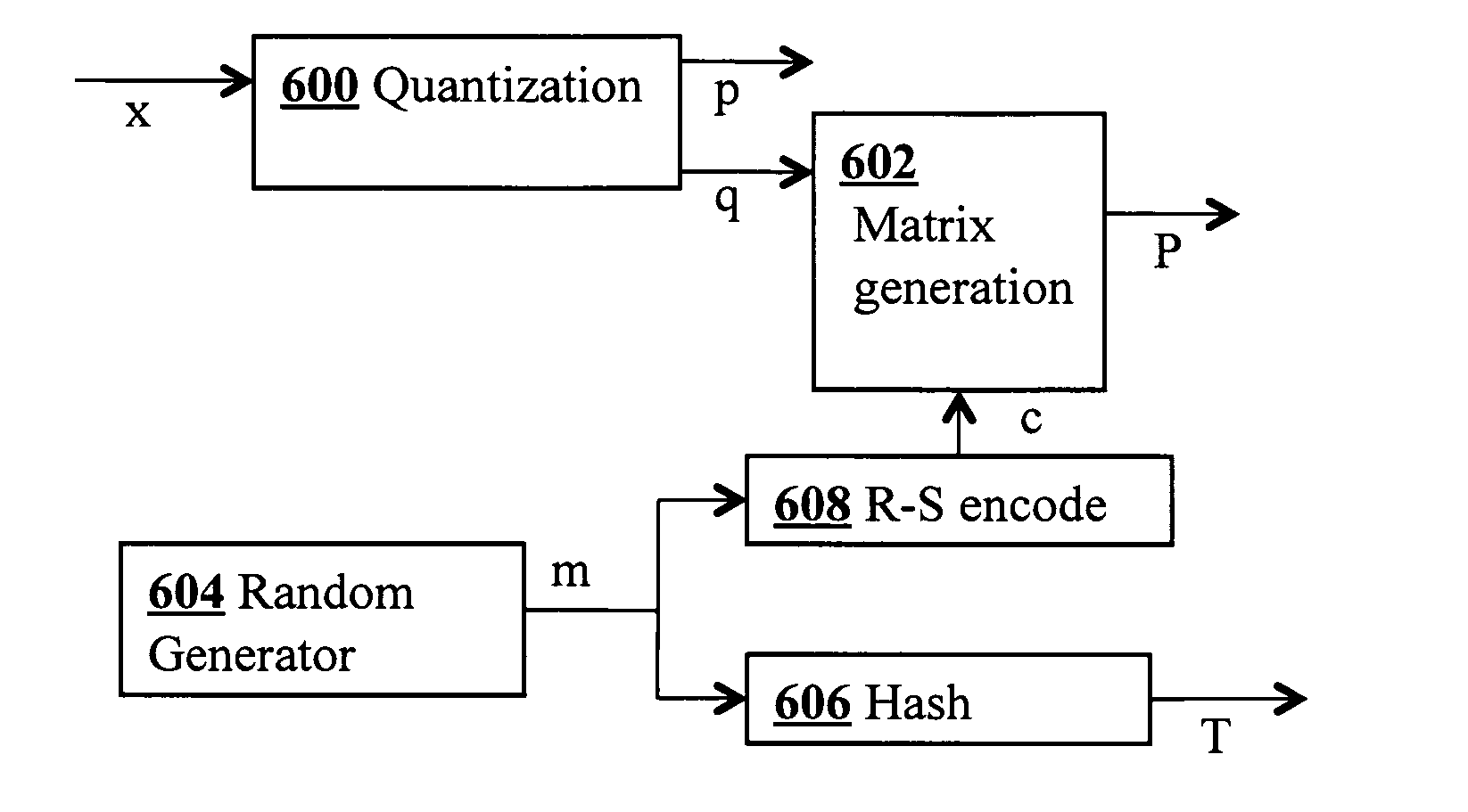
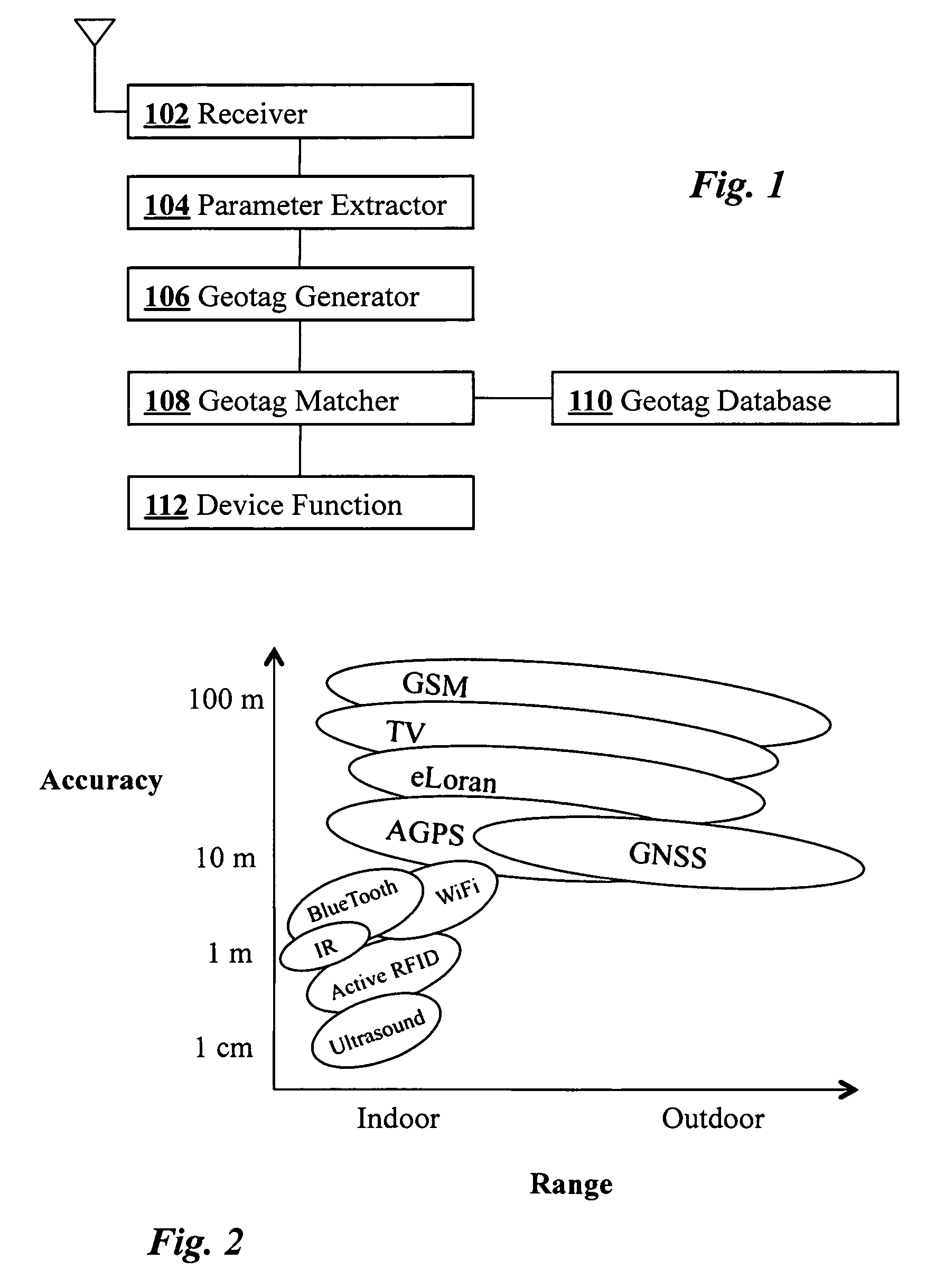
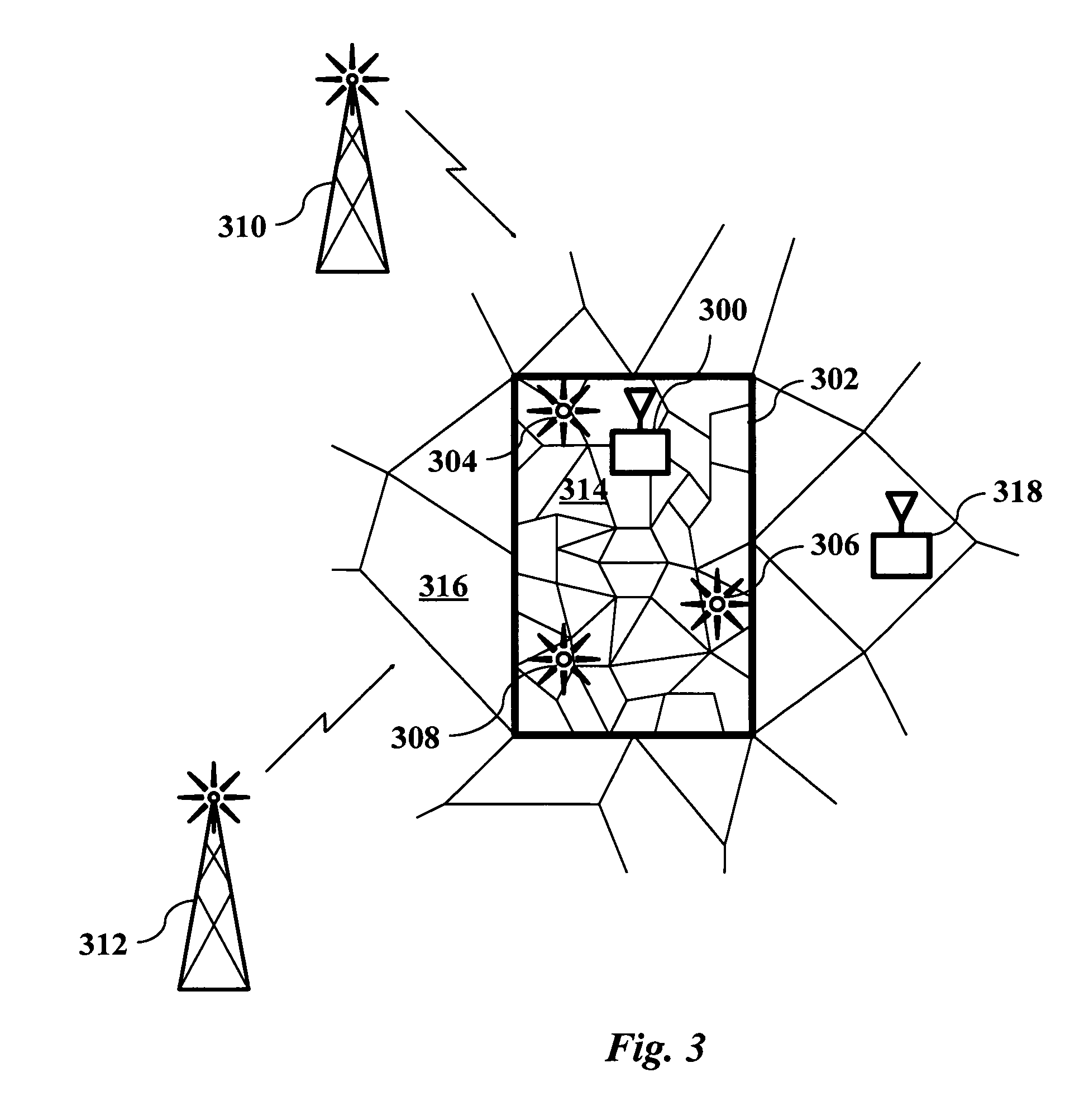
Geosecurity methods and devices using geotags derived from noisy location data from multiple sources
InactiveUS8315389B2Reduce rateImprove securityPosition fixationSecret communicationAlgorithmPosition dependent
In a geo-security system, a device receives RF signals from multiple distinct classes of RF communication systems and extracts location-dependent signal parameters. A current geotag is computed from the parameters by fuzzy extractors involving quantization of the parameters and Reed-Solomon decoding to provide a reproducible unique geotag. The current geotag is compared with a stored geotag, and a geo-secured function of the device is executed based on the result of the comparison. The use of multiple signal sources of different types, combined with special fuzzy extractors provides a robust geotag that allows both lower false rejection rate and lower false acceptance rate.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Multiple registered fingerprint fusing method
InactiveCN1588425AImprove performanceIncreased false acceptance rateCharacter and pattern recognitionPattern recognitionFalse rejection rate
The invention is a multi-register fingerprint identification method belonging to fingerprint identification technology. its character lies in: it carries detail comparison to M fingerprints of the same finger in the databank, works out its similarity, and a excellent parameter is worked out according to the similarity, selects the maximal one as basic fingerprint, and it is copied onto the template; the other fingerprint is compared with its detail points, amends the confidence value of detail point according to the times of success comparisons, and a integral template is acquired; then carries tactics integration and finally integration matching with traditional detail joint character, acquires the similarity between the registered fingerprint and applied fingerprint. Compared with pure detail joint method, it reduces the error refusing rate.
Owner:TSINGHUA UNIV
Iris image data processing for use with iris recognition system
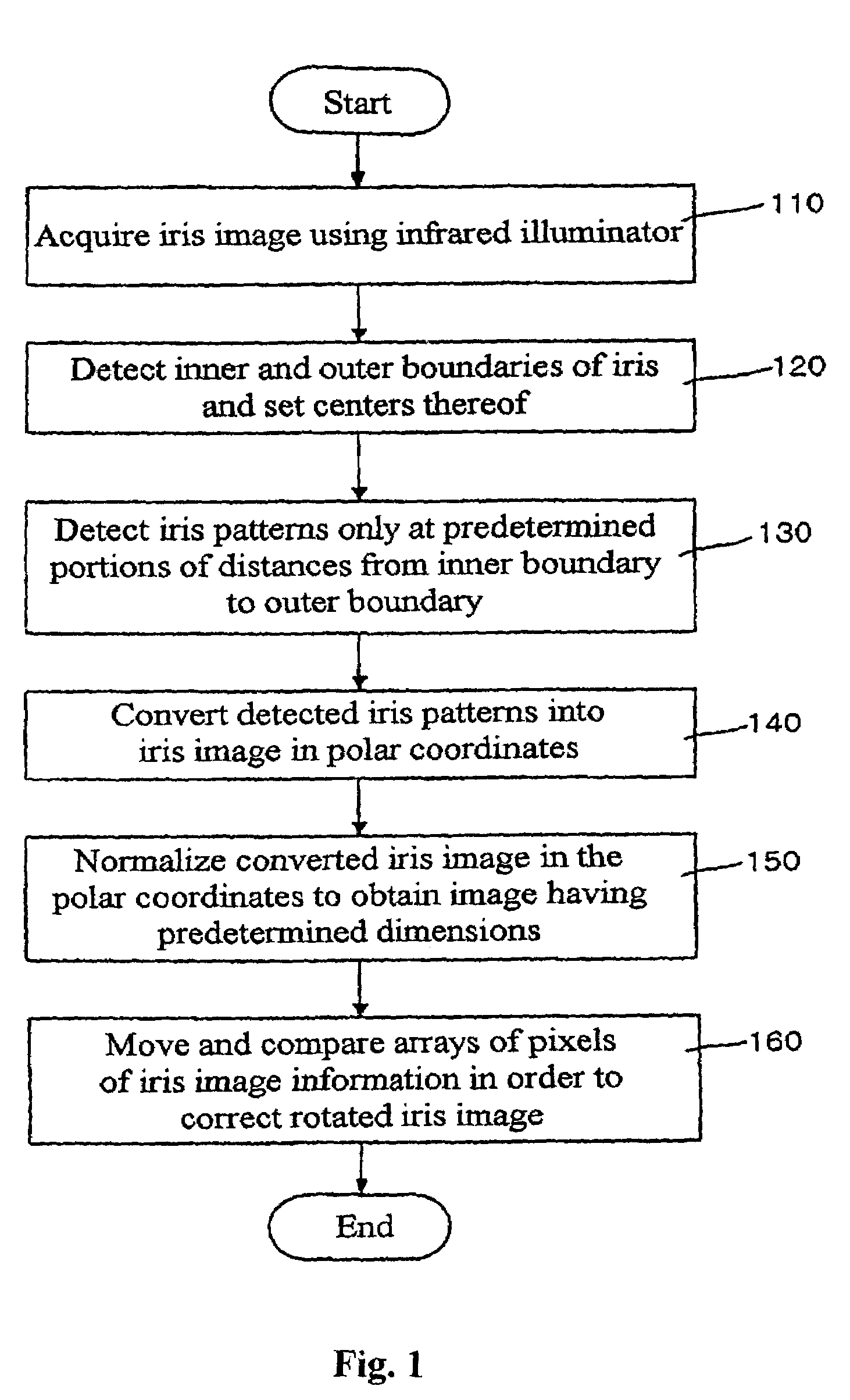
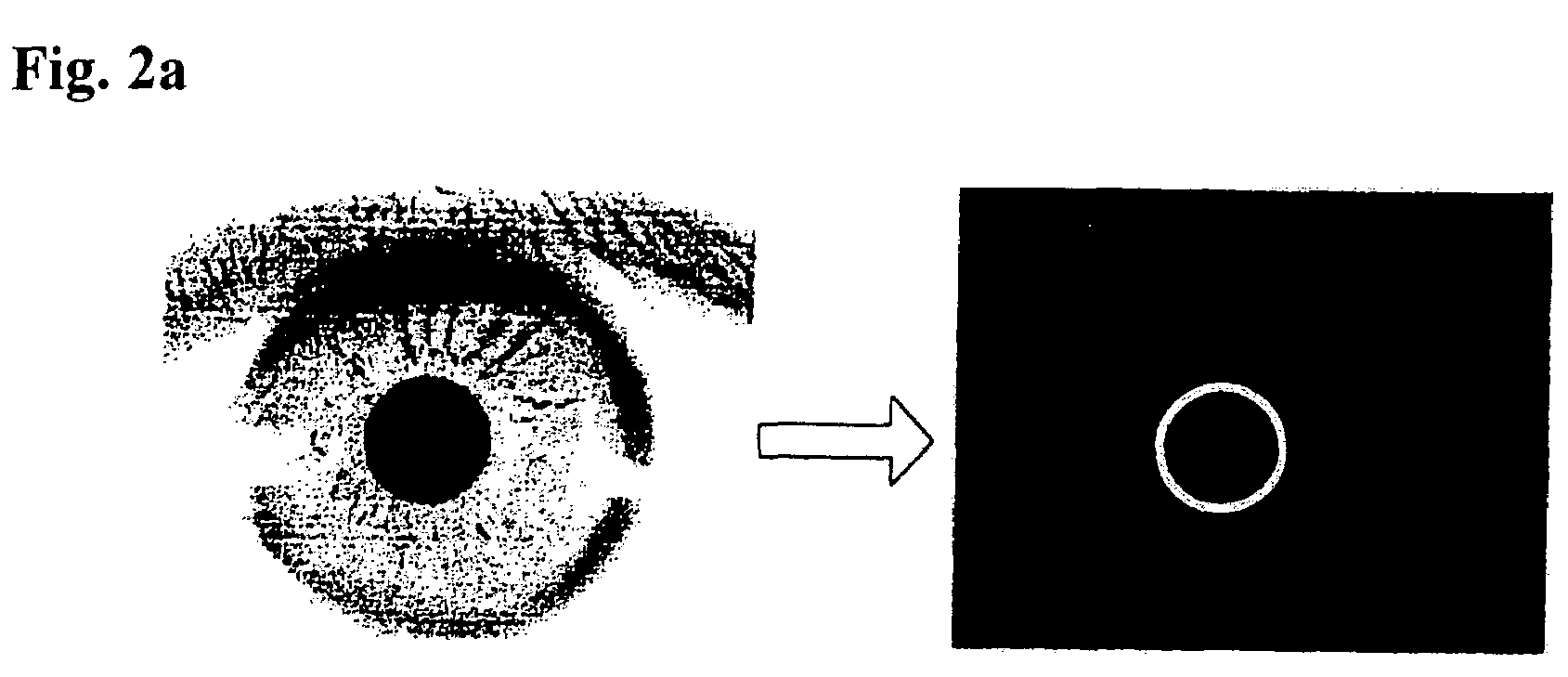
InactiveUS7298874B2Reduce rateImage analysisGeometric image transformationIris imageCanny edge detector
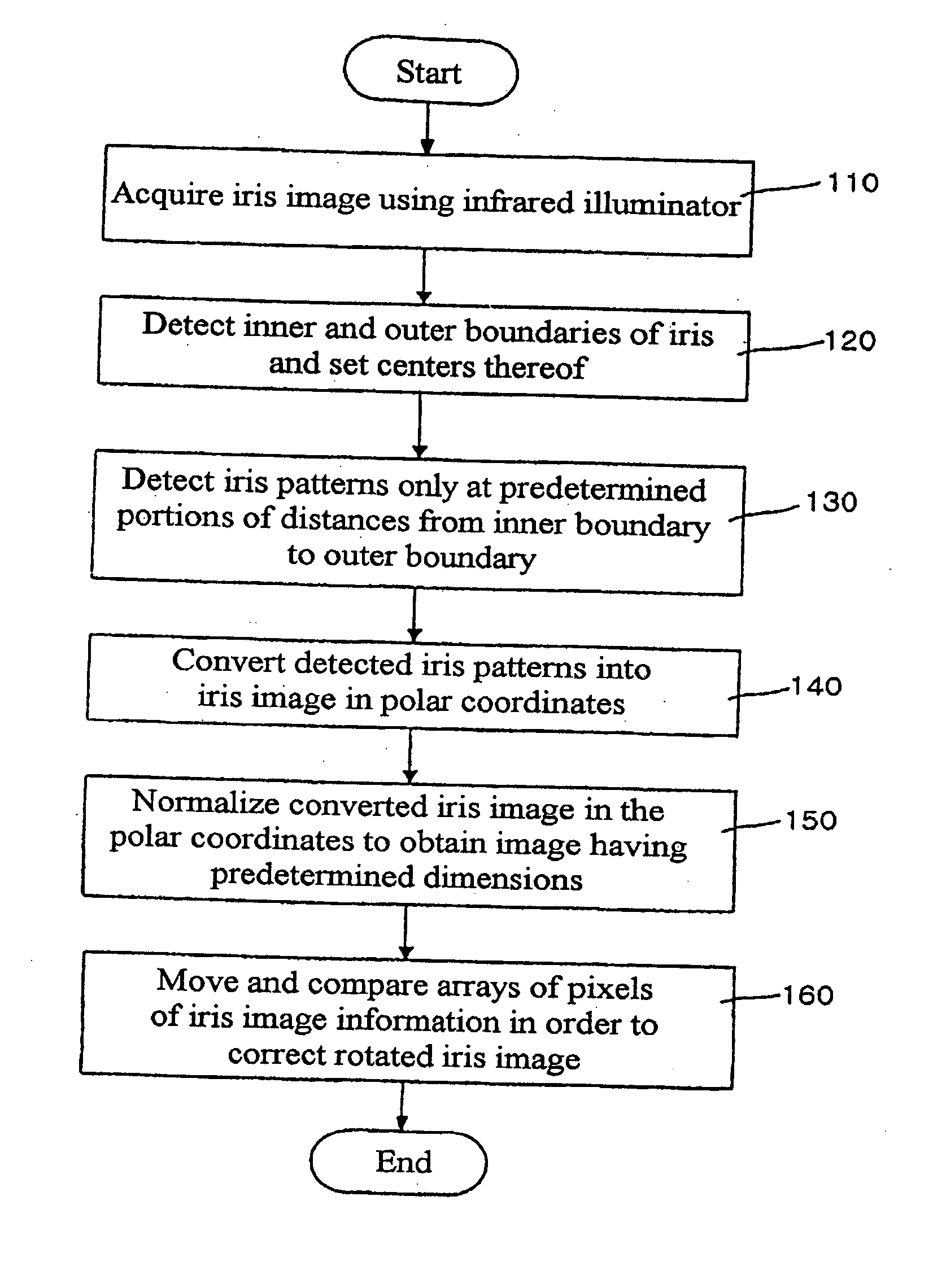
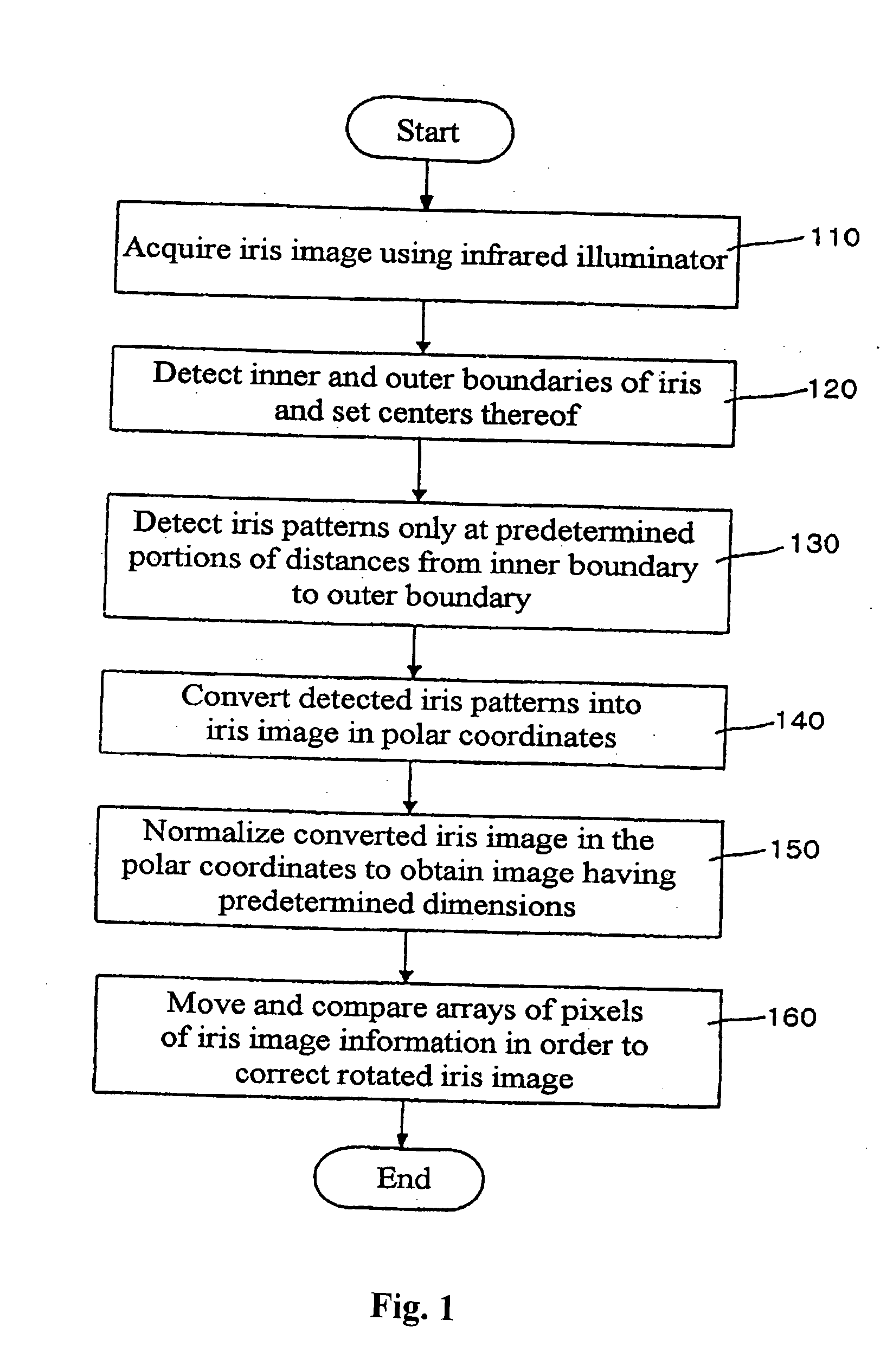
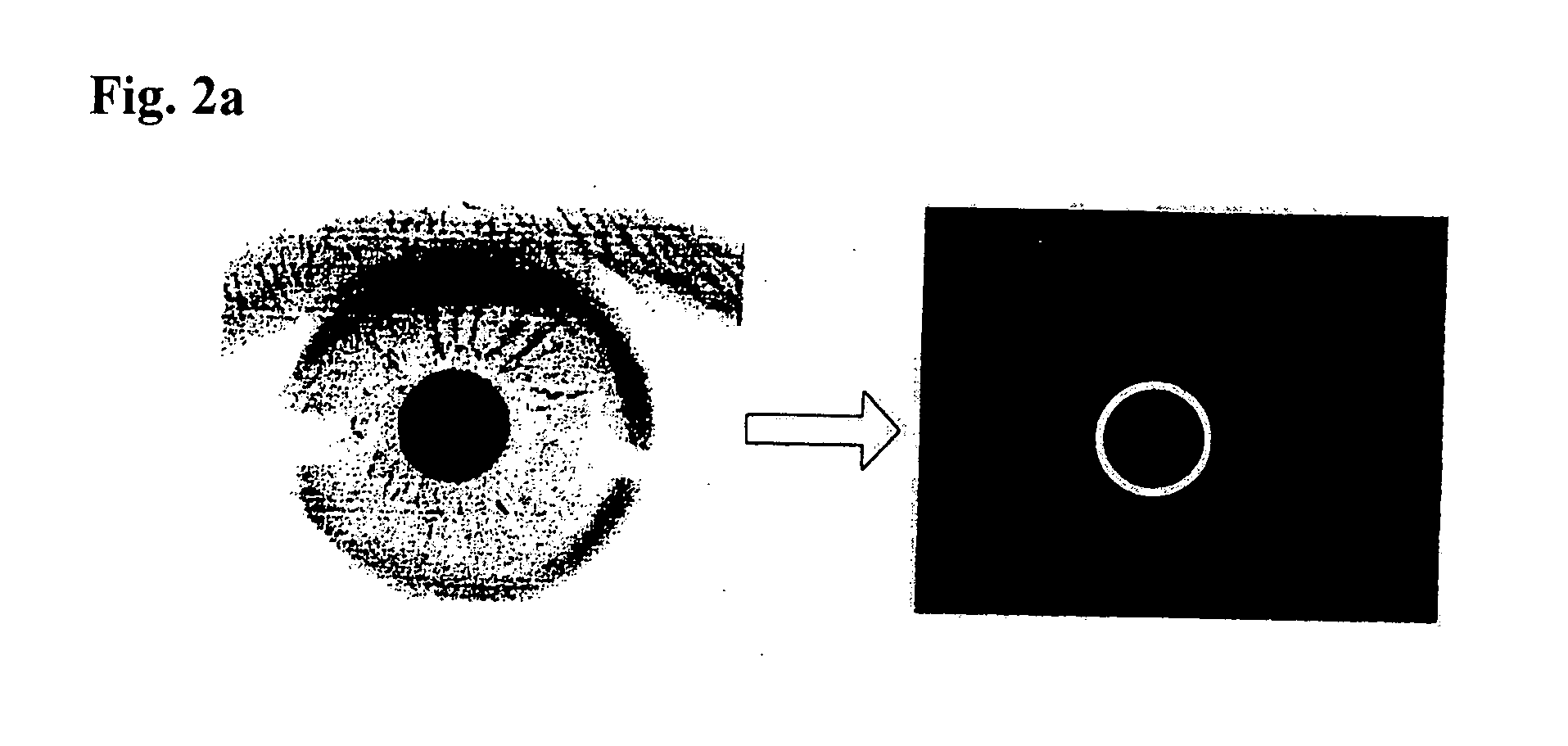
The present invention relates to an iris recognition method which is one of biometric technologies. According to a non-contact-type human iris recognition method by correction of a rotated iris image of the present invention, the iris image is acquired by image acquisition equipment using an infrared illuminator. Inner and outer boundaries of the iris are detected by analyzing differences in pixels of a Canny edge detector and the image for the inputted iris image, so as to allow the boundaries of the iris to be more accurately detected from the eye image of a user. Thus, the iris image with a variety of deformation can be processed into a correct iris image, so that there is an advantage in that a false acceptance rate and a false rejection rate can be markedly reduce.
Owner:SENGA ADVISORS LLC +1
Multimodal fusion decision logic system
InactiveUS20060204049A1Electric signal transmission systemsMultiple keys/algorithms usageData setComputer science
The present invention includes a method of deciding whether a data set is acceptable for making a decision. A first probability partition array and a second probability partition array may be provided. A no-match zone may be established and used to calculate a false-acceptance-rate (“FAR”) and / or a false-rejection-rate (“FRR”) for the data set. The FAR and / or the FAR may be compared to desired rates. Based on the comparison, the data set may be either accepted or rejected. The invention may also be embodied as a computer readable memory device for executing the methods.
Owner:QUALCOMM INC
Multimodal fusion decision logic system for determining whether to accept a specimen
The present invention includes a method of deciding whether a data set is acceptable for making a decision. A first probability partition array and a second probability partition array may be provided. One or both of the probability partition arrays may be a Copula model. A no-match zone may be established and used to calculate a false-acceptance-rate (“FAR”) and / or a false-rejection-rate (“FRR”) for the data set. The FAR and / or the FAR may be compared to desired rates. Based on the comparison, the data set may be either accepted or rejected. The invention may also be embodied as a computer readable memory device for executing the methods.
Owner:QUALCOMM INC
Biological identification method and terminal
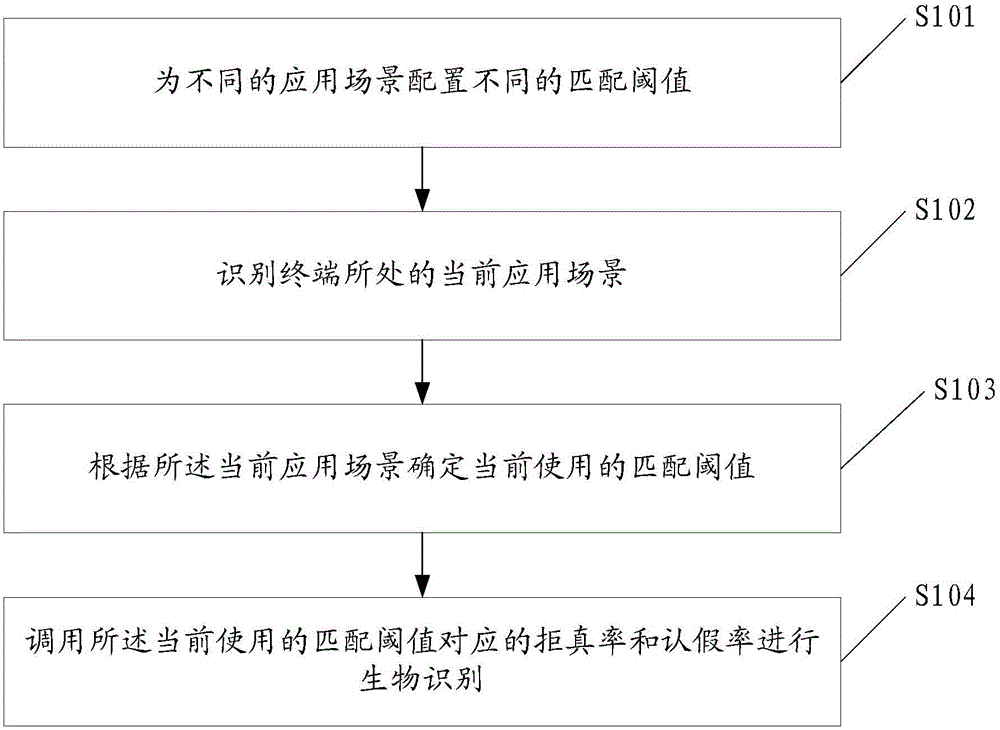
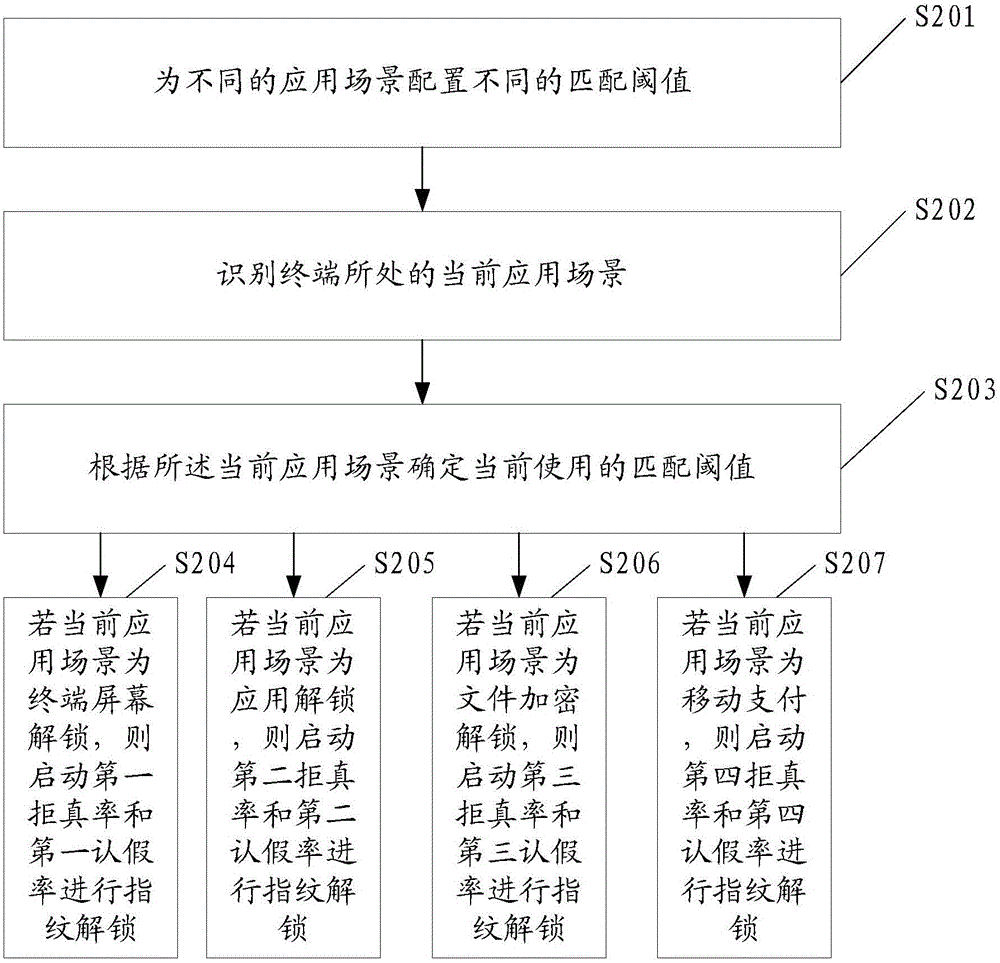
ActiveCN106096539AImprove applicabilityHigh speedMultiple biometrics useComputer terminalArtificial intelligence
The embodiments of the invention disclose a biological identification method and a terminal. The method comprises the following steps: configuring different matched thresholds for different application scenes, wherein the matched thresholds are used for representing a matching degree of biological identification, and each matched threshold is corresponding to one false rejection rate and one fault acceptance rate; identifying a current application scene where a terminal is disposed; according to the current application scene, determining a currently used matched threshold; and invoking the false rejection rate and the fault acceptance rate corresponding to the currently used matched threshold for the biological identification. By use of the method and the terminal, the applicability of the terminal can be improved, and user demands in the different application scenes can be satisfied.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Intelligent analysis system for flow abnormity of power automation system
InactiveCN102122374ARich solutionAdd supportData processing applicationsEarly warning systemService flow
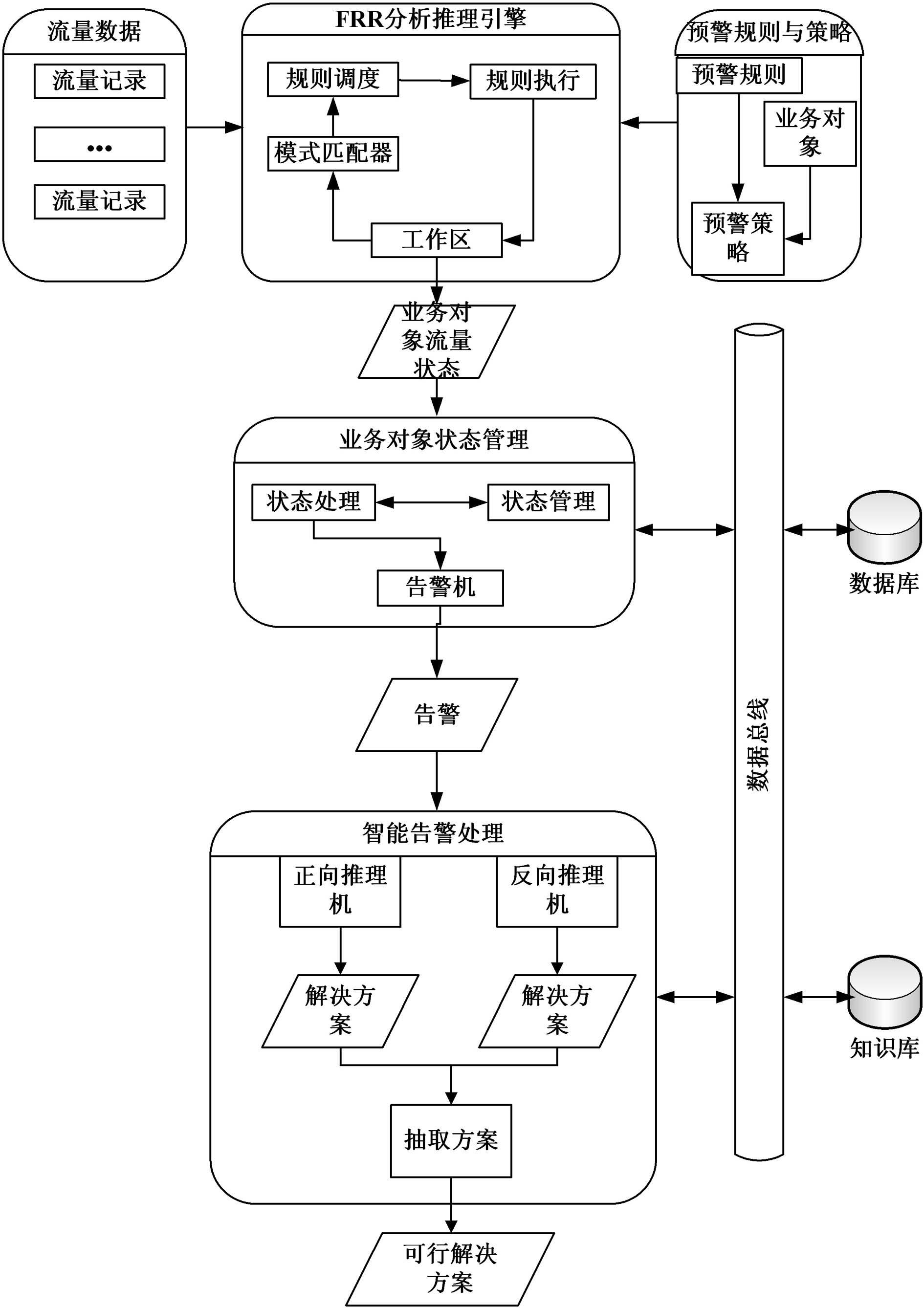
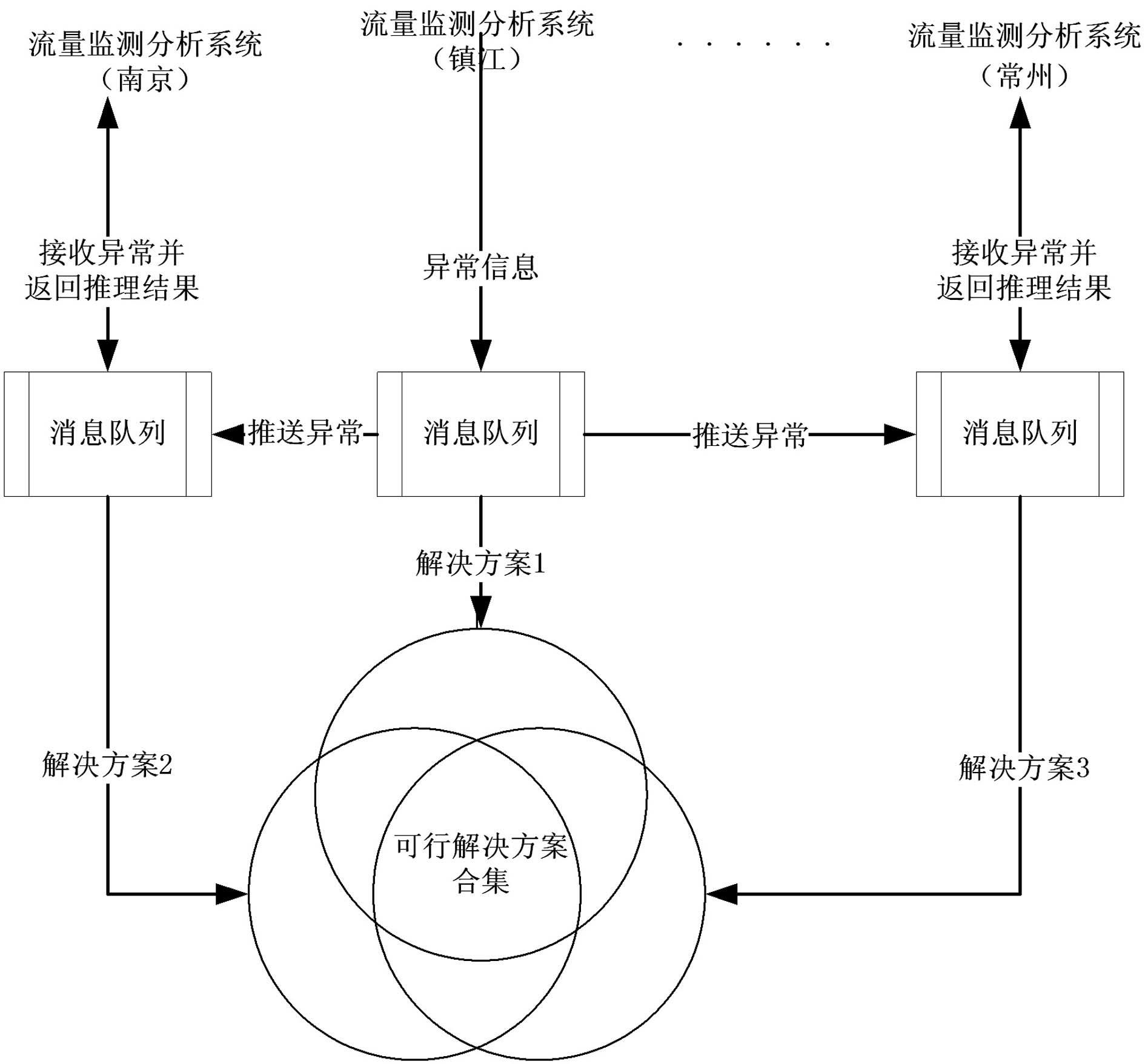
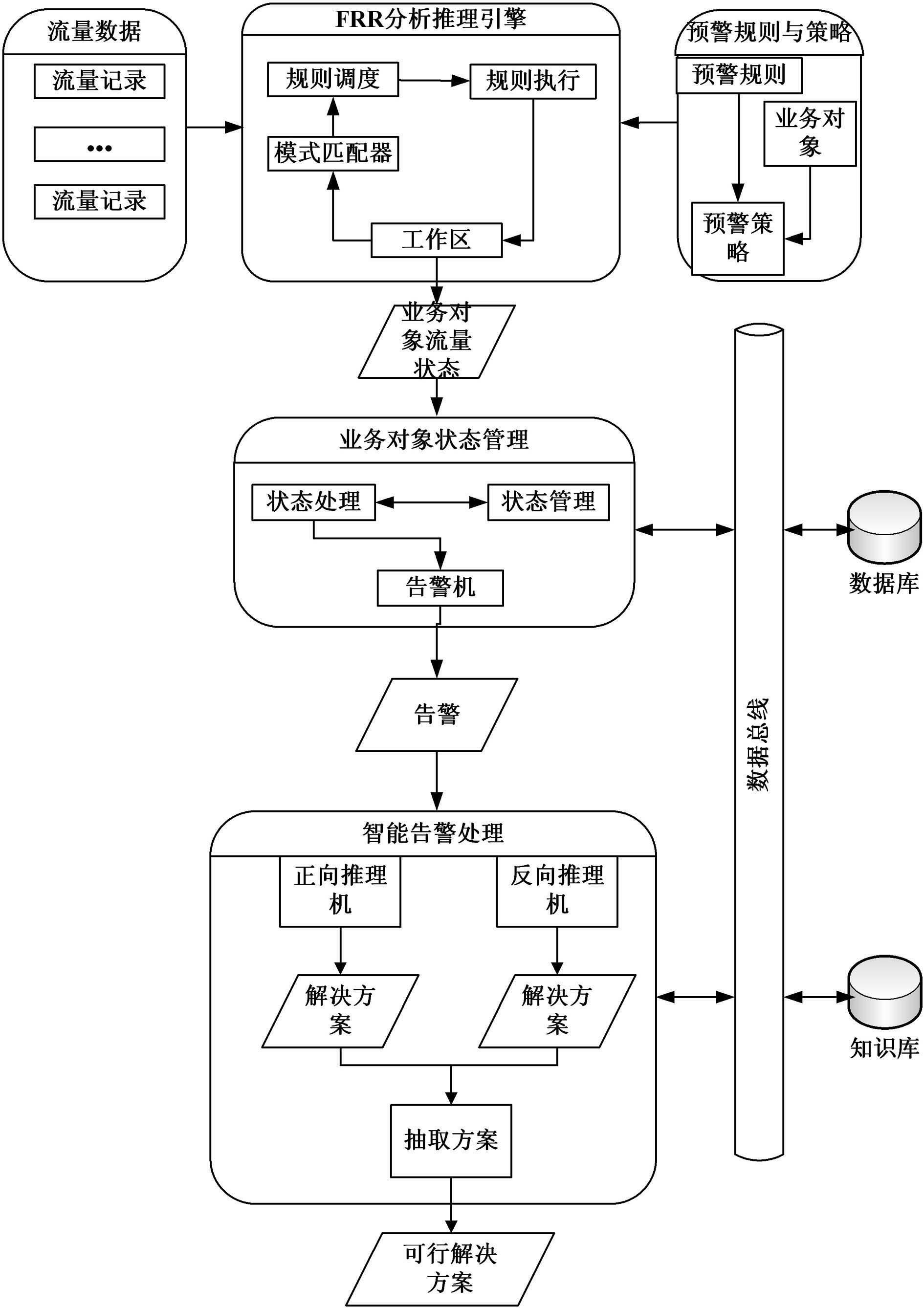
The invention discloses an intelligent analysis system for flow abnormity of a power automation system. The intelligent analysis system is characterized by comprising an early warning rule and strategy module, a real-time monitoring analysis module, a false rejection rate (FRR) analytical reasoning engine module, a cloud reasoning architecture module and a service health analysis module, wherein the early warning rule and strategy module generates early warning strategies aiming at the flow characteristics of the automation system according to abnormity classification and preset rule parameters; the real-time monitoring analysis