Authority scheduling method and device
A dispatching method and a dispatching device technology, applied in the direction of digital data authentication, etc., to achieve the effect of minimizing and optimizing dispatching and reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
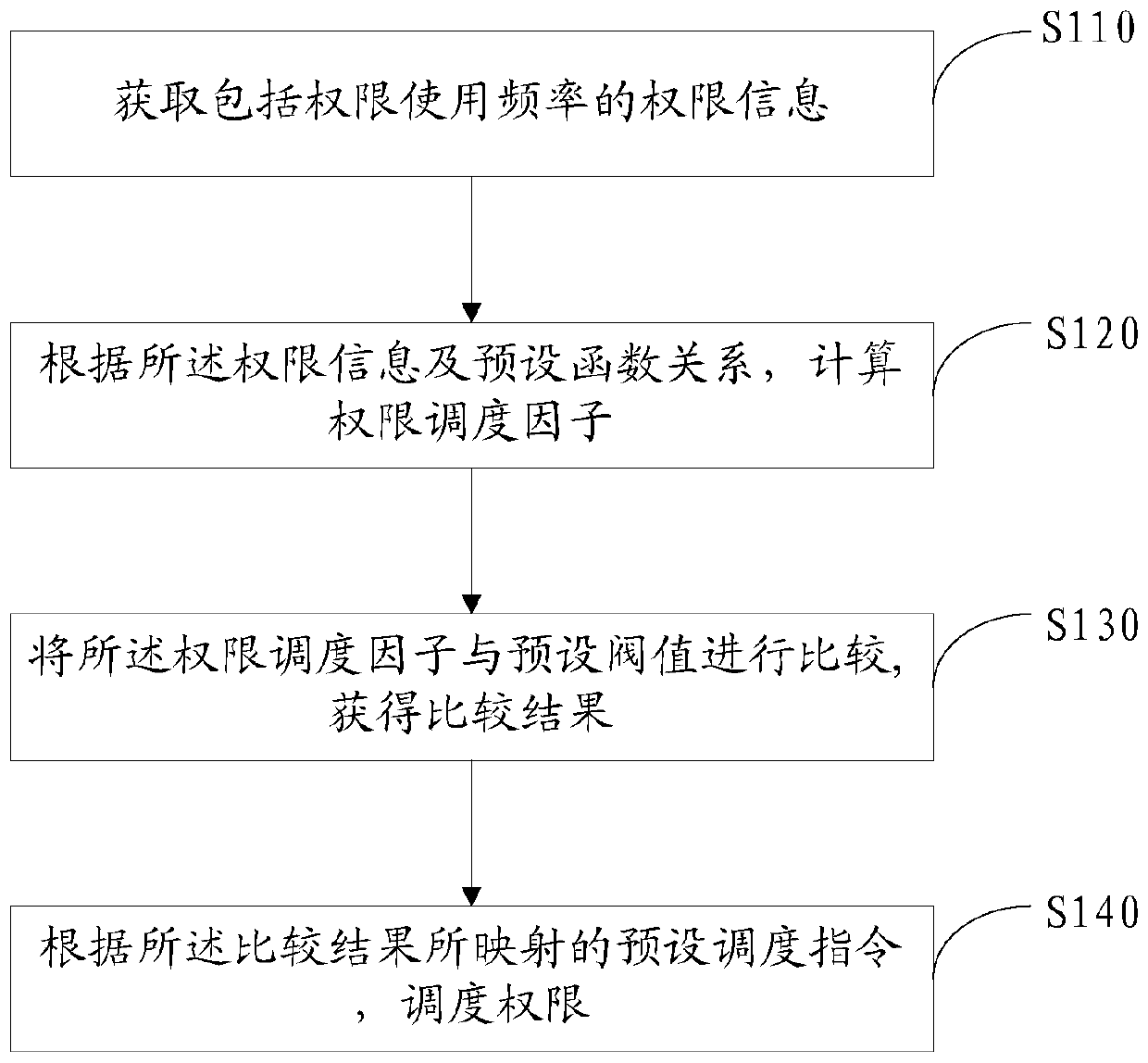
[0079] Such as figure 1 As shown, this embodiment provides a permission scheduling method, the method including:
[0080] Step S110: Obtain permission information including permission usage frequency;
[0081] Step S120: Calculate the authority scheduling factor according to the authority information and the preset functional relationship;
[0082] Step S130: Comparing the authority scheduling factor with a preset threshold to obtain a comparison result;
[0083] Step S140: Scheduling the authority according to the preset scheduling instruction mapped to the comparison result.
[0084] The permission scheduling includes permission scheduling behaviors such as permission recall and permission propagation, and the permission propagation is an authorization form of permissions.
