Device-to-device multicast/broadcast communication processing method, device and user equipment
A technology of broadcast communication and broadcast application, which is applied in the field of communication, and can solve problems such as the inability to realize D2D multicast and broadcast communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
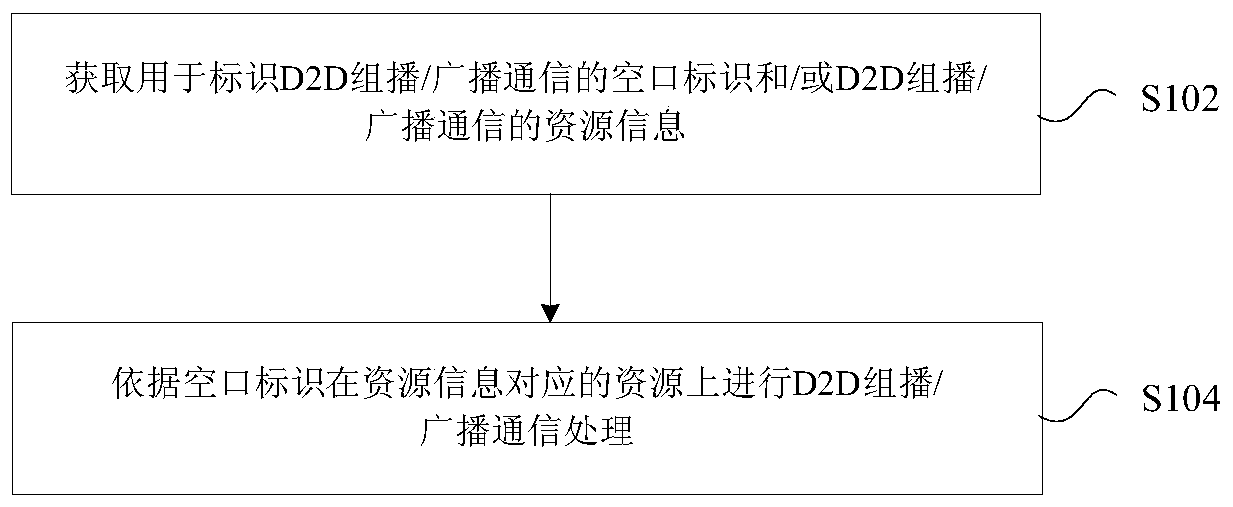
[0113] This embodiment provides a method for establishing D2D multicast broadcast communication in a no-coverage scenario. The feature of this embodiment is that there is no central node for resource coordination and allocation of D2D multicast / broadcast air interface identifiers, and the UE needs to independently complete resource competition and D2D multicast / broadcast air interface identifier mapping or acquisition in a predefined manner. The following is described in detail by Examples 1 to 5.
example 1
[0115] In the public security scenario, Officers A, B, C, and D use public security UE1, UE2, UE3, and UE4 with D2D functions. Officers A, B, C, and D all subscribe to public security services, and UE1, UE2, and UE3 are configured to belong to D2D communication group X, while UE4 belongs to D2D communication group Y. Before Officers A, B, C, and D arrive at the rescue location, the D2D communication group identifier GID and wireless resource information for public safety are known in advance, where the wireless resource information may include frequency point and frequency band information. After arriving at the rescue location, none of them are within the coverage of the network, but UE1, UE2, UE3, and UE4 are within the D2D communication range of each other.
[0116] At the rescue site, Officer A wants to initiate a multicast communication to inform other Officers in the group of related information. UE1 of Officer A monitors the usage of pre-allocated wireless resources, a...
example 2
[0119] In the public security scenario, Officers A, B, C, and D use public security UE1, UE2, UE3, and UE4 with D2D functions. Officers A, B, C, and D all subscribe to public security services, and UE1, UE2, and UE3 are configured to belong to D2D communication group X, while UE4 belongs to D2D communication group Y. Before Officers A, B, C, and D arrive at the rescue location, they should know the GID of the D2D communication group application layer and the wireless resource information for public safety in advance, where the wireless resource information can include frequency point and frequency band information. After arriving at the rescue location, none of the UEs is within the coverage of the network, but UE1, UE2, UE3, and UE4 are within the D2D communication range of each other.
[0120] At the rescue site, Officer A wants to initiate a multicast communication to inform other Officers in the group of related information. At the same time, UE2, UE3, and UE4 of Officer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com