module implements real-time monitoring and early warning of service flow abnormality based on the service flow data of the automation system by using the system associated early warning strategies; the FRR analytical reasoning engine module intelligently analyzes the solution of the reasoning abnormity based on the flow data, the early warning rules and the abnormity type; the cloud reasoning architecture module provides a more accurate solution by using multi-place deployed system resources and combining the solution of the reasoning abnormity condition; and the service health analysis module analyzes and calculates the service health of the automation system according to the flow state of each composition part of the automation system. The intelligent analysis system is used for quickly analyzing fault problems, providing the feasible solution, improving the work efficiency of maintenance personnel and ensuring normal operation of the network and the system.
Owner:JIANGSU FRONTIER ELECTRIC TECH +1
Iris image data processing for use with iris recognition system
InactiveUS20040114782A1Reduce rateImage analysisGeometric image transformationIris imageComputer science
The present invention relates to an iris recognition method which is one of biometric technologies. According to a non-contact-type human iris recognition method by correction of a rotated iris image of the present invention, the iris image is acquired by image acquisition equipment using an infrared illuminator. Inner and outer boundaries of the iris are detected by analyzing differences in pixels of a Canny edge detector and the image for the inputted iris image, so as to allow the boundaries of the iris to be more accurately detected from the eye image of a user. Thus, the iris image with a variety of deformation can be processed into a correct iris image, so that there is an advantage in that a false acceptance rate and a false rejection rate can be markedly reduce.
Owner:SENGA ADVISORS LLC +1
Finger vein identification method based on fusion of multiple characteristic thresholds
ActiveCN108256456AImprove rejection rateEfficient and reasonable useSubcutaneous biometric featuresBlood vessel patternsCorrelation coefficientVein
The invention discloses a finger vein identification method based on fusion of multiple characteristic thresholds. A 2D Gaussian template based on multiple standard deviations is used to calculate a curvature of a finger vein image, a background-area curvature grayscale characteristic, a vein-area curvature grayscale characteristic and a curvature fine line characteristic of the image are extracted; a correlation coefficient method is used to calculate a matching threshold of the background-area curvature grayscale characteristic and the vein-area curvature grayscale characteristic, an MHD algorithm is used to calculate a matching threshold of the curvature fine line characteristic, and a multi-characteristic-threshold fusion decision algorithm is provided to fuse independent identification thresholds of the three characteristics and further to carry out verification and decision. According to the algorithm based on fusion of the thresholds of the three characteristics, background areaavailable information included by the background-area curvature grayscale characteristic is combined, the fuzzy finger vein image identification performance is not decreased obviously, the false rejection rate under a low false accept rate is substantially lower than that of a traditional identification algorithm based on the fine line characteristic only, and the identification algorithm can beutilized reasonably and highly efficiently.
