Heterogeneous wireless sensor network predistribution key management method
A wireless sensor and sensor network technology, applied in wireless communication, network topology, electrical components, etc., can solve the problems of poor survivability of the q-composite scheme, large node resource consumption, and key duplication, etc., and achieves key duplication. The effect of less likelihood, reduced storage requirements, and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0025] Specific implementation mode 1: The specific process of the heterogeneous wireless sensor network pre-distributed key management method of this embodiment is as follows:
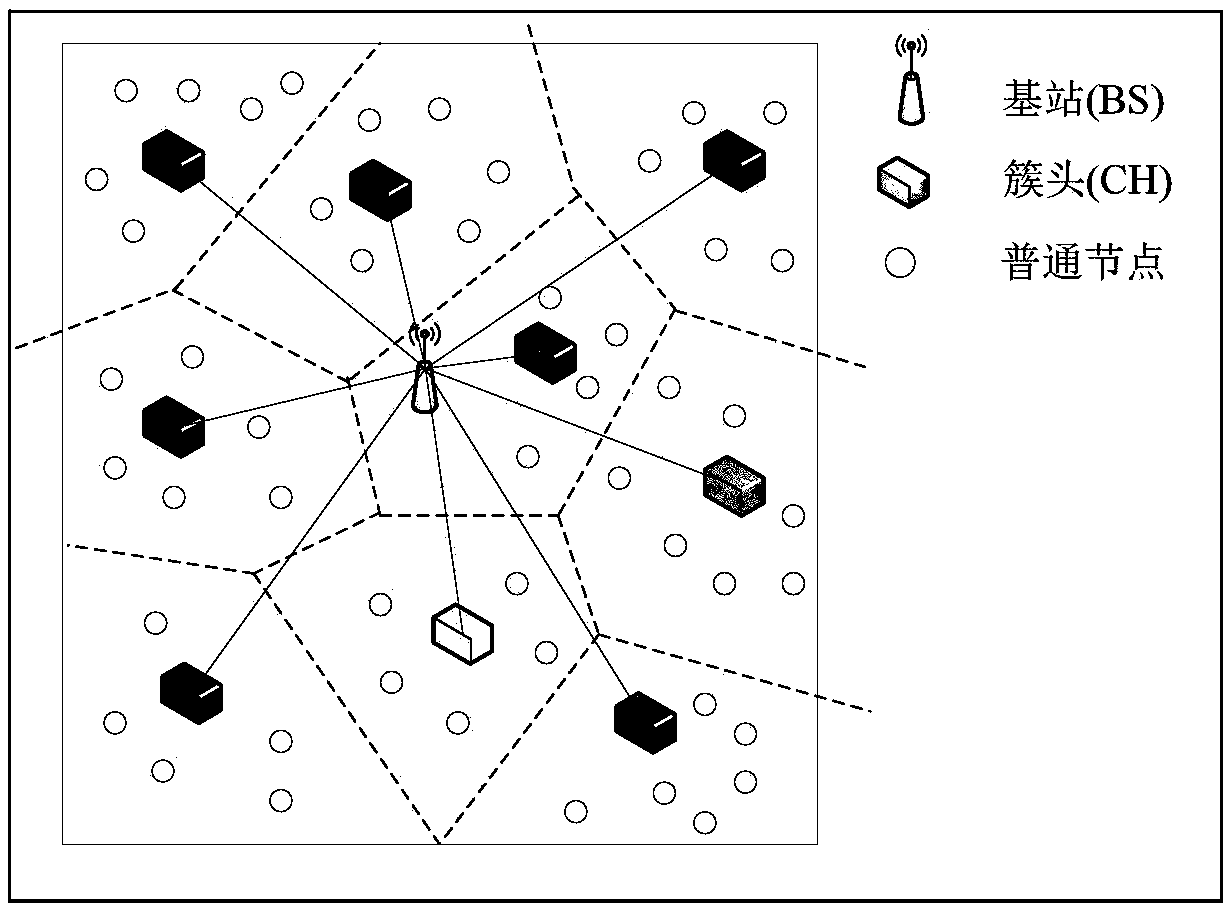
[0026] Step 1. Build the HWSN cluster model;
[0027] HWSN is a heterogeneous wireless sensor network;
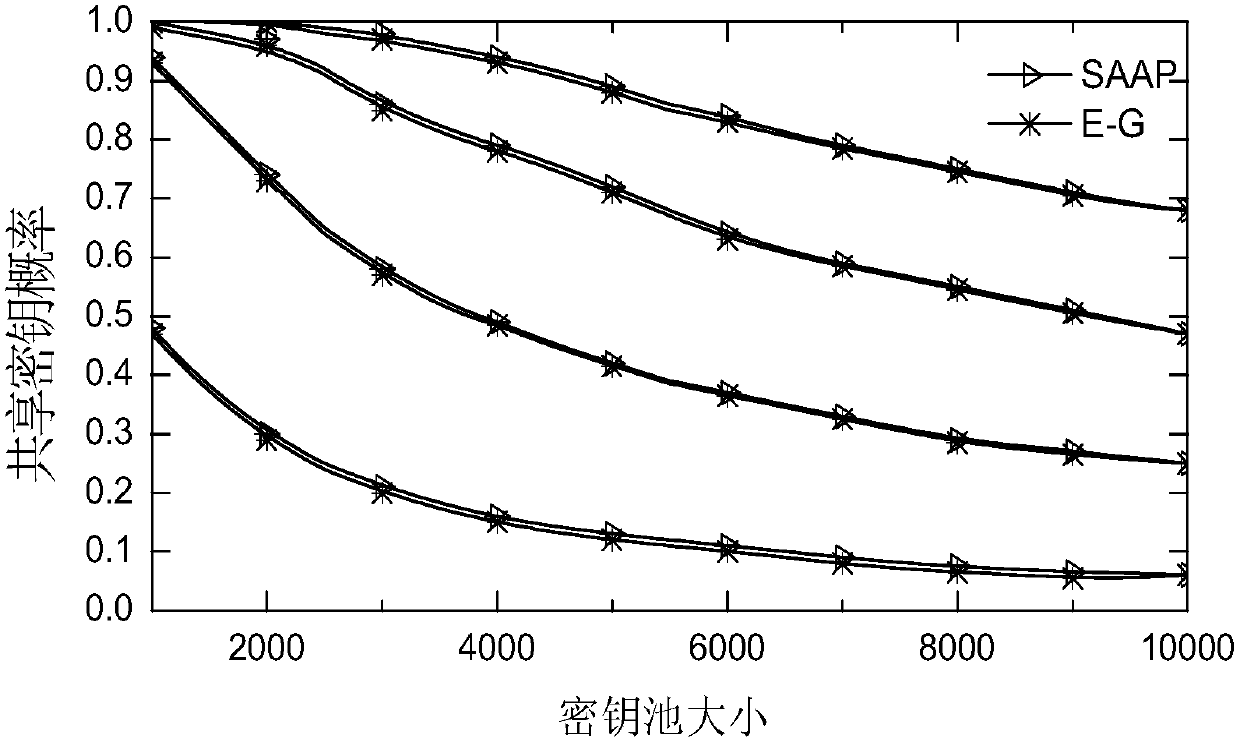
[0028] Step 2: Under the HWSN cluster model constructed in Step 1, establish a SAAP scheme; the process is:
[0029] The SAAP scheme is an asymmetric pre-distributed key management scheme based on Schnorr identity authentication;
[0030] Step 21. Establish the Schnorr identity authentication stage;
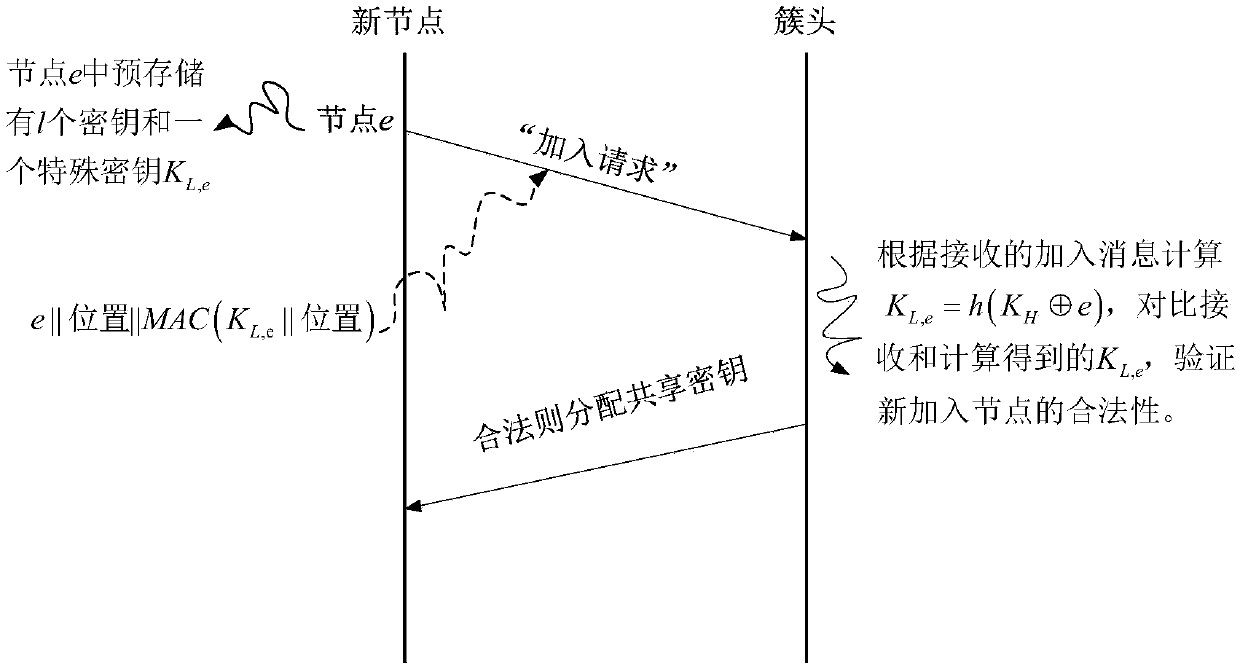
