Security verification method of user's running track
A technology of running trajectory and security verification, applied in the field of information security, can solve the problem that the security problem of user trajectory verification has not been completely resolved, and achieve the effect of resisting collusion attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
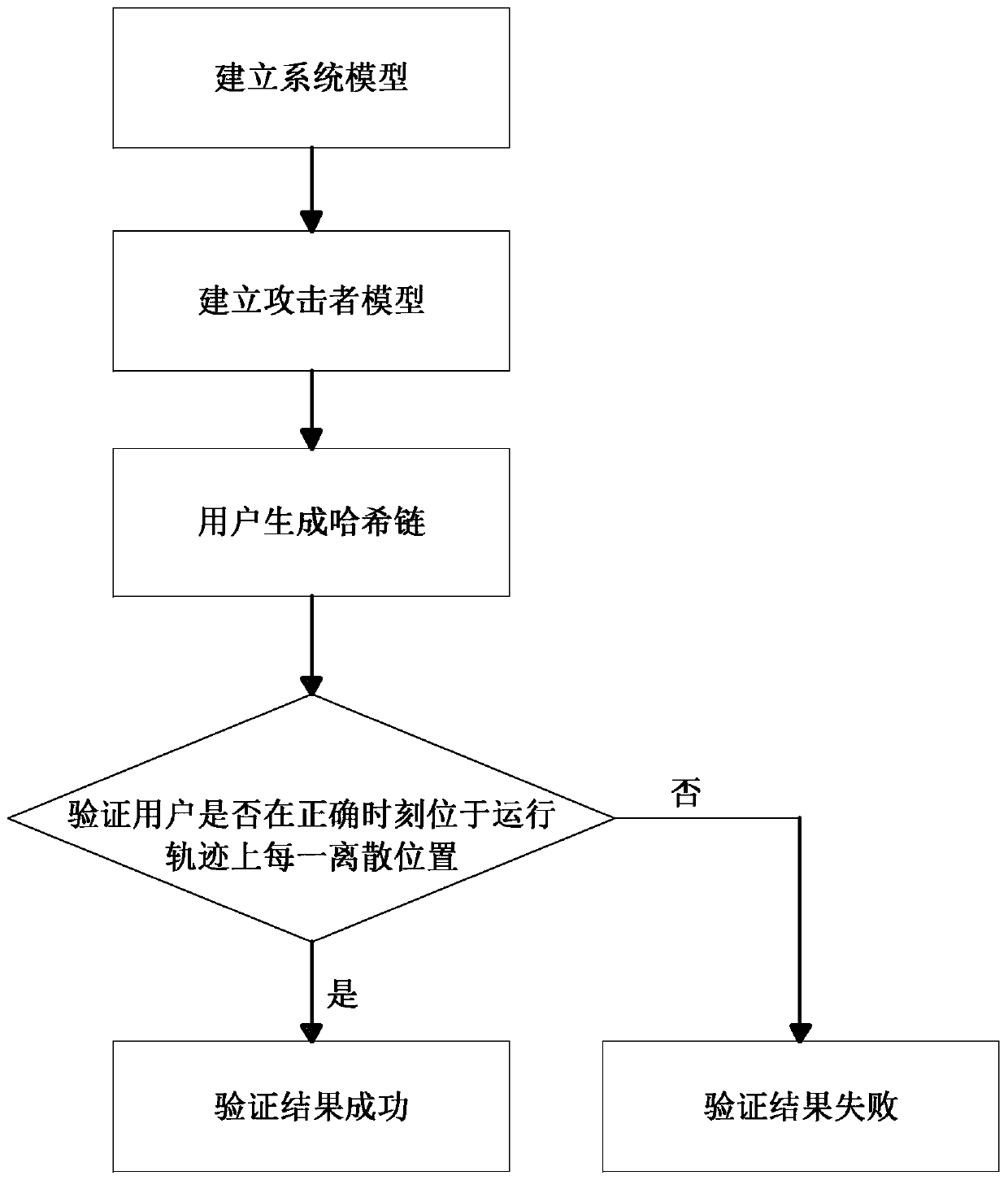
[0032] Due to the increasingly serious problem of network security in the world today, some unmanned or remote-operated operating equipment is facing more and more security attacks, and the attack level of opponents is getting higher and higher, which greatly affects the order of the system and society, and thus produces serious impact, and the existing trajectory verification technology cannot resist the collusion attack of the opponent. In view of this situation, the present invention has carried out research and innovation, and provides a security verification method for the user's running trajectory. See figure 1 , including the following steps:
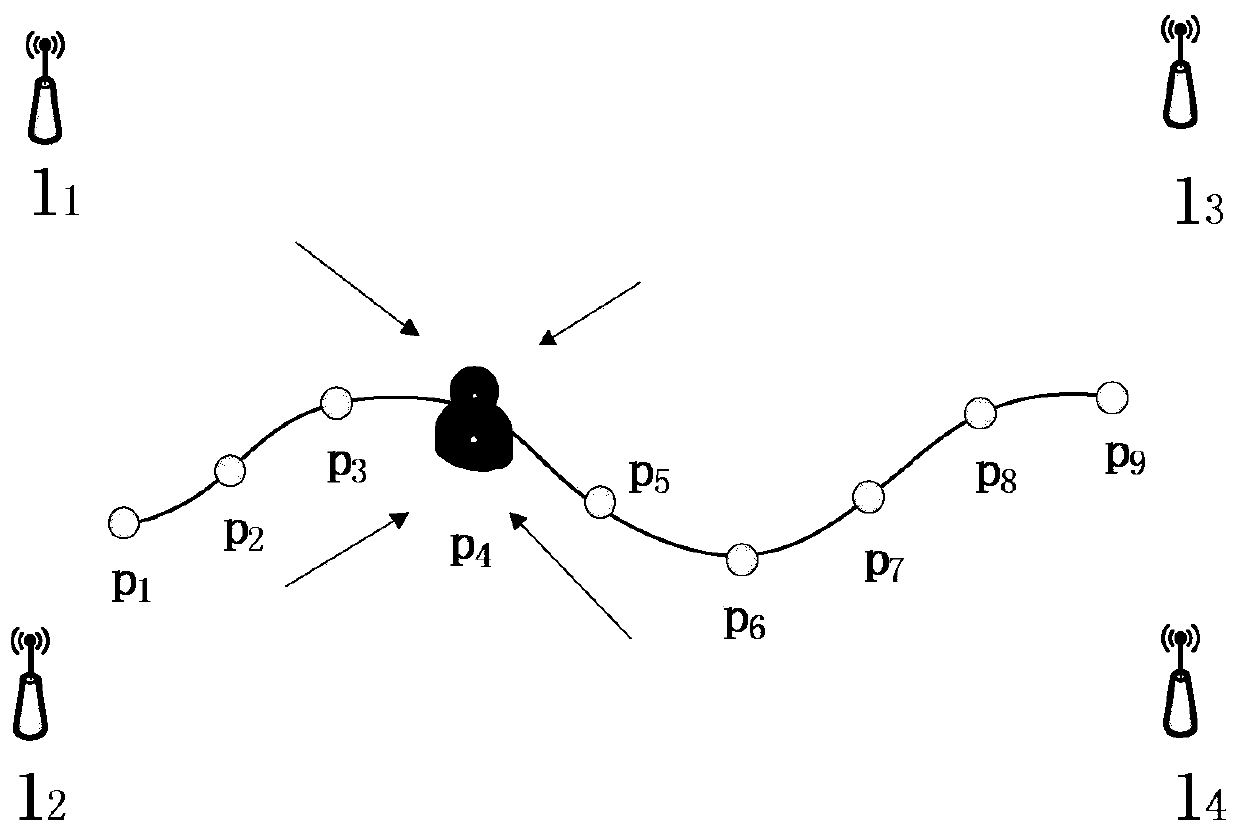
[0033] (1) Establish a system model: In the trajectory verification system, see figure 2 with image 3 , there are users, verifiers, attackers and trajectories to be verified. It is necessary to verify whether the user runs strictly according to the user's running track. Suppose there are four landmarks around the user's runnin...
Embodiment 2
[0043] The technical scheme of the safety verification method of the user's running track is the same as embodiment 1, wherein the position verification in the step (4) first adopts the safety positioning protocol SP to send the verification information, and the specific steps of using the safety positioning protocol SP to send the verification information are as follows:
[0044] 4a) Four Landmarksl 1 , l 2 , l 3 , l 4 First proceed to pair at the first discrete position p 1 The user sends verification information, let the position number be i, since there are n discrete positions in the user's running track, so 1≤i≤n, first initialize the position number i to 1;
[0045] 4b) Four Landmarksl 1 , l 2 , l 3 , l 4 Select the key k separately i,1 ,k i,2 ,k i,3 ,k i,4 ←{0,1} r , r represents the length of the key, and the four landmarks propagate k to each other on the private channel i,1 ,k i,2 ,k i,3 ,k i,4 , landmark l 2 , l 3 , l 4 Generate random informatio...
