A rights management method, a rights management device and an intelligent terminal
A technology of authority management and authority, which is applied in the field of information security, can solve problems such as personal data leakage, automatic exit of applications, unusable applications, etc., and achieve the effect of ensuring the security of personal information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
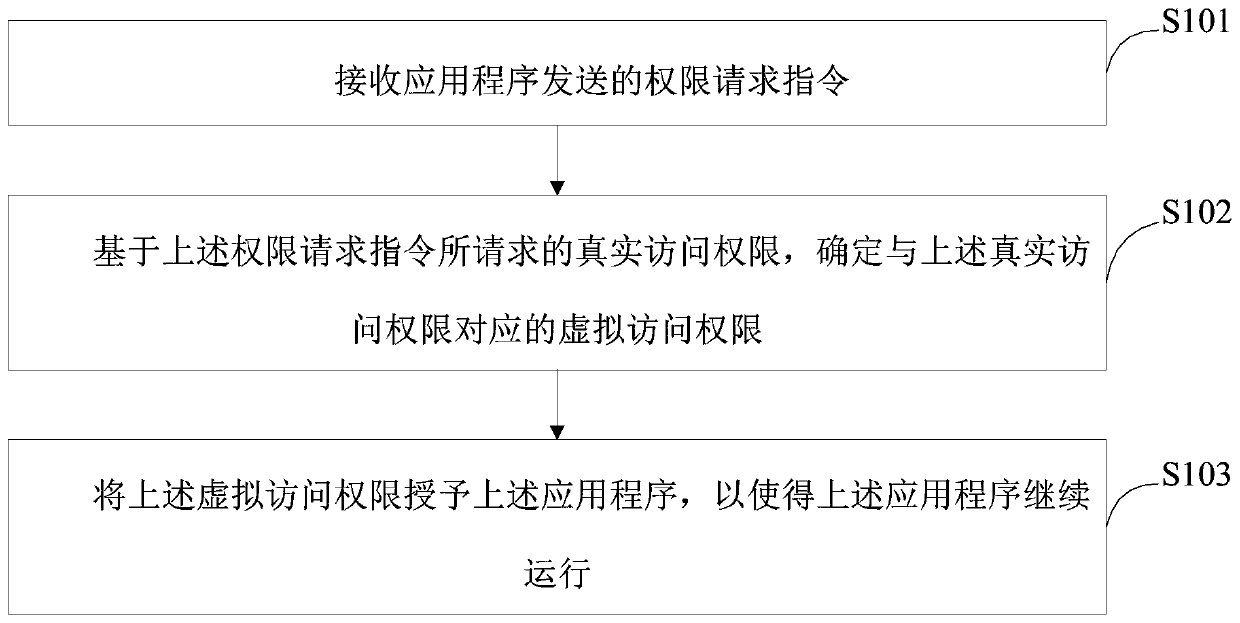
[0024] figure 1 The implementation process of the rights management method provided by Embodiment 1 of the present invention is shown, and the details are as follows:
[0025] In step S101, the permission request instruction sent by the application program is received;
[0026] In the embodiment of the present invention, during the running process of the application program, the permission request instruction sent by the application program is received. Specifically, it may be to receive the permission request instruction sent by the application program when the application program is installed; or, in step S101, it may also be to receive the permission request instruction sent by the application program when the application program is used. limited.
[0027] In step S102, based on the real access permission requested by the permission request instruction, the virtual access permission corresponding to the real access permission is determined;
[0028] In the embodiment of ...
