Mobile terminal user identity authentication method based on multi-finger touch behavior characteristics
An authentication method and multi-finger touch technology, applied in the field of mobile terminal user identity authentication, can solve the problems of high cost, easy forgetting of passwords, inapplicability and no related equipment, etc., and achieve the effect of reduced success rate and good security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
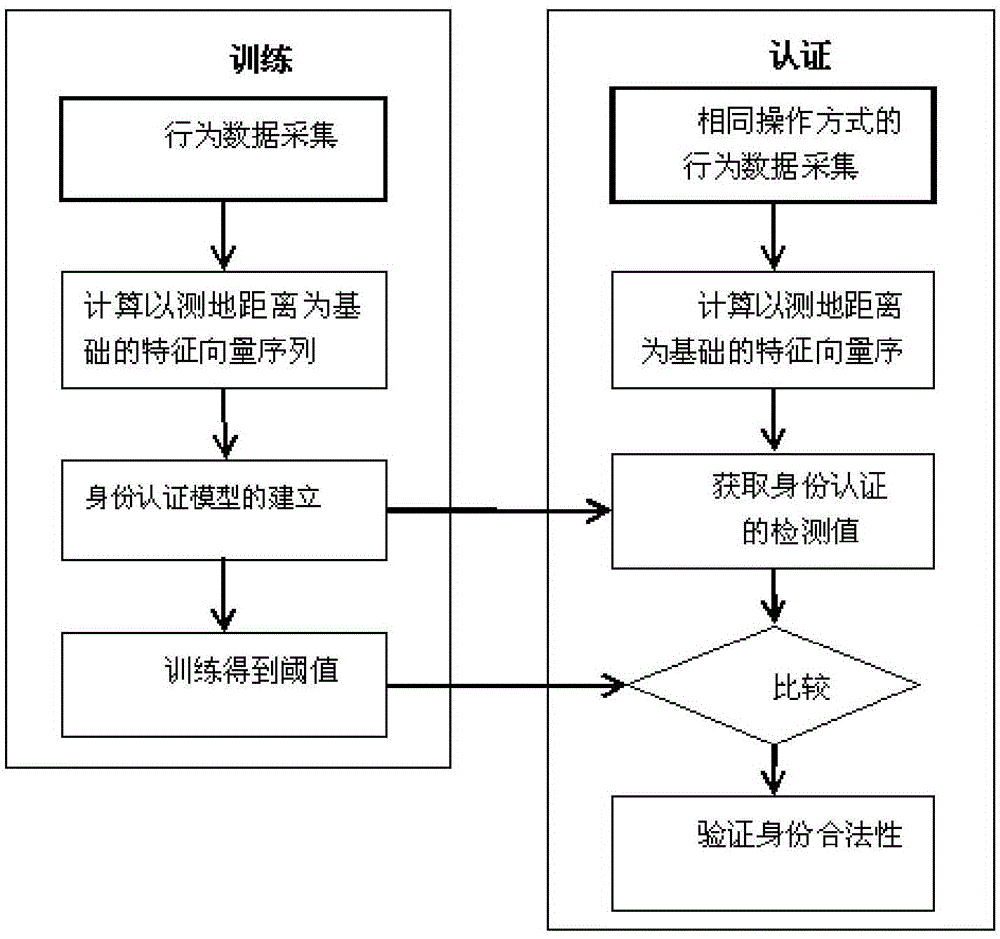
[0025] An intelligent mobile terminal authentication method based on multi-finger touch behavior characteristics, comprising:
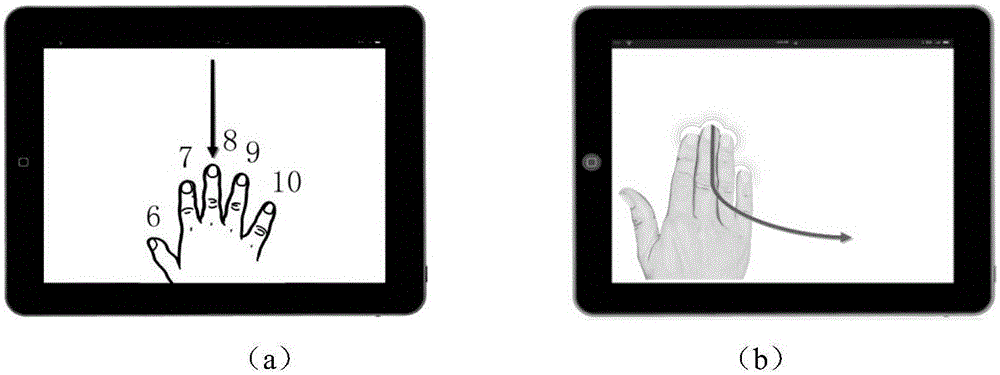
[0026] (1) Obtain the user's touch screen operation information through multi-finger touch screen operation, wherein the multi-finger touch screen operation is the touch screen sliding of multiple fingers in a close state;
[0027] (2) Extract the physiological and behavioral features of the touch screen from the user's touch screen operation information, and combine the above features into a feature vector, the physiological feature is the relative distance of the touch point at each moment; the behavioral feature includes describing different trajectories The pattern of time-dependent velocity, acceleration, pressure and contact area is described;
[0028] (3) utilize the eigenvector of described merging to carry out training to probabilistic neural network classifier and support vector machine classifier, generate the training model of legal user; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com