A Method of Extracting Zero Watermark from Network Data Flow Using Information Entropy and Hash Function
A technology of hash function and zero watermark, applied in the field of confirming the relationship between communication parties in an anonymous network environment, which can solve the problems of high false positive rate and false negative rate, limited router storage resources, and easy loss of packet records.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
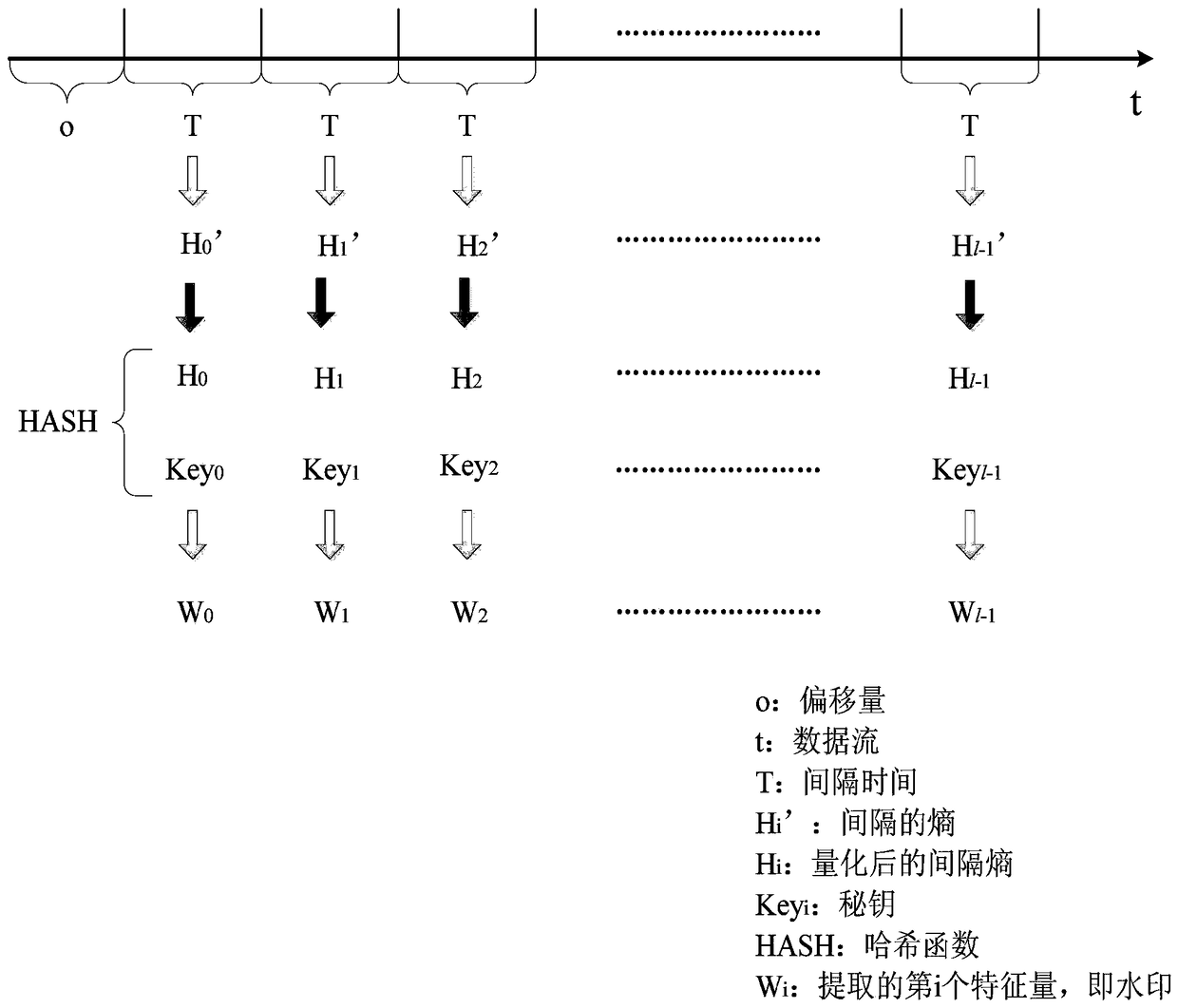
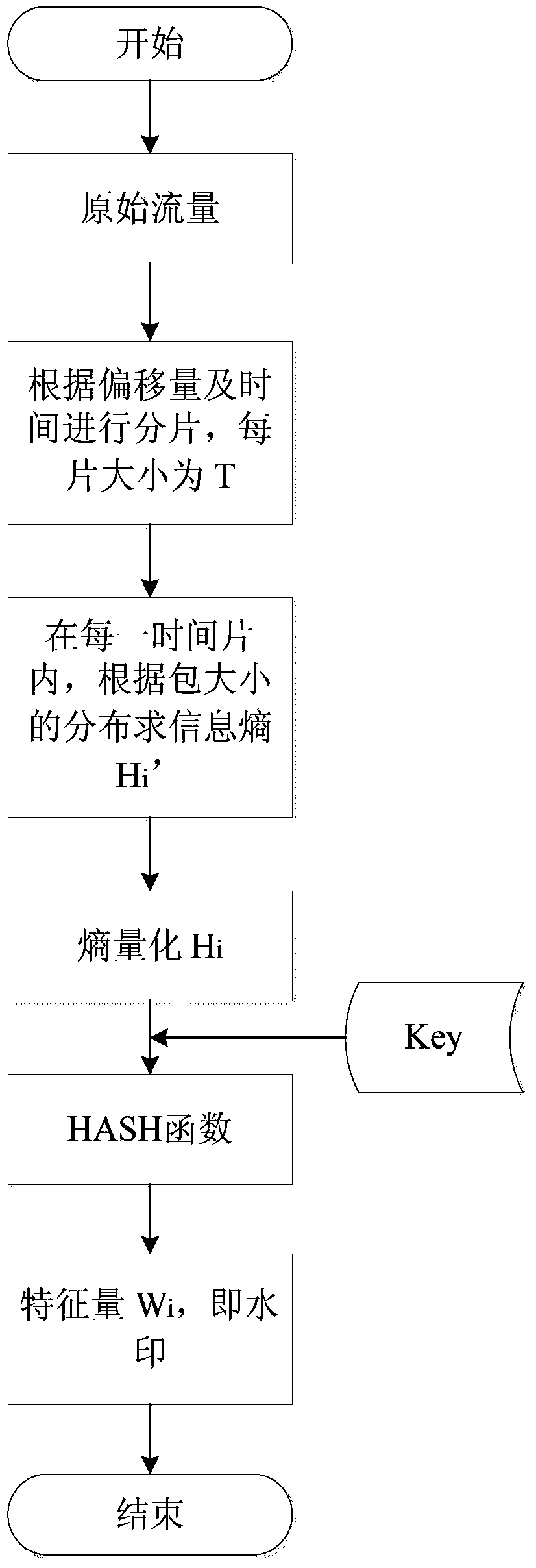
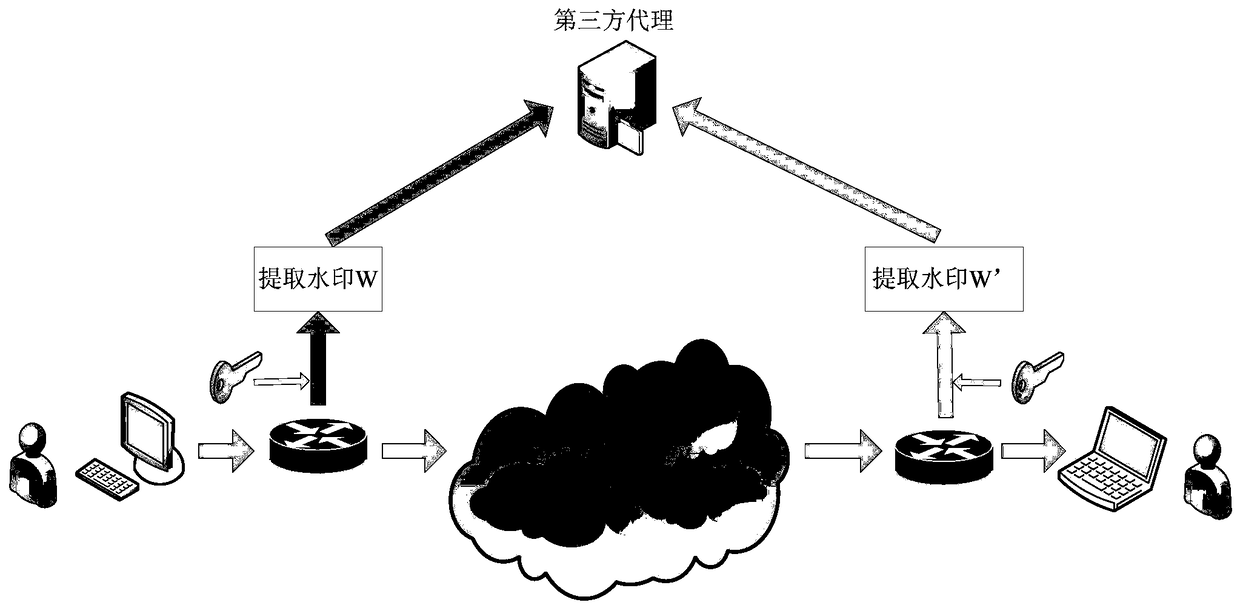
[0050] see Figure 1 to Figure 5As shown, a method of using information entropy and hash function to extract the zero watermark of the network data flow in the present invention includes: in the original flow of the sending end, by fragmenting the data flow according to time, and counting the distribution of the data packet size and calculate the Shannon entropy, and use the hash function to extract the zero watermark; at the receiving end, use the same method to extract the zero watermark from the received traffic again; confirm the transmission by comparing the zero watermark extracted at both ends Whether there is an obvious network communication relationship between the terminal and the receiving terminal.
[0051] The steps of extracting the network stream zero watermark are:
[0052] A1. Obtain the original data stream t at the sending end, select an appropriate offset o, and slice the data stream according to a certain time slice size T to obtain l time slices;
[005...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com