Embodiment 2
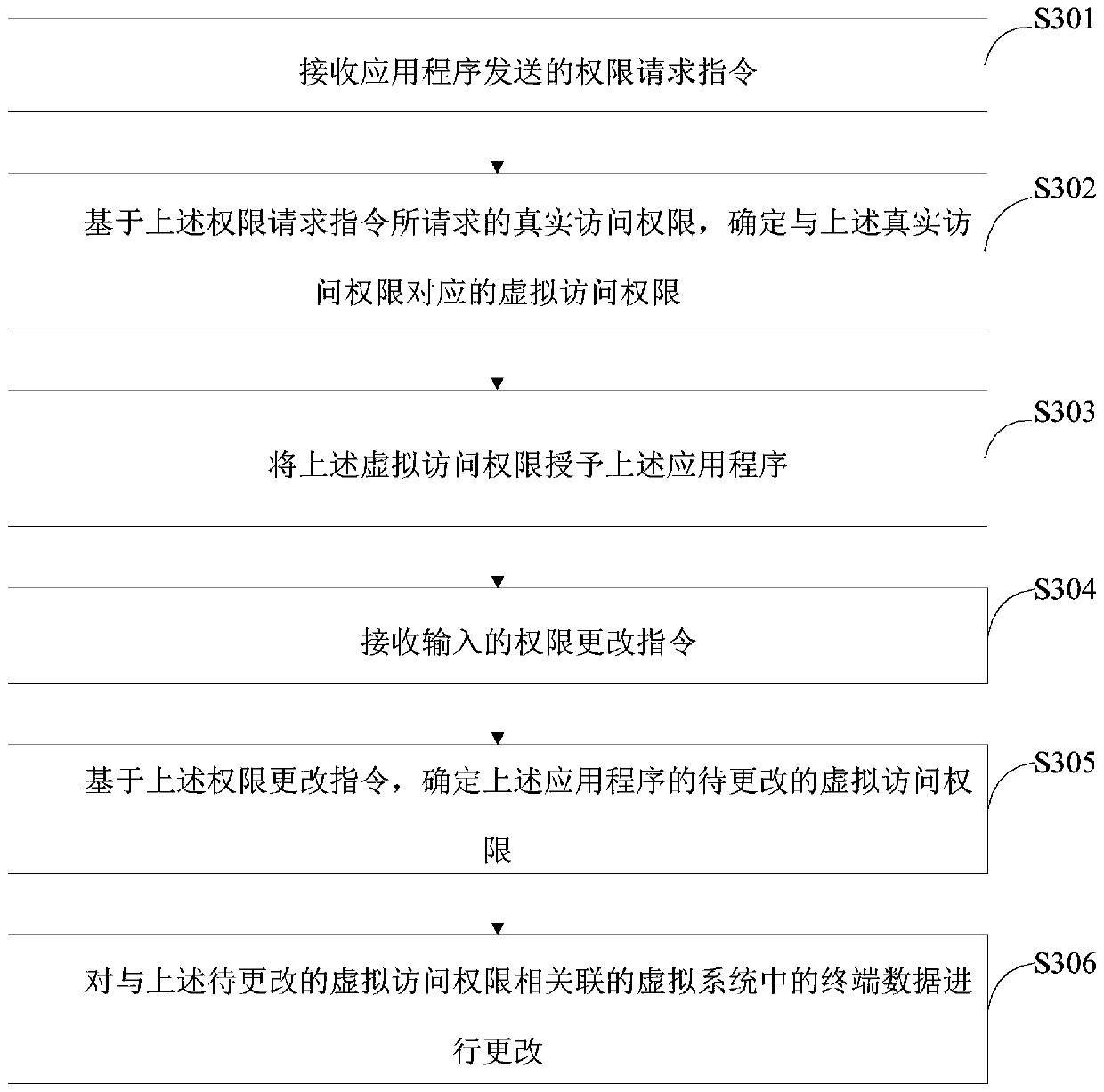
[0045] On the basis of embodiment one, figure 2 The implementation flow of another rights management method provided by Embodiment 2 of the present invention is shown, and the details are as follows:
[0046] In step S301, a permission request instruction sent by an application program is received;
[0047] In step S302, based on the real access permission requested by the permission request instruction, determine the virtual access permission corresponding to the real access permission;
[0048] In step S303, granting the aforementioned virtual access authority to the aforementioned application program;
[0049] In the embodiment of the present invention, the implementation manners of the above step S301 to the above step S303 are the same as or similar to those of the above step S101 and the above step S103 respectively, which will not be repeated here.
[0050] In step S304, receiving an input authority change instruction;
[0051] In the embodiment of the present inven...
Embodiment 3
[0059] Figure 4 A structural block diagram of the rights management device provided by the embodiment of the present invention is shown, and for convenience of description, only parts related to the embodiment of the present invention are shown. The rights management device 4 includes: a request receiving unit 41 , a rights determining unit 42 , and a rights granting unit 43 .
[0060] Wherein, the request receiving unit 41 is configured to receive the permission request instruction sent by the application program;
[0061] The authority determination unit 42 is configured to determine the virtual access authority corresponding to the above-mentioned real access authority based on the real access authority requested by the authority request instruction received by the above-mentioned request receiving unit 41, wherein the above-mentioned real access authority is the same as that of the terminal in the real system data association, the above-mentioned virtual access rights ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com