[0031] Step 22: On the basis of step 21, establish a key pre-distribution stage;
[0032] Step 23: On the basis of step 21 and step 22, the legal authentication node in the network enters the shared key discovery stage;
[0033] Step 24: After performing Step 23, if the LN node has not established a pairing key with a neighbor node, enter the cluster head-based pairing key setting stage;
[0034]...
specific Embodiment approach 2
[0036] Embodiment 2: The difference between this embodiment and Embodiment 1 is that the HWSN cluster model is constructed in the step 1; the specific process is:
[0037] Assume that both CH (cluster head node) and LN (normal node) are randomly and evenly distributed in the network, where CH is an energy-aggregating cluster head. In the process of sensor network initialization, each cluster head node CH broadcasts a Hello message to its nearby LN nodes with maximum power and random delay. After the LN node receives the Hello message from one or G cluster head nodes CH, it passes The cluster head selection method selects the CH with the strongest signal strength as the cluster head (the CH with the strongest signal in the Hello packet received by the LN as the cluster head), and each LN node records the Hello packets received from the CHs of other cluster head nodes. When the cluster head selection fails, other cluster head nodes CH will act as backup cluster heads;
[0038] ...
specific Embodiment approach 3
[0042] Embodiment 3: The difference between this embodiment and Embodiment 1 or 2 is that: the Schnorr identity authentication stage is established in step 21; the specific process is:
[0043] In order to further enhance the security of the network, before the shared key stage, each LN node in the cluster must be authenticated first;
[0044] Step 211: Initialize the sensor network according to the HWSN cluster model constructed in step 1;
[0045] The sensor network initialization process is divided into two steps:
[0046] (1) Select the public parameters of the sensor network;
[0047] The sensor network selects two prime numbers p and q, and p and q satisfy q|p-1, q≥2 140 ,p≥2 512 , the sensor network is Choose a prime number g of order q, and g q ≡1(modp);
[0048] q|p-1 means that q is a prime factor of order p-1;
[0049] (2) Node selection key in sensor network;
[0050] Any LN node A in the sensor network, at node A according to the random principle at Z p Se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com