A mobile terminal and its voice encryption method
A mobile terminal, voice encryption technology, applied in telephone communication, digital transmission system, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
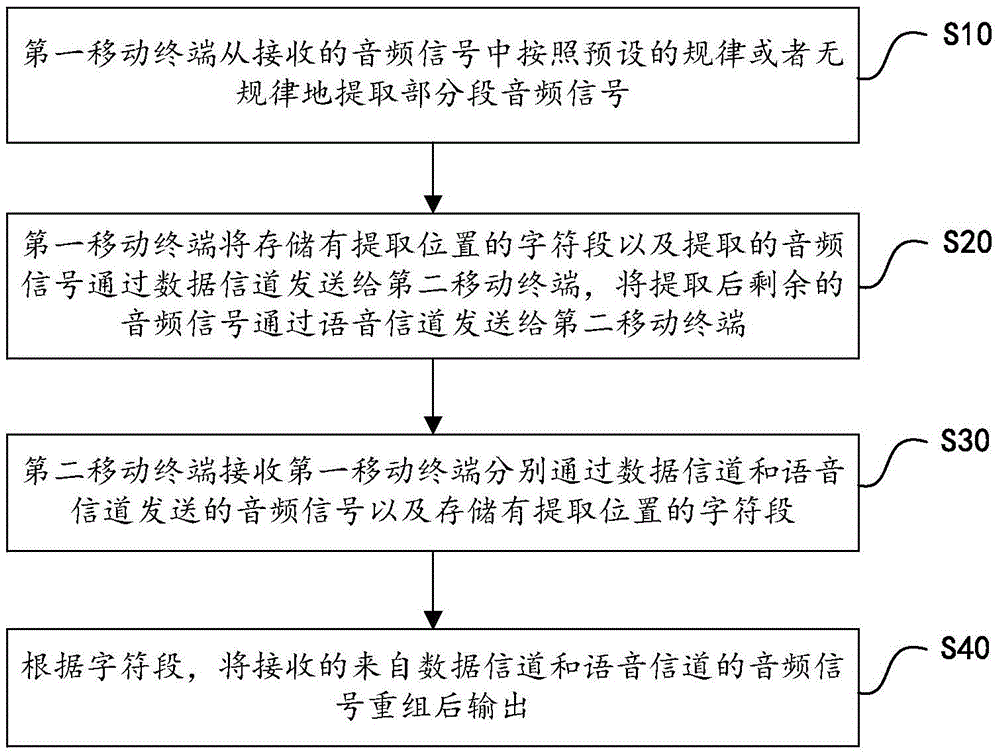
[0042] figure 1 It is the flowchart of the method for voice encryption according to an embodiment of the present invention, below in conjunction with figure 1 To describe the voice encryption method according to an embodiment of the present invention, the method is applied to a first mobile terminal and a second mobile terminal that conduct voice calls with each other, and the mobile terminals, such as mobile phones, tablet computers, etc., can be used for voice calls portable electronic devices such as figure 1 As shown, the method for voice encryption according to an embodiment of the present invention includes the following steps:
[0043] S10. The first mobile terminal extracts partial segment audio signals from the received audio signals according to preset rules or irregular rules;
[0044] S20. The first mobile terminal sends the character segment storing the extraction position and the extracted audio signal to the second mobile terminal through the data channel, and...
Embodiment 2
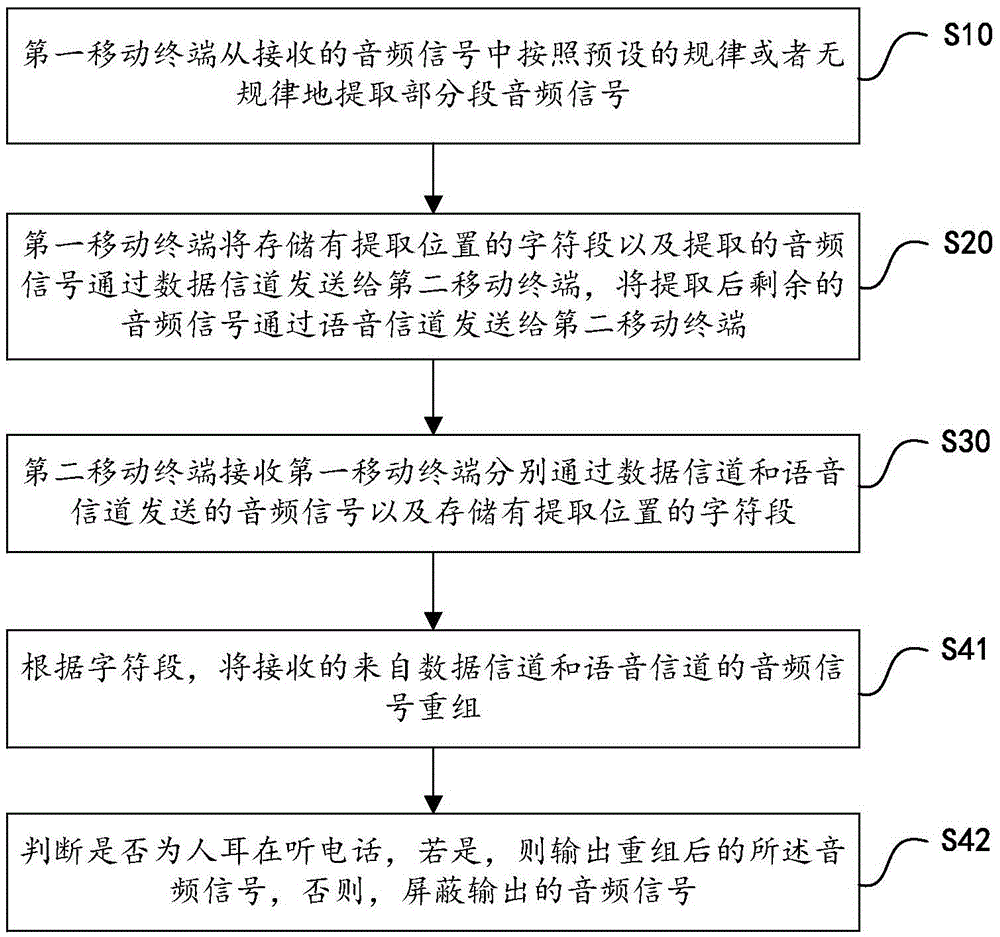
[0059] figure 2 It is the flowchart of the method for voice encryption according to another embodiment of the present invention, as figure 2 As shown, on the basis of including the above-mentioned steps S10, S20, S30, the method for this voice encryption, the above-mentioned S40 specifically includes:
[0060] S41. Recombining the received audio signals from the data channel and the voice channel according to the character field;
[0061] S42. Determine whether the human ear is listening to the phone, if yes, output the recombined audio signal, otherwise, shield the output audio signal.
[0062] Among them, whether the human ear is listening to the phone can be judged by infrared detection, or by a temperature sensor to detect whether the temperature of the contact medium is human body temperature.
[0063] The purpose of this embodiment is to limit the call to the human ear, so that other people cannot use the earphone to expose the call content, or the call content can b...
Embodiment 3
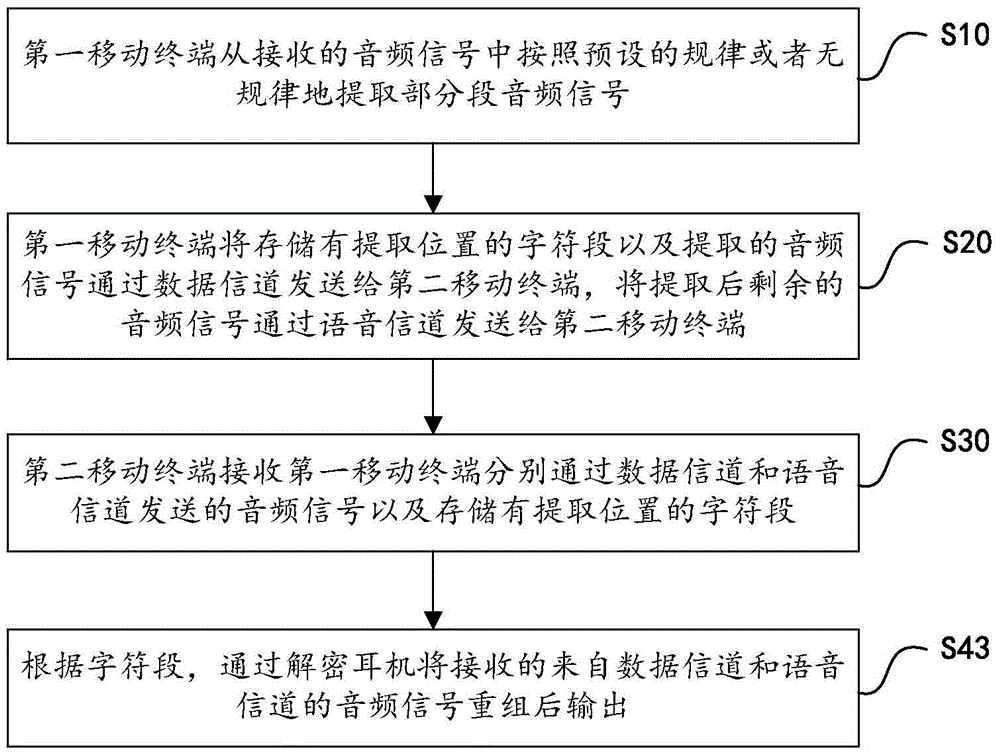
[0065] image 3 It is the flowchart of the method for voice encryption according to another embodiment of the present invention, as image 3 As shown, the method for this voice encryption is on the basis of comprising above-mentioned steps S10, S20, S30, and above-mentioned S40 is specifically:
[0066] S43. According to the character field, the received audio signals from the data channel and the voice channel are reassembled by the earphone through decryption, and then output.
[0067] According to an example of this embodiment, as an option, the method for voice encryption further includes:
[0068] The external playback function of the second mobile terminal is prohibited.
[0069] The purpose of this embodiment is to make the confidentiality of the content of the call better, and only through a specific decryption earphone can an important call be answered.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com