Embodiment 3
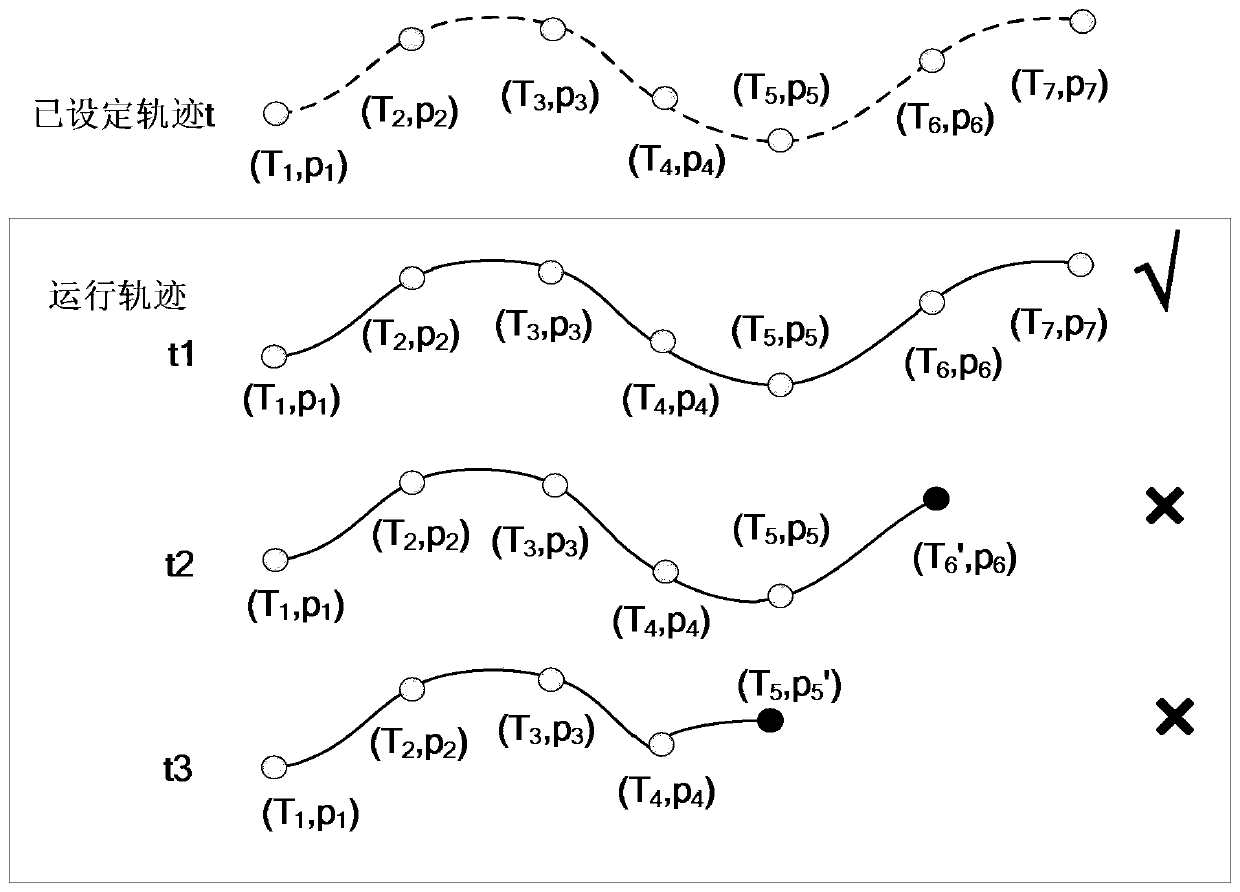
[0059] The technical scheme of the safety verification method of the user's running trajectory is the same as that of embodiment 1-2, and the judgment of the user response information described in step (4) completes the position verification, and the specific steps are as follows:
[0060] 4e) T i time to p i The user of the point can obtain the position p through the secure positioning protocol SP i The fourth key k of i,4 , will respond to message M i =ID U ||k i,4 ||s i broadcast, making the response message M i Teleport to four landmarks l 1 , l 2 , l 3 , l 4 , four landmarks l 1 , l 2 , l 3 , l 4 Verify the received response message M separately i The fourth key k in i,4 , complete the discrete position p in the user's running trajectory i point of location authentication, where ID U is the user identity, k i,4 for p i position fourth key, s i =H n-i+1 (S U ), is the i-th identity key;
[0061] If the location number i=1 and four landmarks l 1 , l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com