Owner:HANGZHOU DIANZI UNIV
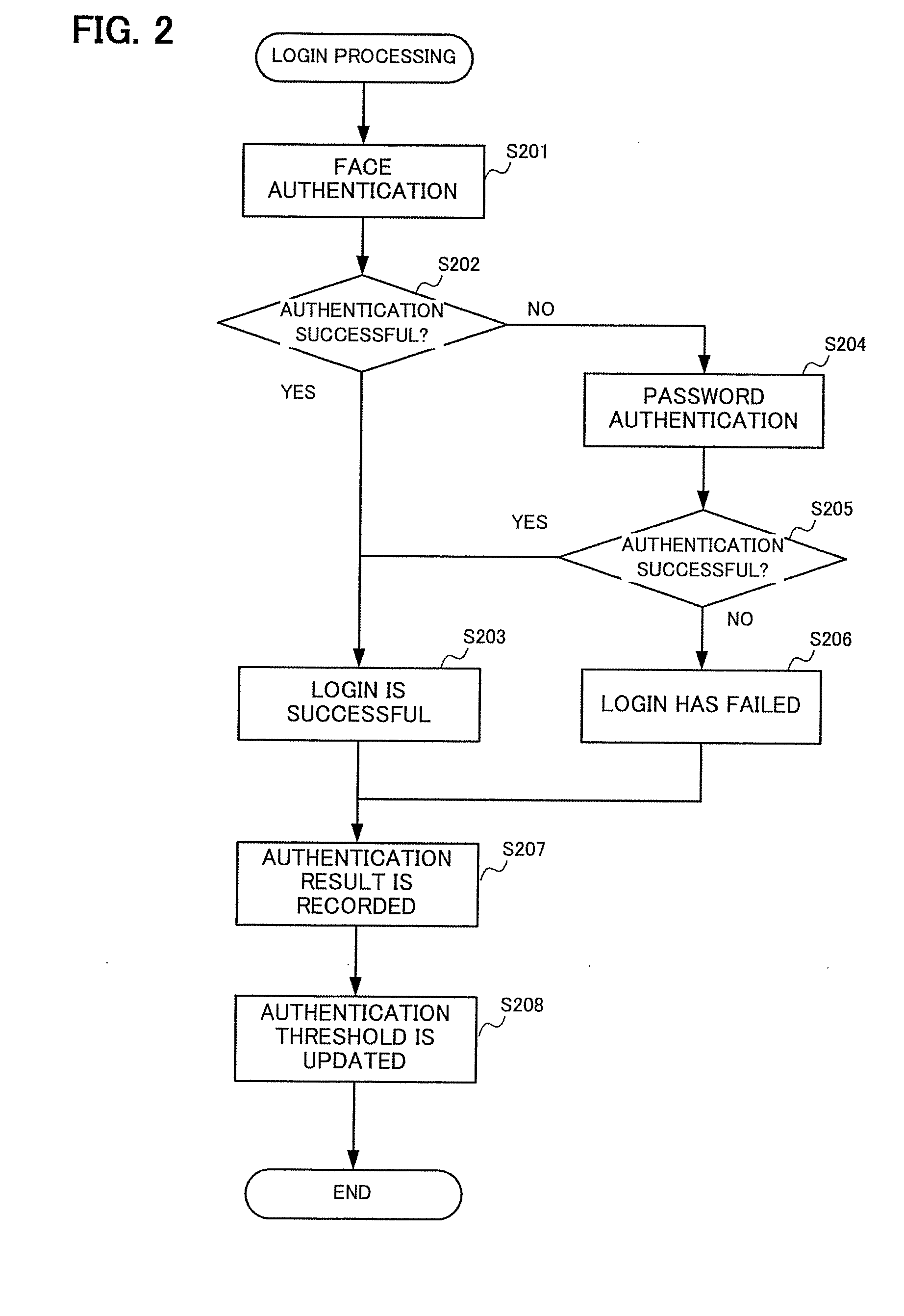
Individual identification device, and identification threshold setting method
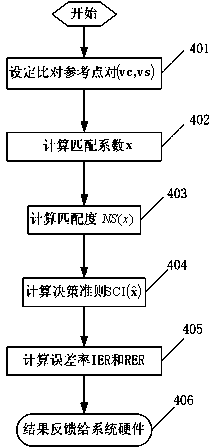
ActiveUS20160292536A1Inadequate valueDigital data authenticationMultiple biometrics usePattern recognitionIdentification device
Provided is an individual identification device including: a biometric information storage unit; a biometric information acquisition unit; an identification unit which calculates a similarity of the biometric information on the subject and the registrant and performs identification of the subject according to whether or not the calculated similarity is equal to or higher than an identification threshold; an identification result storage unit which stores identification result information constituted by the calculated similarity and a correct identification result; and a threshold setting unit which sets the identification threshold such that at least either one of a false rejection rate and a false acceptance rate fulfils a predetermined condition in the identification result information stored in the identification result storage unit.
Owner:ORMON CORP
Finger print identifying method based on broken fingerprint detection
The invention is a fingerprint discriminating method based on broken design detection which belongs to fingerprint identification field. Its character lies in: it carries on broken design detection to detail points extracted with traditional method with 12 groups of best filter, each filter has a discrete value of an angle between the broken design direction and the X axis; works out the filter value under the 12 groups of broken design directions and sets a uniform floor level, acquires 12 groups of binary image, then the stripe region is displayed with rectangular with primary cell analysis method of matrix, and the region is parameterized with length, width and direction of the rectangular; all the binary images are combined together and a real broken design image is acquired, the parameterized images are combined and a broken design model is acquired in order to eliminate the false detail points. To the old people, with the same error reception rate, the fault refusing rate can be decreased to less than 10%.
Owner:TSINGHUA UNIV
Computerized device with voice command input capability
ActiveUS20180330727A1High false acceptance rateReduce false reject rateMemory architecture accessing/allocationMechanical apparatusClock rateSpeech sound
A computerized device with voice command capability processed remotely includes a low power processor, executing a loose algorithmic model to recognize a wake word prefix in a voice command, the loose model having a low false rejection rate but suffering a high false acceptance rate, and a second processor which can operate in at least a low power / low clock rate mode and a high power / high clock rate mode. When the first processor determines the presence of the wake word, it causes the second processor to switch to the high power / high clock rate mode and to execute a tight algorithmic model to verify the presence of the wake word. By using the two processors in this manner, the average overall power required by the computerized device is reduced, as is the amount of waste heat generated by the system.
Owner:GENERAC POWER SYSTEMS
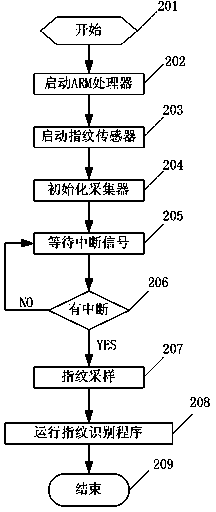
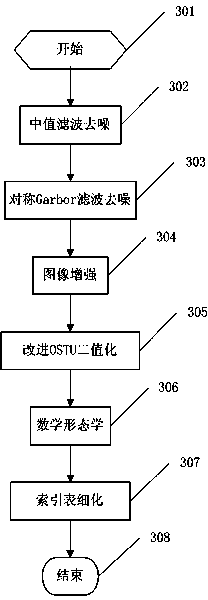
ARM fingerprint identification method and device based on sparse matrix
The invention relates to a fingerprint identification method based on a sparse matrix. The method is characterized by comprising the following steps that hardware of a fingerprint identification system is initialized, fingerprint signals are detected, fingerprint images are collected, relevant information is obtained, the fingerprint images are preprocessed, finger non-detail feature points are extracted, fingerprint identification matching is carried out by utilizing a sparse matrix fingerprint matching algorithm, the matching degree of fingerprints is calculated, comparison is carried out according to the matching degree and a set fingerprint matching degree threshold value, whether the fingerprints are matched or not is judged, and an identification result is transmitted to a hardware platform of a fingerprint identification device to be displayed. Meanwhile, the invention relates to the ARM fingerprint identification device based on the sparse matrix. The fingerprint identification device is used for achieving the fingerprint identification method based on the sparse matrix. According to the method and device, fingerprint identification is carried out, and the method and device are high in identification rate of fingerprint identification, high in speed of fingerprint identification, low in false rejection rate and false identification rate of fingerprint identification, high in reliability and strong in operability. The fingerprint identification method can be applied to the fields of internets, computers, entrance guards and the like. Along with the continuous improvement of requirements of people for encryption techniques, the fingerprint identification method and device have good market prospects in fingerprint identification.
Owner:WUHAN UNIV OF SCI & TECH
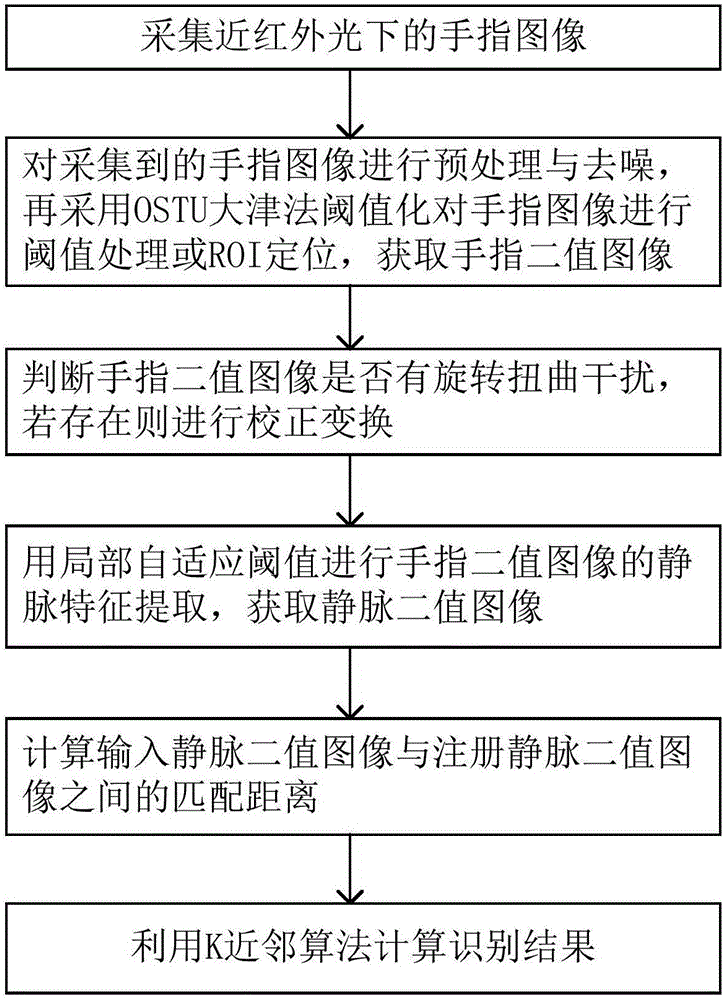
Finger vein recognition method
ActiveCN106096569AImprove robustnessImprove accuracySubcutaneous biometric featuresBlood vessel patternsFinger vein recognitionNeighbor algorithm
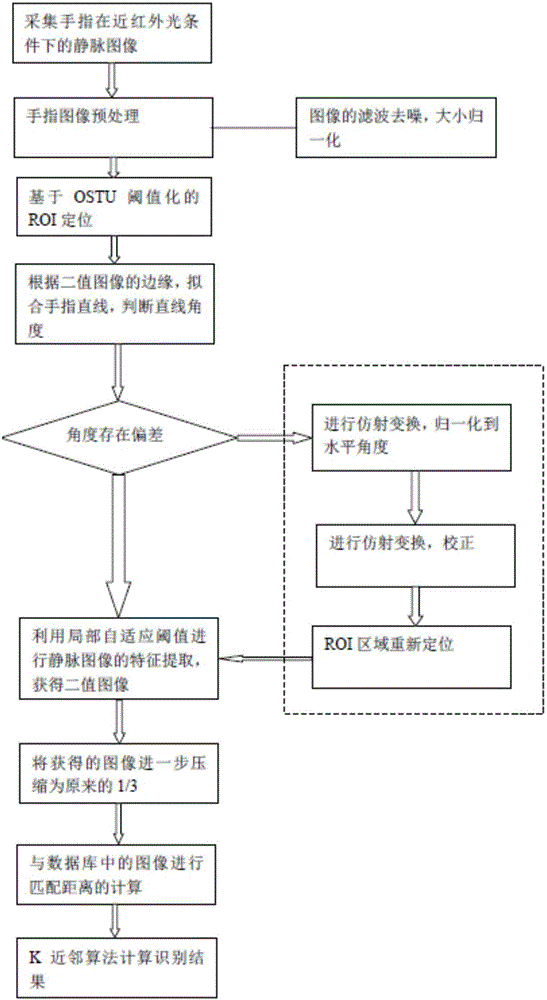
The invention discloses a finger vein recognition method. The method comprises the following steps: S1, a finger image under near infrared light is acquired; S2, preprocessing and denoising are carried out on the acquired finger image, an OSTU threshold method is then adopted to carry out threshold processing or ROI positioning on the finger image, and a finger binary image is acquired; S3, whether rotational distortion interference happens to the finger binary image is judged, and if yes, correction transformation is carried out; S4, a local adaptive threshold is used for carrying out vein feature extraction on the finger binary image, and a vein binary image is acquired; S5, a matching distance between an inputted vein binary image and a registered vein binary image is calculated; and S6, a K nearest neighbor algorithm is used for calculating a recognition result. The method has a strong anti-inteference ability, particularly adverse circumstances such as rotational translation distortion of the image, and at the same time, a false rejection rate and a false accpetance rate can be reduced.
