User terminal unlocking method and device and user terminal
A user terminal, unlocking technology, applied in the direction of digital data authentication, etc., can solve the problem of single unlocking method, and achieve the effect of enriching unlocking methods and improving fun.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
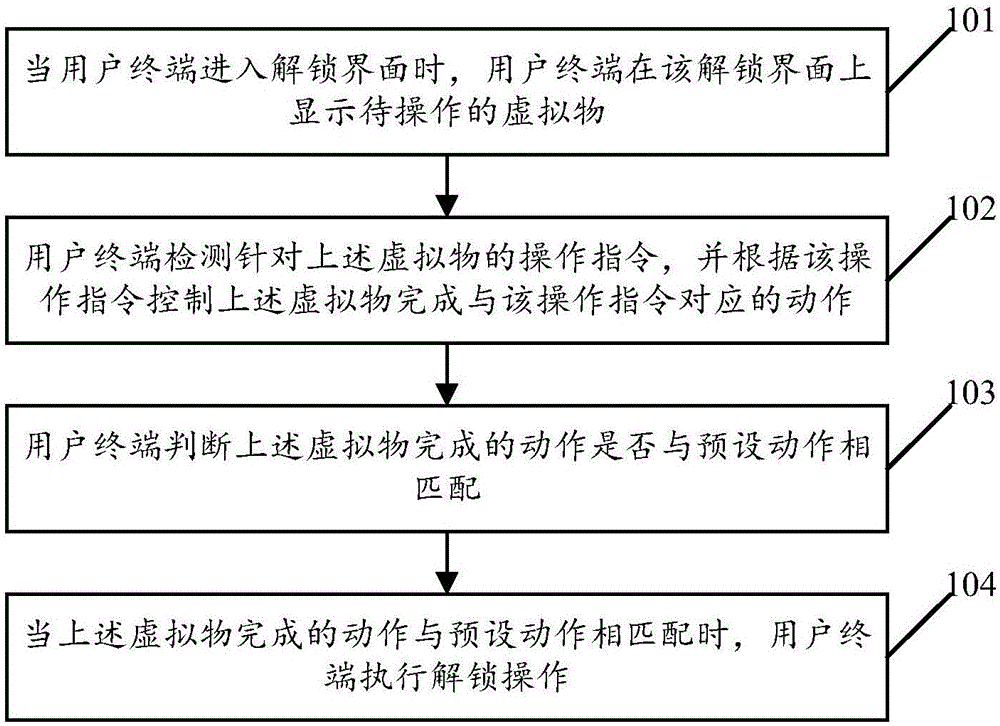
[0067] see figure 1 , figure 1 It is a schematic flowchart of a method for unlocking a user terminal disclosed in an embodiment of the present invention. in, figure 1 The described method for unlocking a user terminal can be applied to user terminals such as smart phones (Android phones, iOS phones, etc.), smart watches, smart bracelets, tablet computers, handheld computers, and mobile Internet devices (Mobile Internet Devices, MIDs). The embodiments of the invention are not limited. Such as figure 1 As shown, the unlocking method of the user terminal may include the following operations:
[0068] 101. When the user terminal enters an unlock interface, the user terminal displays a virtual object to be operated on the unlock interface.
[0069] In the embodiment of the present invention, when the user terminal detects the user's unlock instruction for the user terminal in the locked state, the user terminal can output an unlock interface, and display the virtual object to ...
Embodiment 2
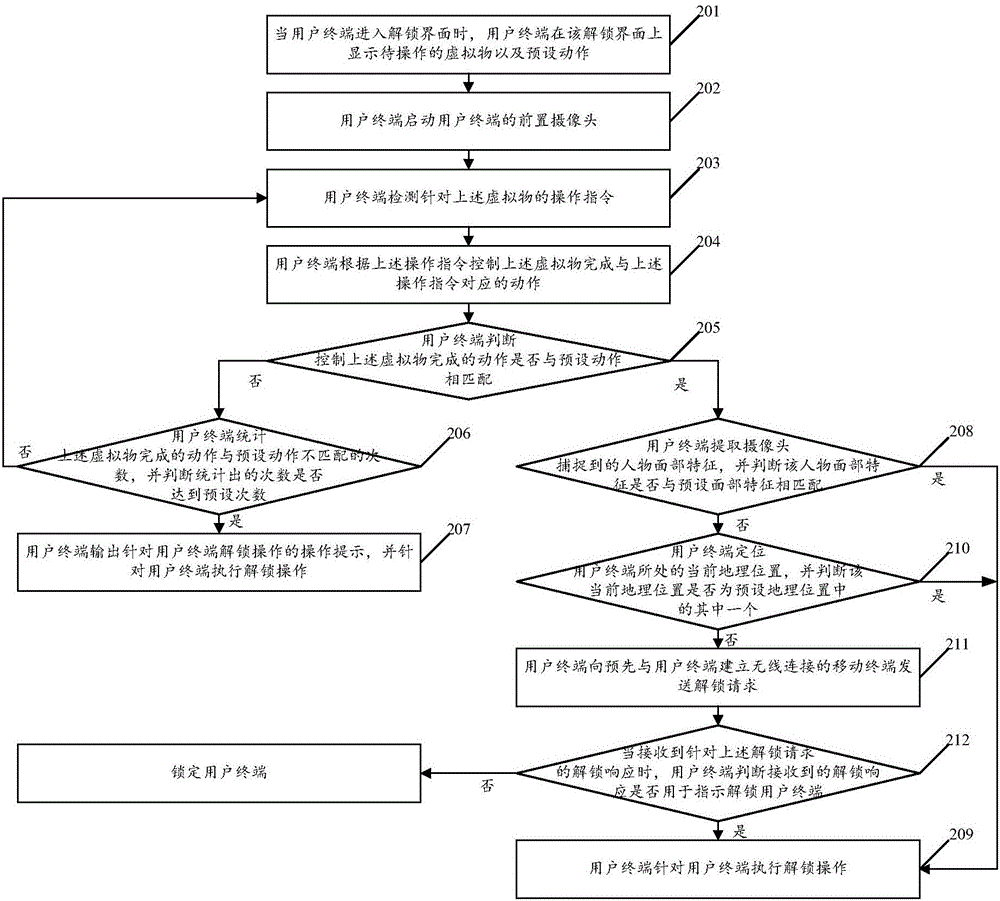
[0090] see figure 2 , figure 2It is a schematic flowchart of another method for unlocking a user terminal disclosed in an embodiment of the present invention. in, figure 2 The described method for unlocking a user terminal can be applied to user terminals such as smart phones (Android phones, iOS phones, etc.), smart watches, smart