Dynamic tracing method for IP spoofing data packet based on SDN
A data packet and dynamic technology, applied in the field of digital information transmission, can solve the problems of inability to accurately find and send IP spoofing data packets, uncertain matching accuracy of flow table items, etc., and achieve high accuracy and high matching accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
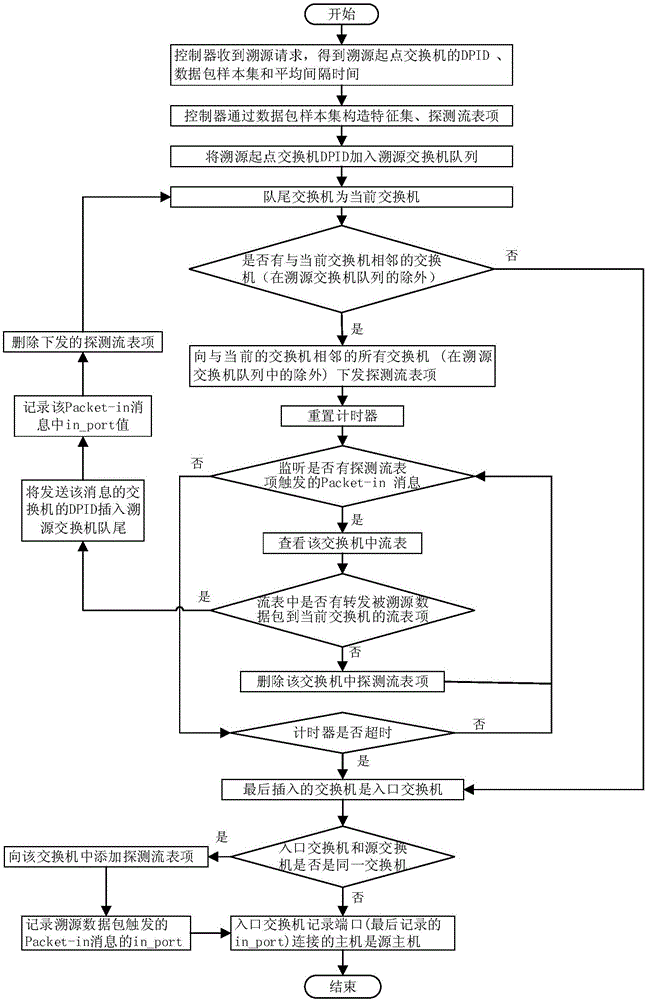
[0046] Figure 5 An example diagram of an implementation method of an application scenario of the present invention is given.
[0047] Figure 5 , the host Attacker uses a forged IP address to send a message to the host Victim, and the sending path of the data packet is Attacker->S4->S3->S2->S1->Victim. Suppose the host Attacker sends more than one such packet to the host Victim. At this time, the traceability requester wants to trace the sending source of this type of data packet. The traceability requester gives the source traceability switch as S1, the data packet sample set and the average interval time. The controller obtains the feature set through the data packet sample set, assuming : Destination IP address (Victim's IP address), IP protocol number, and destination port number of the transport layer. And these three feature items are enough to distinguish this type of data packet from other data packets, and the controller uses these three feature items as the match...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com