Apk security risk automatic static auditing system and method
A security risk, static technology, applied in the field of mobile information security, can solve the problems of large amount of log information, unaudited code normative, too much redundant information, etc., to reduce workload, review efficiency, and reduce workload. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described in detail below in conjunction with the drawings and specific embodiments.
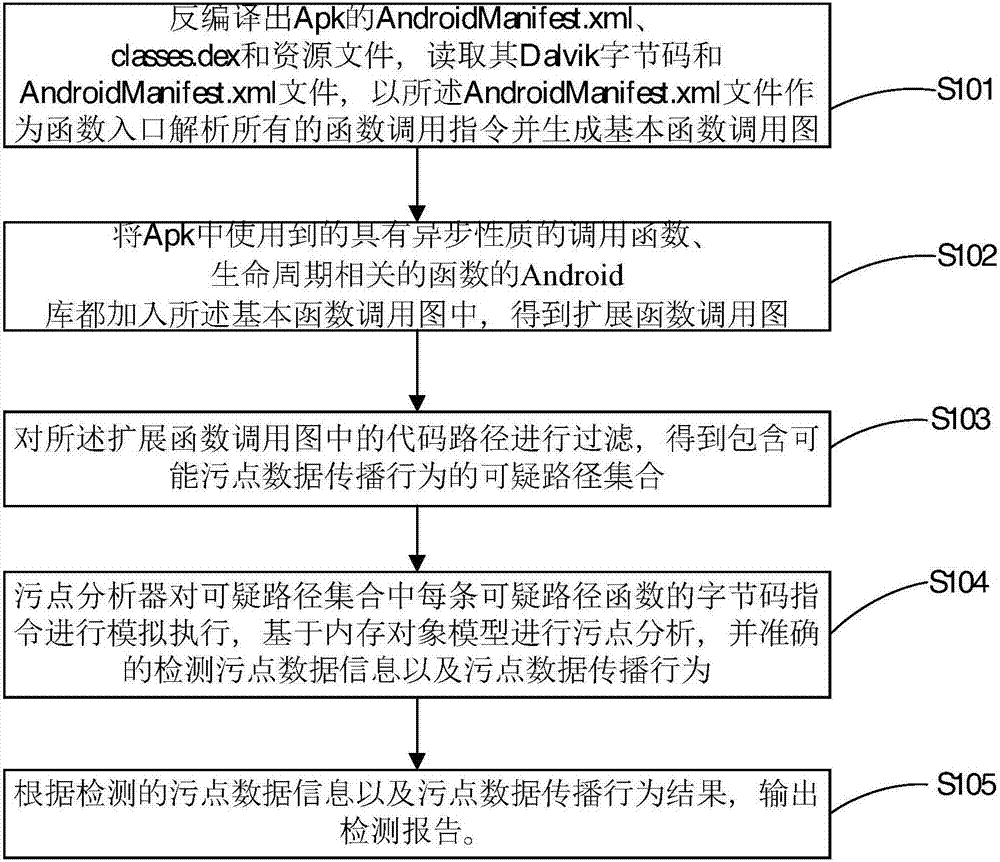
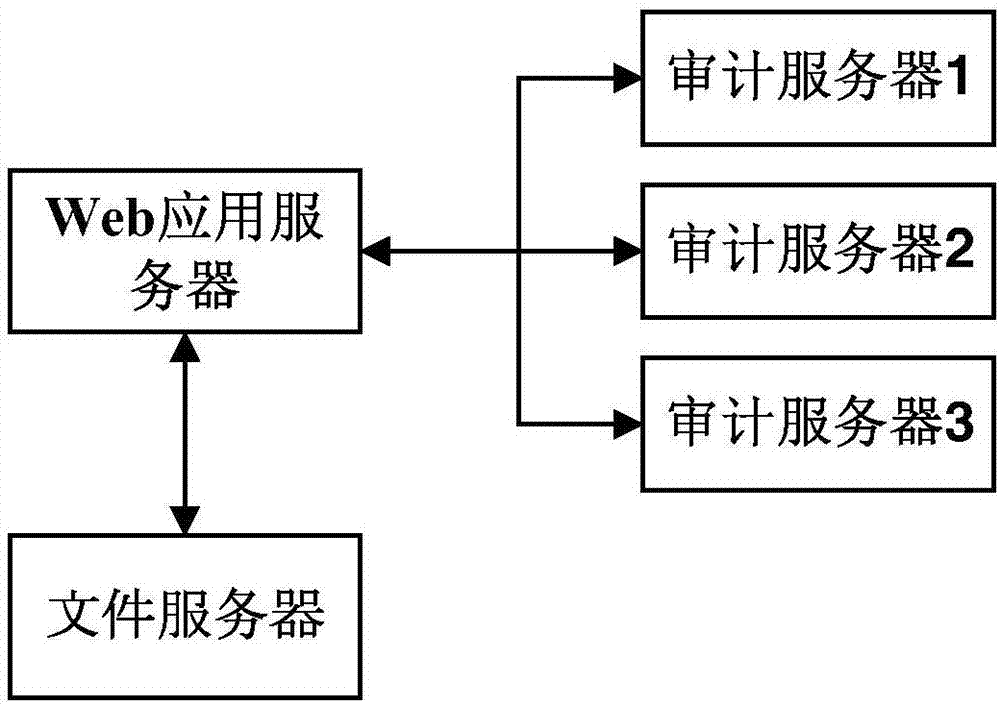
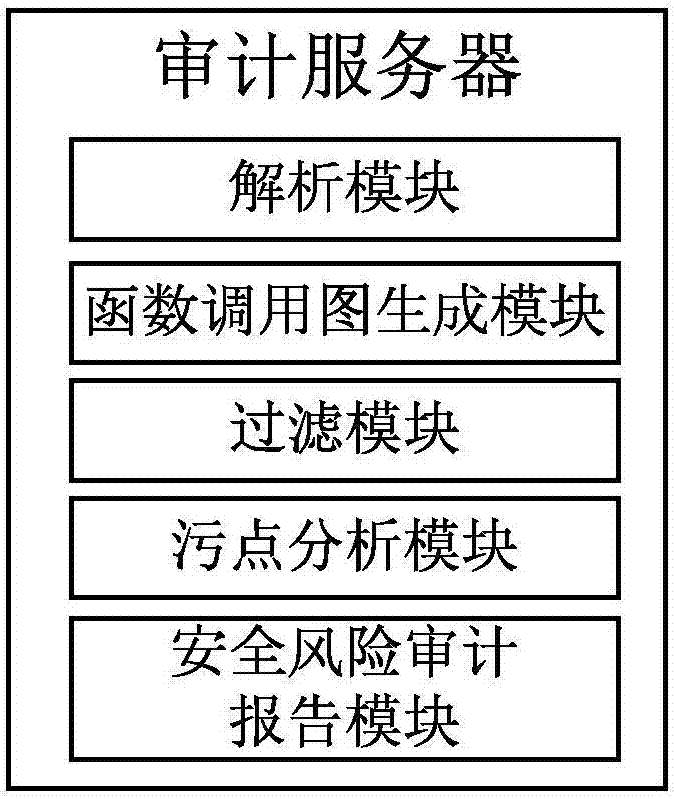
[0041] The present invention proposes an Apk security risk automated static audit system and method. The method is based on FlowDroid static stain analysis. When FlowDroid stain analysis deals with access to object domains or arrays, objects and arrays are processed through reverse alias analysis Reference problem, the time complexity rises to O(n 2 ). This method introduces the memory object model and fuzzy branch analysis on this basis. The introduction of the memory object model reduces the time complexity of processing object fields or arrays to O(n), and asynchronously calls functions and the life cycle of Android applications Related functions are included in the audit scope to expand the audit coverage of the App; the introduction of fuzzy branch analysis solves the detection problems of unknown value branches, infinite loop branches and infin...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap