A Database-Based Encryption Method for Embedded System
An embedded system and encryption method technology, applied in the field of system management, can solve the problems of inconvenient administrator passwords and registration code keys, inability to restrict illegal copying of firmware, inability to use configuration file system functions or modules, etc., and achieve convenient parameters. The effect of passing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below according to the accompanying drawings.
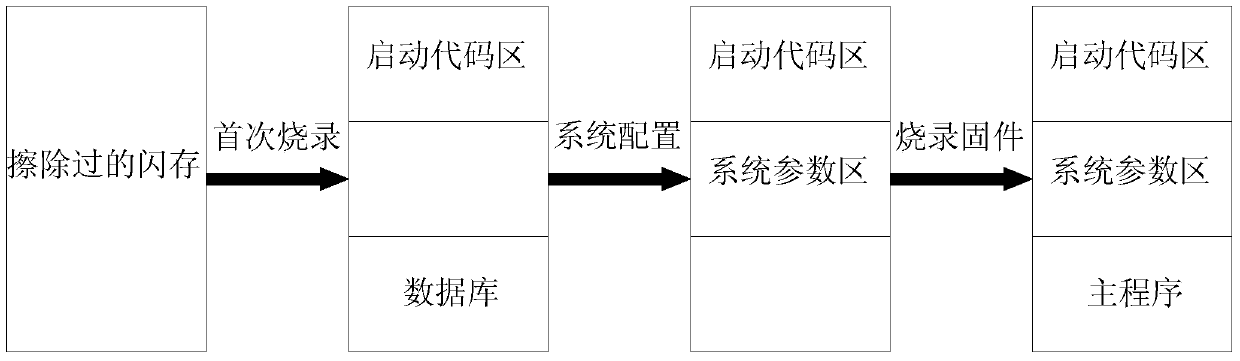
[0021] Such as figure 1 As shown, the FLASH is divided into three areas: the startup code area, the system parameter area and the database / main program area.
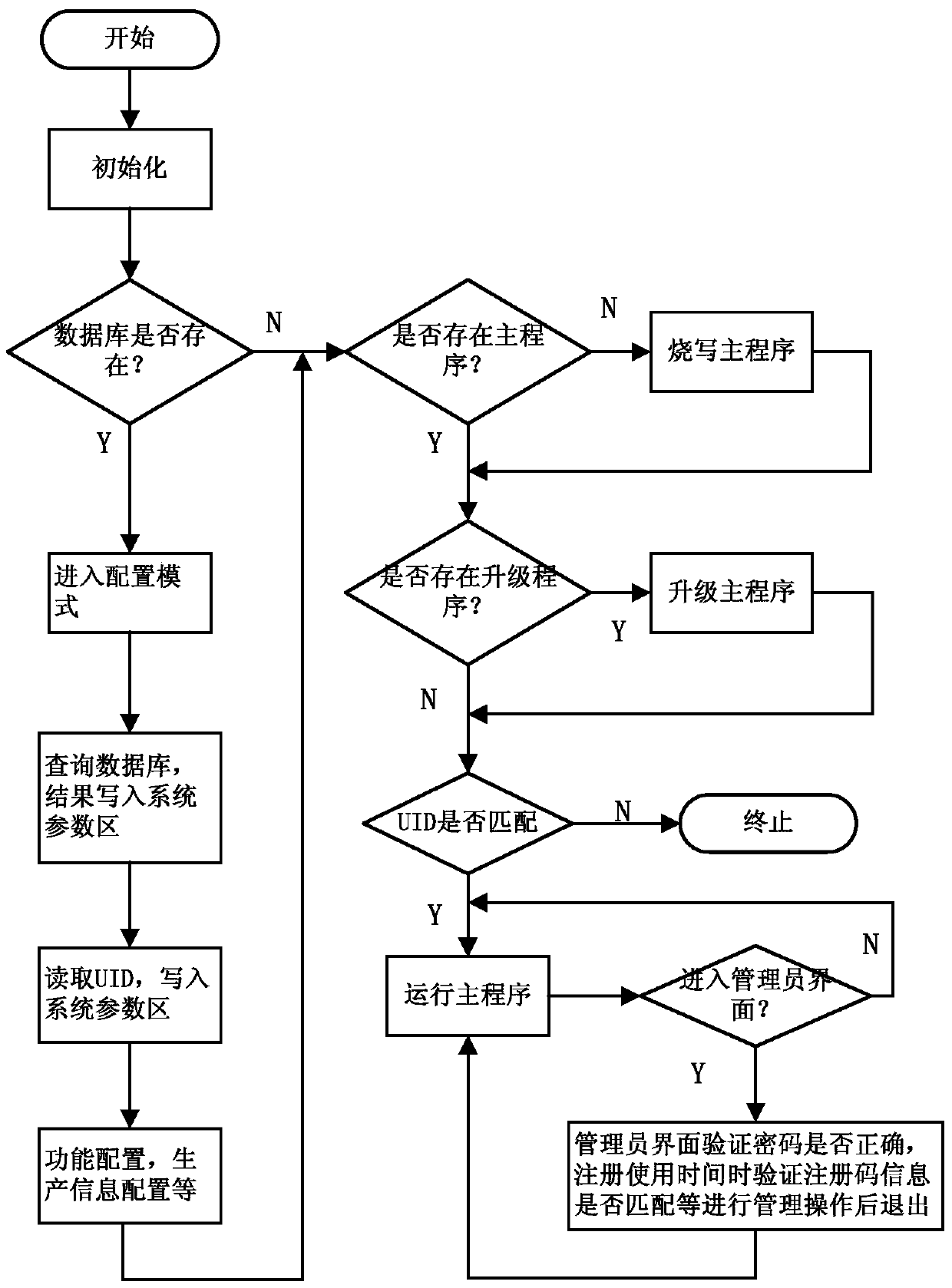
[0022] After initializing the system, the startup code area has two modes by judging the content stored in the database / main program area: configuration mode and normal mode.
[0023] Configuration mode: When it is judged that the database / main program area is stored in the database, enter the configuration mode. In the configuration mode, many operations can be performed with the participation of the user, such as: query the database, extract and store the relevant data such as the administrator password and registration code key in the database to the system parameter area; read the chip UID and store it in the system parameter area; generate configuration files, store them in the system parameter area, etc.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com