Identification code generation method, device, identification code decryption method and device
A technology for identifying codes and generating units, applied to public keys, electrical components, transmission systems, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
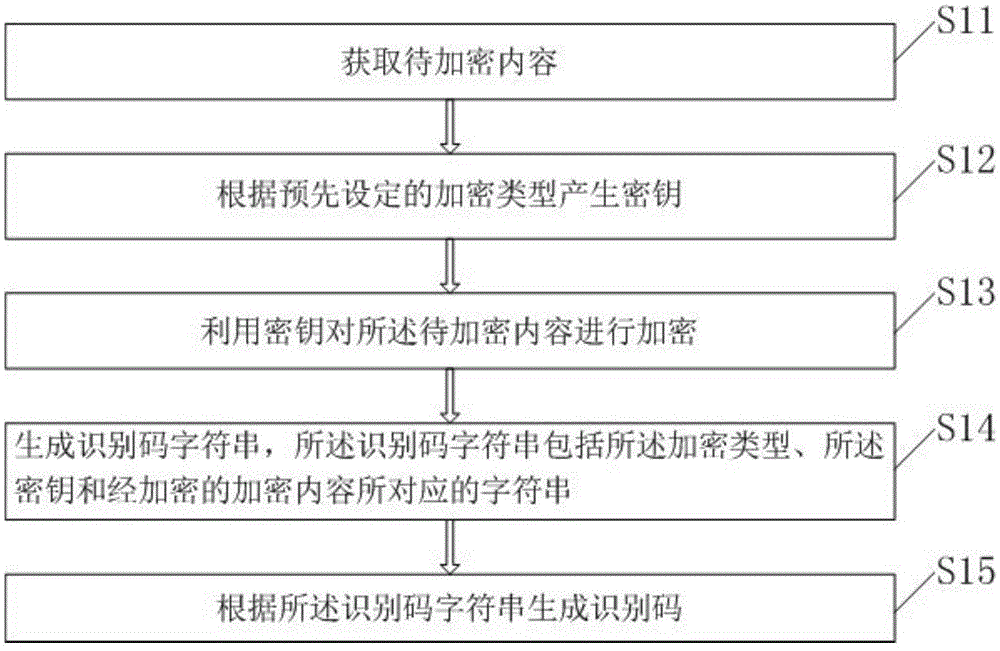
[0055] This embodiment provides a method for generating an identification code, such as figure 1 Shown include:
[0056] S11. Obtain content to be encrypted. The content to be encrypted may be various business contents, such as certain commodity information, including commodity name, code, quantity and so on.
[0057] S12. Generate a key according to a preset encryption type. The encryption type refers to the method of encrypting the content to be encrypted, or is called an encryption algorithm. In practical applications, an encryption type can be selected according to actual business needs. Preferably, the encryption type includes AES (AdvancedEncryptionStandard), which is an advanced encryption algorithm in cryptography, DES (DataEncryptionStandard), which is a data encryption algorithm, TDES (TripleDataEncryptionAlgorithm), which is a triple data encryption algorithm, or a private encryption algorithm, which is an encryption algorithm. Encryption algorithm created by th...
Embodiment 2
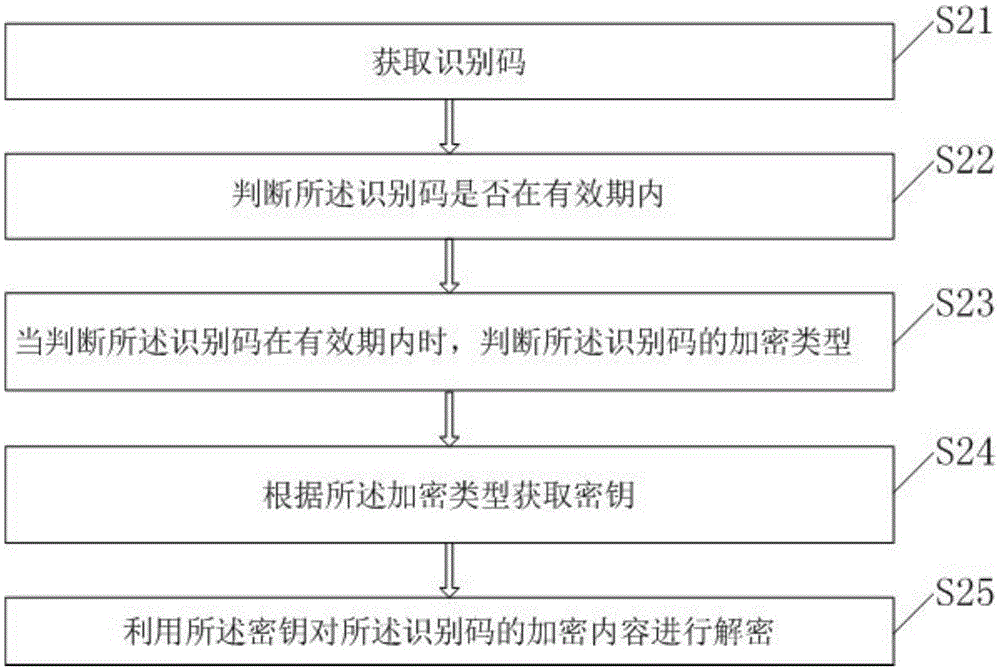
[0066] The present invention also provides a decoding method corresponding to the identification code generated in the first embodiment above, such as figure 2 The method shown includes:
[0067] S21. Obtain an identification code. Specifically, the acquisition method may be scanning and acquisition, and the visible identification code may be converted into a character string after acquisition. Preferably, the identification code may be a two-dimensional code.
[0068] S22. Determine whether the identification code is within the validity period. Specifically, the long character string corresponding to the identification code may be composed of multiple substrings, including a character string used to indicate the validity period, for example, the first four digits of a long character string are a character string indicating the validity period, and its content is A012, According to the recorded validity period data, it can be known that the validity period of the identific...
Embodiment 3
[0077] This embodiment provides an identification code generation device, such as Figure 4 The unit shown consists of:
[0078] A content-to-be-encrypted acquisition unit 41, configured to acquire content to be encrypted;
[0079] A key generating unit 42, configured to generate a key according to a preset encryption type;
[0080] An encryption unit 43, configured to use the key to encrypt the content to be encrypted;
[0081] A character string generating unit 44, configured to generate an identification code character string, the identification code character string including a character string corresponding to the encryption type, the key, and the encrypted encrypted content;
[0082] An identification code generating unit 45, configured to generate an identification code according to the identification code string.
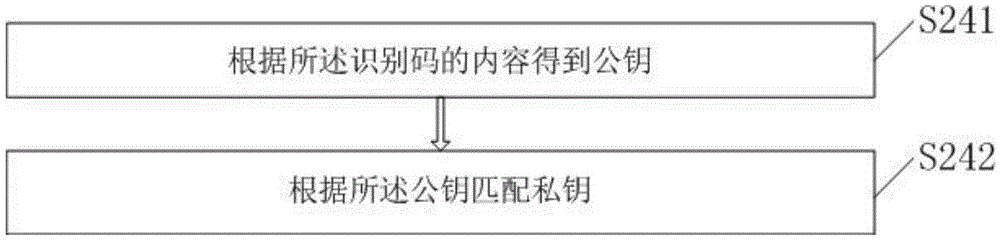
[0083] Preferably, the identification code string generated by the character string generation unit 44 also includes a character string corresponding to ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap