Method for establishing virtual machine countermeasure technology based on hardware virtualization technology
A technology of hardware virtualization and establishment method, applied in computer security devices, instruments, electrical digital data processing and other directions, can solve the problem of inability to fight against anti-virtual machines
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
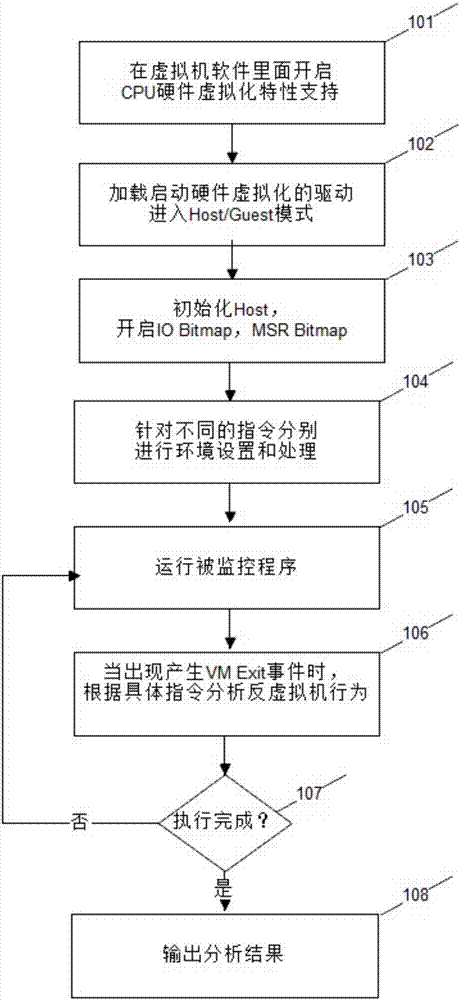
[0037] The present invention utilizes hardware virtualization technology to realize monitoring, hijacking and virtual execution of key instructions of a virtual host in a virtual machine-based manner, so as to monitor and deceive malicious codes, thereby gaining the initiative in virtual machine attack and defense confrontation.
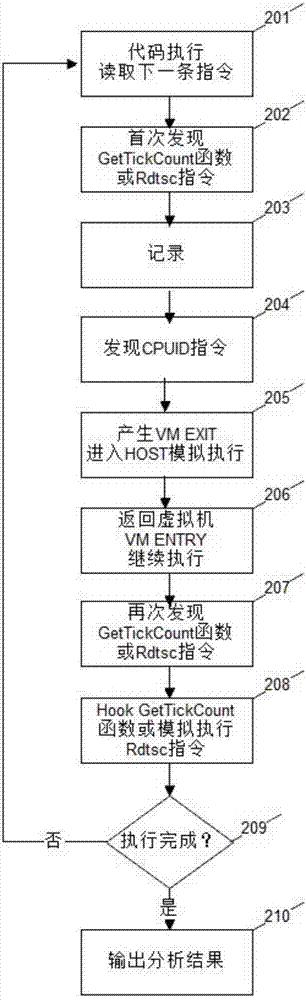
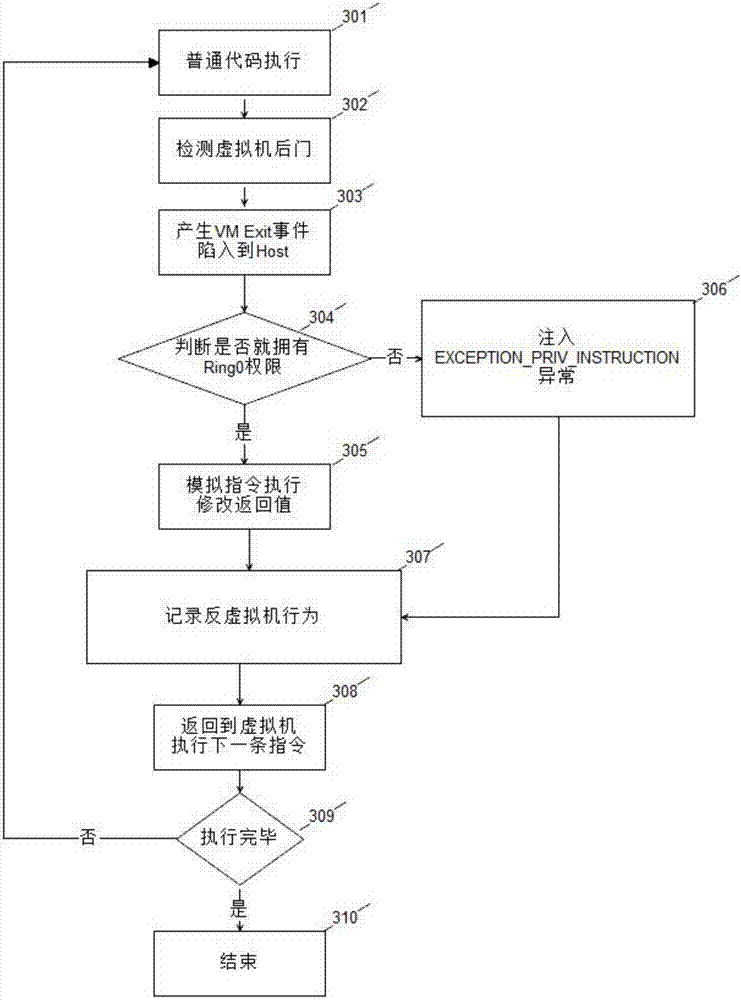
[0038] see figure 1 , is a schematic flow chart of the present invention. The present invention is a method for establishing a virtual machine confrontation technology based on hardware virtualization technology, and its specific process steps are as follows:
[0039] Step 101: Enable CPU hardware virtualization feature support in the virtual machine software. Depending on the manufacturer of the CPU, enable Intel VT-x or AMD-V. This patent takes the CPU generated by Intel as an example, and the protection right is not limited to the CPU.
[0040] Step 102: Load the driver for starting hardware virtualization, and then enter the host mode (Host mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com