Owner:GUANGZHOU INST OF ADVANCED TECH CHINESE ACAD OF SCI
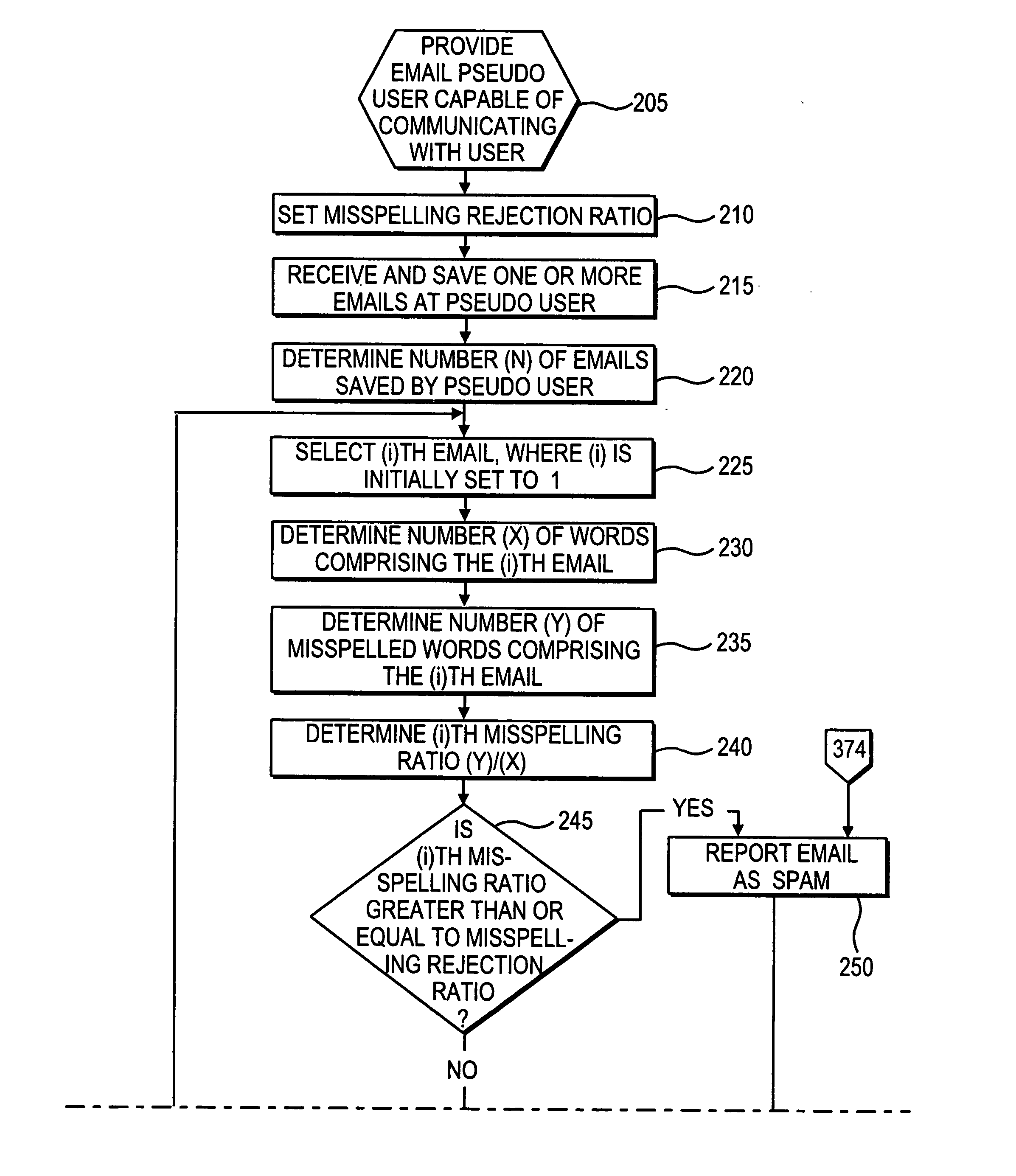
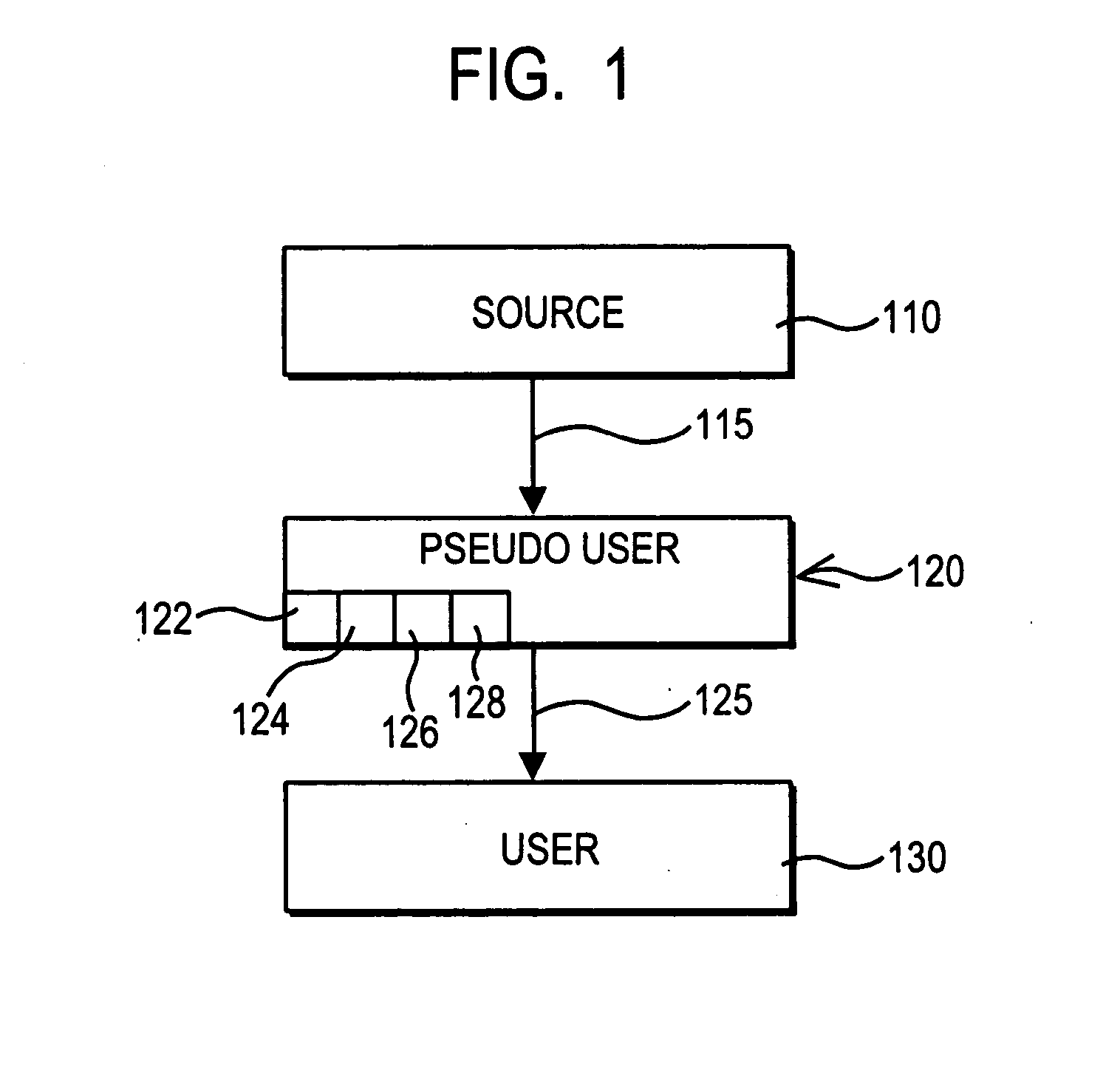
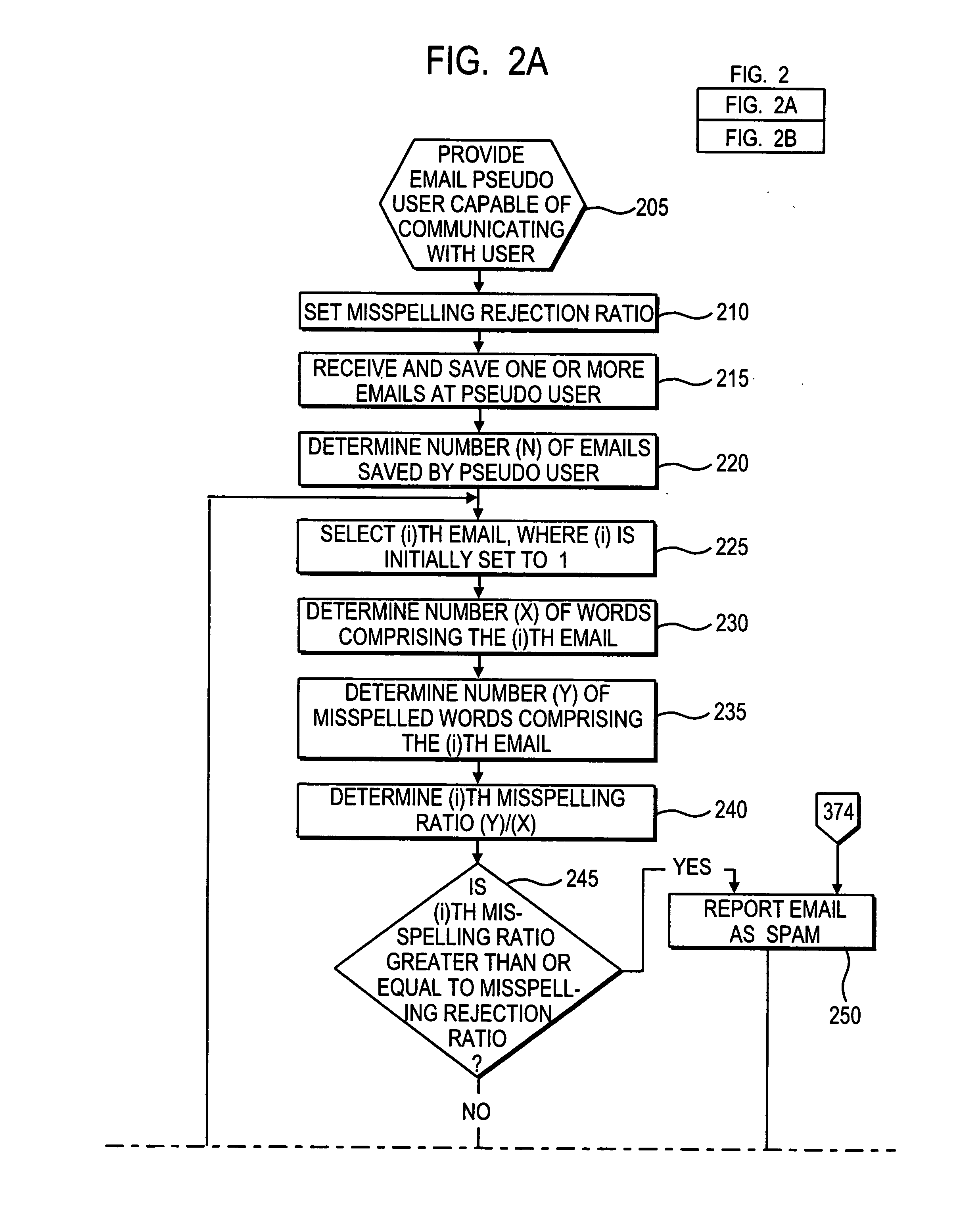
Apparatus and method to identify SPAM emails
A method and apparatus to identity SPAM emails is disclosed. The method sets a misspelling rejection ratio. Upon receipt of an email comprising (X) words, the method determines the number (Y) of misspelled words comprising that email. The method then calculates a misspelling ratio by dividing (Y) by (X), and then determines if the misspelling ratio is greater than or equal to the misspelling rejection ratio. If the method determines that the misspelling ratio is greater than or equal to the misspelling rejection ratio, then the method reports the email as SPAM. In certain embodiments, the detection of words used to trigger the rejection of SPAM is based on a fuzzy search of alternate spellings. These alternate spellings may come from a spell checker.
Owner:TREND MICRO INC
Finger vein identification method, apparatus and vein authentication terminal device
InactiveCN104866828AKeep rejection rateMatching and classificationSubcutaneous biometric featuresFinger vein recognitionTerminal equipment
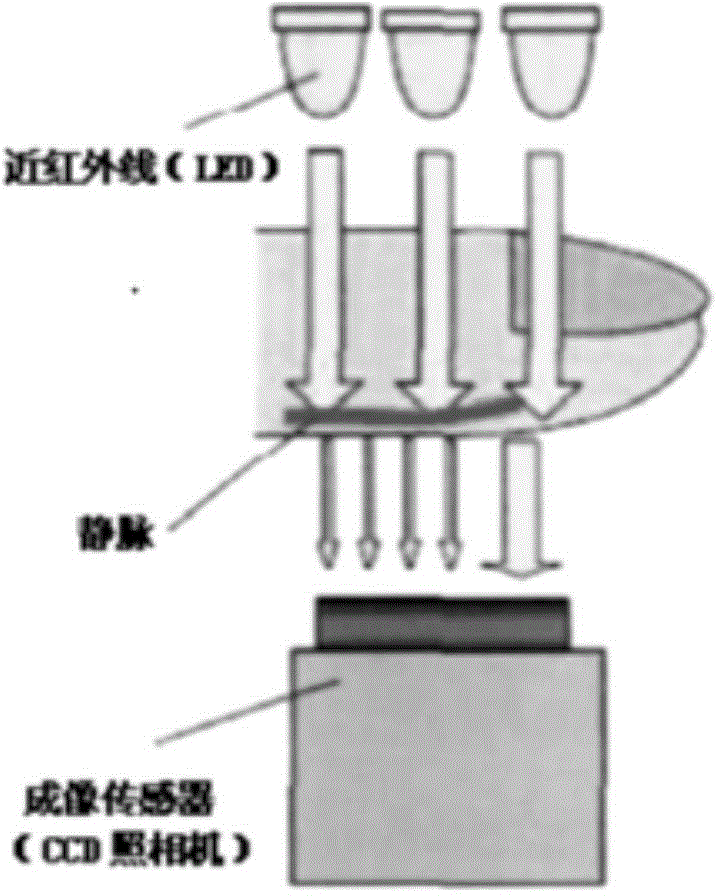
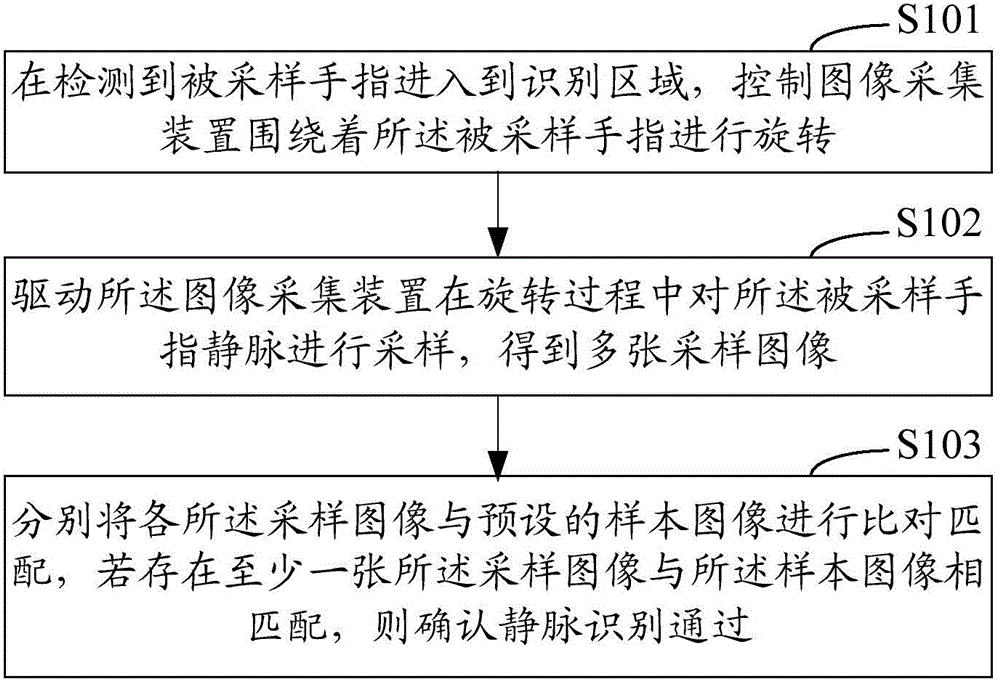
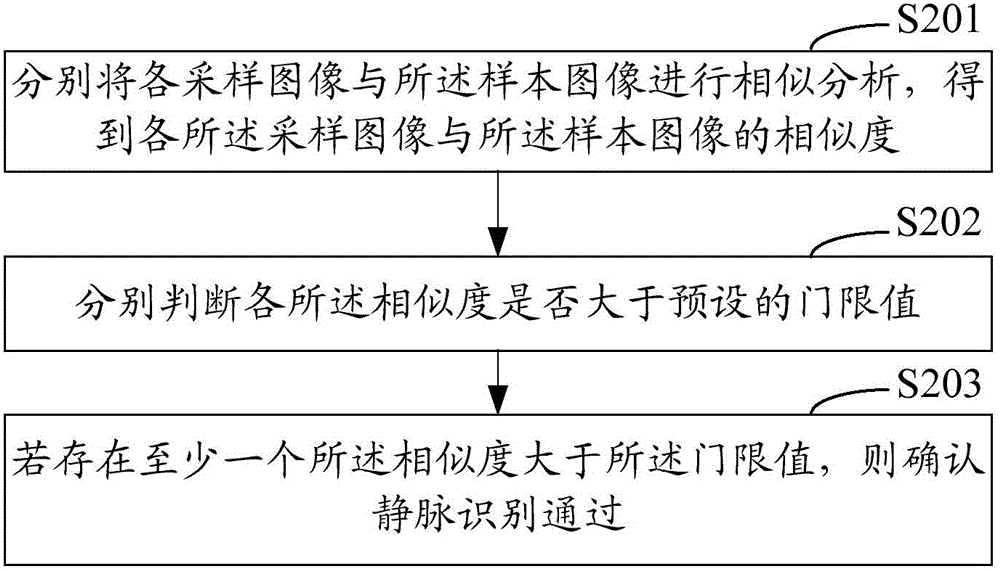
The invention relates to a finger vein identification method, an apparatus and a vein authentication terminal device. The method includes controlling an image acquisition apparatus to rotate about a sample finger once the sampled finger entered in an identification area is detected, driving the image acquisition apparatus to sample the vein of the sampled finger to obtain a plurality of sampling images, comparing and matching the sampling images with preset sample images, and determining passing of vein identification if at least one sampling image matches with the sample images. The vein false rejection rate can be maintained even when the finger plane is not perpendicular to the image acquisition apparatus. The invention is easy to realize.
