Non-key signature infrastructure building method based on block chain
A construction method and blockchain technology, applied in the field of blockchain-based keyless signature infrastructure construction, can solve the problems of long CRH release cycle, difficult identification and processing, lack of credibility of the release media, etc., and achieve throughput Strong volume and scalability, low storage and network load requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
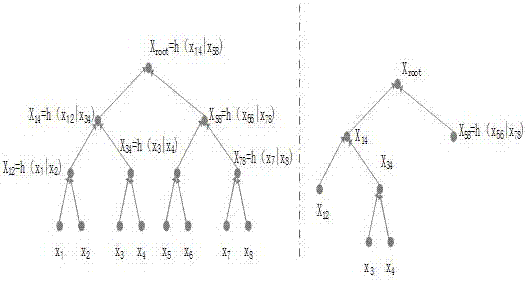
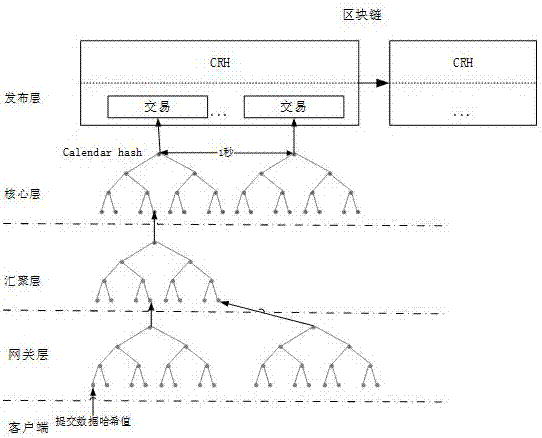
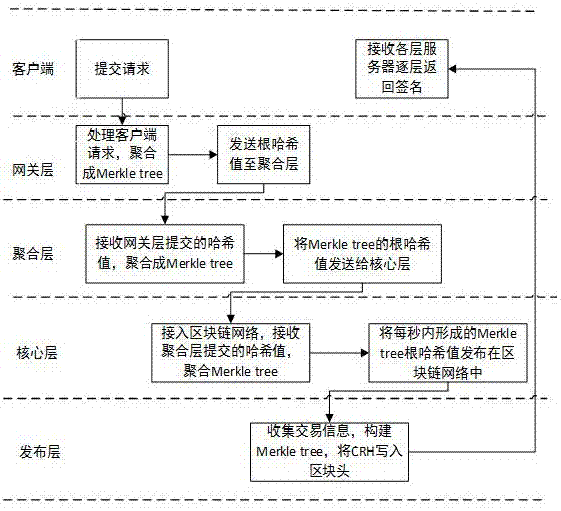
[0043] In order to make the objectives, technical solutions and advantages of the present invention clearer, the following further describes the present invention in detail with reference to the drawings and specific embodiments.
[0044] n Blockchain
[0045] Blockchain is a decentralized recording technology. It participates in any number of nodes in the system, and records all the data exchanged in the system for a period of time into a block through cryptographic methods, and at the same time generates the block The fingerprint is used to link the next block and verify. All participating nodes in the system jointly determine the record and verification, and jointly determine whether the record is true, and each node can make a copy of the complete record. Compared with traditional accounting technology, its characteristics are as follows:
[0046] 1) The chain jointly maintained by the system nodes is constantly growing, and only records can be added, and the records that have ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com