A method for dynamic Internet of things security encryption
A security encryption and Internet of Things technology, which is applied in the field of dynamic Internet of Things security encryption, can solve problems such as inability to achieve automatic processing, and achieve the effects of cost saving, good compatibility, and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] Below in conjunction with accompanying drawing and embodiment, further elaborate the present invention.
[0050] Example to use bluetooth connection between device and phone:
[0051] To transmit data on a wireless device, a connection must be established first. The way to establish a connection is nothing more than entering a password for verification when establishing for the first time, or opening a connection without verification.
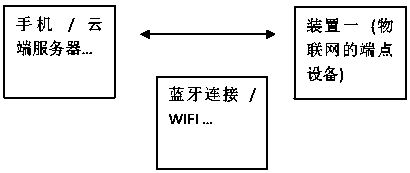
[0052] In this example, if figure 1 As shown, the Bluetooth setting of "Device 1" is set to open connection, and the mobile phone can connect to "Device 1" at any time. In this way, there is no security authentication mechanism at all.
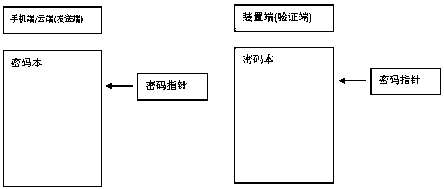
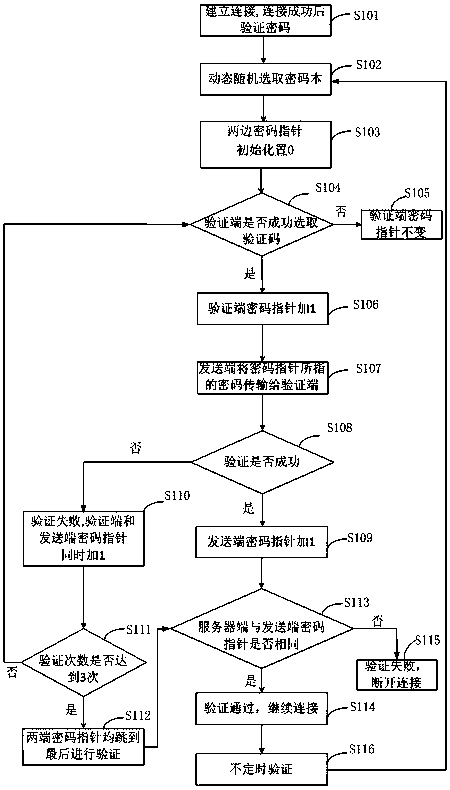
[0053] The way of password acquisition in the method of the present invention is as follows: figure 2 Shown, the flow process of the inventive method is as image 3 Shown:
[0054] A general non-secure connection is established first. It may be a one-time authentication method, that is, authentic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com