Access control method and device
A technology of access control and congestion control, which is applied in the field of wireless communication, and can solve the problems of broken applications and unfavorable applications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
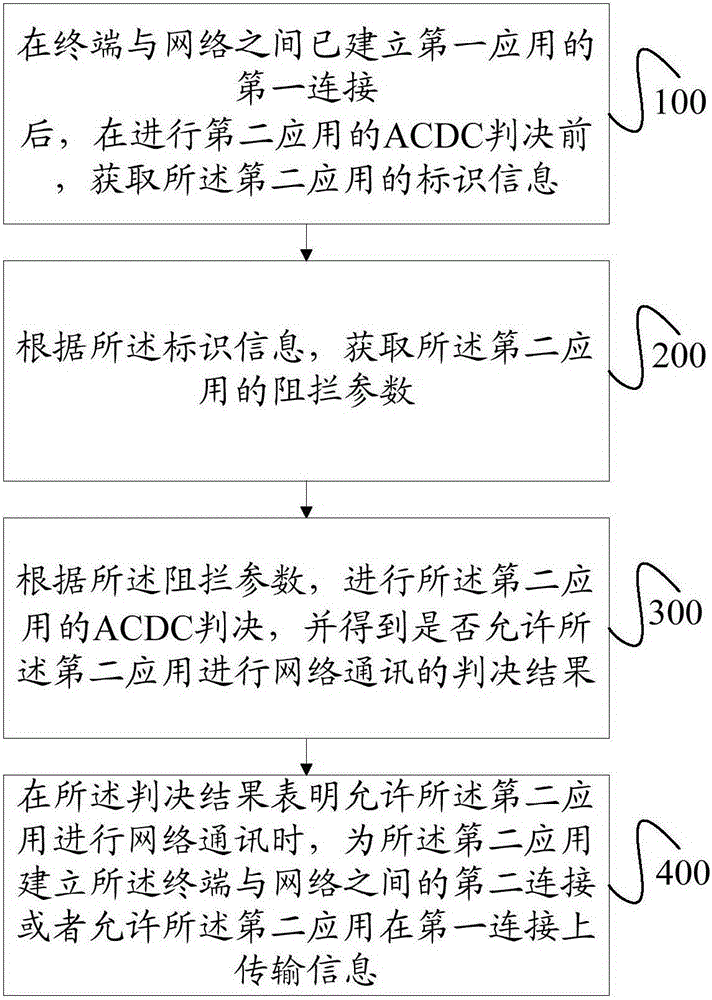
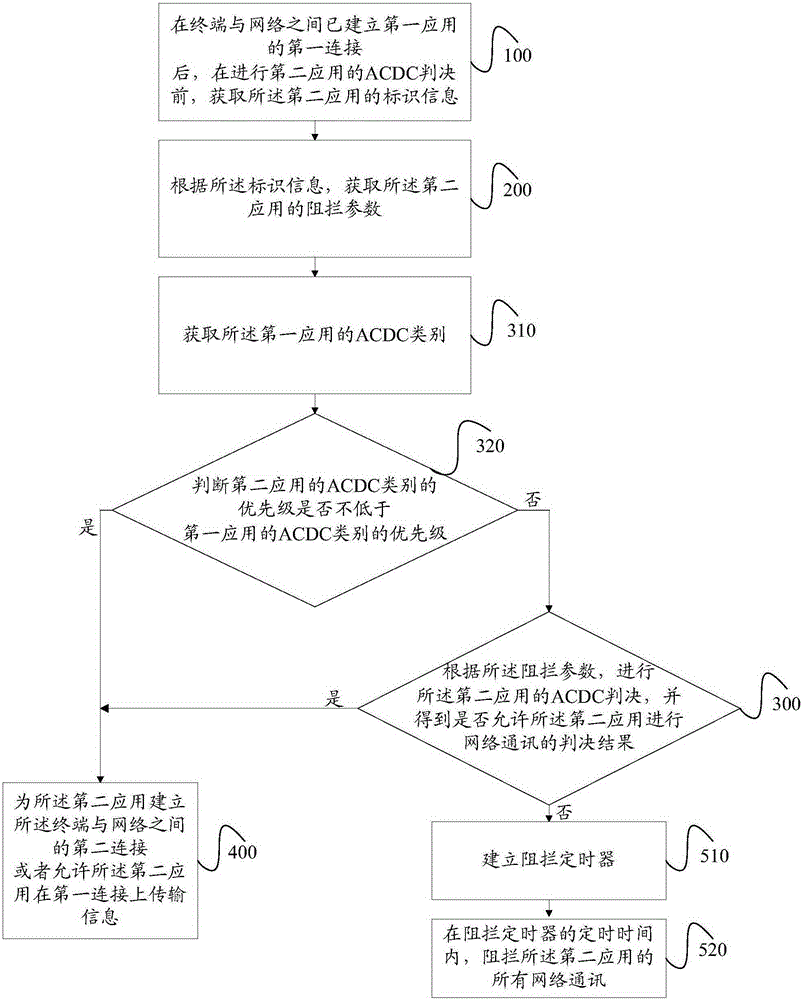
[0173] The implementation method in Embodiment 1 makes it necessary for each new application to make an ACDC decision when accessing the network. This method is more suitable when the priority of the new application is not lower than that of the application that has established a network connection. This way, it does not take advantage of the priority of the new application when it is lower priority than the application with established network connection, so if the figure 2 As shown, on the basis of Embodiment 1, Embodiment 2 of the present invention provides an access control method, including:
[0174] Step 100, after the first connection of the first application is established between the terminal and the network, before the ACDC decision of the second application is made, the identification information of the second application is acquired;
[0175] Step 200, according to the identification information, obtain the blocking parameters of the second application;
[0176] ...