Owner:HITACHI BUILDING TECH GUANGZHOU CO LTD
Method for optimizing resources of static-dynamic mixed service in three-layer network
InactiveCN101895422AOptimal initial topologyReduce blocking rateData switching networksTopology informationResource coordination
The invention discloses a method for optimizing resources of a static-dynamic mixed service in a three-layer network, which mainly solves the problem of transmission of the static-dynamic mixed service resource in the three-layer network, and comprises the following steps of: 1) inputting three-layer network topology information and a static service matrix; 2) taking a priority routing algorithm of request bandwidth total maximum as static service routing; 3) taking an ant colony optimization-based integrated routing algorithm as dynamic service routing; 4) determining whether to call an interlayer or intralayer resource optimization method or not according to grade parameters of the dynamic service and the joint routing result; 5) performing network periodic triggering on the global resource scheduling and optimizing method based on the adaptive period of the load intensity; and 6) carrying out the algorithm running result. In the invention, by introducing transport network layering,the ant colony optimization-based dynamic service joint routing algorithm, an interlayer resource coordination mechanism and a tabu search-based static service re-grooming method, global network resource optimal utilization is improved, the false rejection rate of a user connection request is reduced, and the requirement of end-to-end quality of service (QoS) is met.
Owner:XIDIAN UNIV
Identity recognition system and method based on hybrid biometrics
InactiveCN103136505AImprove the recognition rateReduce mistakesPerson identificationMultiple biometrics usePattern recognitionIdentity recognition
Disclosed are an identity recognition system and method based on hybrid biometric which capture an image of a subject that is projected by light of different wavelengths, extract various biometric information from the image, analyze and compare for each of the biometric information to generate a matching score, and determine an identity for the subject according to all of the matching scores. The system and method have higher recognition accuracy, lower false acceptance rate, lower false rejection rate, and higher flexibility.
Owner:PIXART IMAGING INC
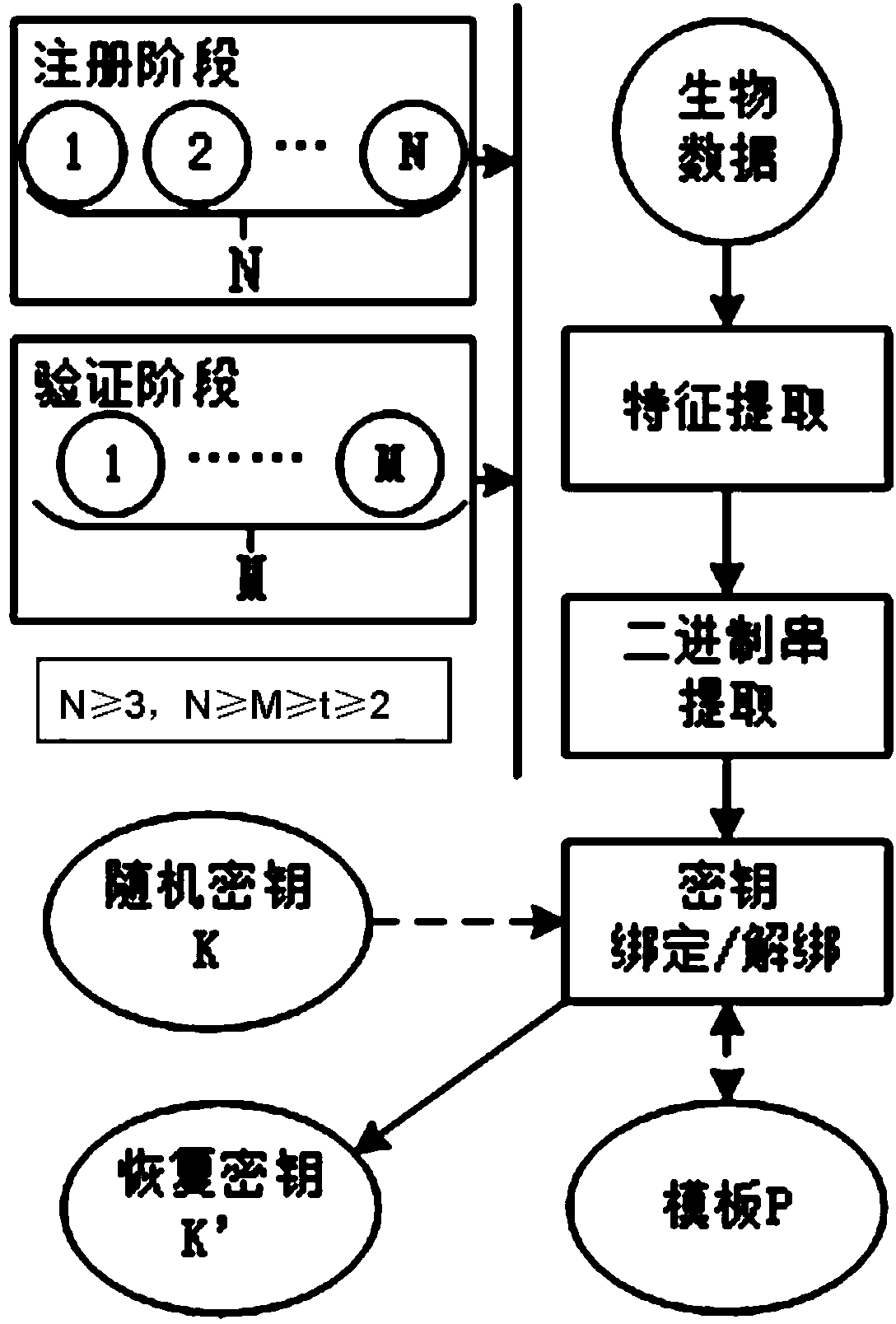
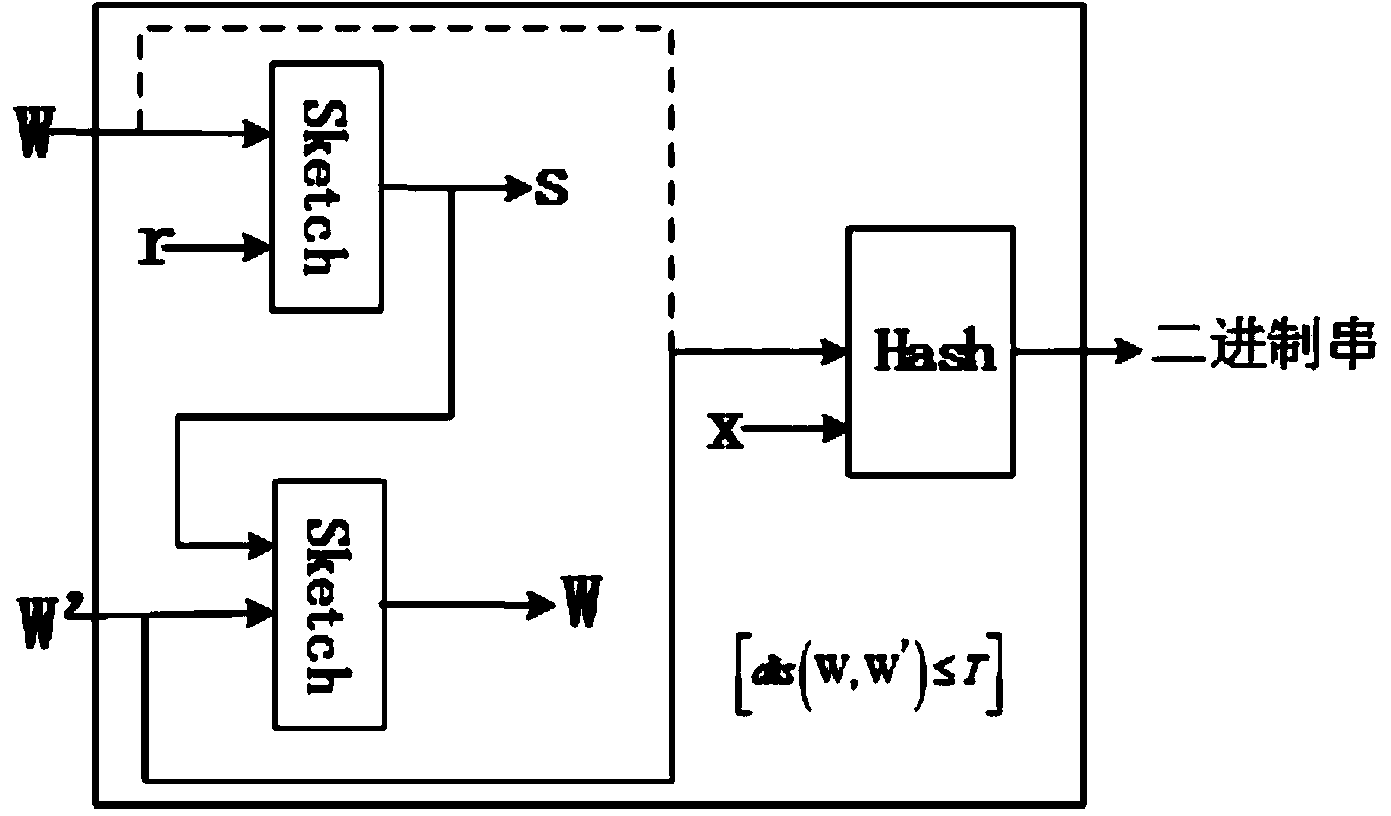
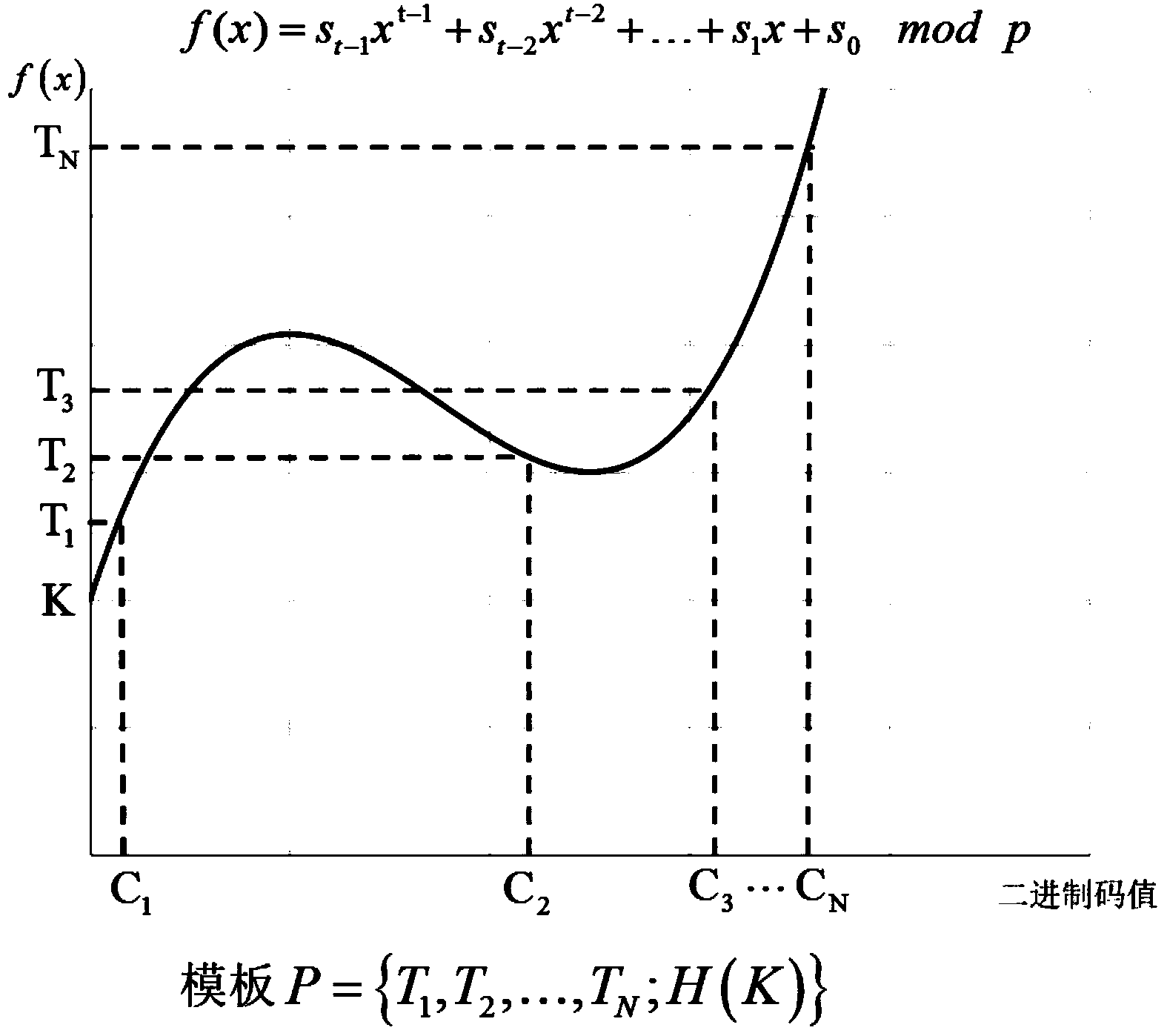
Secret key generation method based on multi-modal biological characteristics
InactiveCN104168112AMeet the needs of obtaining encrypted dataKey distribution for secure communicationUser identity/authority verificationFeature vectorBiometric data
The invention discloses a secret key generation method based on multi-modal biological characteristics, comprising (1) collecting characteristic images of N species of biology, extracting and quantifying the biological characteristic data as characteristic vector, (2) processing the characteristic vector and extracting the binary string to present the characteristic of the creature, (3) generating a random secret key, binding and outputting a public template P by utilizing a Shamir secret sharing method with the binary string collection, (4) sampling M creature characteristics and obtaining a binary string collection, wherein n>-M>=t>=2, and the t is a threshold value of the Shamir method, 5) inputting the binary string collection and the template P into the Shamir secret sharing method to recovery a secret key K', (6)and comparing the K and K'. The invention can improve the recognition rate and reduce the false rejection rate, can produce secret key with higher entropy, and can finish the user authentification while recovering the secret key by binding the user identity and the secret key.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
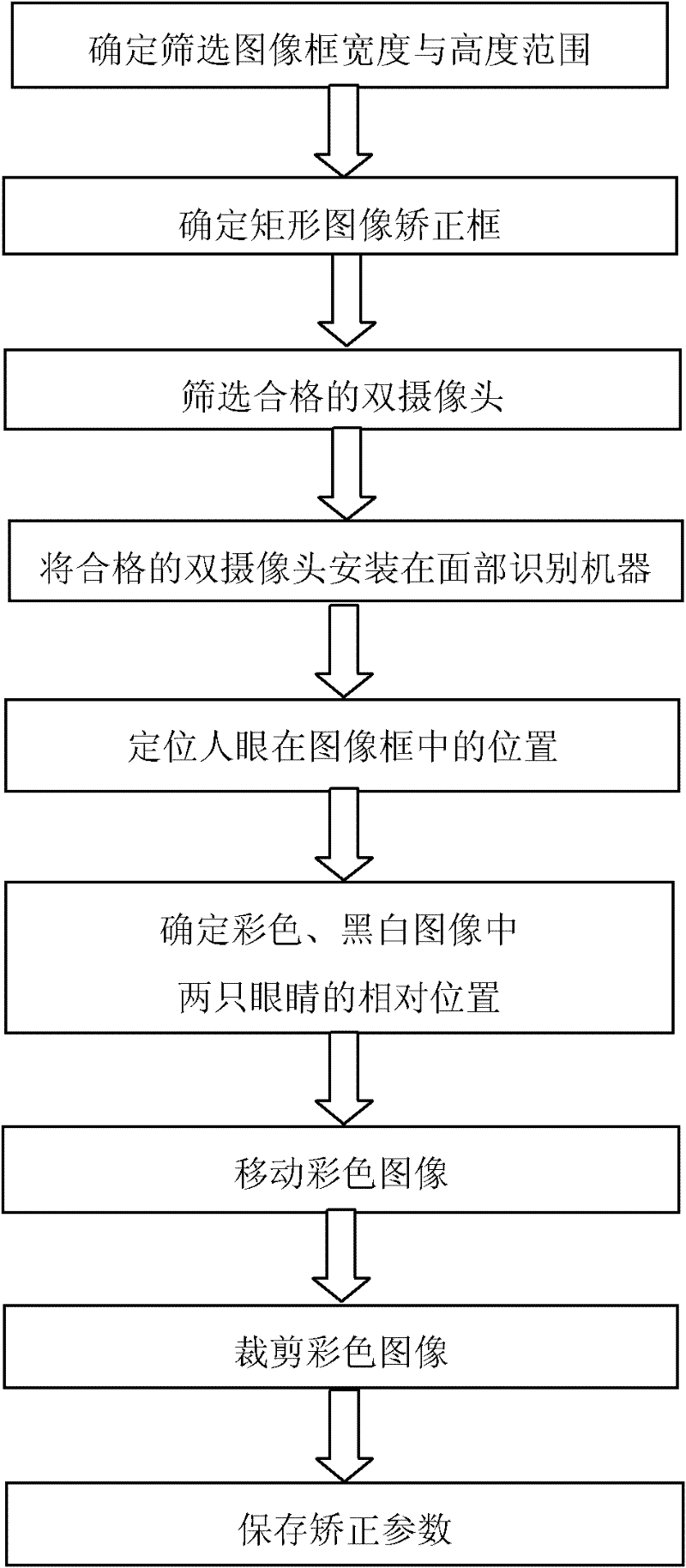
Method for correcting color image and black-and-white image based on double-camera face identification
ActiveCN102567714ASolve problems that are not correctly identifiedImprove praiseCharacter and pattern recognitionPicture signal generatorsColor imageImage correction
The invention discloses a method for correcting a color image and a black-and-white image based on double-camera face identification. A double-camera plate with a black-and-white camera and a color camera is connected with a computer for correction. The method is characterized in that: a correction plate is also used. The method comprises the following steps of: 1) determining the widths and heights of screened image frames; 2) determining a rectangular image correction frame; 3) screening double qualified cameras; 4) installing the double qualified cameras in a face identification machine; 5) positioning human eyes in the image frames; 6) determining the relative positions of two eyes in the color image and the black-and-white image; 7) moving the color image; 8) cutting the color image;and 9) storing correction parameters. By adoption of the method, the problem that when a face is located at the edge of a color image frame, a complete face image which is displayed by the face identification machine cannot be accurately identified is effectively solved; identification rate, identification accuracy and identification speed can be remarkably improved; false rejection rate is reduced; and particularly, a product can be highly appreciated by a customer.
Owner:熵基科技(广东)有限公司
Speaker recognition systems
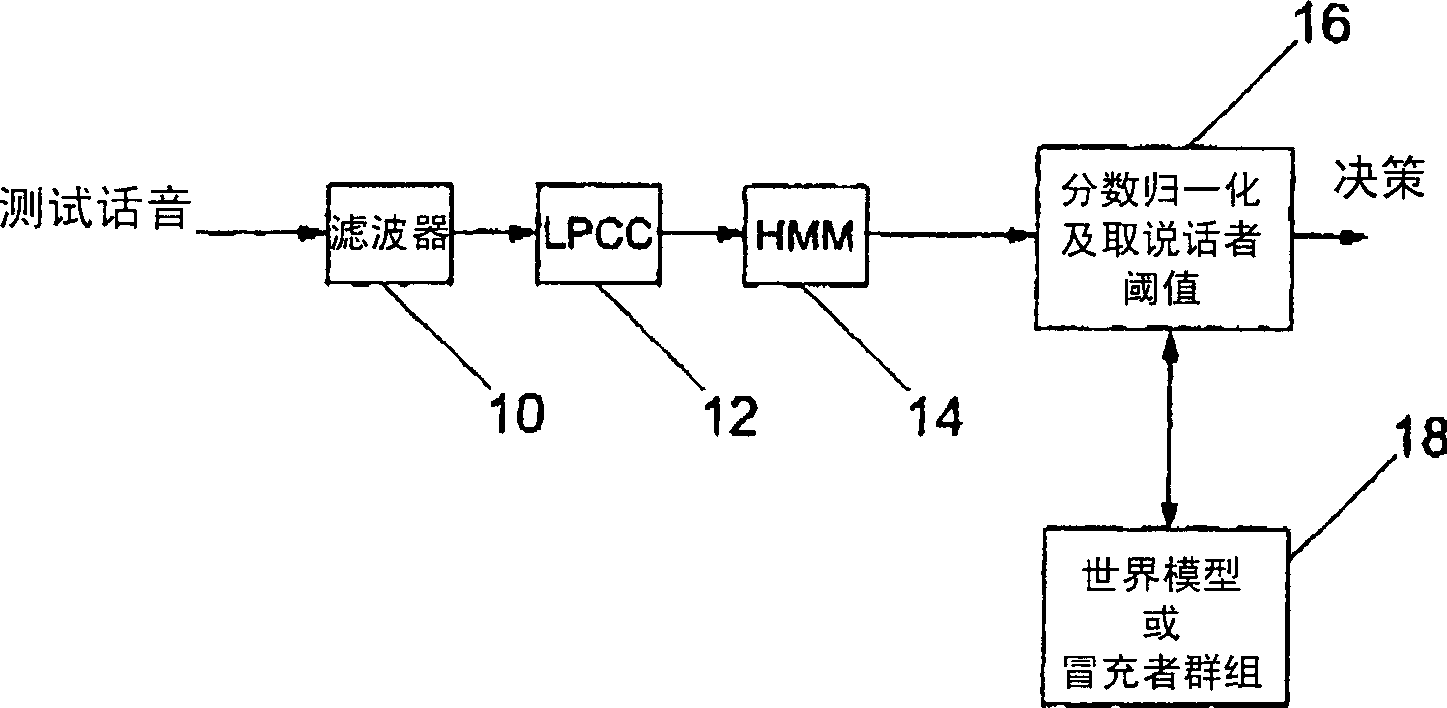
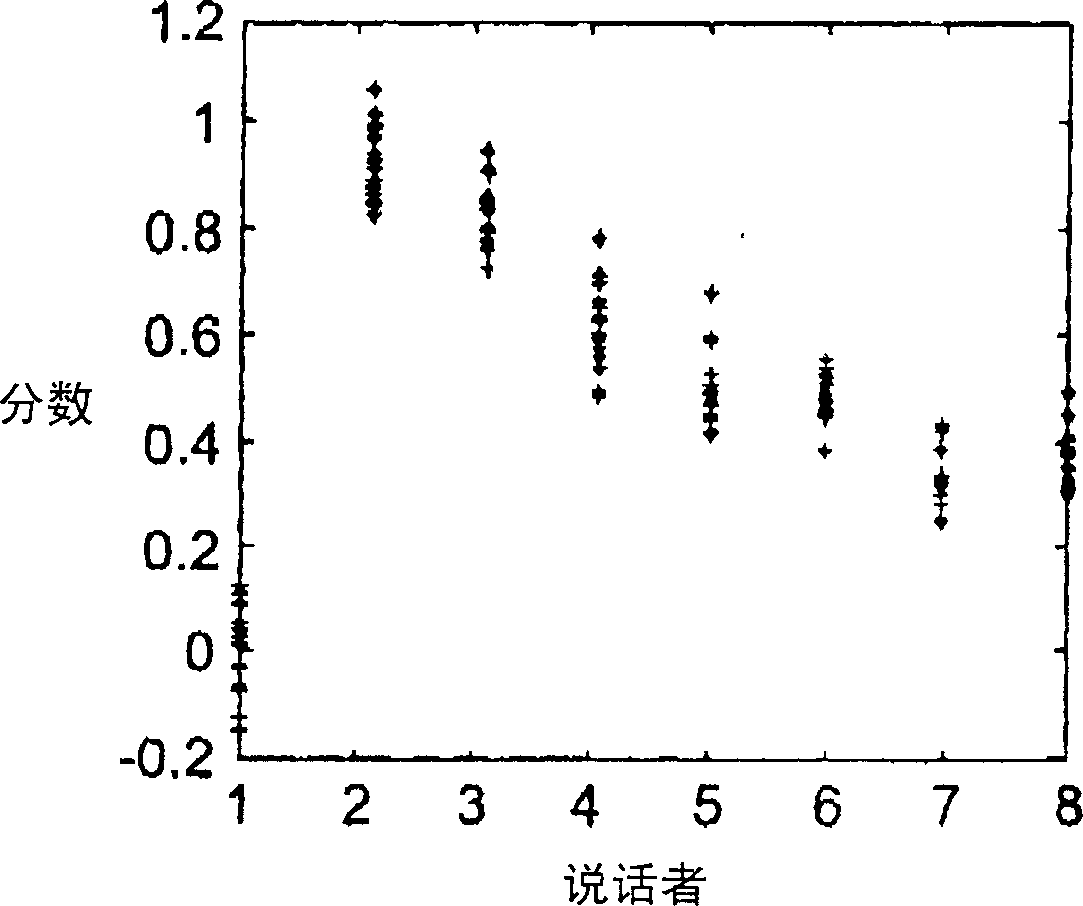
Speaker recognition (identification and / or verification) methods and systems, in which speech models for enrolled speakers consist of sets of feature vectors representing the smoothed frequency spectrum of each of a plurality of frames and a clustering algorithm is applied to the feature vectors of the frames to obtain a reduced data set representing the original speech sample, and wherein the adjacent frames are overlapped by at least 80%. Speech models of this type model the static components of the speech sample and exhibit temporal independence. An identifier strategy is employed in which modelling and classification processes are selected to give a false rejection rate substantially equal to zero. Each enrolled speaker is associated with a cohort of a predetermined number of other enrolled speakers and a test sample is always matched with either the claimed identity or one of its associated cohort. This makes the overall error rate of the system dependent only on the false acceptance rate, which is determined by the cohort size. The false error rate is further reduced by use of multiple parallel modelling and / or classification processes. Speech models are normalised prior to classification using a normalisation model derived from either the test speech sample or one of the enrolled speaker samples (most preferably from the claimed identity enrolment sample).
Owner:SECURIVOX
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com