Decryption engine and decryption method
An engine and decryption technology, applied in the decryption engine and related decryption fields, which can solve the problems of synchronization failure, bad user experience, and users unable to watch images.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
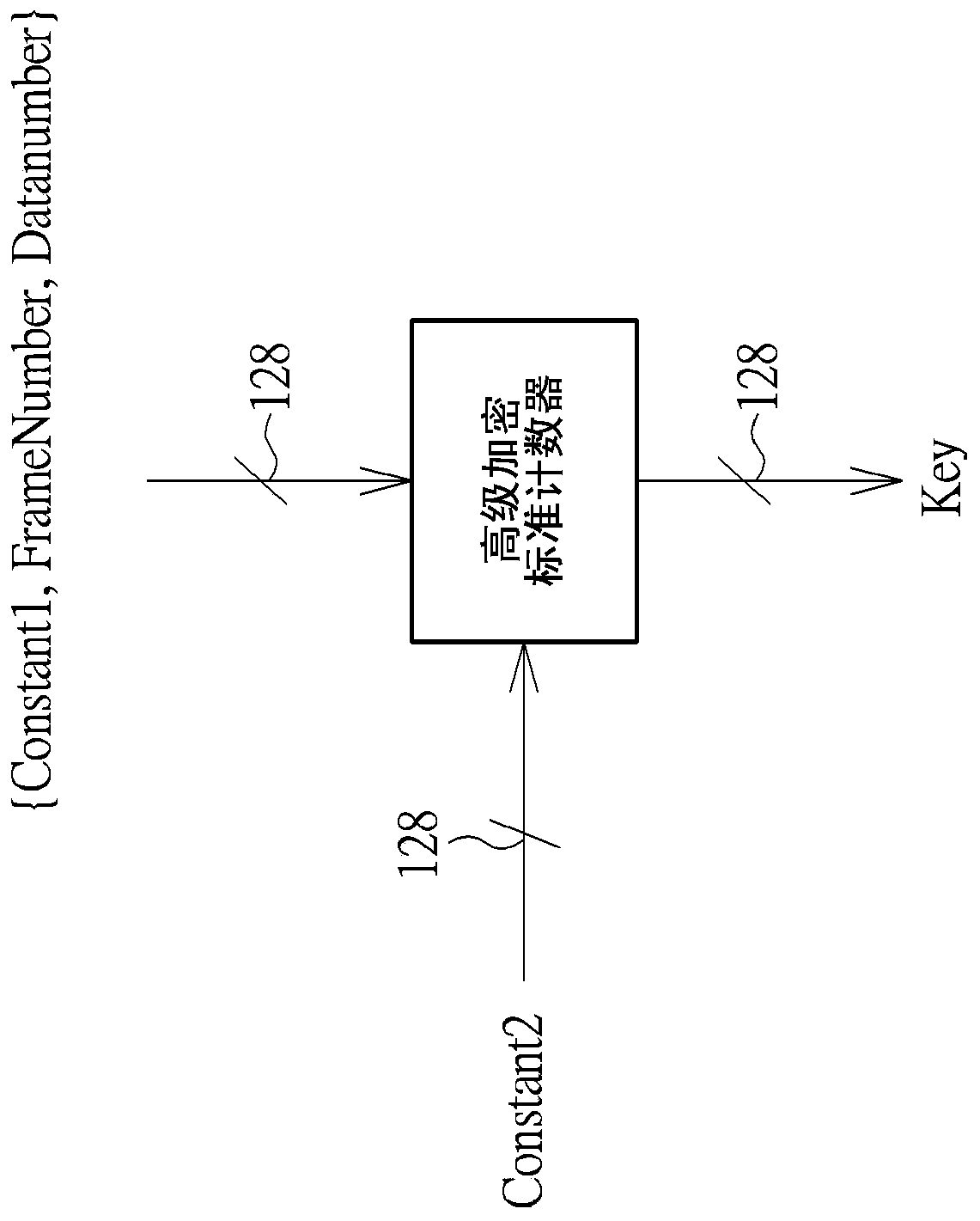
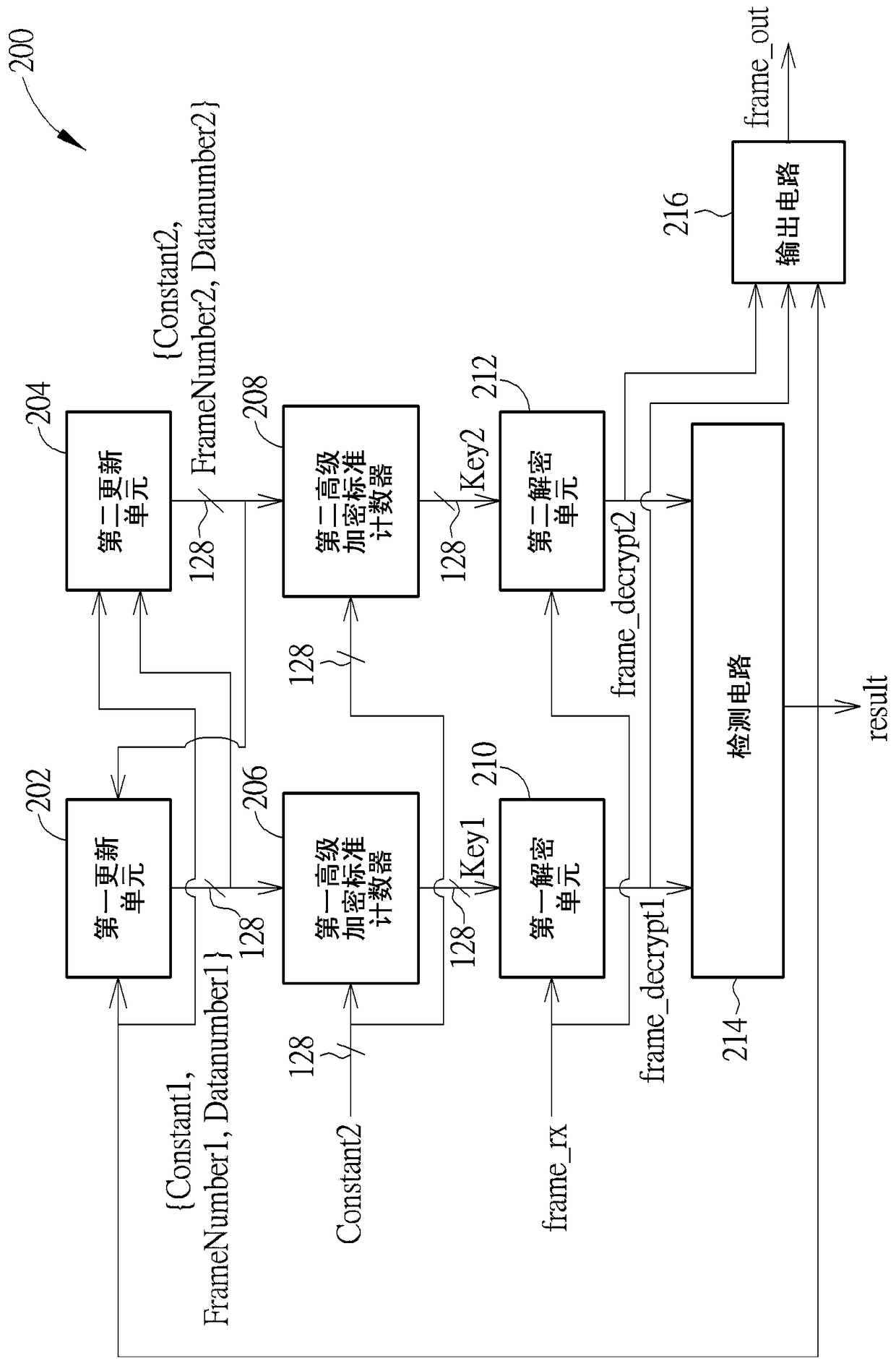
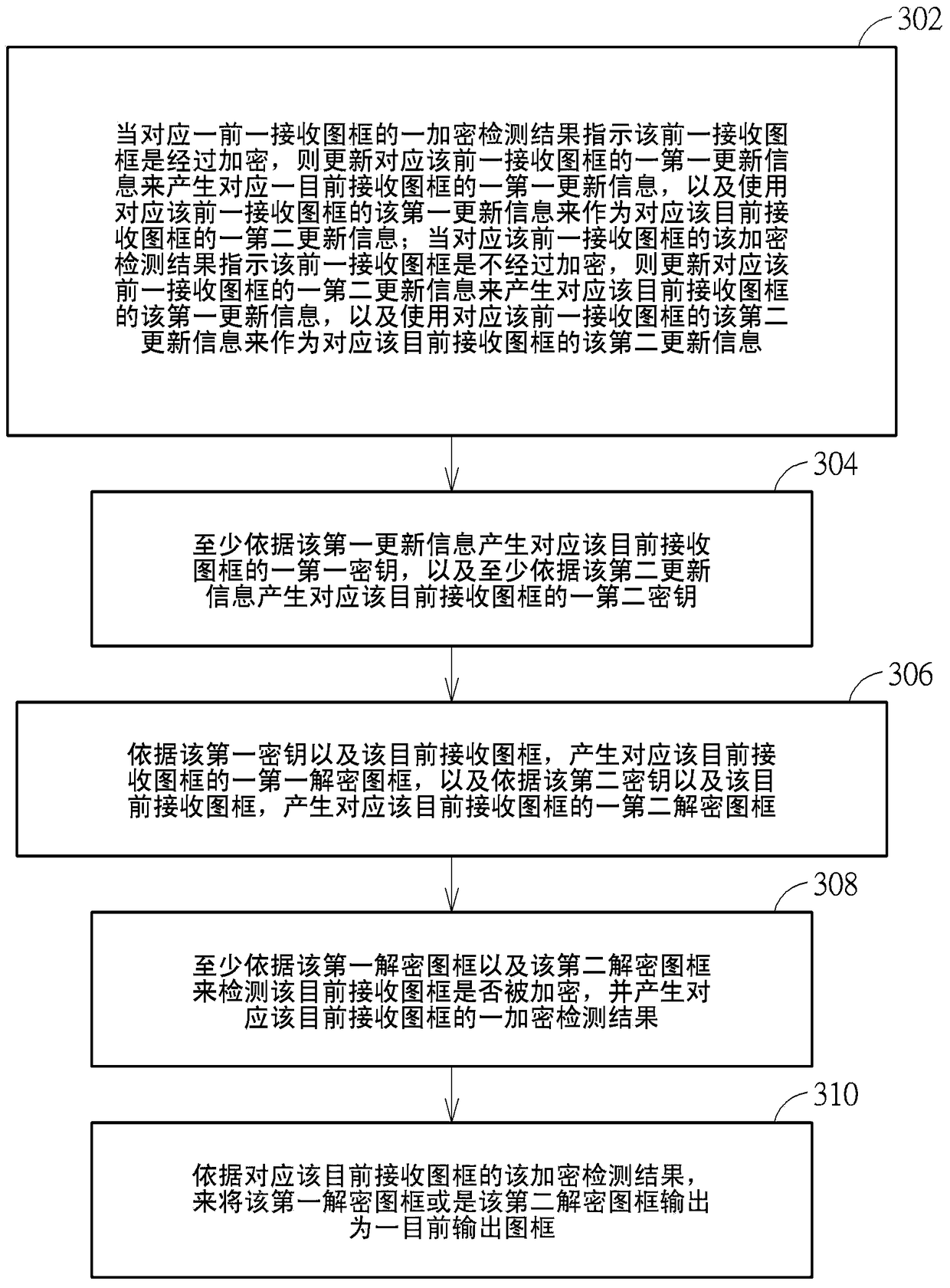
[0022] Therefore, one of the objectives of the present invention is to disclose a decryption engine and a decryption method to solve the problems in the prior art. figure 1 As the well-known advanced encryption standard counter (Advanced Encryption Standard Counter, AES-CTR), in general, a receiving end can obtain a first constant Constant1 and a second constant Constant2 after going through an authentication process with a transmitting end, which are two fixed values respectively. After starting to transmit data (such as frames or packets), the Advanced Encryption Standard counter needs to calculate the key Key according to the first constant Constant1, the second constant Constant2, the frame number FrameNumber and the data number DataNumber. The frame number FrameNumber is used to indicate the number of frames that have been decrypted; the data number DataNumber is used to indicate the number of keys that have been generated. Normally, the transmitting end will transmit ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com