bracelets, tablet computers, handheld computers, and mobile Internet devices (Mobile Internet Devices, MIDs). The embodiments of the invention are not limited. Such as figure 2 As shown, the unlocking method of the user terminal may include the following operations:
[0091] 201. When the user terminal enters an unlock interface, the user terminal displays a virtual object to be operated and a preset action on the unlock interface.
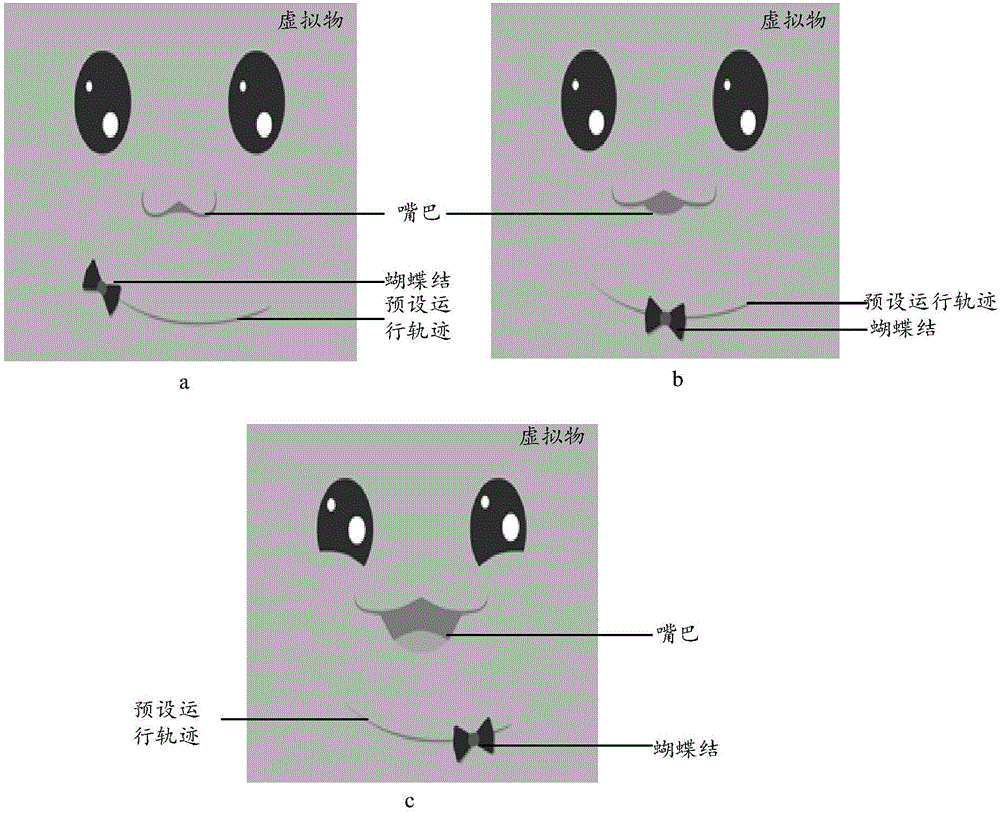
[0092] In the embodiment of the present invention, the preset action is used to indicate that the virtual object needs to complete the preset expression, and the preset expression can be determined according to...
Embodiment 3
[0120] see Figure 4 , Figure 4 It is a schematic structural diagram of an unlocking device for a user terminal disclosed in an embodiment of the present invention. in, Figure 4 The described unlocking device 400 for a user terminal can be applied to user terminals such as smart phones (Android phones, iOS phones, etc.), smart watches, smart bracelets, tablet computers, palmtop computers, and mobile Internet devices (Mobile InternetDevices, MIDs), The embodiments of the present invention are not limited. Such as Figure 4 As shown, the unlocking device 400 of the user terminal may include a display unit 401, a detection unit 402, a control unit 403, a judging unit 404, and an unlocking unit 405, wherein:
[0121] The display unit 401 is used for displaying a virtual object to be operated on the unlocking interface when the user terminal enters the unlocking interface.
[0122] The detection unit 402 is configured to detect an operation instruction for the virtual object...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com