[0085] Specifically, when the permission a corresponding to the account A has not been used for a long time, it means that the frequency of use of the permission a is low, and the permission a can be ...
Embodiment 2
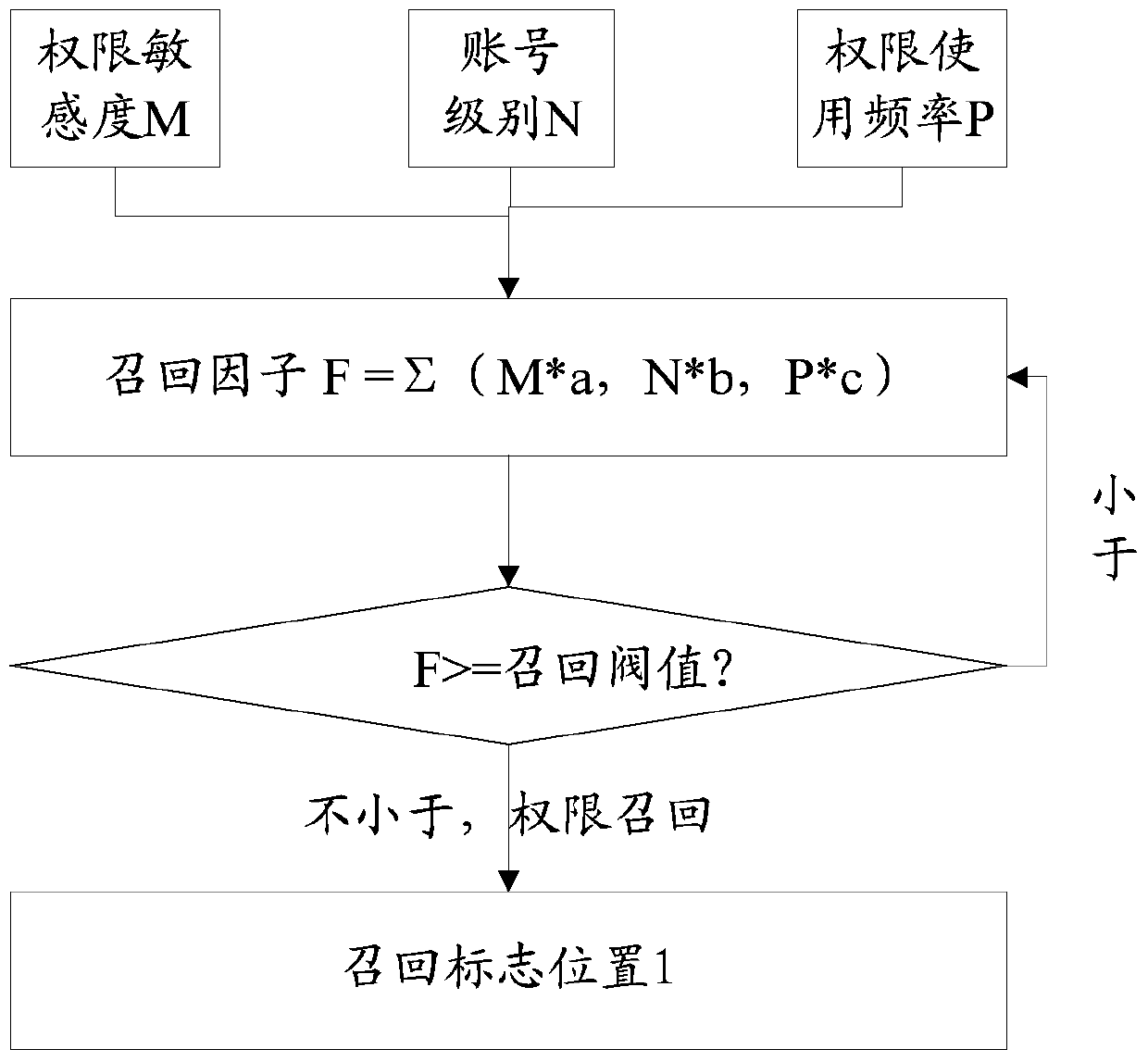
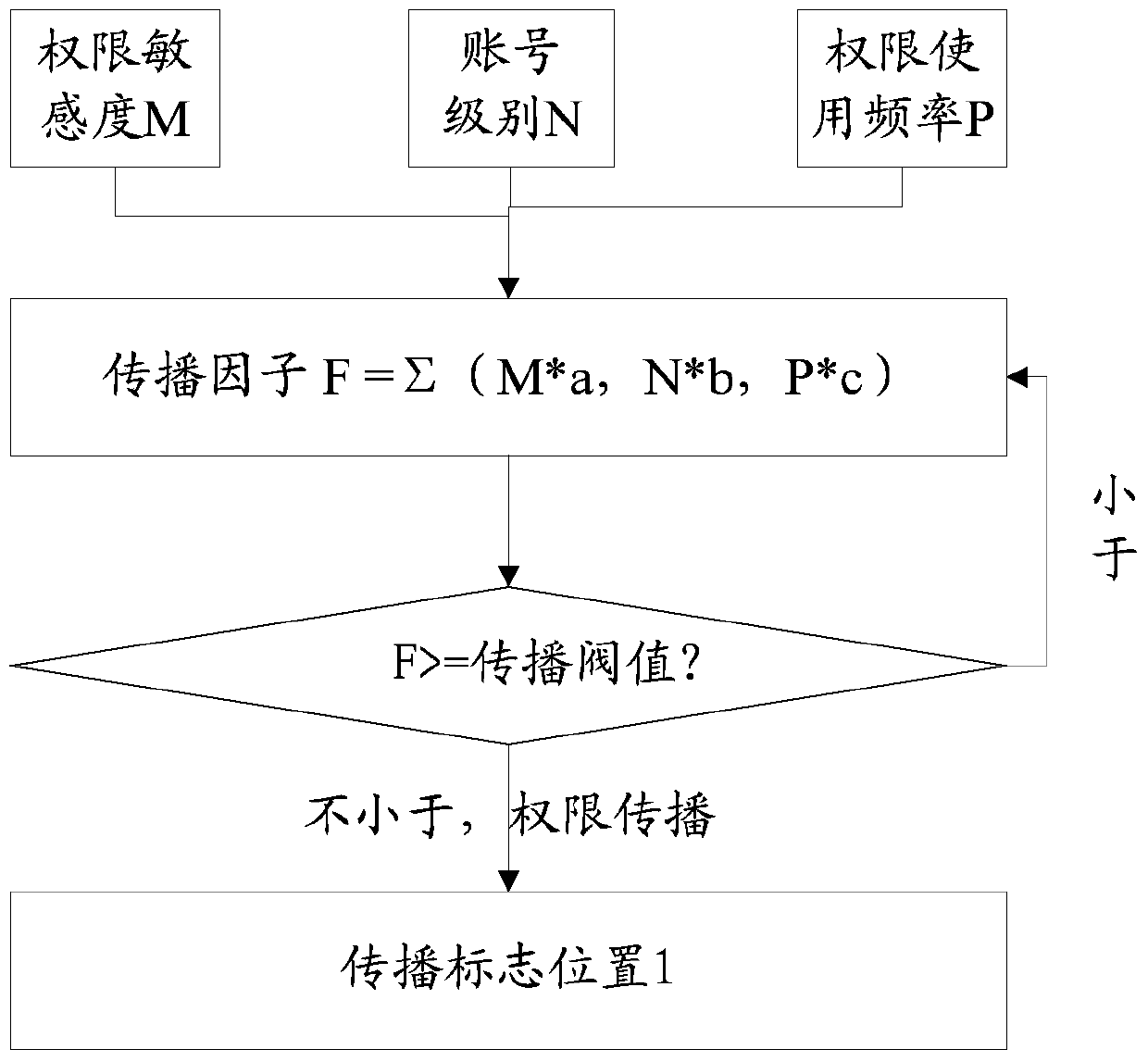
[0090] Permission sensitivity represents the importance of permissions. Specifically, such as the payment change permission and user identity change permission corresponding to the account, the sensitivity is high, such as the sensitivity of applying for service activation is low; the higher the sensitivity, the information The more important, the higher the security required.
[0091] Account levels generally include ordinary accounts, management accounts, and super accounts. Super accounts have higher authority than management accounts, and management accounts have higher authority than ordinary accounts.
[0092] For different accounts and different permissions, depending on the conditions set for recall or dissemination according to the frequency of use of permissions, more optimal permission scheduling can be achieved. Therefore, on the basis of the previous embodiment, this embodiment further includes Added permission sensitivity and user level to better schedule permiss...
Embodiment 3
[0098] This embodiment is based on Embodiment 1 or Embodiment 2, and specifically designed for authority recall and authority propagation. Specifically: the authority scheduling factor is a recall factor for authority recall or a propagation factor for authority replication between accounts in the first specified group.
[0099] Taking account B and its corresponding authority b as an example, when the authority scheduling factor is the recall factor, compare the recall factor with the preset threshold (at this time, the preset threshold is the recall threshold), and judge according to the comparison result Whether to recall the permission b corresponding to account B; specifically, when the recall factor is not less than the recall threshold, the permission b is recalled, and account B can no longer use permission b; when the recall factor is smaller than the recall threshold, the permission b is not recalled , account B can continue to use permission b.
[0100] In the abov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com