A privacy protection method for health data based on k-anonymity
A privacy protection and health data technology, applied in the field of privacy protection with low information loss, can solve the problems of inability to prevent consistency attacks and background knowledge attacks, achieve flexible anonymous processing, prevent consistency attacks, and balance processing speed and information loss degree relationship effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
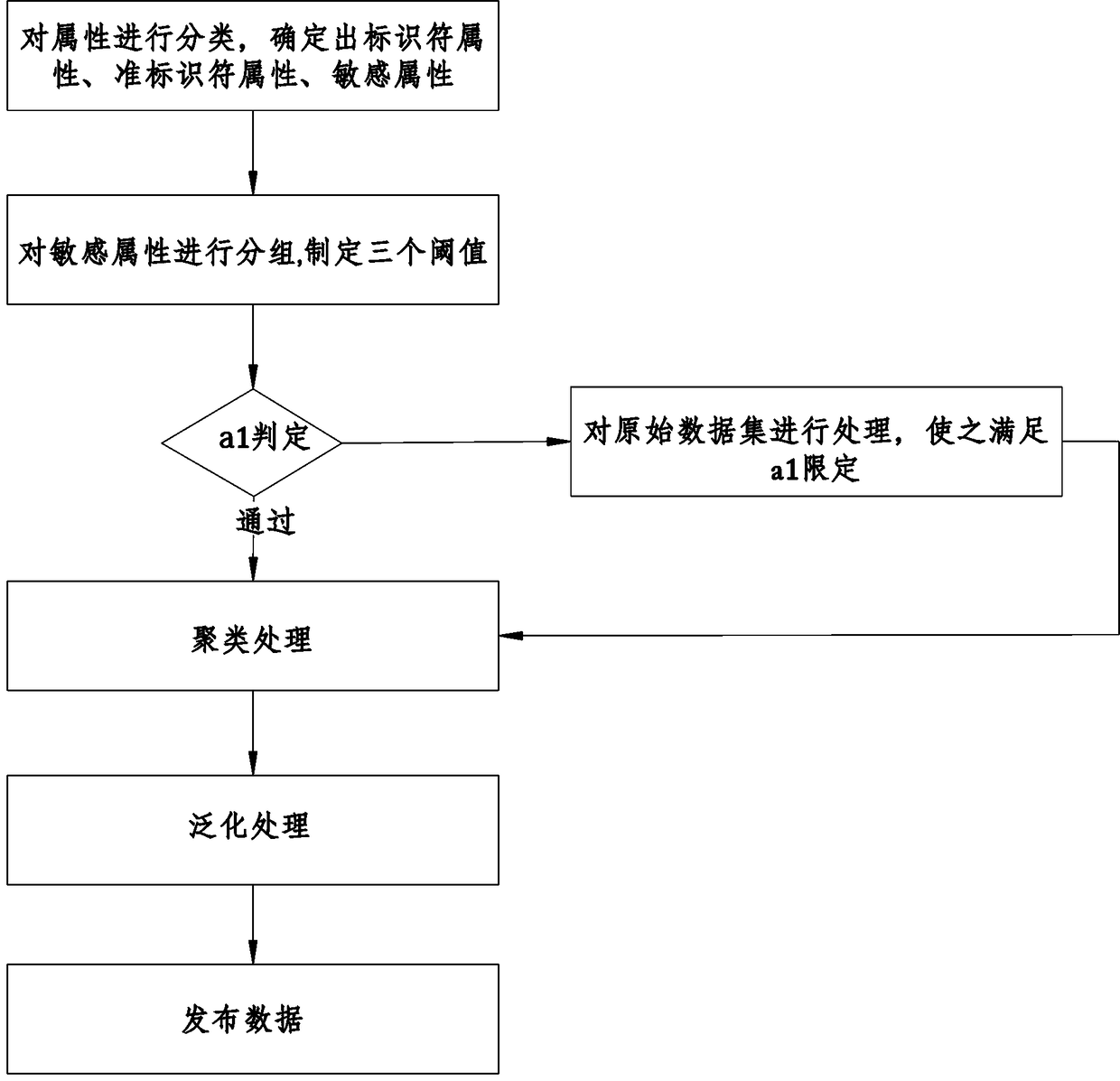
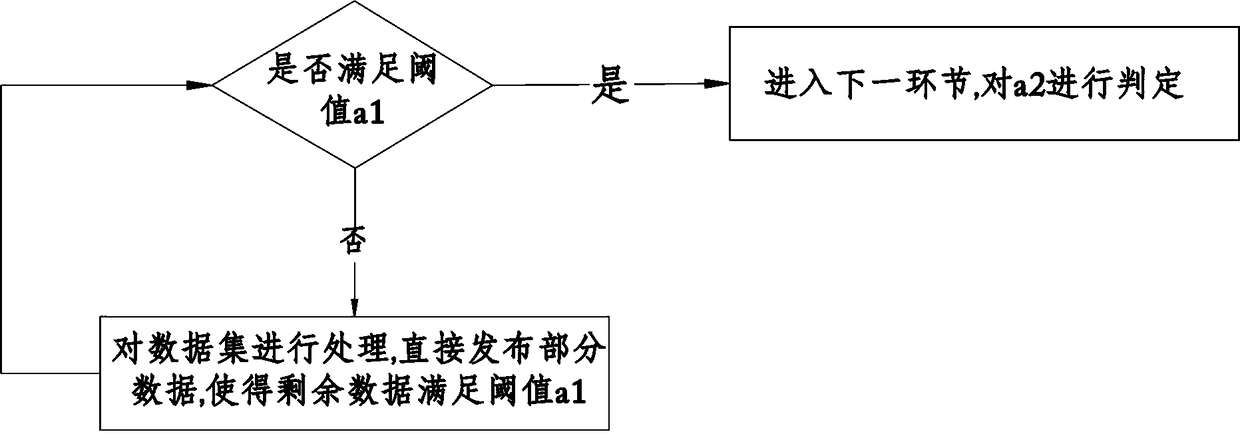
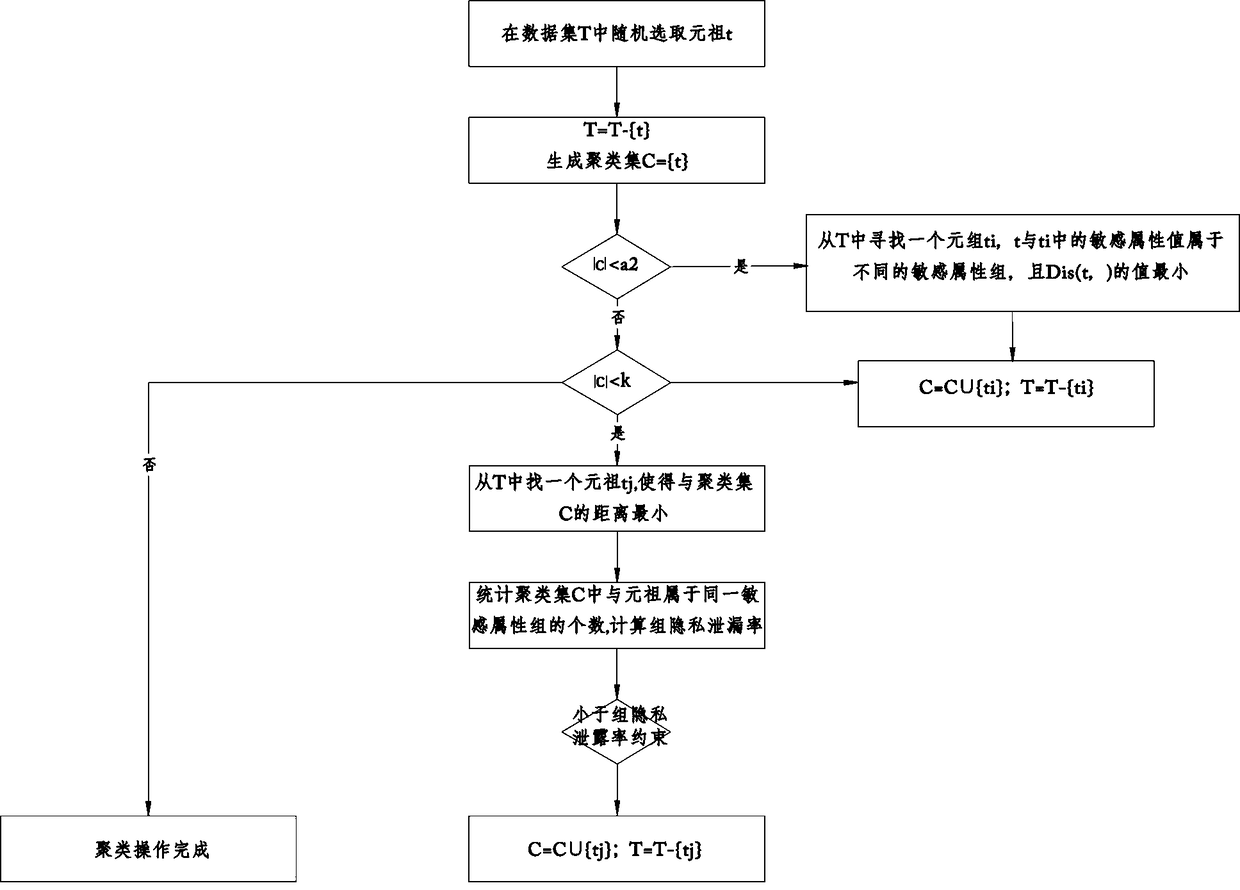
[0035] A method for protecting health data privacy based on K-anonymity, comprising the following steps:
[0036] Determine the identifier attributes, sensitive attributes, and quasi-identifier attributes of the published data;
[0037] Identifier attribute: If an attribute in the data table can uniquely identify an individual, it can directly determine a specific individual, such as name, passport number, phone number and other attributes. Such attributes are called identifier attributes. When data is published, this attribute is generally removed directly from the table.
[0038] Quasi-identifier attribute (Quasi-identifiers, QI): The quasi-identifier attribute is a set of attributes that exist in both the published data table and the external data source table, such as a set of attributes for zip code, date of birth, and gender. The attribute set is used...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com