Embodiment 3
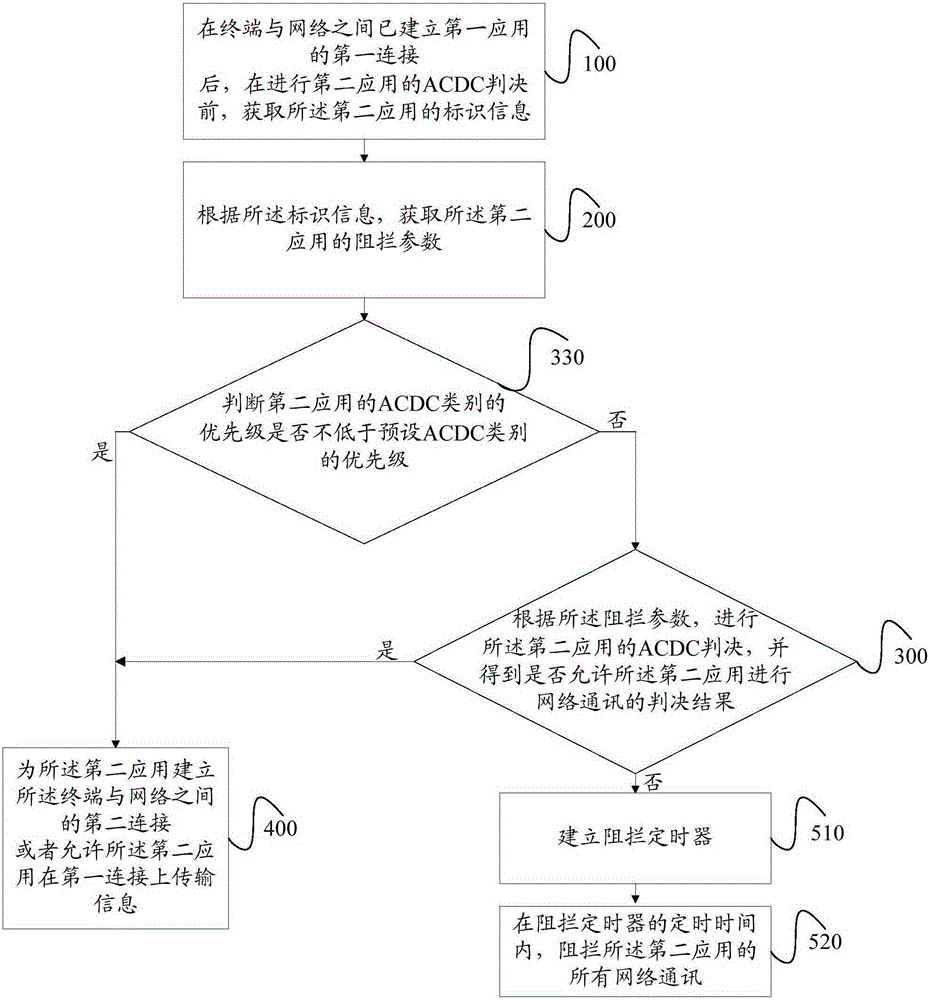
[0194] In the third embodiment, by comparing the ACDC category of the second application with the preset ACDC category, it is determined whether the second application directly accesses the network. This method can reasonably control the number of ACDC decisions made by the application.
[0195] It should be noted that the access control method may be applied to a terminal (UE), may be applied to a base station (eNB), and may also be applied to a core network (MME) side.
[0196] When the access control method is applied to the LTE network, the above-mentioned applications are divided according to the category of the application software, and the specific implementation of the access control method on different application objects is described in detail as follows.
[0197] 1. When the access control method is applied to a terminal
[0198] When the terminal is performing network communication, the data will be transmitted from the upper layer to the lower layer in turn, and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com