An information processing method, terminal and server
An information processing method and server technology, applied in the field of terminals, servers, and information processing methods, can solve problems such as user property loss, inaccurate scanning results, hidden dangers, etc., and achieve the effect of improving scanning efficiency and saving labor and time costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
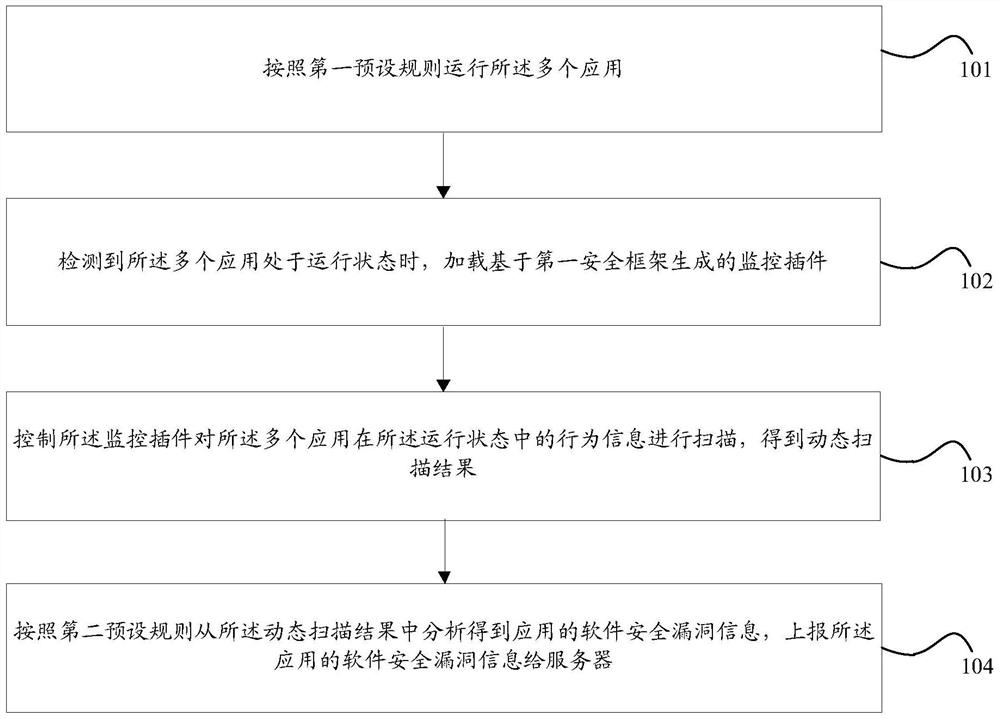
[0070] An information processing method according to an embodiment of the present invention, the method is applied to a terminal, and the terminal is installed with multiple applications, such as figure 1 As shown, the method includes:
[0071] Step 101, run the multiple applications according to a first preset rule;
[0072] Step 102, when it is detected that the multiple applications are running, load the monitoring plug-in generated based on the first security framework;
[0073] Step 103, controlling the monitoring plug-in to scan the behavior information of the multiple applications in the running state to obtain a dynamic scanning result;
[0074] Step 104: Analyzing the application software security vulnerability information from the dynamic scanning result according to the second preset rule, and reporting the application software security vulnerability information to the server.
[0075] Using the embodiment of the present invention, through the automatic dynamic sc...
Embodiment 2
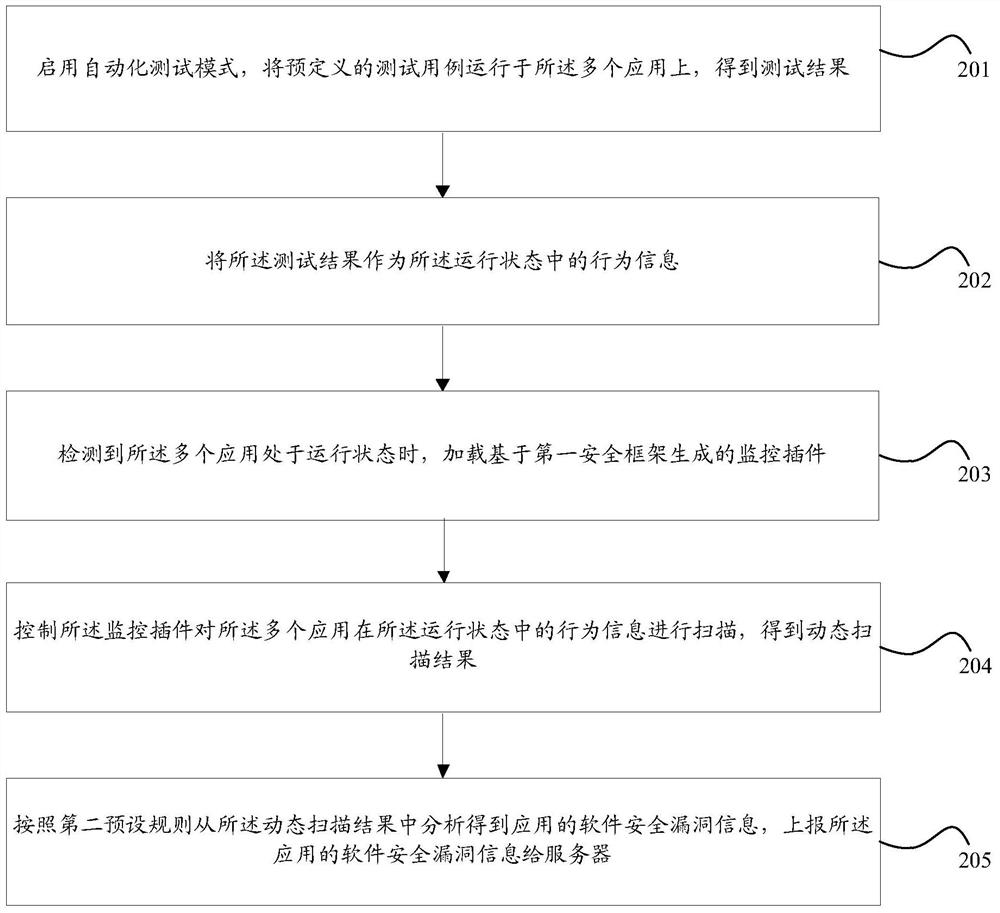
[0079] An information processing method according to an embodiment of the present invention, the method is applied to a terminal, and the terminal is installed with multiple applications, such as figure 2 As shown, the method includes:
[0080] Step 201, enabling the automated test mode, running predefined test cases on the multiple applications, and obtaining test results;
[0081] Step 202, using the test result as behavior information in the running state;
[0082] Step 203, when it is detected that the multiple applications are running, load the monitoring plug-in generated based on the first security framework;
[0083] Step 204, controlling the monitoring plug-in to scan the behavior information of the multiple applications in the running state to obtain a dynamic scanning result;
[0084] Step 205: Analyzing the application software security vulnerability information from the dynamic scanning result according to the second preset rule, and reporting the application s...
Embodiment 3
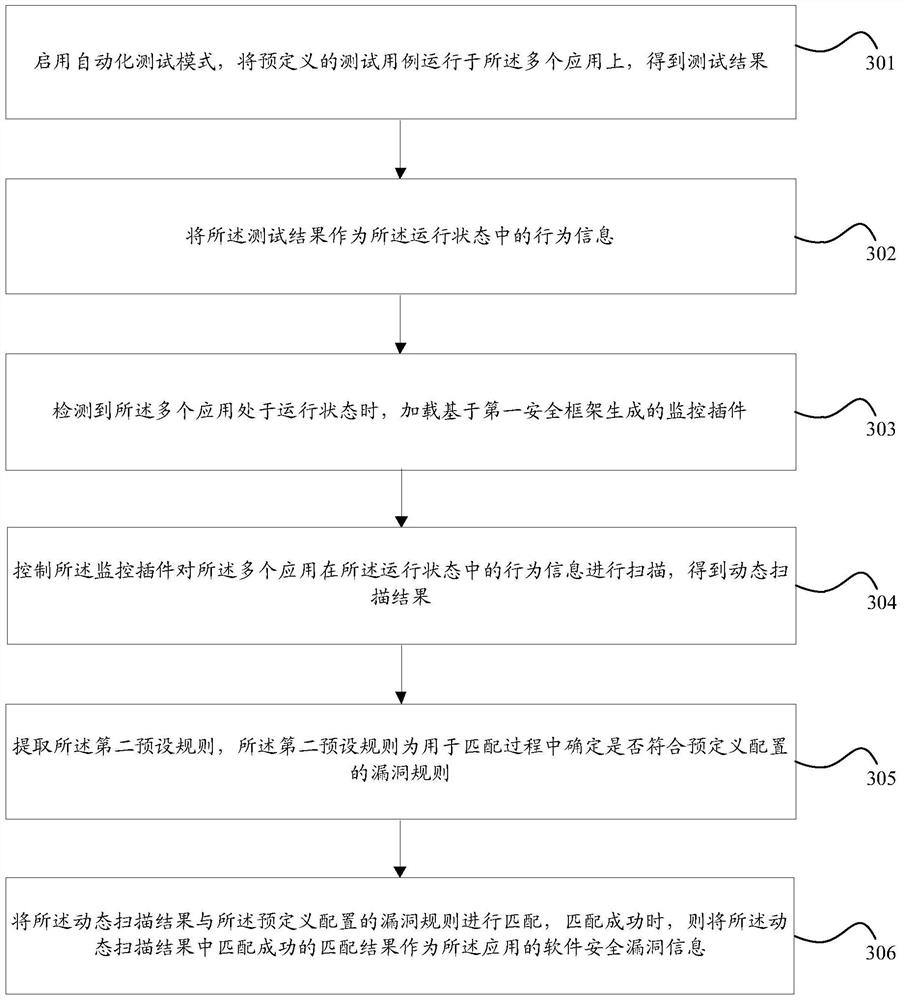
[0100] An information processing method according to an embodiment of the present invention, the method is applied to a terminal, and the terminal is installed with multiple applications, such as image 3 As shown, the method includes:
[0101] Step 301, enabling the automated test mode, running predefined test cases on the multiple applications, and obtaining test results;
[0102] Step 302, using the test result as behavior information in the running state;
[0103] Step 303, when it is detected that the multiple applications are running, load the monitoring plug-in generated based on the first security framework;
[0104] Step 304, controlling the monitoring plug-in to scan the behavior information of the multiple applications in the running state to obtain a dynamic scanning result;
[0105] Step 305, extracting the second preset rule, the second preset rule is a vulnerability rule used in the matching process to determine whether it conforms to the predefined configurat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com